Fresh malware samples caught in the wild from random places.
(Currently creating a honeypot)
I'm not responsible for any damages done to any network infrastructure or computer, all of these files contain LIVE malware that will damage a computer. All of the files here are for educational and research purposes only, none other. By downloading these files, you automatically agree that you take full responsibility for any actions that occur.
Default password: perfect
All file names are encrypted (Prevent anti-virus from scanning file names and CRC checksums within compressed file) and all files are 7zipped. It is to note, that the hashing algorithm is SHA256 to avoid collision.
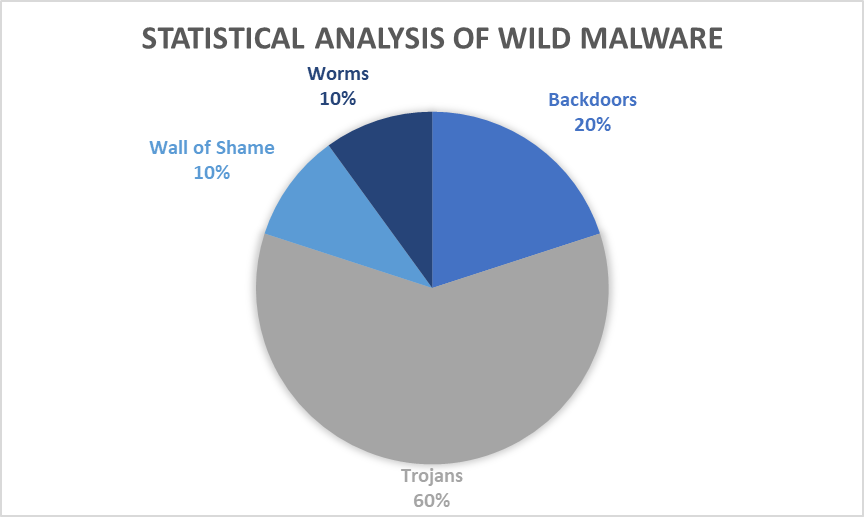
6/22/19: Backdoor:MSIL/Bladabindi.BT!bit | SHA256 checksum: 0dec66b1a3ac75cae41d91cfc4f25616590e25fefe3106166e272748b60a9ca4
6/21/19: HackTool.CryptoDoubler | SHA256 checksum: 29441fe3eb30afa8c664d95ca6466dc7de88713643f6793d4679b42848f238f5
6/20/19: HEUR:Worm.Script.Generic | SHA256 checksum: 823a313dcb80c6684fd22b6a1666240cf0e4612ddaab1bdb3ed9d0afd152e9a0
6/19/19: Trojan:Win32/Tiggre!plock | SHA256 checksum: 95f95fae6c1325fd4842f05d12210083aa5b4d28b13b6e13123fbc866beaf538
6/18/19: Trojan:Win32/Occamy.C | SHA256 checksum: f1ed060f21cd2c7f276ed00e16e80a55cb7abdb4aa0d87fc7b2791607b20070f
6/17/19: Trojan:Win32/Spursint.F!cl | SHA256 checksum: 734ceb637b21c3f27897716c151be3eff1bf0c95702f3a9d83c0ca753b96ebc8
6/16/19: Backdoor:Win32/LimeRat.YA!MTB | SHA256 checksum: 159d208aa3726c213003ba764d6473f3eaedd1018b826f1951769da022d9ea9a
6/15/19: Trojan:Win32/Fuerboos.C!cl | SHA256 checksum: 8c889e0aa50c5ed1b05658afa302c4001c18d784100e312f2962fac72e572b38
6/14/19: Trojan:Win32/Predator.J!MTB | SHA256 checksum: f9a84a3a6492ab46c3e64e7c14071d693028ba7e71319c4664eadae7a076be21
6/13/19: Trojan:Win32/Wacatac.A!ml | SHA256 checksum: 8085469c8e17c0523b91fcadadbcac9c0a3c7643fcb935d6fa33b1aa2c5cd983
6/21/19: hacktool.cryptodoubler.7z was placed in the Wall of Shame folder due to the bad attempt of social engineering people to send Bitcoins to the malware developers wallet.
6/20/19: HEUR:Worm.Script.Generic connects to a domain (alop01.ddns.net) in Peru to download a file and an IP address (181.64.35.184) with obfuscated VBScript in the original file.
Updated every week (6/22/19)
If you want to contribute or make changes, make an issue or just fork and push a file alongside with the SHA256 checksum of the 7-zipped file also make sure the file names encrypted, please make sure it's malware with the default password perfect (Credit will be given).