Knowledge
source ~ https://miro.com/app/board/uXjVPFOvxQk=/?share_link_id=347742750356
Mandatory
Partitions
Download Debian https://www.debian.org/CD/netinst/
STEP 1 - VM settings
VirtualBox > New
Name Anything of your choice
Machine Folder > goinfre/VirtualBox VMs/
Type: Linux
Version: Debian 64-bit
Continue > RAM 1024 MB > Continue
> Create a virtual hard disk now > VDI
> Fixed size > 8gb or 30.80gb for bonus
Settings > Storage > Controller: IDE
> Optical Drive: disk icon
> Choose a disk file
> your debian-xx-x-x-amd64.iso > Ok > Start
STEP 2 - Installation
Install (Not Graphical install)
Choose language (English)
Territory or area: Choose yours. or -> America
> Hostname: yourintralogin42
> Domain name: leave empty
> Root password: (dont forget it); Re-enter.
> Full name: Your full name.
> Username: yourintralogin
> Password: (whatever) -> Time zone: Your time zone or Moscow for Moscow
campus (yes). Wait.
STEP 3 - partition setup
For Mandatory part:
Partition method: Guided - Use entire disk and set up encrypted LVM
> SCSIX (0,0,0) (sda) 8.6 GB ATA VBOX HARDDISK
> separate /home partition
> yes. Wait.
> Enter encryption passphrase twice > max >
> Finish partitioning and write changes to disk
> yes. Wait.
For Bonus part:
Partition method: Manual > SCSIX (0,0,0) (sda) > 30.80 GB ATA HARDDISK >
> yes > pri/log 30.80 GB FREE SPACE > Create a new partition >
> 500M > Primary > Beginning > Mount point > Boot >
> Done setting up the partition(DSUP) > pri/log > CRANP > "max">
> Logical > mount point > Do not mount it > DSUP >
> Configure encrypted volumes > Yes > Create encrypted volumes >
> /dev/sda5 (press space to choose it) > DSUTP > Finish > yes > Wait.
Enter encryption passphrase twice > Configure the Logical Volume Manager >
> yes > Create volume groupe > LVMGroup >
> press pace on /dev/mapper/sda5_crypt, continue >
> Create logical volume(CLV next) > LVMGroup (LVMG next) > root > 10G
CLV > LVMG > swap > 2.3G
CLV > LVMG > home > 5G
CLV > LVMG > var > 3G
CLV > LVMG > srv > 3G
CLV > LVMG > tmp > 3G
CLV > LVMG > var-log > 4G > Finish
Now u see "[!!] Partition disks" window and a lot of LVM VG LVMGroup LV ...
Go to first #1 (under home, <volumename> #1 for next steps) >
> Use as (UA next): > EXT4 jfl > Mount point: (MP next) > /home >
> Done setting up the partition (yep, DSUP)
root #1 > UA > ext4 > MU > / - the root fs > DSUP
srv #1 > UA > ext4 > MU > /srv > DSUP
swap #1 > UA > swap area > DSUP
tmp #1 > UA > ext4 > MU > /tmp > DSUP
var #1 > UA > ext4 > MU > /var > DSUP
var-log #1 > UA > ext4 > MU > Enter manually > /var/log > DSUP
Scroll below > Finish partitioning and write changes to disk > yes
Now chill, you have plenty of time to stretch your back while debian is installing.
[!] Configure the package manager > no
Debian archive mirror country > deb.debian.org (doesn't matter) >
> leave proxy info field empty and proceed.
Participate in the package usage survey? > NO!
Soft seclection: remove stars from ssh/standart system utilities/etc. (space)
GRUB - YES! > /dev/sda
Installlation complete > continue
Virtual machine is ready...
source ~ https://www.redhat.com/sysadmin/lvm-vs-partitioning
Server configuration
login to the root account
$ suand install the sudo package (sudo gives limited users root privileges)
$ apt install sudoAdds the specified user to the sudo group
$ adduser yelaissa sudoCheck if the user is added to sudo group
$ getent group sudoReboot the system with the "reboot" command.source ~ https://wiki.debian.org/sudo/https://wiki.debian.org/sudo/
source ~ https://www.cloudpanel.io/tutorial/how-to-add-user-to-sudoers-in-debian/ (add user to sudoers)
Update the package lists.
