Unified Agent & MCP Server Registry – Enterprise-Ready Gateway for AI Development Tools
🚀 Get Running Now | Quick Start | Documentation | Enterprise Features | Community
Demo Videos: ⭐ MCP Registry CLI Demo | Full End-to-End Functionality | OAuth 3-Legged Authentication | Dynamic Tool Discovery
The MCP Gateway & Registry is a unified, enterprise-ready platform that centralizes access to both MCP Servers and AI Agents using the Model Context Protocol (MCP). It serves three core functions:
- Unified MCP Server Gateway – Centralized access point for multiple MCP servers
- MCP Servers Registry – Register, discover, and manage access to MCP servers with unified governance
- Agent Registry & A2A Communication Hub – Agent registration, discovery, governance, and direct agent-to-agent communication through the A2A (Agent-to-Agent) Protocol
The platform integrates with external registries such as Anthropic's MCP Registry (and more to come), providing a single control plane for both tool access, agent orchestration, and agent-to-agent communication patterns.
Why unified? Instead of managing hundreds of individual MCP server configurations, agent connections, and separate governance systems across your development teams, this platform provides secure, governed access to curated MCP servers and registered agents through a single, unified control plane.
Transform this chaos:
❌ AI agents require separate connections to each MCP server
❌ Each developer configures VS Code, Cursor, Claude Code individually
❌ Developers must install and manage MCP servers locally
❌ No standard authentication flow for enterprise tools
❌ Scattered API keys and credentials across tools
❌ No visibility into what tools teams are using
❌ Security risks from unmanaged tool sprawl
❌ No dynamic tool discovery for autonomous agents
❌ No curated tool catalog for multi-tenant environments
❌ A2A provides agent cards but no way for agents to discover other agents
❌ Maintaining separate MCP server and agent registries is a non-starter for governance
❌ Impossible to maintain unified policies across server and agent access
Into this organized approach:
✅ AI agents connect to one gateway, access multiple MCP servers
✅ Single configuration point for VS Code, Cursor, Claude Code
✅ Central IT manages cloud-hosted MCP infrastructure via streamable HTTP
✅ Developers use standard OAuth 2LO/3LO flows for enterprise MCP servers
✅ Centralized credential management with secure vault integration
✅ Complete visibility and audit trail for all tool usage
✅ Enterprise-grade security with governed tool access
✅ Dynamic tool discovery and invocation for autonomous workflows
✅ Registry provides discoverable, curated MCP servers for multi-tenant use
✅ Agents can discover and communicate with other agents through unified Agent Registry
✅ Single control plane for both MCP servers and agent governance
✅ Unified policies and audit trails for both server and agent access
┌─────────────────────────────────────┐ ┌──────────────────────────────────────────────────────┐
│ BEFORE: Chaos │ │ AFTER: MCP Gateway & Registry │
├─────────────────────────────────────┤ ├──────────────────────────────────────────────────────┤
│ │ │ │
│ Developer 1 ──┬──► MCP Server A │ │ Developer 1 ──┐ ┌─ MCP Server A │
│ ├──► MCP Server B │ │ │ ├─ MCP Server B │
│ └──► MCP Server C │ │ Developer 2 ──┼──► MCP Gateway │ │
│ │ │ │ & Registry ───┼─ MCP Server C │
│ Developer 2 ──┬──► MCP Server A │ ──► │ AI Agent 1 ───┘ │ │ │
│ ├──► MCP Server D │ │ │ ├─ AI Agent 1 │
│ └──► MCP Server E │ │ AI Agent 2 ──────────────┤ ├─ AI Agent 2 │
│ │ │ │ │ │
│ AI Agent 1 ───┬──► MCP Server B │ │ AI Agent 3 ──────────────┘ └─ AI Agent 3 │
│ ├──► MCP Server C │ │ │
│ └──► MCP Server F │ │ Single Connection Point │
│ │ │ │
│ ❌ Multiple connections per user │ │ ✅ One gateway for all │
│ ❌ No centralized control │ │ ✅ Unified server & agent access │
│ ❌ Credential sprawl │ │ ✅ Unified governance & audit trails │
└─────────────────────────────────────┘ └──────────────────────────────────────────────────────┘
Note on Agent-to-Agent Communication: AI Agents discover other AI Agents through the unified Agent Registry and communicate with them directly (peer-to-peer) without routing through the MCP Gateway. The Registry handles discovery, authentication, and access control, while agents maintain direct connections for efficient, low-latency communication.
