Original Codebase Repository: https://github.com/Western-OC2-Lab/Intrusion-Detection-System-Using-Machine-Learning
- Logan Falkenberg
- Brad Hayes
- Phillip Henry
- Angela Noronha
- Collin Reisman
Welcome to the Multi-Tiered Hybrid Intrusion Detection System for Internet of Vehicles (IoV)! This cutting-edge project is engineered to bolster the security of vehicular networks through a sophisticated, layered approach that detects and prevents intrusions. By harnessing the power of machine learning algorithms and real-time data analysis, our system identifies and mitigates potential threats, ensuring robust protection for connected vehicles in an increasingly interconnected world.
- Multi-Tiered Hybrid Intrusion Detection System for Internet of Vehicles (IoV) 🚗
Access the project repository on GitHub:
🔗 4371-Project-Structure-For-Jupyter-Notebook
To seamlessly run the codebase from our repository, follow the comprehensive steps outlined below. These instructions are tailored for our group's setup, though alternative methods may also be applicable.
Ensure you have the following tools installed on your machine:
-
Git: Version control system.
📥 Download Git -
Anaconda: Python environment manager.
📥 Download Anaconda
Open your terminal or command prompt and clone the repository:
git clone https://github.com/TheTallProgrammer/4371-Project-Structure-For-Jupyter-Notebook.gitNavigate to the cloned directory:
cd 4371-Project-Structure-For-Jupyter-NotebookIf Anaconda isn't installed, download it from the Anaconda Download Page and follow the installation instructions for your operating system.
Open the Anaconda Powershell Prompt (or Anaconda Prompt on Windows) and execute the following commands:
-
- Ensure Conda is up to date:
conda update conda -y
- Ensure Conda is up to date:
-
-
Create a Conda environment named
myenvwith Python 3.10:conda create -n myenv python=3.10 -y
-
-
-
Activate the newly created environment:
conda activate myenv
-
Install the necessary Python packages:
conda install numpy=1.26.4 scipy scikit-learn notebook ipykernel -yRegister the Conda environment as a Jupyter kernel:
python -m ipykernel install --user --name myenv --display-name "Python (myenv)"Start Jupyter Notebook:
jupyter notebookThis command will open Jupyter Notebook in your default web browser.
For future sessions, simply perform the following steps:
-
Activate the Conda Environment:
conda activate myenv
-
Launch Jupyter Notebook:
jupyter notebook
-
Navigate to the
MTH_IDS_IoTJ-enhanced.ipynbfile in the Jupyter interface and run the notebook as usual.
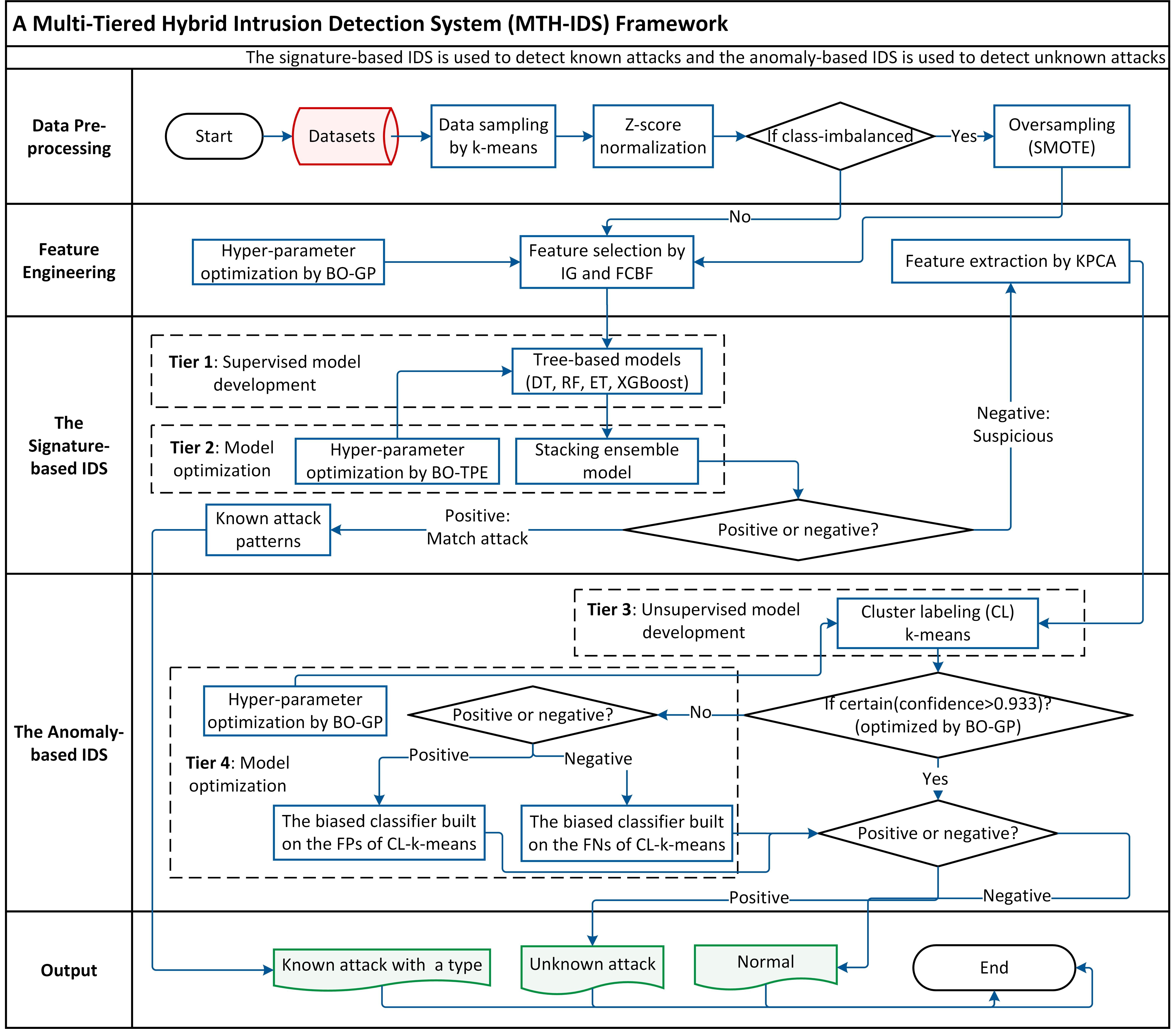
The Multi-Tiered Hybrid Intrusion Detection System (MTH-IDS) employs a tri-layered anomaly detection framework to enhance its capability in distinguishing between benign and malicious network traffic. This multi-tiered strategy ensures a more accurate and efficient intrusion detection mechanism by pre-filtering anomalies before the final threat detection stage.