$ sudo apt updateOpen sudo files with "visudo"
Creates a more secure structure, we created a new file called 1337 in the specified directory
$ sudo visudo -f /etc/sudoers.d/1337And we will add the following codes.
// The maximum number of password attempts with Sudo is 3 (3 is the standard)
Defaults passwd_tries=3
// Your error message after incorrect password attempts
Defaults badpass_message="incorrect password"
// Stores all used sudo commands in the specified file
Defaults logfile="/var/log/sudo/1337"
// Used to keep logs of input and output events.
Defaults log_input,log_output
// Archive log_input and log_output events to the specified directory.
Defaults iolog_dir="/var/log/sudo"
// Enforces TTY mode.
Defaults requiretty
// To restrict the directories used by Sudo.
Defaults secure_path="see subject"Reboot the system with the "reboot" command.source ~ https://www.tecmint.com/sudoers-configurations-for-setting-sudo-in-linux/
source ~ https://manpages.debian.org/bullseye/sudo-ldap/sudoers.5.en.html#Tag_Spec
Openssh provides a secure channel over an unsecured network from outside
let install the Openssh-server package
$ sudo apt install openssh-serverSSH Configuration section.
$ sudo nano /etc/ssh/sshd_config
Change "#Port 22" to "Port 4242"
Change "#PermitRootLogin prohibit-password"to "PermitRootLogin no"
Reboot the system with the "reboot" command.source ~ https://phoenixnap.com/kb/how-to-enable-ssh-on-debian
You can view ssh status by typing this command.
$ sudo service ssh status
UFWIt stands for "uncomplicated firewall"you install that package.
$ sudo apt install ufwWe activate our firewall.
$ sudo ufw enableWe add a new rule to our firewall for port 4242 and allow it.
$ sudo ufw allow 4242check the status of our firewall.
$ sudo ufw statuspoweroff the system with the "poweroff" command.source ~ https://www.digitalocean.com/community/tutorials/how-to-set-up-a-firewall-with-ufw-on-debian-9
Login to our server from our host machine
if you're using NAT
you need to do port forwarding on the vm in order to make ssh connection
| NAME | HOST IP | HOST PORT | GUEST IP | GUEST PORT |
|---|---|---|---|---|