This platform serves as a comprehensive, unified registry supporting:
- ✅ MCP Server Registration & Discovery – Register, discover, and manage access to MCP servers
- ✅ AI Agent Registration & Discovery – Register agents and enable them to discover other agents
- ✅ Agent-to-Agent (A2A) Communication – Direct agent-to-agent communication patterns using the A2A protocol
- ✅ Multi-Protocol Support – Support for various agent communication protocols and patterns
- ✅ Unified Governance – Single policy and access control system for both agents and servers
- ✅ Cross-Protocol Agent Discovery – Agents can discover each other regardless of implementation
- ✅ Integrated External Registries – Connect with Anthropic's MCP Registry and other external sources
- ✅ Agent Cards & Metadata – Rich metadata for agent capabilities, skills, and authentication schemes
Key distinction: Unlike separate point solutions, this unified registry eliminates the need to maintain separate MCP server and agent systems, providing a single control plane for agent orchestration, MCP server access, and agent-to-agent communication.
Watch how MCP Servers, A2A Agents, and External Registries work together for dynamic tool discovery:
MCP-Gateway-Registry-vidcast.mp4
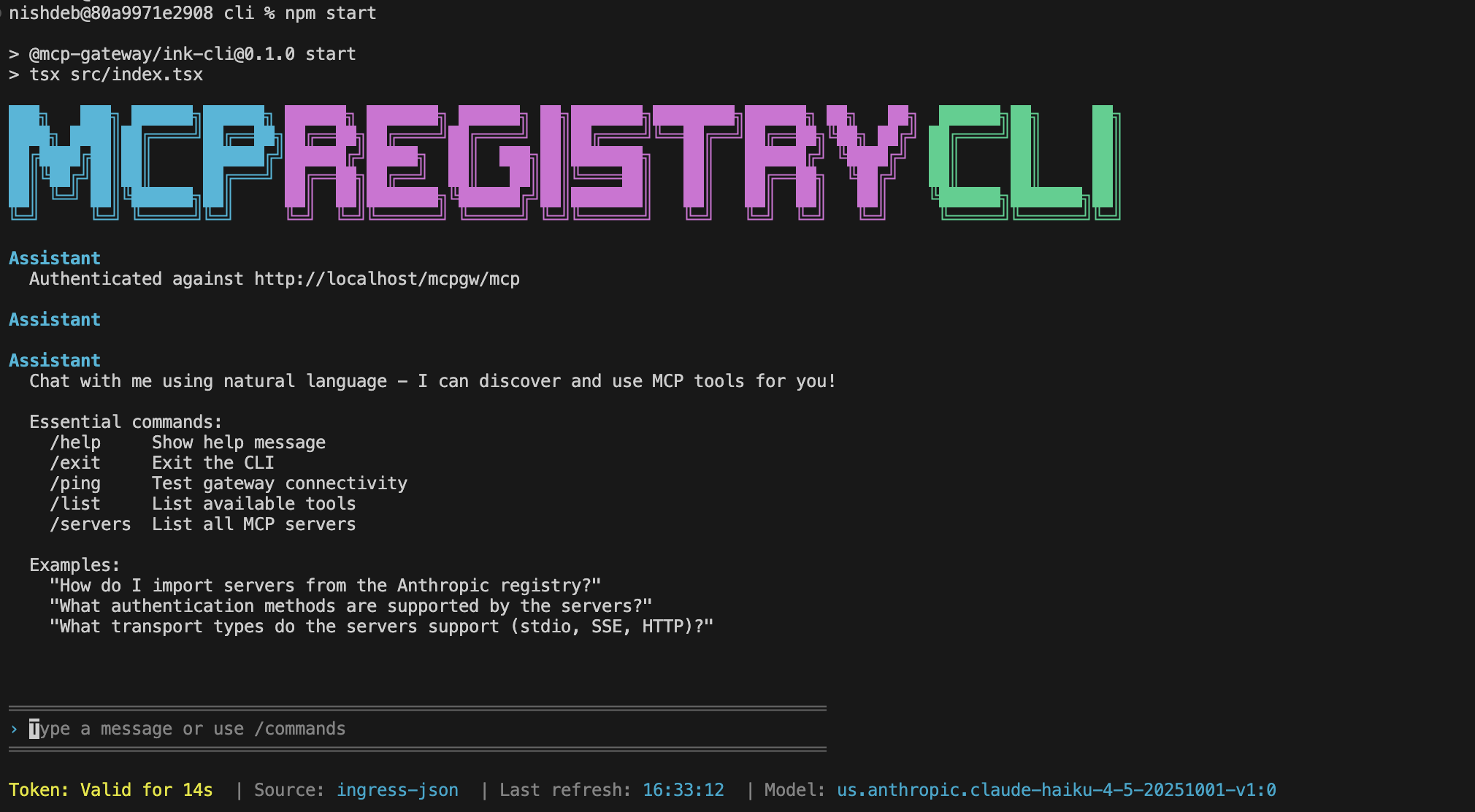
Interactive terminal interface for chatting with AI models and discovering MCP tools in natural language. Talk to the registry using a Claude Code-like conversational interface with real-time token status, cost tracking, and AI model selection.
Quick Start: registry --url https://mcpgateway.ddns.net | Full Guide
- 🔗 Agent-to-Agent (A2A) Protocol Support - Agents can now register, discover, and communicate with other agents through a secure, centralized registry. Enable autonomous agent ecosystems with Keycloak-based access control and fine-grained permissions. A2A Guide
- 🤖 Agentic CLI for MCP Registry - Talk to the Registry in natural language using a Claude Code-like interface. Discover tools, ask questions, and execute MCP commands conversationally. Learn more
