API study
arpit-dwivedi opened this issue · 19 comments
Amazon, Microsoft and Google are the leading solution providers in AI.
These are the solutions provided by these three,
As you can see all three provide the most common solution, but what is the difference.
This issue is for studying the differences between these three solution providers.
After studying, comment the difference in all three in tabular format.
Note: Just do the surface study for now, we'll study separate API's later.
API
- An application programming interface (API) is a computing interface that defines interactions between multiple software intermediaries. It defines the kinds of calls or requests that can be made, how to make them, the data formats that should be used, the conventions to follow, etc.
What is meant by API with example?
- An Application Programming Interface (API) is a tool set that programmers can use in helping them create software. ... An example is the Apple (iOS) API that's used to detect touchscreen interactions. APIs are tools. They allow you as a programmer to deliver solid solutions fairly rapidly.
What is an API used for?
- An API (Application Programming Interface) is a set of functions that allows applications to access data and interact with external software components, operating systems, or microservices. To simplify, an API delivers a user response to a system and sends the system's response back to a user
How does an API work?
- API stands for Application Programming Interface. An API is a software intermediary that allows two applications to talk to each other. In other words, an API is the messenger that delivers your request to the provider that you're requesting it from and then delivers the response back to you.
What does Filestack do?
Whenever you need to manage files in your application, whether it’s web, mobile or a desktop environment, Filestack can help you provide amazing experiences to your users through various, carefully crafted UI integrations (like our File Picker or Tranformation UI. They are easy to implement and they are backed by Filestack’s powerful APIs that are simple to use and provide great flexibility to your Software Developers.
Filestack operates in three main areas of the modern software file management systems: Uploads, Transformations and Delivery (that includes performance optimization, responsiveness, etc.). For your business teams we can also provide insights into how your users use the system and what impact that has to your business objectives.
Uploads
So you have to give your users ability to upload files in your application. To provide them with the best experience you can integrate Filestack’s File Picker that not only allows them to upload files from their local computer but it also integrates with the most popular social media networks, like Facebook or Instagram, commonly used storage solutions like Google Drive or Dropbox and stock image providers like Unsplash.
File Picker is extremely configuratble and customizable what gives your developers flexibility when they integrate it in your application. And it is very quick to start with - you can have production-ready file uploading functionality in less than an hour.
Filestack ships File Picker for Web (JavaScript, React, Angular) and natively for iOS and Android.
Under the hood, File Picker is utilizing powerfull Filestack API that is also available to your Developers through number of Open Source SDKs.
Where to go for more information:
• File Picker Quick Start
• Uploading Overview
Delivery
For every file uploaded with Filestack, you will receive uniqe URL that you can use to display it in your application, download it or transform it using Filestack’s Processing API.
Filestack CDN is extremely fast and reliable Content Delivery Network, designed to give your users world class performance wherever they are.
With Filestack you can also deliver external URLs and files from your own Storage, without a need to re-upload those files.
Where to go for more information:
• Filestack CDN and Caching Overview
• Filestack Storage Overview
• Blog: Filestack CDN - Deliver Content Anywhere, Faster
Transformations
In most cases you will not want to present your users with the files uploaded as is. You might want to transform those files in a way that they conform with your application requrements. For example you might want to resize, rotate or enhance your images before displaying them to your users, or you might want to convert Office documents to PDF format before you show preview to your customers.
Filestack’s Processing Engine is very powerful system that allows developers to transform various types of files,including images, documents and videos. Additionally we provide insights into the contents of the files through our Intelligence System
With Filestack you can transform your files either in real time, by appending parameters to the URLs, or asynchronously using Workflows.
If you need to give your users ability to transform images, you can use Transformation UI to provide them with beautiful UI and and great experience manipulating their files.
GOOGLE CLOUD VISION
- The Google Cloud Vision API allows developers to easily integrate vision detection features within applications, including image labeling, face and landmark detection, optical character recognition (OCR), and tagging of explicit content. In this codelab you will focus on using the Vision API with Python.
- Based on the Tensorflow open-source framework that also powers Google Photos, Google launched the Cloud Vision API (beta) in February 2016. It includes multiple functions, including optical character recognition (OCR), as well as face, emotion, logo, inappropriate content and object detection.
Microsoft Cognitive Services
- Formerly known as Project Oxford, Microsoft Cognitive Services encompasses 22 API’s that include a wide variety of detection API’s such as dominant color, face, emotion, celebrity, image type and not-safe-for-work content (NSFW). For the purposes of our object recognition testing, we focused on the Computer Vision API (preview), which employs the 86-category concept for tagging.
Amazon Rekognition
- Amazon Rekognition is an image recognition service that was propelled by the quiet Orbeus acquisition back in 2015. Rekognition is focused on object, facial, and emotion detection. One major difference from the other services tested was the absence of NSFW content detection. Moving forward, Amazon has thrown their full support behind MXNet as their deep-learning framework of choice.
Performance Testing
- MacBook Pro, Kraków, 1000 files, 10 at a time
| Average | Minimum | Maximum | 90th percentile | |
|---|---|---|---|---|
| Amazon | 2.42s | 1.03s | 3.73s | 3.21s |
| 1.23s | 0.69s | 1.68s | 1.42s | |
| Microsoft | 1.11s | 0.65s | 5.07s | 1.5s |
- N. Virginia, 1000 files, 10 at a time
| Average | Minimum | Maximum | 90th percentile | |
|---|---|---|---|---|
| Amazon | 1.1s | 0.302s | 3.64s | 1.97s |
| 0.98s | 0.4s | 1.79s | 1.12s | |
| Microsoft | 1.38s | 0.81s | 4.22s | 2.14s |
- N. Virginia, 3000 files, 10 at a time
| Average | Minimum | Maximum | 90th percentile | |
|---|---|---|---|---|
| Amazon | 1.08 | 0.25 | 2.71 | 1.96 |
| Amazon S3 | 1.26 | 0.35 | 4.02 | 2.17 |
| 0.97 | 0.41 | 2.87 | 1.11 | |
| Microsoft | 1.31 | 0.73 | 14.74 | 1.87 |
Object recognition testing
| Amazon | Diagram (92%), Plan (92%), Atlas (60%), Map (60%) |
|---|---|
| Map (92%), Plan (60%) | |
| Microsoft | Text (99%), Map (99%) |
I prepared a DOC file with all details Please go through it
API
Application Programming Interface:
An Application Programming Interface (API) is a tool set that programmers can use in helping them create software. A good API will have clear and concise commands that a programmer can use and reuse, so they don't have to build everything over again.
Even Windows has a huge set of APIs that you can use in order to work with the user interface. There's no need to completely rebuild forms, commands, or even scroll bars. All of these actions are accessible within various APIs, and can be brought into your program. This also ensures a consistent look and feel among applications, but still allows for unique functionality.
You can find APIs for both standard desktop computers and mobile devices. With the explosion in mobile device usage, like iPhones and Androids, the number of mobile-ready APIs has grown exponentially. Many may seem basic, but are huge for developers who need to quickly develop apps. An example is the Apple (iOS) API that's used to detect touchscreen interactions.
APIs are tools. They allow you as a programmer to deliver solid solutions fairly rapidly. If you have to rebuild everything from scratch every time, your solutions will be cumbersome.
There are, many API providers, but Amazon, Google, and Microsoft top all of them in the context of AI or ML.
Here is a brief comparison of these companies.
-
Considering speech/text recognition first:
From the above table, we can clearly see, that Google does not provide the benefits of text-speech APIs.
Diving deep into this comparison,
Let's find out, how many languages are supported by these companies or what are the prices of using them etc -
A better API for any text-speech or speech-text is that which have the least errors. Below table, shows a brief comparison of that -
Voice recognition:
Apart from speech recognition, voice recognition can also be another criteria to discuss upon.
Below table, briefs out the comparison -
Cloud Machine Learning:
As these 3 compaines are the leading API providers for AI,ML, it is very interesting to the differences between them,
like shown below -
In response to Issue :
Image Analysis API’s Comparison of Amazon, Microsoft, and Google
The battle from web browsers and online search has progressed into another arena — Artificial Intelligence. A battle that every IT organization today wants to win through key AI talent hires and acquisitions. The race to develop and deploy powerful AI tools is one of the hottest topics in the tech world and organizations in every industry are already investing a hefty sum in AI-based tools to boost business profitability.
Tech biggies like Amazon, Microsoft, and Google are the forerunners leveraging artificial intelligence. These top tech giants are using AI to deliver better products and services by positioning themselves at the crossroads in the challenging and competitive AI race on the road ahead.
Before proceeding further we should know a few terms:
What is Amazon Rekognition Image?
Amazon Rekognition is one of the leading service providers to add powerful visual analysis to your applications. Rekognition lets you easily build applications with their APIs to search, verify, and organize millions of images. They have the ability to detects objects, scenes, and faces, extract text, recognize celebrities, and identify inappropriate content in images. It also allows you to search and compare faces.
What is Azure Cognitive Services?
Computer Vision API is hosted on Microsoft Azure and provides developers with access to advanced to image processing algorithms returning information after analyzing the images. By uploading an image or specifying an image URL, Microsoft Computer Vision algorithms can analyze visual content in different ways based on inputs and user choices.
What is Google Cloud Vision?
Cloud Vision API enables developers to understand the content and hidden information of an image by using machine learning models with the help of the REST API. It spontaneously classifies images into thousands of categories, detects unique objects and faces within the images, and reads printed words that are contained within images. This API allows you to build metadata on your image catalog, moderate offensive content, and enables the use of new marketing scenarios through image sentiment analysis.
As in issue, we see all three provide the most common solution, but what is the difference.
To know the differences between these three solution providers, I have created tabular data for easy understanding which helps to determine which service to use, by looking at features, pricing, image size limits, rate limits, some advantages & disadvantages, and usecases. --
| Amazon | Microsoft | ||
|---|---|---|---|
| Image processing API’s (Click on the particular to know more) |
Amazon Rekognition | Microsoft Azure Cognitive Services | Google Cloud Services |
| Image Size Limits | 5Mb / Image, 15Mb / Image from S3 | 4 MB / Image | 20 MB / Image |
| Rate limits | Not defined in documentation | 10 Requests per second | Varies by plan |
| Pricing details on service provider website | Amazon pricing details | Microsoft Machine vision pricing | Google Cloud Vision Pricing |
| Advantages | 1] This API can analyze 5,000 images per month 2] Store up to 1,000 face metadata per month |
1] The API learning curve is made easier in different ways with quick starts, tutorials, and samples. 2] The options of either uploading the image or passing a URL are both available. 3] The response times are very good. 4] High level of SLA guarantying that the standard tier will be available at least 99.9 percent of the time. 5] Tightly Integrated with Microsoft Azure, blog Storage, SQL database, and Virtual machine so can be packaged as an end to end solution. |
1] They have no upfront costing and it is a pay as you go service with no termination fees. 2] Google comes with the highest security, privacy, and compliance control where it provides ISO and SOC certification for the products 3] Cloud vision API can detect any object using Google Image Search. 4] Cloud Vision can moderate content search using the powerful Google Analytics. 5] Multiple filter parameters can be applied to a single image. |
| Disadvantages/ Limitations | 1] The maximum image size that can be stored as an Amazon S3 object is limited to 15 MB. 2] The minimum pixel resolution for height and width is 80 pixels. 3] It supports only JPEG and PNG image formats. The video must be encoded using the H.264 codec. The supported file formats are MPEG-4 and MOV. 4] For detection, the face dimension must be no smaller than 40×40 pixels in an image with 1920X1080 pixels. Images having dimensions higher than 1920X1080 pixels will need a larger minimum face size proportionally. |
1] If you go beyond the mentioned number of transactions per second, your response time will be throttled to be within the agreed-upon limit, so if you get bursts of calls — you will have a problem. 2] Usage-based pricing model can be difficult to comprehend and implement effective cost controls. |
1] Cloud Datastore is feature-limited and hard to switch out from. 2] Google CDN does not work with custom sources 3] StackDriver (GCP logs) feels detached. 4] Facial Recognition is not supported. |
| Use cases | 1] Use Label detection across multiple images, do face detection and comparison, image moderation and text in image detection 2] Ability to correct images for uploading the right orientation 3] Ability to detect and breakdown scene elements 4] Do monitoring for statistics like how many faces are tracked and how many requests are sent per second. 5] It is able to facial recognition like the position of the eye and other facial features. |
1] Image classification applications using 2000 recognizable objects, living beings, scenery, and actions 2] Identification, categorization, and tagging images 3] Identifying faces, mood, age, and scene 4] Optical Character Recognition (OCR) to detect text content in an image and helpful for maintaining records for medical, security, banking, and in general record-keeping 5] Intelligent manipulation of photos and restriction to show moderated content |
1] Run image detection and animation on a batch of images 2] Face Detection detects multiple faces within an image along with the associated key facial attributes such as emotional state or wearing headwear 3] Detects popular product logos within an image 4] Text Detection performs Optical Character Recognition. It detects and extracts text within an image with support for a broad range of languages. It also features automatic language identification. 4] Landmark Detection detects popular natural and man-made structures within an image. |
Amazon vs Microsoft vs Google
The big three Amazon, Microsoft and Google provide important technologies and services in the field of cloud, ML and AI. Machine Learning as a service is being used by many corporate for delivering their deliverable to clients and also enhancing the solution on the go and with cloud and pandemic around the corner the importance of these service has increased many folds.
MLaas is provide in the cloud-based service for AI solutions. So here is a comparison of the big three below:
Major Clients of the big three