| SSH | 127.0.0.1 | 4242 | 10.0.2.15 | 4242 |
| HTTP | 127.0.0.1 | 80 | 10.0.2.15 | 80 |
| FTP | 127.0.0.1 | 21 | 10.0.2.15 | 21 |
(Or just use Bridged Adapter)
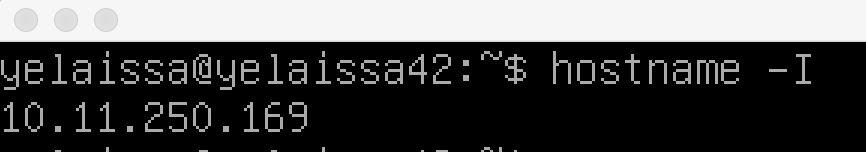
Then check your ip
$ hostname -Imake sure ssh is running
sudo service ssh status
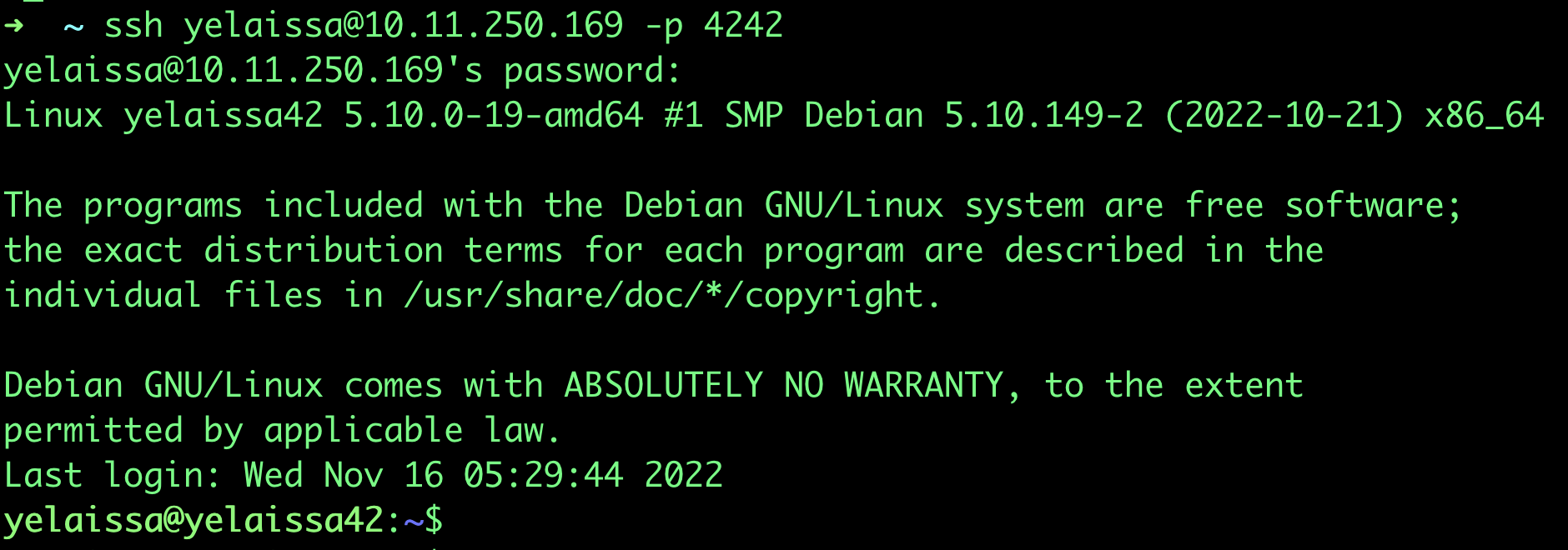
fire up the terminal in your host machine and try to remote login to the VM
$ ssh <username>@<ip_address> -p <port>source ~ https://medium.com/platform-engineer/port-forwarding-for-ssh-http-on-virtualbox-459277a888be
Change password policy
(sudo chage) to modify the user you're using
We open the file
login.defswith Nano/vim
$ sudo nano /etc/login.defs//Password will expire every 30 days
Before > PASS_MAX_DAYS 99999
After > PASS_MAX_DAYS 30
// The minimum number of days allowed before the modification of a password will be set to 2
Before > PASS_MIN_DAYS 0
After > PASS_MIN_DAYS 2
// The user has to receive a warning message 7 days before their password expires
PASS_WARN_AGE 7To increase the security of passwords you have to install
libpam-pwquality
$ sudo apt install libpam-pwquality
$ sudo nano /etc/pam.d/common-passwordFind this line
password requisite pam_pwquality.so retry=3And add to it the following
//Your password must be at least 10 characters long
minlen=10
// It must contain an uppercase letter
ucredit=-1
// a lowercase letter
lcredit=-1
// and a number
dcredit=-1
//it must not contain more than 3 consecutive identical characters
maxrepeat=3
// The password must not include the name of the user
reject_username
// The password must have at least 7 characters that are not part of the former password
difok=7
// your root password has to comply with this policy
enforce_for_rootIt should look like this
password requisite pam_pwquality.so retry=3 minlen=10 ucredit=-1 lcredit=-1 dcredit=-1 maxrepeat=3 reject_username difok=7 enforce_for_root
source ~ https://linux.die.net/man/8/pam_cracklib
source ~ https://www.networkworld.com/article/2726217/how-to-enforce-password-complexity-on-linux.html
Create a group
$ sudo addgroup user42add a user to the
user42andsudogroups.