- 💬 Interactive MCP-Registry CLI - Terminal-based chat interface with AI-powered MCP tool discovery. Supports Amazon Bedrock and Anthropic API. MCP-Registry CLI
- 🔒 MCP Server Security Scanning - Integrated vulnerability scanning with Cisco AI Defence MCP Scanner. Automatic security scans during server registration, periodic registry-wide scans with detailed markdown reports, and automatic disabling of servers with security issues.
- 📥 Import Servers from Anthropic MCP Registry - Import curated MCP servers from Anthropic's registry with a single command. Import Guide
- 🔌 Anthropic MCP Registry REST API Compatibility - Full compatibility with Anthropic's MCP Registry REST API specification. API Documentation
- 🚀 Pre-built Images - Deploy instantly with pre-built Docker images. Get Started | macOS Guide
- 🔐 Keycloak Integration - Enterprise authentication with AI agent audit trails and group-based authorization. Learn more
- 📊 Real-Time Metrics & Observability - Grafana dashboards with SQLite and OpenTelemetry integration. Observability Guide
- Amazon Bedrock AgentCore Integration - AgentCore Gateway support with dual authentication. Integration Guide
Provide both autonomous AI agents and human developers with secure access to approved tools through AI coding assistants (VS Code, Cursor, Claude Code) while maintaining IT oversight and compliance.
Centralized authentication, fine-grained permissions, and comprehensive audit trails for SOX/GDPR compliance pathways across both human and AI agent access patterns.
AI agents can autonomously discover and execute specialized tools beyond their initial capabilities using intelligent semantic search, while developers get guided tool discovery through their coding assistants.
Single gateway supporting both autonomous AI agents (machine-to-machine) and AI coding assistants (human-guided) with consistent authentication and tool access patterns.