Image Text Comparison
There was handwriting imaging comparison by CAZTON based on AI models performed on the three service providers.
We will be comparing the following three services for their accuracy to convert handwritten documents correctly:
• Amazon Textract
• Microsoft Azure Vision
• Google Vision
Error made by all three service providers in the table mentioned below.

Reference: CAZTON
Summary: Out of all the services, Microsoft Azure Vision performed the best for English language, while Google Vision performed the best for French language. Amazon Textract is clearly a distant third.
More Comparison for solving the choosing dilemma

Market share of major service providers

Conclusion:
AWS leads the pack of cloud services and especially in image processing as it enjoys the being released early and set up its depth in the market. But as new technologies and algorithm are evolving market share is distributing to other cloud service provider like Azure and Google and many other entering the domain.
Though all the three ie. Google, Microsoft and Amazon provide the most common services through Image Analysis API, these leading providers can be compared from their features, speed, accuracy, image size limits, performance, pricing, use cases, advantages and disadvantages.
| Amazon | Microsoft | ||
|---|---|---|---|
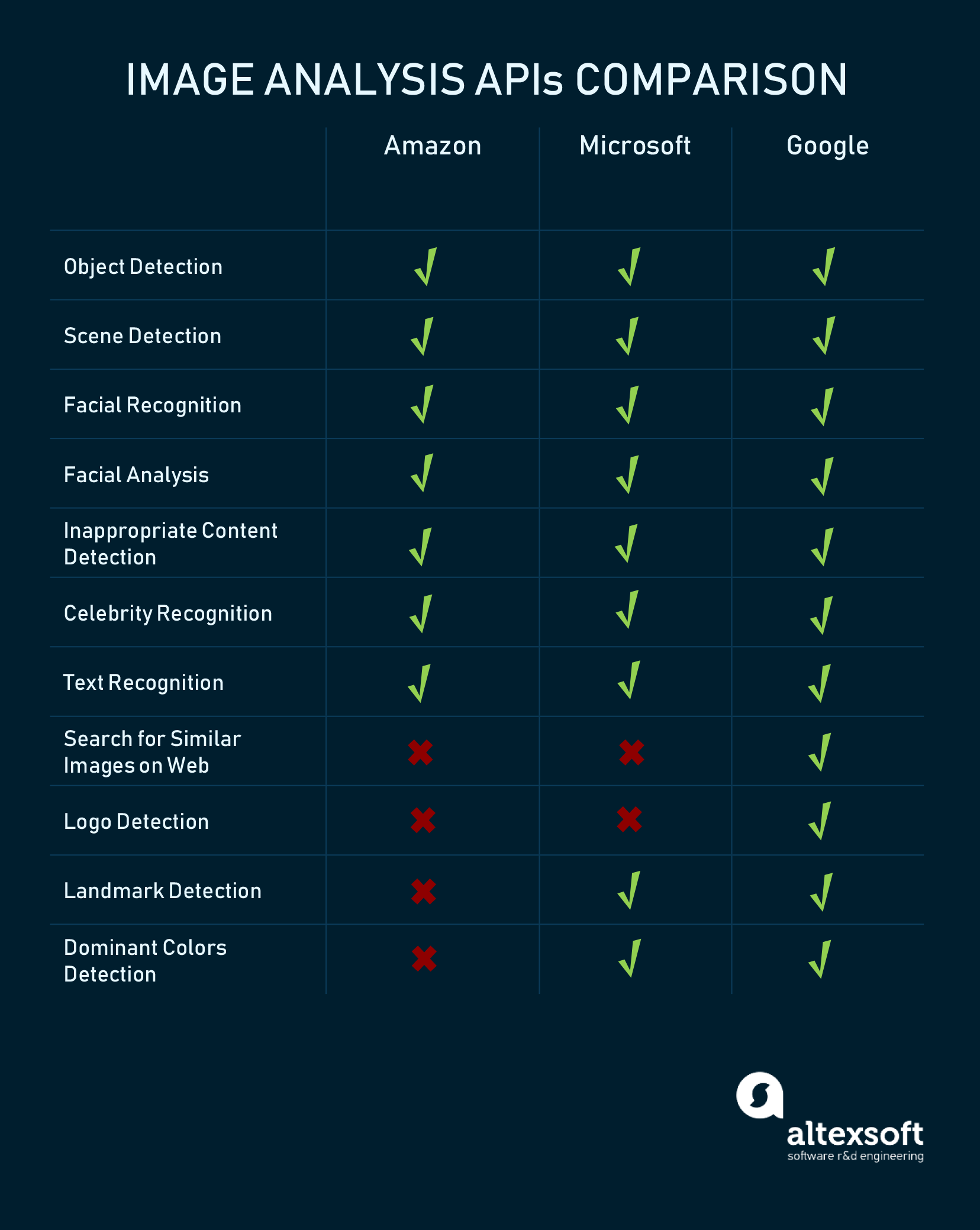
| Services/Features Provided | 1. Object Detection 2. Scene Detection 3. Facial Recognition 4. Facial Aanalysis 5. Incorporate Content Detection 6. Celebrity Recognition 7. Text Recognition |
1. Object Detection 2. Scene Detection 3. Facial Recognition 4. Facial Aanalysis 5. Incorporate Content Detection 6. Celebrity Recognition 7. Text Recognition 8. Landmark Detection 9. Dominant Colours Detection |
1. Object Detection 2. Scene Detection 3. Facial Recognition 4. Facial Aanalysis 5. Incorporate Content Detection 6. Celebrity Recognition 7. Text Recognition 8. Landmark Detection 9. Dominant Colours Detection 10. Search for Similar Images on web 11. Landmark Detection |
| Image Size Limits | 5Mb / Image, 15Mb / Image from S3 | 20 MB / Image | 4 MB / Image |
| Pricing | Amazon Pricing | Microsoft Pricing | Google Pricing |
| Advantages | 1. It’s fast and easy to use 2. Capable of analyzing 5,000 images per month 3. Store up to 1,000 face metadata per month 4. Easily integrate with AWS |
1. Provides Flexible deployment- Run Computer Vision in the cloud or on the edge, in containers 2. The options of either uploading the image or passing a URL are both available 3. Response times are very good 4. Integrated with Microsoft Azure, blog Storage, SQL database and Virtual machine so can be used as an end to end solution 5. No termination fees. Pay only for what you use |
1. Capturing huge data sets 2. Large scale data processing 3. Tackling generic domains 4. It is a pay as you go service with no termination fees 5. Provides highest security, privacy and compliance controlnd provides ISO and SOC certification for the products 6. Can detect any image using Google Image Search 7. Multiple filter parameters can be applied to a single image |
| Use Cases | 1. Use Label detection across multiple images 2. Face detection and comparison 3. Image moderation 4. Correcting images for uploading right orientation 5. Statistical monitoring like how many faces are tracked or how many requests are sent per second |
1. Identification, categorization, and tagging images 2. Identifying faces, mood, age, and scene 3. Optical Character Recognition (OCR) helpful in maintaining general, banking, medical records,etc 4. Intelligent manipulation of photos and restriction to show moderated content |
1. Face Detection detects multiple faces within an image along with the associated key facial attributes such as emotional state or wearing goggle 2. Detects product logos within image 3. Optical Character Recognition (OCR) with support for wide range of languages 4. Automatic identification of language 5. Landmark Detection |
| Disadvantages | 1. The maximum image size that can be stored as an Amazon S3 object is limited to 15 MB 2. The minimum pixel resolution for height and width is 80 pixels 3. It supports only JPEG and PNG image formats 4. Restriction on face dimension while face detection (no smaller than 40×40 pixels in an image with 1920X1080 pixels) |
1. If no. of transactions per second are crossed then response time will be throttled 2. Usage-based pricing model can be expensive |
1. Cloud Datastore is feature-limited and hard to switch out from 2. Google CDN does not work with custom sources 3. Doesn't support Face Recognition |
What is an API?
An application programming interface (API) is a computing interface that defines interactions between multiple software intermediaries. It defines the kinds of calls or requests that can be made, how to make them, the data formats that should be used, the conventions to follow, etc. It can also provide extension mechanisms so that users can extend existing functionality in various ways and to varying degrees.
Purpose
building applications, an API (application programming interface) simplifies programming by abstracting the underlying implementation and only exposing objects or actions the developer needs. While a graphical interface for an email client might provide a user with a button that performs all the steps for fetching and highlighting new emails, an API for file input/output might give the developer a function that copies a file from one location to another without requiring that the developer understand the file system operations occurring behind the scenes .
APIs for Speech and Text Processing
AWS
Amazon has a wide range of offerings in its machine learning as a service APIs for common tasks in speech and text analysis. The Amazon Lex API can recognize written and spoken text through its natural language processing (NLP) and automatic speech recognition (ASR) capabilities.
Microsoft Azure
Microsoft also has high-level APIs and Cognitive Services, which integrate effectively with any infrastructure. The speech translation APIs include four APIs with different natural language processing techniques for speech recognition. The four APIs are Translator Speech API, Bing Speech API, Speaker Recognition API, and Custom Speech Service.
Google Cloud
There are many similarities between the functionalities of Google Cloud Machine Learning APIs and those of Amazon and Microsoft Azure. Furthermore, Google ML APIs offer an alternative for training custom models. The prominent APIs in Google Cloud’s MLaaS portfolio includes Dialogflow, Cloud Speech API, AutoML translation API, Cloud Translation API, Cloud natural language API, and AutoML Natural Language API.
The thought of implementing machine learning sounds unattainable for the majority of businesses. Thanks to companies like Google, Amazon, and Microsoft, it is now possible to get Machine Learning as a service (MLaaS).
Machine Learning as a Service:
It refers to the different cloud-based platforms which handle most infrastructural issues related to machine learning. These include model training, model evaluation, and data pre-processing among other things.
The leading providers of MLaaS include Microsoft Azure Machine Learning, Amazon Machine Learning services, and Google Cloud AI. All of these services facilitate fast training of models as well as deployment.
Amazon and Microsoft are clearly the top dogs in enterprise adoption of cloud services such as MLaaS while Google still lags behind.
Amazon Web Services(AWS):
Amazon Web Services offers two main services for businesses.
- Predictive Analytics:
AWS predictive analytics is the tool with the highest level of automation. It is capable of loading data from a number of sources including CSV files, Amazon Redshift, and Amazon RDS among others.
The service performs all pre-processing automatically, identifying numerical and categorical fields. In all of these processes, it does not give the user an opportunity to select the methods they would like to use for further pre-processing if necessary.
This tool limits prediction capacities to three main alternatives:
-
Regression
-
Binary classification
-
Multiclass classification
The main benefit of this tool is the fact that it does not require users to know any machine learning as everything is automated. But it does not offer support for any unsupervised learning approaches. All in all, it is a great solution if you are looking for a fully automated service and do not mind the limitations.
- SageMakerTool:
A service that aims to provide data scientists with the tools they need to build models and deploy them fast. For example, it includes built-in algorithms optimized for computations in distributed frameworks and large datasets. It also allows data scientists to simplify data analysis and exploration without the hassle of server management.
Data scientists can use the APIs that the company provides or get a little more creative and use their own data sets.
Microsoft Azure:
Azure has the ultimate objective of creating the ideal framework for both experienced data scientists and newcomers in the field. Azure offers greater flexibility when it comes to ready-to-use algorithms.
- Azure Machine Learning Studio:
It requires users with basic knowledge of how Machine Learning works. It offers a visual peek into every step of the workflow for the new users. It also offers support for over 100 algorithms that handle:
-
Clustering
-
Binary and Multi-class Classification
-
Text analysis
-
Anomaly detection
-
Recommendation
-
Regression
Another major merit is the Cortana Intelligence Gallery, a collection of machine learning tools that the Microsoft community provides for exploration and reuse.
- Microsoft Azure Machine Learning Service