$ sudo adduser <username> user42
$ sudo adduser <username> sudoScript
The script will display some information on
all ter-minalsevery10 minutes
we need to configure crontab
Cron is used for scheduling jobs so we will use it to run our script every 10 minutes
$ sudo crontab -eAdd this at the end
*/10 * * * * /path/to/script
The script will run every 10 minutes
If you want to run it every startup add this
@reboot && /path/to/script
source ~ https://www.cyberciti.biz/faq/crontab-every-10-min/
source ~ https://webdock.io/en/docs/how-guides/system-maintenance/how-configure-crontab-linux
helpful ~ https://crontab.guru/#
Let create the script now
helpful ~ https://serverfault.com/questions/287724/can-i-place-my-script-in-usr-bin
The architecture of your operating system and its kernel version.
uname -a
s ~ https://www.cyberciti.biz/faq/find-print-linux-unix-kernel-version/
The number of physical processors
grep "physical id" /proc/cpuinfo | sort | uniq | wc -l
s ~ https://www.networkworld.com/article/2715970/counting-processors-on-your-linux-box.html
The number of virtual processors
grep "^processor" /proc/cpuinfo | sort | uniq | wc -l
s ~ https://www.networkworld.com/article/2715970/counting-processors-on-your-linux-box.html
The current available RAM on your server and its utilization rate as a percentage
// Used memory/total
free -m | grep Mem: | awk '{printf("%d/%dMB", $3, $2)}'
// utilization rate as a percentage
free -m | grep Mem: | awk '{printf("%.2f\n"), $3/$2*100}'s ~ https://www.2daygeek.com/linux-check-cpu-memory-swap-utilization-percentage/
The current available memory on your server and its utilization rate as a percentage
diskUsed=$(df -Bm | grep '^/dev/' | grep -v '/boot$' | awk '{used += $3} END {print used}')
diskTotal=$(df -Bg | grep '^/dev/' | grep -v '/boot$' | awk '{total += $2} END {printf("%dGb", total)}')
percDisk=$(df -Bm | grep '^/dev/' | grep -v '/boot$' | awk '{total += $2} {used += $3} END {printf("%.2f"), used/total*100}')s ~
The current utilization rate of your processors as a percentage
top -bn1 | grep '^%Cpu' | awk -F , '{printf("%.1f%%\n"), 100 - $4}'
To be continued
monitoring.sh
#! /bin/bash
arch=$(uname -a)
cpuPhy=$(grep "physical id" /proc/cpuinfo | uniq | wc -l)
cpuV=$(grep "^processor" /proc/cpuinfo | wc -l)
usedMem=$(free -m | grep Mem: | awk '{printf("%d/%dMB", $3, $2)}')
percMem=$(free -m | grep Mem: | awk '{printf("%.2f\n"), $3/$2*100}')
diskU=$(df -Bm --total | grep ^total | awk '{print $3}' | awk -F M '{print $1}')
diskT=$(df -Bg --total | grep ^total | awk '{printf("%sb", $2)}')
percDisk=$(df --total | grep ^total | awk '{print $5}')
cpuL=$(top -bn1 | grep '^%Cpu' | awk -F , '{print $4}' | awk '{print 100 - $1}')
lboot=$(who -b | awk '{printf("%s %s"), $3, $4}')
LVMS=$(lsblk | grep lvm | awk '{if ($6 == "lvm") print "yes"; else print "no"}' | uniq)
cTCP=$(ss | grep tcp | wc -l)
userlog=$(w -h | wc -l)
Ipv4=$(hostname -I)
MAC=$(ip addr | grep "link/ether" | awk '{printf("(%s)"),$2}')
sudoCMD=$(journalctl _COMM=sudo | grep COMMAND | wc -l)
wall "
#Architecture : $arch
#CPU physical : $cpuPhy
#vCPU : $cpuV
#Memory Usage: $usedMem ($percMem%)
#Disk Usage: $diskU/$diskT ($percDisk)
#CPU load: $cpuL%
#Last boot: $lboot
#LVM use: $LVMS
#Connections TCP : $cTCP ESTABLISHED
#User log: $userlog
#Network: IP $Ipv4 $MAC
#Sudo : $sudoCMD cmd"Bonus
Wordpress website
Install
lighttpdand configure it
Lighttpd is a “secure, fast, compatible and very flexible” web server optimized for high-performance environments. It consumes very few resources compared to other web servers and especially fast for running AJAX applications. It is also open source and uses a BSD license and works on UNIX-like systems, such as Linux or BSD.