The MCP Gateway & Registry provides a unified platform for both autonomous AI agents and AI coding assistants to access enterprise-curated tools through a centralized gateway with comprehensive authentication and governance.
flowchart TB
subgraph Human_Users["Human Users"]
User1["Human User 1"]
User2["Human User 2"]
UserN["Human User N"]
end
subgraph AI_Agents["AI Agents"]
Agent1["AI Agent 1"]
Agent2["AI Agent 2"]
Agent3["AI Agent 3"]
AgentN["AI Agent N"]
end
subgraph EC2_Gateway["<b>MCP Gateway & Registry</b> (Amazon EC2 Instance)"]
subgraph NGINX["NGINX Reverse Proxy"]
RP["Reverse Proxy Router"]
end
subgraph AuthRegistry["Authentication & Registry Services"]
AuthServer["Auth Server<br/>(Dual Auth)"]
Registry["Registry<br/>Web UI"]
RegistryMCP["Registry<br/>MCP Server"]
end
subgraph LocalMCPServers["Local MCP Servers"]
MCP_Local1["MCP Server 1"]
MCP_Local2["MCP Server 2"]
end
end
%% Identity Provider
IdP[Identity Provider<br/>Keycloak/Cognito]
subgraph EKS_Cluster["Amazon EKS/EC2 Cluster"]
MCP_EKS1["MCP Server 3"]
MCP_EKS2["MCP Server 4"]
end
subgraph APIGW_Lambda["Amazon API Gateway + AWS Lambda"]
API_GW["Amazon API Gateway"]
Lambda1["AWS Lambda Function 1"]
Lambda2["AWS Lambda Function 2"]
end
subgraph External_Systems["External Data Sources & APIs"]
DB1[(Database 1)]
DB2[(Database 2)]
API1["External API 1"]
API2["External API 2"]
API3["External API 3"]
end
%% Connections from Human Users
User1 -->|Web Browser<br>Authentication| IdP
User2 -->|Web Browser<br>Authentication| IdP
UserN -->|Web Browser<br>Authentication| IdP
User1 -->|Web Browser<br>HTTPS| Registry
User2 -->|Web Browser<br>HTTPS| Registry
UserN -->|Web Browser<br>HTTPS| Registry
%% Connections from Agents to Gateway
Agent1 -->|MCP Protocol<br>SSE with Auth| RP
Agent2 -->|MCP Protocol<br>SSE with Auth| RP
Agent3 -->|MCP Protocol<br>Streamable HTTP with Auth| RP
AgentN -->|MCP Protocol<br>Streamable HTTP with Auth| RP
%% Auth flow connections
RP -->|Auth validation| AuthServer
AuthServer -.->|Validate credentials| IdP
Registry -.->|User authentication| IdP
RP -->|Tool discovery| RegistryMCP
RP -->|Web UI access| Registry
%% Connections from Gateway to MCP Servers
RP -->|SSE| MCP_Local1
RP -->|SSE| MCP_Local2
RP -->|SSE| MCP_EKS1
RP -->|SSE| MCP_EKS2
RP -->|Streamable HTTP| API_GW
%% Connections within API GW + Lambda
API_GW --> Lambda1
API_GW --> Lambda2
%% Connections to External Systems
MCP_Local1 -->|Tool Connection| DB1
MCP_Local2 -->|Tool Connection| DB2
MCP_EKS1 -->|Tool Connection| API1
MCP_EKS2 -->|Tool Connection| API2
Lambda1 -->|Tool Connection| API3
%% Style definitions
classDef user fill:#fff9c4,stroke:#f57f17,stroke-width:2px
classDef agent fill:#e1f5fe,stroke:#29b6f6,stroke-width:2px
classDef gateway fill:#e8f5e9,stroke:#66bb6a,stroke-width:2px
classDef nginx fill:#f3e5f5,stroke:#ab47bc,stroke-width:2px
classDef mcpServer fill:#fff3e0,stroke:#ffa726,stroke-width:2px
classDef eks fill:#ede7f6,stroke:#7e57c2,stroke-width:2px
classDef apiGw fill:#fce4ec,stroke:#ec407a,stroke-width:2px
classDef lambda fill:#ffebee,stroke:#ef5350,stroke-width:2px
classDef dataSource fill:#e3f2fd,stroke:#2196f3,stroke-width:2px
%% Apply styles
class User1,User2,UserN user
class Agent1,Agent2,Agent3,AgentN agent
class EC2_Gateway,NGINX gateway
class RP nginx
class AuthServer,Registry,RegistryMCP gateway
class IdP apiGw
class MCP_Local1,MCP_Local2 mcpServer
class EKS_Cluster,MCP_EKS1,MCP_EKS2 eks
class API_GW apiGw