This tool is designed for experienced data scientists. It does not have built-in out-of-box solutions but rather, requires custom engineering. The tool incorporates Python packages with libraries and functions for various tasks and visual studio tools for AI among other things.
Google Cloud AI:
-
Google Cloud AutoML
It will be useful for inexperienced users looking to deploy machine learning models. However, it is yet to launch. -
Google Cloud Machine Learning Engine
This is one of the most flexible platforms for data scientists. It recommends the use of TensorFlow and Google Cloud infrastructure as its drivers. TensorFlow is a Google product that is essentially an open-source library of various machine learning tools. It has a rather steep learning curve and no visual interface. Its main targets are software engineers who are looking to transition into data science. The service claims to offer user-friendly approaches for building machine learning models for any type and volume of data. Furthermore, the service is integrated with all Google services and has a focus on deep neural networks.
5 Factors Businesses Consider Before Choosing an ML Service:
- Services and Features:
The top priority for any company is to find a suite of features and services that address its wants and needs. In some cases, achieving this requires that an organization makes use of several providers, each targeting a different aspect of operations.
In the case of Amazon, Microsoft, and Google, the capabilities are by and large similar, with flexibility in computing, storage, and networking requirements.
-
Agility:
the most important factor to look for in this highly dynamic field is a service provider who is flexible in terms of change and innovation. -
Technical Capabilities:
For service to yield any amount of benefits, a company should be in a position to implement it smoothly and efficiently. For example, if a business has a team of data scientists or resources, then it won't be a problem. But in case the business has to find a way to implement a simple solution without extra manpower, consider the automated solutions offered by the different providers. -
Pricing:
Pricing is a huge factor to consider when seeking an MLaaS solution. For all the three top competing providers, high competition has created a sustained downward trend. Though their prices are not very different, each one offers a different pricing model, discount framework, and periodic price cuts. -
Functionality:
Successful implementation of machine learning usually requires proper identification of the problem at hand and how the technology can solve it. By the time a company gets to the point of selecting vendors, they need to know exactly what problems they are looking to solve and the benefits they expect.
Future for MLaaS:
With MLaaS, businesses can reap the benefits of technology without undertaking the rigorous process of building their own models from scratch. They no longer have to worry so much about in-house capability or having data science and engineering degrees. Rather, the main focus is on getting the solution that best integrates into their existing framework and delivers the most value.
Introduction to Multitenancy¶
The goal of multitenancy is to maximize resource sharing by allowing multiple users (tenants) to log in and use a single server/cluster at the same time, in a tenant-isolated manner. That is, each user is given the experience of using his/her own server, rather than a shared environment. Multitenancy ensures optimal performance of the system's resources such as memory and hardware and also secures each tenant's personal data.
You can register tenant domains using the Management Console of WSO2 products.
- Info
When multitenancy is enabled and a tenant becomes inactive for a long period of time, the tenant is unloaded from the server's memory. By default, the time period is 30 minutes. After that, the tenant has to log in again before sending requests to the server.
You change the default time period allowed for tenant inactiveness by adding -Dtenant.idle.time=<time_in_minutes> java property to the product's startup script ( ./wso2server.sh file for Linux and wso2server.bat for Windows) as shown below:
JAVA_OPTS
-Dtenant.idle.time=30 \
• Architecture
• Resource sharing
• Tenant loading policy
• Restrictions
• Request dispatching
• Scaling
NOTE :- A tenant is property or product within an organization. Each tenant can have several applications deployed to multiple environments and regions. The response format is JSON. The current API version is 2.
Parameters: None
- Architecture¶
The multi-tenant architecture of WSO2 products allows you to deploy Web applications, Web services, ESB mediators, mashups etc. in an environment that supports the following:
• Tenant isolation: Each tenant has its own domain, which the other tenants cannot access.
• Data isolation: Each tenant can manage its data securely in an isolated manner.
• Execution isolation: Each tenant can carry out business processes and workflows independent of the other tenants. No action of a tenant is triggered or inhibited by another tenant.
• Performance Isolation: No tenant has an impact on the performance of another tenant.
A tenant is an isolated domain. The users within this domain can manage their own data and perform their own transactions without being affected by actions carried out in other domains.
These domains are allocated server space from the complete server space of a WSO2 product instance which is referred to as the super tenant.
The super tenant as well as each individual tenant has its own configuration and context module.
Each tenant has its own security domain. A domain has a set of users, and permissions for those users to access resources. Thus, a tenant is restricted by the users and permissions of the domain assigned to it. The artifact repositories of the tenants are separated from each other.
An individual tenant can carry out the following activities within the boundaries of its own configuration and context module:
• Deploying artifacts
• Applying security
• User management
• Data management
• Request throttling
• Response caching
WSO2 Carbon provides a number of Admin services which have special privileges to manage the server. These admin services are deployed in the super tenant. Other tenants can make use of these admin services to manage their deployment. The admin services operate in a tenant aware fashion. Thus, privileges and restrictions that apply to any client using an admin service are taken into account.
- Resource sharing¶
WSO2 Carbon supports the following methods for sharing resources among tenants:
• Private Jet mode : This method allows the load of a tenant ID to be deployed in a single tenant mode. A single tenant is allocated an entire service cluster. The purpose of this approach is to allow special privileges (such as priority processing and improved performance) to a tenant.
• Separation at hardware level : This method allows different tenants to share a common set of resources, but each tenant has to run its own operating system. This approach helps to achieve a high level of isolation, but it also incurs a high overhead cost.
• Separation at JVM level : This method allows tenants to share the same operating system. This is done by enabling each tenant to run a separate JVM instance in the operating system.
• Native multitenancy : This method involves allowing all the tenants to share a single JVM instance. This method minimises the overhead cost.
3.Tenant loading policy¶
Lazy loading is a design pattern used specifically in cloud deployments to prolong the initialization of an object or artifact until it is requested by a tenant or an internal process. In WSO2 products based on Carbon 4.4.0 or later versions, you have the option of setting the required tenant loading policy by enabling either Lazy Loading or Eager Loading of tenants. Additionally, you can separately control the loading policy for web applications and axis2 services deployed in your tenants using the GhostDeployment setting.
See Configuring the Tenant Loading Policy for more information.
Restrictions¶
The following restrictions are imposed to ensure that each individual tenant has the required level of isolation and maintains fine-grained security control over its own services without affecting the other tenants.
• Only the super tenant can modify its own configuration. In addition, it can add, view and delete tenants.
• When a tenant logs into the system, it can only access artifacts deployed under its own configuration. One tenant cannot manipulate the code of another tenant.
• The super admin or tenant admin can add user stores to their own domain. Dynamic configurations are possible only for secondary user stores and the primary user store is not configurable at run time. This is because primary user stores are available for all tenants and allowing changes to the configuration at run time can lead to instability of the system. Therefore, the primary user store is treated as a static property in the implementation and it should be configured prior to run time.
• A tenants code cannot invoke sensitive server side functionality. This is achieved via Java security.
• Tenants share the transports provided by the system. They are not allowed to create their own transports.
- Request dispatching¶
This section describes how the multi tenancy architecture described above works in a request dispatching scenario.