Combining Debian with Lighttpd is a safe bet if you want a fast, efficient and secure web server. Go for it.
$ sudo apt install lighttpdwe should enable port 80 with ufw
$ sudo ufw allow 80source ~ https://www.osradar.com/install-lighttpd-debian-10/
install
PHP
$ sudo apt install php-cgi php-fpm php-mysqlinstall
mariadb
$ sudo apt install mariadb-serverThen, once the installation is complete, the mysq_secure_installation script must be run to define a new key for the root user and other configurations.
$ sudo mysql_secure_installationAfter defining the new password for the root user, you will have to answer a few questions.
Remove anonymous users? Y
Disallow root login remotely? Y
Remove test database and access to it? Y
Reload privilege tables now? Y
Now access the MariaDB console
$ sudo mysql -u root -p
or
$ sudo mariadb
And create the database for WordPress and a new user.
CREATE DATABASE wordpress;GRANT ALL PRIVILEGES on wordpress.* TO 'yelaissa'@'localhost' IDENTIFIED BY 'wp-pss123';FLUSH PRIVILEGES;EXIT;Now check if whether database user was successfully created by logging in to the MariaDB console via mariadb -u -p.
SHOW DATABASES;That’s enough. Now let’s download
WordPress.
$ sudo apt install wgetDownload wp to /var/www/html
$ sudo wget http://wordpress.org/latest.tar.gz -P /var/www/htmlcd /var/www/html
extract the file
sudo tar -xzvf /var/www/html/latest.tar.gz
sudo cp -r /var/www/html/wordpress/* /var/www/html
sudo cp /var/www/html/wp-config-sample.php /var/www/html/wp-config.php
sudo chown -R www-data:www-data /var/www/html
sudo chmod -R 755 /var/www/html
sudo vim /var/www/html/wp-config.php
change these
define( 'DB_NAME', 'wordpress' );
define( 'DB_USER', 'yelaissa' );
define( 'DB_PASSWORD', 'wp-pss123' );sudo lighty-enable-mod fastcgi
sudo lighty-enable-mod fastcgi-php
sudo service lighttpd force-reload
source ~ https://www.osradar.com/install-wordpress-with-lighttpd-debian-10/
FTP
install FTP
sudo apt install vsftpd
allow FTP port (21) and (20)
sudo ufw allow 21/tcp
sudo ufw allow 20/tcp
Configure ftp configurations
sudo nano /etc/vsftpd.conf
listen=NO
listen_ipv6=YES
anonymous_enable=NO
local_enable=YES
write_enable=YES
local_umask=022
dirmessage_enable=YES
use_localtime=YES
xferlog_enable=YES
connect_from_port_20=YES
chroot_local_user=YES
secure_chroot_dir=/var/run/vsftpd/empty
pam_service_name=vsftpd
force_dot_files=YES
pasv_min_port=40000
pasv_max_port=50000
user_sub_token=$USER
local_root=/home/$USER/ftpCreate a new FTP user
sudo adduser ftpyelaissa
create an ftp folder in the directory where our user is located.
sudo mkdir /home/ftpyelaissa/ftp
create a folder of files
sudo mkdir /home/ftpyelaissa/ftp/files
We set the ownership and group of the ftp folder to nobody.
sudo chown nobody:nogroup /home/ftpyelaissa/ftp
sudo chown ftpyelaissa:ftpyelaissa /home/ftpyelaissa/ftp/files
We give write permission to all users.
sudo chmod a-w /home/ftpyelaissa/ftp
We add our user to the list of users.
echo ftpyelaissa | sudo tee -a /etc/vsftpd.userlist
Finally restart FTP service
sudo systemctl restart vsftpd.service
sudo systemctl enable vsftpd.service
source ~ https://linuxhint.com/setup-vsftpd-ftp-server-on-debian10/