class Lambda1,Lambda2 lambda
class DB1,DB2,API1,API2,API3 dataSource
Key Architectural Benefits:
- Unified Gateway: Single point of access for both AI agents and human developers through coding assistants
- Dual Authentication: Supports both human user authentication and machine-to-machine agent authentication
- Scalable Infrastructure: Nginx reverse proxy with horizontal scaling capabilities
- Multiple Transports: SSE and Streamable HTTP support for different client requirements
- OAuth 2.0/3.0 compliance with IdP integration
- Fine-grained access control at tool and method level
- Zero-trust network architecture
- Complete audit trails and comprehensive analytics for compliance
- Single configuration works across autonomous AI agents and AI coding assistants (VS Code, Cursor, Claude Code, Cline)
- Dynamic tool discovery with natural language queries for both agents and humans
- Instant onboarding for new team members and AI agent deployments
- Unified governance for both AI agents and human developers
- Container-native (Docker/Kubernetes)
- Real-time health monitoring and alerting
- Dual authentication supporting both human and machine authentication
📱 Running on macOS? See our macOS Setup Guide for platform-specific instructions and optimizations.
Get running in under 2 minutes with pre-built containers:
Step 1: Clone and setup
git clone https://github.com/agentic-community/mcp-gateway-registry.git
cd mcp-gateway-registry
cp .env.example .envStep 2: Download embeddings model Download the required sentence-transformers model to the shared models directory:
hf download sentence-transformers/all-MiniLM-L6-v2 --local-dir ${HOME}/mcp-gateway/models/all-MiniLM-L6-v2Step 3: Configure environment Complete: Initial Environment Configuration - Configure domains, passwords, and authentication
export DOCKERHUB_ORG=mcpgatewayStep 4: Deploy with pre-built images
./build_and_run.sh --prebuiltFor detailed information about all Docker images used with --prebuilt, see Pre-built Images Documentation.
Step 5: Initialize Keycloak Complete: Initialize Keycloak Configuration - Set up identity provider and security policies
Step 5.5: Set up users and service accounts Run the bootstrap script to create default users and M2M service accounts:
./cli/bootstrap_user_and_m2m_setup.shThis script:
- Creates 3 Keycloak groups:
registry-users-lob1,registry-users-lob2,registry-admins - Creates 6 users for testing and management:
- LOB1:
lob1-bot(M2M service account) andlob1-user(human user) - LOB2:
lob2-bot(M2M service account) andlob2-user(human user) - Admin:
admin-bot(M2M service account) andadmin-user(human user)
- LOB1:
- Generates and saves OAuth credentials to
.oauth-tokens/directory
All user passwords default to the value set in your .env file (INITIAL_USER_PASSWORD).
Step 6: Access the registry
open http://localhost:7860Step 7: Create your first agent Complete: Create Your First AI Agent Account - Create agent credentials for testing
Step 8: Restart auth server to apply new credentials
docker-compose down auth-server && docker-compose rm -f auth-server && docker-compose up -d auth-serverStep 9: Test the setup Complete: Testing with mcp_client.py and agent.py - Validate your setup works correctly
Benefits: No build time • No Node.js required • No frontend compilation • Consistent tested images
New to MCP Gateway? Start with our Complete Setup Guide for detailed step-by-step instructions from scratch on AWS EC2.