When a Carbon server receives a request, the message is first received by the handlers and dispatchers defined for the server configuration (i.e. super tenant). The server configuration may include handlers that implement cross tenant policies and Service Level Agreement (SLA) management. For example, a priority based dispatcher can be applied at this stage to offer differentiated qualities of service to different clients. Once the relevant handlers and dispatchers are applied, the request is sent to the tenant to which it is addressed. Then the message dispatchers and handlers specific to that tenant will be applied.
The following example further illustrates how message dispatching is carried out in a multi tenant server.
For example, two tenants named foo.com and bar.com may deploy a service named MyService. When this service is hosted on the two tenants, they would have the following URLs. http://example.com/t/foo.com/services/MyService , http://example.com/t/bar.com/services/MyService
The name of the tenant in the URL allows the tenant to be identified when the Carbon server receives a message which is addressed to a specific client. Alternatively, you may configure a CNAME record in DNS (Domain Name System) as an alias for this information.
If a request is addressed to the MyService service hosted by foo.com , the message handlers and dispatchers of the super tenant will be applied and the tenant foo.com will be identified by the tenant name in the URL. Then the request will be sent to foo.com where it will be processed.
5.Scaling¶
The multi tenancy architecture described above mainly refers to a scenario where a single instance of a Carbon server acts as a single multi tenant node. In a situation where a very high load of requests are handled, you may need multiple multi tenant nodes. In order to operate with multiple multi tenant nodes, you need load balancing. The load balancer you use also needs to be tenant-aware.
What is Multitenancy?
Multitenancy is a reference to the mode of operation of software where multiple independent instances of one or multiple applications operate in a shared environment. The instances (tenants) are logically isolated, but physically integrated.
Multi-tenant architecture, commonly referred to as multitenancy, is a software architecture in which multiple single instances of software run on a single physical server. The server then serves multiple tenants.
“Tenants” is a term for a group of users or software applications that all share access to the hardware through the underlying software. Multiple tenants on a server all share the memory, which is dynamically allocated and cleaned up as needed. They also share access to system resources, such as the network controller.
Architecture
The multitenant architecture of WSO2 API Manager allows you to deploy Web applications, Web services, ESB mediators, mashups etc. in an environment that supports the following:
Tenant isolation: Each tenant has its own domain, which the other tenants cannot access.
Data isolation: Each tenant can manage its data securely in an isolated manner.
Execution isolation: Each tenant can carry out business processes and workflows independent of the other tenants. No action of a tenant is triggered or inhibited by another tenant.
Performance Isolation: No tenant has an impact on the performance of another tenant.
A tenant is an isolated domain. The users within this domain can manage their own data and perform their own transactions without being affected by actions carried out in other domains.
Each tenant has its own security domain. A domain has a set of users, and permissions for those users to access resources. Thus, a tenant is restricted by the users and permissions of the domain assigned to it. The artifact repositories of the tenants are separated from each other.
An individual tenant can carry out the following activities within the boundaries of its own configuration and context module:
- Deploying artifacts
- Applying security
- User management
- Data management
- Request throttling
- Response caching
WSO2 API Manager provides a number of Admin services which have special privileges to manage the server. These admin services are deployed in the super tenant. Other tenants can make use of these admin services to manage their deployment. The admin services operate in a tenant aware fashion. Thus, privileges and restrictions that apply to any client using an admin service are taken into account.
Resource sharing
WSO2 API Manager supports the following methods for sharing resources among tenants:
- Private Jet mode: This method allows the load of a tenant ID to be deployed in a single tenant mode. A single tenant is allocated an entire service cluster. The purpose of this approach is to allow special privileges (such as priority processing and improved performance) to a tenant.
- Separation at hardware level: This method allows different tenants to share a common set of resources, but each tenant has to run its own operating system. This approach helps to achieve a high level of isolation, but it also incurs a high overhead cost.
- Separation at JVM level: This method allows tenants to share the same operating system. This is done by enabling each tenant to run a separate JVM instance in the operating system.
- Native multitenancy: This method involves allowing all the tenants to share a single JVM instance. This method minimises the overhead cost.
Tenant loading policy
Lazy loading is a design pattern used specifically in cloud deployments to prolong the initialization of an object or artifact until it is requested by a tenant or an internal process. In WSO2 API Manager, you have the option of setting the required tenant loading policy by enabling either Lazy Loading or Eager Loading of tenants. Additionally, you can separately control the loading policy for web applications and axis2 services deployed in your tenants using the GhostDeployment setting.
Restrictions
The following restrictions are imposed to ensure that each individual tenant has the required level of isolation and maintains fine-grained security control over its own services without affecting the other tenants.
Only the super tenant can modify its own configuration. In addition, it can add, view and delete tenants.
When a tenant logs into the system, it can only access artifacts deployed under its own configuration. One tenant cannot manipulate the code of another tenant.
The super admin or tenant admin can add user stores to their own domain. Dynamic configurations are possible only for secondary user stores and the primary user store is not configurable at run time. This is because primary user stores are available for all tenants and allowing changes to the configuration at run time can lead to instability of the system. Therefore, the primary user store is treated as a static property in the implementation and it should be configured prior to run time.
A tenants code cannot invoke sensitive server side functionality. This is achieved via Java security.
Tenants share the transports provided by the system. They are not allowed to create their own transports.
Request dispatching
This section describes how the multitenancy architecture described above works in a request dispatching scenario.
When a WSO2 API Manager server receives a request, the message is first received by the handlers and dispatchers defined for the server configuration (i.e. super tenant). The server configuration may include handlers that implement cross tenant policies and Service Level Agreement (SLA) management. For example, a priority based dispatcher can be applied at this stage to offer differentiated qualities of service to different clients. Once the relevant handlers and dispatchers are applied, the request is sent to the tenant to which it is addressed. Then the message dispatchers and handlers specific to that tenant will be applied.
Scaling
The multitenancy architecture described above mainly refers to a scenario where a single instance of a WSO2 API Manager server acts as a single multitenant node. In a situation where a very high load of requests are handled, you may need multiple multitenant nodes. In order to operate with multiple multitenant nodes, you need load balancing. The load balancer you use also needs to be tenant-aware.
What is MULTITENANCY Architecture?
The term "software multitenancy" refers to a software architecture in which a single instance of software runs on a server and serves multiple tenants. Systems designed in such manner are often called shared (in contrast to dedicated or isolated). A tenant is a group of users who share a common access with specific privileges to the software instance. With a multitenant architecture, a software application is designed to provide every tenant a dedicated share of the instance - including its data, configuration, user management, tenant individual functionality and non-functional properties. Multitenancy contrasts with multi-instance architectures, where separate software instances operate on behalf of different tenants.
Why Multitenancy?
• Cost savings
Multitenancy allows for cost savings over and above the basic economies of scale achievable from consolidating IT resources into a single operation.
• Data aggregation/data mining
One of the most compelling reasons for vendors/ISVs to utilize multitenancy is for the inherent data aggregation benefits. Instead of collecting data from multiple data sources, with potentially different database schemas, all data for all customers is stored in a single database schema.
• Complexity
Because of the additional customization complexity and the need to maintain per-tenant metadata, multitenant applications require a larger development effort. Considerations such as vector-based data sequencing, encryptable algorithm infrastructure, and virtualized control interfaces, must be considered.
• Release management
