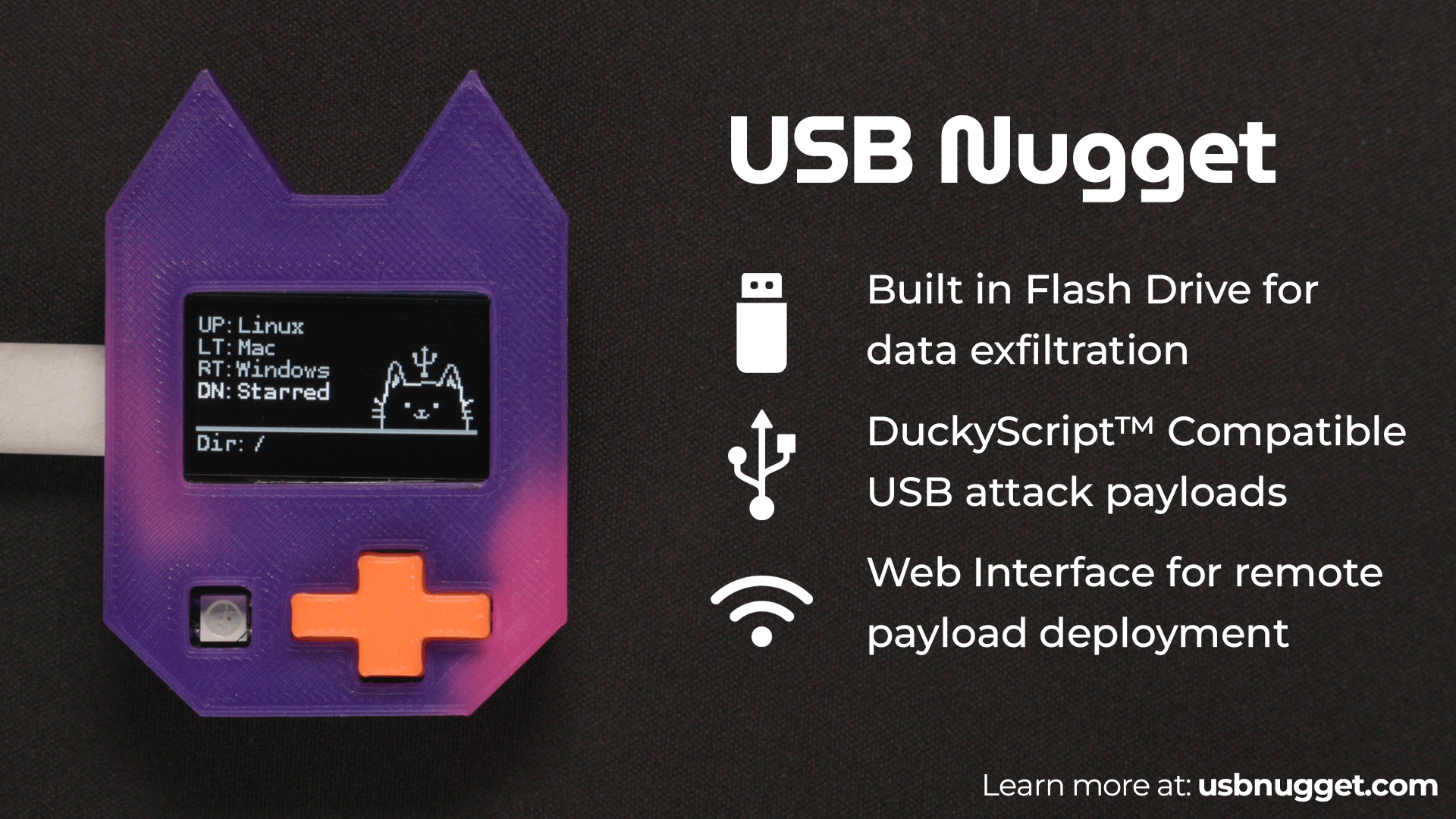
A versatile USB attack platform that lets you hack computers in seconds using a USB Nugget!
- Download the latest binary file here
- Place your Nugget in Device Firmware Upgrade (DFU) mode.
- Open our web flasher tool in Google Chrome (other browsers not currently supported)
- Click on "Connect" and then select the "ESP32-S2" board. Click "Erase" and "OK" to continue.
- Once you see "Finished", click "Choose a file" and select the .BIN file you downloaded in step one. Click "Program" to flash your Nugget!
- When its done, unplug your Nugget and plug it in again to see the new features.
To upload a payload, you can save a .txt file to the USB Nugget flash drive. Payloads must be saved under an operating system, then category type. (OS->Category->Payload.txt)
To access the web interface, connect to Nugget AP with the password nugget123. In a web browser, navigate to 192.168.4.1 to access the payload deployment system.
To edit your USB Nugget's default AP name & password, edit or create the .usbnugget.conf file on your NUGGET drive, and add the following 2 lines:
network = "Nugget AP"
password = "nugget123"
To change the VID and PID of the keyboard, you can just add:
vid = "0x05ac"
pid = "0x20b"
If .usbnugget.conf is not present or contains invalid entries, the above
settings will be used.
- DuckyScript Compatible
- Basic syntax:
STRING,DELAY, keypress combos - Basic colors:
RGBCYMW - International keyboard support
- German:
LOCALE DE - US English:
LOCALE EN - Spanish:
LOCALE ES - French:
LOCALE FR - Portuguese:
LOCALE PT
- Basic syntax:
- Web Interface
- Deploy payloads
- Edit payloads
- Create new payloads
- USB Flash Drive
- FAT filesystem
- Create default OS folders
- Follows Hak5 naming convention (OS->Category->Payload)
- Nugget Interface
- Custom graphics
- Live command preview
- Reactive RGB NeoPixel