Python Scripts:
./cli/mcp_client.py- Core MCP operations (ping, list tools, call tools)./tests/mcp_cmds.sh- Shell-based MCP testing operations
Python Agent:
agents/agent.py- Full-featured Python agent with advanced AI capabilities
Next Steps: Testing Guide | Complete Installation Guide | Authentication Setup | AI Assistant Integration
Transform how both autonomous AI agents and development teams access enterprise tools with centralized governance:
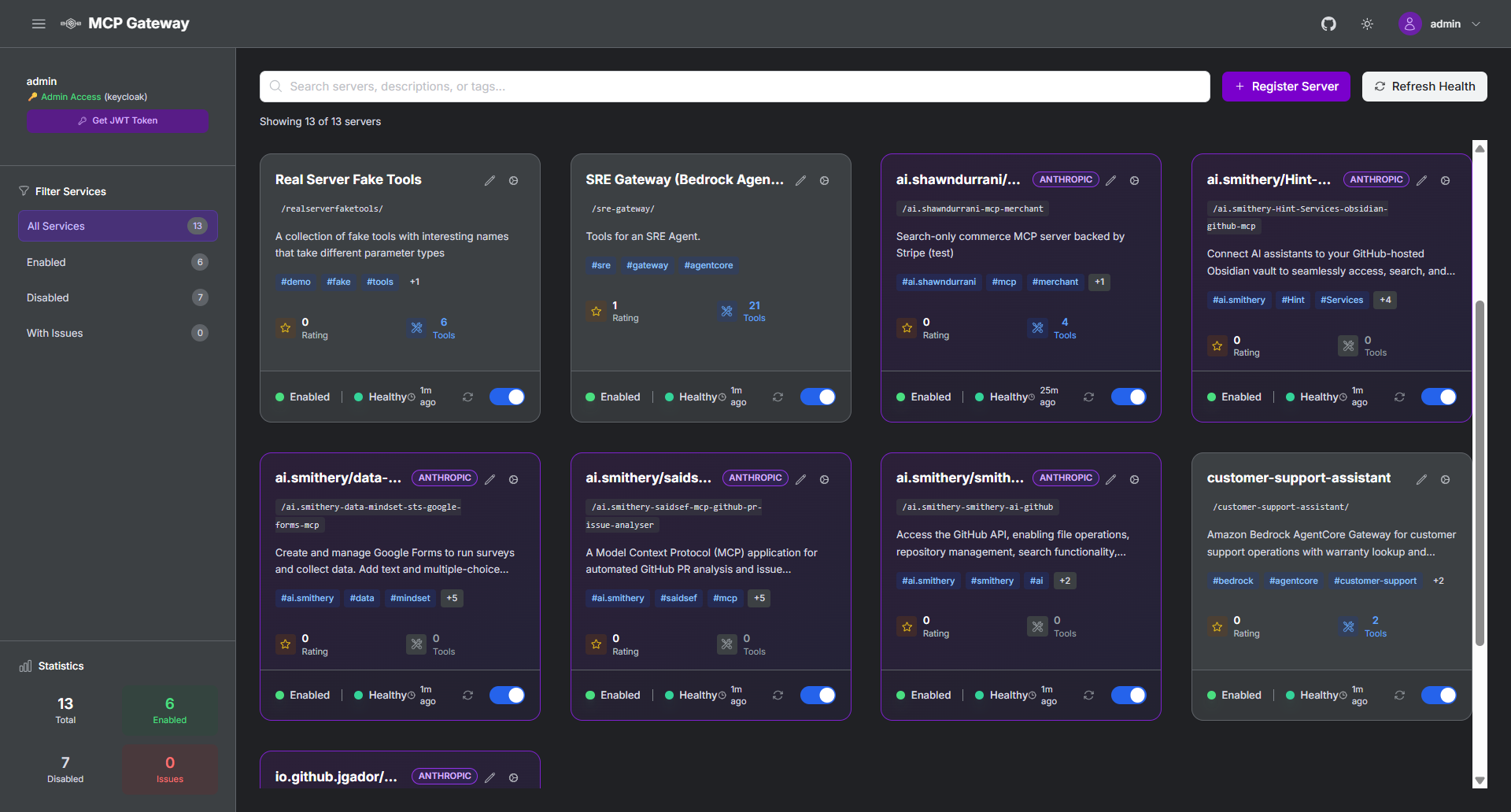