Multitenancy simplifies the release management process. In a traditional release management process, packages containing code and database changes are distributed to client desktop and/or server machines; in the single-instance case, this would be one server machine per customer. These packages then must be installed on each individual machine. With the multitenant model, the package typically only needs to be installed on a single server. This greatly simplifies the release management process, and the scale is no longer dependent on the number of customers.
Multitenant Applications in Azure
A multitenant application is a shared resource that allows "users in separate tenants" to view the application as though it was their own. A typical scenario that lends itself to a multitenant application is one in which all users of the application from different tenants may wish to customize the user experience but otherwise have the same basic business requirements. Examples of large multitenant applications are Microsoft 365, Outlook.com, and visualstudio.com.
From an application provider's perspective, the benefits of multitenancy mostly relate to operational and cost efficiencies. One version of your application can meet the needs of many tenants/customers, allowing consolidation of system administration tasks such as monitoring, performance tuning, software maintenance, and data backups.
The following provides a list of the most significant goals and requirements from a provider's perspective.
• Provisioning: You must be able to provision new tenants for the application. For multitenant applications with many tenants, it is usually necessary to automate this process by enabling self-service provisioning.
• Maintainability: You must be able to upgrade the application and perform other maintenance tasks while multiple tenants are using it.
• Monitoring: You must always be able to monitor the application to identify any problems and to troubleshoot them. This includes monitoring how each tenant is using the application.
A properly implemented multitenant application provides the following benefits to users.
• Isolation: The activities of individual tenants do not affect the use of the application by other tenants. Tenants cannot access each other's data. It appears to the tenant as though they have exclusive use of the application.
• Availability: Individual tenants want the application to be constantly available, perhaps with guarantees defined in an SLA. Again, the activities of other tenants should not affect the availability of the application.
• Scalability: The application scales to meet the demand of individual tenants. The presence and actions of other tenants should not affect the performance of the application.
• Costs: Costs are lower than running a dedicated, single-tenant application because multi-tenancy enables the sharing of resources.
• Customizability: The ability to customize the application for an individual tenant in various ways such as adding or removing features, changing colors and logos, or even adding their own code or script.
API management with multi-tenancy
WSO2 API Manager allows users to control API visibility and subscription availability. API visibility can be one of the following options:
• Public: The API is accessible to everyone and can be advertised in multiple stores - a central store and/or non-WSO2 stores.
• Restricted by roles: The API is visible only to specific user roles in the tenant store that you specify.
Subscription availability has three options. Those options are as follows:
• Available to current Tenant Only: Only users in the current organization/tenant domain can subscribe to the API
• Available to All the Tenants: Users of all organizations’ tenant domains can subscribe to the API
• Available to Specific Tenants: Users of the organizations/tenant domains you specify as well as the current tenant domain can subscribe to the API
What is Multitenancy? | Multitenant Architecture
Multitenancy
What is Multitenancy?
In cloud computing, multitenancy means that multiple customers of a cloud vendor are using the same computing resources. Despite the fact that they share resources, cloud customers aren't aware of each other, and their data is kept totally separate. Multitenant architecture is a feature in many types of public cloud computing, including IaaS, PaaS, SaaS, containers, and serverless computing.
To understand multitenancy, think of how banking works. Multiple people can store their money in one bank, and their assets are completely separate even though they're stored in the same place. Customers of the bank don't interact with each other, don't have access to other customers' money, and aren't even aware of each other. Similarly, in public cloud computing, customers of the cloud vendor use the same infrastructure – the same servers, typically – while still keeping their data and their business logic separate and secure.
The classic definition of multitenancy was a single software instance that served multiple users, or tenants i.e. A multi-tenancy is a software architecture that implies centralized administration. It means that a single instance of an application serves many customers (called also tenants) and each one has access to shared resources (Code, storage, and networking).
However, in modern cloud computing, the term has taken on a broader meaning, referring to shared cloud infrastructure instead of just a shared software instance.
What are the benefits of multitenancy?
Many of the benefits of cloud computing are only possible because of multitenancy. Here are two crucial ways multitenancy improves cloud computing:
-
Better use of resources: One machine reserved for one tenant isn't efficient, as that one tenant is not likely to use all of the machine's computing power. By sharing machines among multiple tenants, the use of available resources is maximized.
-
Lower costs: With multiple customers sharing resources, a cloud vendor can offer their services to many customers at a much lower cost than if each customer required their own dedicated infrastructure.
What are the drawbacks of multitenancy?
-
Possible security risks and compliance issues: Some companies may not be able to store data within shared infrastructure, no matter how secure, due to regulatory requirements. Additionally, security problems or corrupted data from one tenant could spread to other tenants on the same machine, although this is extremely rare and shouldn't occur if the cloud vendor has configured their infrastructure correctly. These security risks are somewhat mitigated by the fact that cloud vendors typically are able to invest more in their security than individual businesses can.
-
The "noisy neighbor" effect: If one tenant is using an inordinate amount of computing power, this could slow down performance for the other tenants. Again, this should not occur if the cloud vendor has set up its infrastructure correctly.
Multitenant Architecture
Multitenant architecture is an ecosystem or model, in which a single environment can serve multiple tenants utilizing a scalable, available, and resilient architecture. The underlying infrastructure is completely shared, logically isolated, and with fully centralized services. The multitenant architecture evolves according to the organization or subdomain and is totally transparent to the end-user.
Let’s take a look at the architecture first. The example below is designed based on N-tire architecture and has the following layers:
- Presentation layer or Web API
- Service layer or Application layer that will accommodate all the business logic and workflow
- Management layer- Provisioning, Metering, Billing, Configuration, Subscription, and Security
- Data access layer that is implemented using Shared data, UnitOfWork and Repository patterns.
- Infrastructure layer- Hardware and OS shared by all the tenants.
Further reading -
As an example, we will see the highlight to build Multi-tenant Web API using dot net core:
Note:
Source: Detail explanation of implementation can be viewed here.
The key component of tenant separation is ContextFactory that contains logic to get the tenant id from the HTTP header, retrieve a tenant database name using DataBaseManager and replace a database name in the connection string. As a result, a database context (Entity Framework context) is created.
The diagram below demonstrates this architecture.
Implementation
- Create ContextFactory --
ContextFactory is a key component of the whole architecture. It constructs Entity Framework context-specific to a tenant database. - Add the database manager --
Database manager orchestrates all tenants metadata such as tenant database name, the activation status of tenants (activated/deactivated), and a bunch of other properties. - Add Unit of Work class --
UnitOfWork solves two tasks. It commits all changes made by Entity Framework in entities and disposes of a specific context. - Add Generic Repository class --
The repository will make changes in EF entities and the Unit of Work will commit changes to tenants database. - Add the tenant header operation filter --
TenantHeaderOperationFilter class will add tenant id field to all API calls (as HTTP header). And you are done!
Multi-Tenancy:
It is an architecture in which a single instance of a software application serves multiple customers. Each customer is called a tenant. Tenants may be given the ability to customize some parts of the application, such as the color of the user interface (UI) or business rules, but they cannot customize the application's code.
In a multi-tenant architecture, multiple instances of an application operate in a shared environment. This architecture is able to work because each tenant is integrated physically, but logically separated; meaning that a single instance of the software will run on one server and then serve multiple tenants. In this way, a software application in a multi-tenant architecture can share a dedicated instance of configurations, data, user management, and other properties.