-
Isolation Forest (Logan Falkenberg)
- Purpose: Detects and filters out outliers from the dataset before applying synthetic data balancing techniques like SMOTE.
- Implementation Details:
- Applied after Z-score normalization and before SMOTE to ensure data cleanliness.
- Parameters:
n_estimators=200,contamination='auto',random_state=42,n_jobs=-1. - Filters out anomalies to prevent SMOTE from misclassifying anomalies as normal data, thereby reducing confusion in model training.
-
One-Class SVM (Brad Hayes)
- Purpose: Learns the characteristics of normal data to effectively identify anomalies.
- Implementation Details:
- Utilizes a radial basis function (RBF) kernel with
gamma='auto'andnu=0.5. - Maps predictions to binary labels to align with the dataset's labeling convention.
- Evaluates model performance using classification reports and confusion matrices to ensure reliability.
- Utilizes a radial basis function (RBF) kernel with
-
Local Outlier Factor (LOF) (Collin Reisman and Angela Noronha)
- Purpose: Identifies local density deviations of data points, effectively detecting outliers in the dataset.
- Implementation Details:
- Standardizes data before applying PCA for dimensionality reduction.
- Uses
n_neighbors=20andcontamination=0.1to fine-tune anomaly detection sensitivity. - Visualizes anomaly scores and outlier distributions to assess detection thresholds and model performance.
-
Voting Mechanism (Phillip Henry)
- Purpose: Combines the predictions from multiple machine learning models (Decision Tree, Random Forest, Extra Trees, and XGBoost) to enhance robustness, accuracy, and overall model performance.
- Implementation Details:
- Uses soft voting, where the predicted probabilities from all models are averaged to determine the final prediction. This approach leverages the confidence of each model's prediction.
- Integrates hyperparameter-optimized versions of Decision Tree, Random Forest, and Extra Trees, along with an XGBoost classifier.
- Evaluates ensemble performance with metrics such as accuracy, classification reports, and confusion matrices, providing insights into its effectiveness.
Integrating these algorithms serves to reduce the number of undiagnosed anomalies within the system. By differentiating as many anomalies as possible—whether they are threats or benign network traffic—before the final threat detection stage, the system maintains a filtered dataset. This pre-filtering ensures that the intrusion detection mechanisms operate on high-quality, noise-reduced data, enhancing overall accuracy and efficiency.
Key Benefits:
- Enhanced Data Quality: Removes noise and outliers, ensuring that the training data is clean and representative.
- Improved Model Performance: Reduces confusion caused by synthetic data generation on anomalous points, leading to more reliable threat detection.
- Efficient Anomaly Management: Differentiates between malicious and benign anomalies, allowing for targeted responses and better resource allocation.
Note: While these functionalities have been successfully implemented and tested within our group, there may be alternative methods or additional optimizations that can further enhance the system's capabilities.
Once the notebook is running, you can interact with the Multi-Tiered Hybrid Intrusion Detection System to:
- 📊 Analyze Data: Process and visualize data related to vehicular networks.
- 🧠 Train Models: Utilize machine learning algorithms to train intrusion detection models.
- 🔍 Detect Intrusions: Apply trained models to identify and respond to potential security threats in real-time.
Foundational Research:
The study by Hoppe, Kiltz, and Dittmann (2008) laid the groundwork for securing vehicular networks by analyzing vulnerabilities in CAN protocols and proposing initial countermeasures. This foundational work emphasized the critical need for intrusion detection systems in automotive communication.
- Hoppe, T., Kiltz, S., & Dittmann, J. (2008). Security Threats to Automotive CAN Networks – Practical Examples and Selected Short-Term Countermeasures. In M. D. Harrison & M. A. Sujan (Eds.), Computer Safety, Reliability, and Security. SAFECOMP 2008. Lecture Notes in Computer Science (Vol. 5219). Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-540-87698-4_21
Subsequent Research:
The study by Qin, Xun, and Liu (2024) builds on prior frameworks, including MTH-IDS, by introducing a cloud–vehicle collaborative system for intrusion detection in the Internet of Vehicles. It extends hybrid methodologies to improve detection accuracy and response in modern vehicular networks.
- Qin, J., Xun, Y., & Liu, J. (2024). CVMIDS: Cloud–Vehicle Collaborative Intrusion Detection System for Internet of Vehicles. IEEE Internet of Things Journal, 11(1), 321–332. https://doi.org/10.1109/JIOT.2023.3318181