Multi-tenancy applications can share the same users, displays, rules -- although users can customize these to an extent -- and database schemas, which tenants can also customize.
Importance of multi-tenancy
Multi-tenancy has seen a lot of could adoption and is used most with cloud computing. Multi-tenant architectures are found in both public cloud and private cloud environments, allowing each tenant's data to be separated from each other. For example, in a multi-tenant public cloud, the same servers will be used in a hosted environment to host multiple users. Each user is given a separate and ideally secure space within those servers to store data.
Multi-tenancy is also important for the scalability of public and private clouds and has helped make multi-tenancy a standard. The multi-tenant architecture can also aid in providing a better ROI for organizations, as well as quickening the pace of maintenance and updates for tenants.
Types of multi-tenant architecture
There are three main multi-tenancy model types, all with varying levels of complexity and costs. A single, shared database schema is a multi-tenancy model with a multi-tenant database. This is the simplest form out of the three and is a relatively low cost for tenants because of the use of shared resources. This form uses a single application and database instance to host tenants and store data. Using a single, shared database schema allows for easier scaling; however, operational costs can be higher.
Another multi-tenant architecture includes the use of a single database with multiple schemas. This tenant system uses a single application instance with individual databases for each tenant. In addition, this architecture has a higher cost with more overhead with each database. It is a valuable architecture when data from different tenants need to be treated differently -- such as if they had to go through different geographic regulations.
The third type of multi-tenant architecture hosts data in multiple databases. This model is relatively complex in terms of management and maintenance, but tenants can be separated by a chosen criterion.
Multi-tenant vs. single-tenant
Multi-tenancy can be contrasted with single-tenancy, an architecture in which each customer has their own software instance and may be given access to source code. In single-tenant architectures, a tenant will have a singular instance of a SaaS application dedicated to them, unlike multi-tenancy where there are shared services. Because each tenant is in a separate environment, they are not bound in the same way that users of shared infrastructure would be; meaning single-tenant architectures are much more customizable.
Multi-tenancy is the more used option of the two, as most SaaS services operate on multi-tenancy. In comparison to single-tenancy, multi-tenancy is cheaper, has more efficient resource usage, fewer maintenance costs as well as a potential for larger computing capacity. With a multi-tenant architecture, the provider only has to make updates once. With a single-tenant architecture, the provider must touch multiple instances of the software in order to make updates.
A potential customer would likely choose a single-tenant infrastructure over multi-tenancy for the ability to have more control and flexibility in their environment -- typically to address specific requirements.
Multi-tenancy- Software multitenancy refers to one instance of software architecture running on one server and then serving multiple customers or tenants. Despite the fact that the customers share resources, they are not aware of each other, each customer's data is kept separate and no customer has access to the data of others.
In a multi-tenant architecture, multiple instances of an application operate in a shared environment. This architecture is able to work because each tenant is integrated physically, but logically separated. In this way, a software application in a multi-tenant architecture can share a dedicated instance of configurations, data, user management, and other properties.
Benefits of Multi-tenancy-
- Efficient use of resources- If one machine is reserved for one tenant then the tenant might not use all of the machine's computing power. So, the use of available resources can be maximized by sharing machines among multiple tenants.
- Low cost- If multiple customers share resources, a cloud vendor can offer their services to many customers at a much lower cost than if each customer required their own dedicated infrastructure.
- The architecture is easily scalable.
- Decreases infrastructure operating costs.
Drawbacks of Multi-tenancy-
- Security risks and compliance issues- Some companies may not be able to store data within shared infrastructure despite high security. Additionally, security problems or corrupted data from one tenant could spread to other tenants on the same machine.
- The "noisy neighbor" effect- If one tenant is using a high amount of computing power on the same processor, this could slow down performance for the other tenants.
- Multi-tenant apps need stricter authentication and access controls for security.
There are multiple well-known strategies to implement this architecture. Multi-tenancy can be implemented using any of the following approaches:
- Database per Tenant- Each Tenant has its own database and is isolated from other tenants.
- Shared Database, Shared Schema- All Tenants share a database and tables. Every table has a Column with the Tenant Identifier, that shows the owner of the row.
- Shared Database, Separate Schema- All Tenants share a database but have their own database schemas and tables.
Steps for implementing multi-tenant communication generally involves the following three steps-
- Accept the incoming connection, and authenticate the user if necessary.
- Intercept the request and identify the tenant for which the user is issuing the request.
- Establish a connection with the database or schema of the tenant.
Multi-tenancy is an architecture in which a single instance of a software application serves multiple customers. Each customer is called a tenant. Tenants may be given the ability to customize some parts of the application, such as the color of the user interface or business rules, but they cannot customize the application's code.
In a multi-tenant architecture, multiple instances of an application operate in a shared environment. This is able to work because each tenant is integrated physically, but logically separated; meaning that a single instance of the software will run on one server and then serve multiple tenants. In this way, a software application in a multi-tenant architecture can share a dedicated instance of configurations, data, user management and other properties.
When it comes to multi-tenancy the only variant is the tenant Id. Since its a stateless system, the system needs to know tenant information in order to process the request and get the corresponding resources. For example, each tenant’s data either get saved in different tenant database or separated with tenant id as a namespace. The only option for the backend to access the tenant-specific is to send the tenant identifier part of every API.
A URL contains scheme/protocol and a domain. Every URL get differentiated from others by changing the path or query param.
The methods in which a tenant can get identified as part of REST API are
- Query parameter based tenant identification
- URL path based tenant identification
- Domain-based tenant identification
- Custom Http header-based tenant identification
Multi-tenancy concepts
There are already several multi-tenancy architecture design patterns available. Our concept can be used to apply any of these. But let us briefly look into three common patterns. To satisfy the requirements mentioned above, the data of the tenants must be separated. Three typical ways of data separation for databases are:
• Shared-nothing, i.e. a separate database instance for each tenant.
• Schema-separation, i.e. a separate database schema for each tenant.
• Shared-everything (aka row-based separation), i.e. using the same database tables for all tenants with a tenant separator
column.
When designing a multi-tenant SaaS application, you must carefully choose the tenancy model that best fits the needs of your application. A tenancy model determines how each tenant's data is mapped to storage. Your choice of tenancy model impacts application design and management.
-
SaaS concepts and terminology
In the Software as a Service (SaaS) model, your company does not sell licenses to your software. Instead, each customer makes rent payments to your company, making each customer a tenant of your company.
The term tenancy model refers to how tenants' stored data is organized:
• Single-tenancy: Each database stores data from only one tenant.
• Multi-tenancy: Each database stores data from multiple separate tenants (with mechanisms to protect data privacy).
• Hybrid tenancy models are also available -
How to choose the appropriate tenancy model
• Scalability:
- Number of tenants.
- Storage per-tenant.
- Storage in aggregate.
- Workload.
• Tenant isolation:
- Data isolation and performance (whether one tenant's workload impacts others).
• Per-tenant cost:
- Database costs.
• Development complexity:
- Changes to schema.
- Changes to queries (required by the pattern).
• Operational complexity:
- Monitoring and managing performance.
- Schema management.
- Restoring a tenant.
- Disaster recovery.
• Customizability:
- Ease of supporting schema customizations that are either tenant-specific or tenant class-specific.
- Standalone single-tenant app with single-tenant database
Application level isolation

the whole application is installed repeatedly, once for each tenant. Each instance of the app is a standalone instance, so it never interacts with any other standalone instance. Each instance of the app has only one tenant, and therefore needs only one database. The tenant has the database all to itself.
-
Multi-tenant app with database-per-tenant
A new database is provisioned for each new tenant. The application tier is scaled up vertically by adding more resources per node. Or the app is scaled out horizontally by adding more nodes. The scaling is based on workload, and is independent of the number or scale of the individual databases.

Other management features that scale well include the following:
• Built-in backups.
• High availability.
• On-disk encryption.
• Performance telemetry. -
Multi-tenant app with multi-tenant databases
Another available pattern is to store many tenants in a multi-tenant database. The application instance can have any number of multi-tenant databases. The schema of a multi-tenant database must have one or more tenant identifier columns so that the data from any given tenant can be selectively retrieved.
-
Multi-tenant app with a single multi-tenant database
The simplest multi-tenant database pattern uses a single database to host data for all tenants. As more tenants are added, the database is scaled up with more storage and compute resources. This scale up might be all that is needed, although there is always an ultimate scale limit. However, long before that limit is reached the database becomes unwieldy to manage. -
Multi-tenant app with sharded multi-tenant databases

Most SaaS applications access the data of only one tenant at a time. This access pattern allows tenant data to be distributed across multiple databases or shards, where all the data for any one tenant is contained in one shard. Combined with a multi-tenant database pattern, a sharded model allows almost limitless scale.

Example of an Architechture of Multitenancy at a Bank Application:

Multi-tenancy @ AWS
For explaining the concept consider a simple service that returns a list of pets in a pet store. The data is stored in a DynamoDB table. The website is hosted using S3’s static website hosting. Your architecture looks typically like the following:

The updated Architecture is shown below.

Multi-tenancy @ Google
- In the Google Cloud Console, on the project selector page, select or create a Google Cloud project.
- Make sure that billing is enabled for your Cloud project.

Use the drop-down menu in the top-left corner to switch between tenants.

Multi-tenancy @microsoft Azure
Each tenant has its own providers, settings, and users. Once you've selected a tenant, you can manage it the same way as a non-tenant Identity Platform project.
In multi-tenant architectural designs in web servers, multiple websites are running on the same web server instance. Hostnames are used to differentiate between the different applications which are hosted. By default, application gateway does not change the incoming HTTP host header from the client and sends the header unaltered to the back end. This works well for backend pool members such as NICs, virtual machine scale sets, public IP addresses, internal IP addresses and FQDN as these do not rely on a specific host header or SNI extension to resolve to the correct endpoint. However, there are many services such as Azure App service web apps and Azure API management that are multi-tenant in nature and rely on a specific host header or SNI extension to resolve to the correct endpoint



Why Multi-tenancy is a win-win situation
For many years, hardware virtualization and multi-tenancy have been the building blocks of providing hosted software services to customers, while creating a cost model that worked for software providers. This model gave customers the ability to use software without the cost and hassle of hosting it internally within their own datacenters. In many cases, this was a win-win situation.
Multitenancy:
Multi-tenancy is an architecture in which a single instance of a software application serves multiple customers. Each customer is called a tenant. Tenants may be given the ability to customize some parts of the application, such as the color of the user interface UI or business rules, but they cannot customize the application's code.
In a multi-tenant architecture, multiple instances of an application operate in a shared environment. This architecture is able to work because each tenant is integrated physically, but logically separated; meaning that a single instance of the software will run on one server and then serve multiple tenants. In this way, a software application in a multi-tenant architecture can share a dedicated instance of configurations, data, user management, and other properties.
Importance of Multitenancy:
Multi-tenancy is used most with cloud computing. Multi-tenant architectures are found in both public cloud and private cloud environments, allowing each tenant's data to be separated from each other. For example, in a multi-tenant public cloud, the same servers will be used in a hosted environment to host multiple users. Each user is given a separate and ideally secure space within those servers to store data. Multi-tenancy is also important for the scalability of public and private clouds.
Types of Multitenant Architecture:
There are three main multi-tenancy model types:
-
A single, shared database schema:
It is a multi-tenancy model with a multi-tenant database. This is the simplest form out of the three and is a relatively low cost for tenants because of the use of shared resources. This form uses a single application and database instance to host tenants and store data. Using a single, shared database schema allows for easier scaling; however, operational costs can be higher. -
A single database with multiple schemas:
This tenant system uses a single application instance with individual databases for each tenant. In addition, this architecture has a higher cost with more overhead with each database. It is a valuable architecture when data from different tenants need to be treated differently -- such as if they had to go through different geographic regulations. -
Data in multiple databases:
This model is relatively complex in terms of management and maintenance, but tenants can be separated by a chosen criterion.
Advantages of multi-tenancy:
-
It is less expensive when compared to other tenant hosting architectures.
-
An offering of pay-for-what-you-need pricing models.
-
Tenants don't have to worry about updates since they are pushed out by the host provider.
-
Tenants don't have to worry about the hardware their data is being hosted on.
-
Providers only have to monitor and administrate a single system.
-
The architecture is easily scalable.
Disadvantages of multitenant architecture:
-
Multi-tenant apps tend to be less flexible than apps in other tenant architectures, such as single-tenancy.
-
Multi-tenancy is, in general, more complex than single-tenancy.
-
Multi-tenant apps need stricter authentication and access controls for security.
-
Tenants have to worry about noisy neighbors, meaning someone else on the same CPU that consumes a lot of cycles, which
may slow response time. -
Downtime may also be an issue depending on the provider.
Example:
In cloud computing, the meaning of multi-tenant architecture has broadened because of new service models that take advantage of virtualization and remote access. A software-as-a-service (SaaS) provider, for example, can run one instance of its application on one instance of a database and provide web access to multiple customers. In such a scenario, each tenant's data is isolated and remains invisible to other tenants.
Multi-tenant vs. single-tenant:
In single-tenant architectures, a tenant will have a singular instance of a SaaS application dedicated to them, unlike multi-tenancy where there are shared services. Because each tenant is in a separate environment, they are not bound in the same way that users of shared infrastructure would be; meaning single-tenant architectures are much more customizable. Multi-tenancy can be contrasted with single-tenancy, an architecture in which each customer has their own software instance and may be given access to source code.
Multi-tenancy is the more used option of the two, as most SaaS services operate on multi-tenancy.
In comparison to single-tenancy, multi-tenancy is cheaper, has more efficient resource usage, fewer maintenance costs as well as a potential for larger computing capacity.
With a multi-tenant architecture, the provider only has to make updates once. With a single-tenant architecture, the provider must touch multiple instances of the software in order to make updates.
A potential customer would likely choose a single-tenant infrastructure over multi-tenancy for the ability to have more control and flexibility in their environment -- typically to address specific requirements.

Multitenancy
Multitenancy is a reference to the mode of operation of software where multiple independent instances of one or multiple applications operate in a shared environment. The instances (tenants) are logically isolated, but physically integrated. The degree of logical isolation must be complete, but the degree of physical integration will vary. The more physical integration, the harder it is to preserve the logical isolation. The tenants (application instances) can be representations of organizations that obtained access to the multitenant application (this is the scenario of ISV offering services of an application to multiple customer organizations). The tenants may also be multiple applications competing for shared underlying resources (this is the scenario of a private or public cloud where multiple applications are offered in a common cloud environment).
Multi-Tenant Architecture
Multi-tenant architecture, commonly referred to as multitenancy, is a software architecture in which multiple single instances of software run on a single physical server. The server then serves multiple tenants.
“Tenants” is a term for a group of users or software applications that all share access to the hardware through the underlying software. Multiple tenants on a server all share the memory, which is dynamically allocated and cleaned up as needed. They also share access to system resources, such as the network controller.
This is the opposite of single-tenancy, in which the server runs one instance of the operating system and one application. This one application could be something simple like file and print apps, complexes like Web or application servers, or mission-critical, such as a database.
Applications
Multitenancy is often used in cloud computing, to offer shared tenancy on public cloud providers like Amazon Web Services and Microsoft Azure. Additionally, multitenancy is a key part of another cloud model, software as a service, and so is deployed by many software as a service companies.
Advantages of Multi-Tenant Hosting
The chief advantage of multi-tenant hosting is that it is less expensive. The resource pooling greatly reduces the cost since you only pay for what you need. And since multi-tenant is part of a SaaS provider, you are not paying for on-premises hardware. Functions like system monitoring and servicing the deployment become shared among all of the customers, which makes it less expensive as the cost is spread around.
There are other advantages as well.
- Simplified hosting: It’s not your hardware to manage anymore, reducing a lot of time and expense.
- Better protection of systems: With less interaction with the outside world, exposure to malicious software is reduced.
- Upgrading software is no longer your problem: You always get the latest version of software pushed out to you by the provider.
Disadvantages of Multi-Tenant Hosting
Despite its cost advantage, multi-tenant environments have some downsides.
- They have their own security risks: For starters, you need strict authentication and access controls to make sure the right people get access. Second, data corruption could possibly spread from one user to all, though precautions guard against this.
- Downtime: Outages can be nationwide, and often make the news when they happen. SaaS providers tend to build enough redundancy into the system to minimize this.
- Noise neighbors: As mentioned earlier, someone else on your CPU might be consuming cycles and slowing you down. Capacity is supposed to be elastic and expand as needed but that’s not always the case.
API
API stands for Application Programming Interface, which is a mechanism that allows the interaction between two applications using a set of rules.
APIs are beneficial because they allow developers to add specific functionality to an application, without having to write all of the code themselves. APIs also allow developers to access data from other applications. For example, when bloggers put their Twitter handle on their blog’s sidebar, WordPress enables this by using Twitter’s API.
Types of Web APIs
There are four main types of APIs:
- Open APIs: Also known as Public API, there are no restrictions to access these types of APIs because they are publicly available.
- Partner APIs: A developer needs specific rights or licenses to access this type of API because they are not available to the public.
- Internal APIs: Also known as Private APIs, only internal systems expose this type of API. These are usually designed for internal use within a company. The company uses this type of API among the different internal teams to be able to improve its products and services.
- Composite APIs: This type of API combines different data and service APIs. It is a sequence of tasks that run synchronously as a result of the execution, and not at the request of a task. Its main uses are to speed up the process of execution and improve the performance of the listeners in the web interfaces.
Many companies are providing different APIs for text & speech recognition, video & Image analysis, different ML predictive algorithms, etc. examples of some companies are Amazon, Google, Microsoft, IBM, etc.
APIs for text and speech recognition:
These APIs can easily be embedded by a programmer. It helps in receiving the speech from the user and convert it into text, then interpreted that text to get the meaning and do the task as per the instruction. Some examples are Amazon lex, amazon transcribe, Bing Speech API & Speaker Recognition API by Microsoft, Cloud natural language API, Cloud Speech API, and Cloud Translation API by Google.
APIs for image and video recognition:
These APIs get input as Images or Videos, identifies objects inside the image like identifying faces, vehicles, and their number, identifies different animals, recognize places from the maps, etc. Some APIS are Amazon Rekognition, Microsoft Azure Cognitive Services, Cloud Vision API, AutoML video intelligence classification API & AutoML vision API by Google.
Comparison between APIs providers ( Amazon(AWS), Microsoft(Azure), Google(Google Cloud)
| Criteria | AWS | Azure | Google Cloud |
|---|---|---|---|
| Machine Learning Services for Predictive Analytics | |||
| Machine Learning APIs for speech and text recognition | |||
| Machine learning APIs for image and video recognition | |||
| In-built algorithms | Available with Amazon SageMaker | No in-built algorithms | Available with Google ML Engine |
| Classification | Allowed | Allowed | Allowed |
| Regression | Allowed | Allowed | Allowed |
| Clustering | Allowed | Allowed | Not Allowed |
| Supported Frameworks |