Enterprise-curated MCP servers accessible through unified gateway |
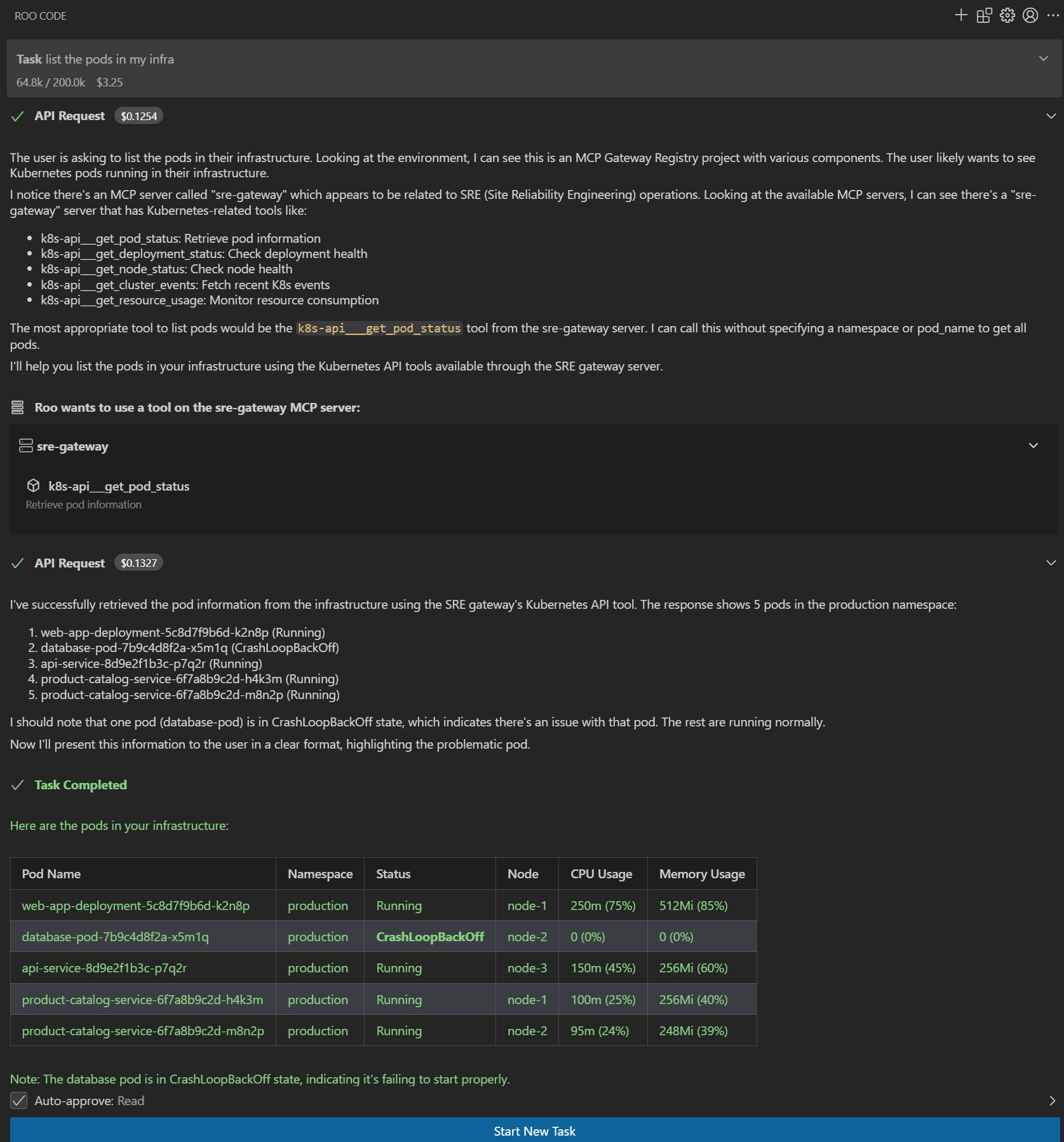
AI assistants executing approved enterprise tools with governance |
|
Comprehensive real-time metrics and monitoring through Grafana dashboards with dual-path storage: SQLite for detailed historical analysis and OpenTelemetry (OTEL) export for integration with Prometheus, CloudWatch, Datadog, and other monitoring platforms. Track authentication events, tool executions, discovery queries, and system performance metrics. Learn more 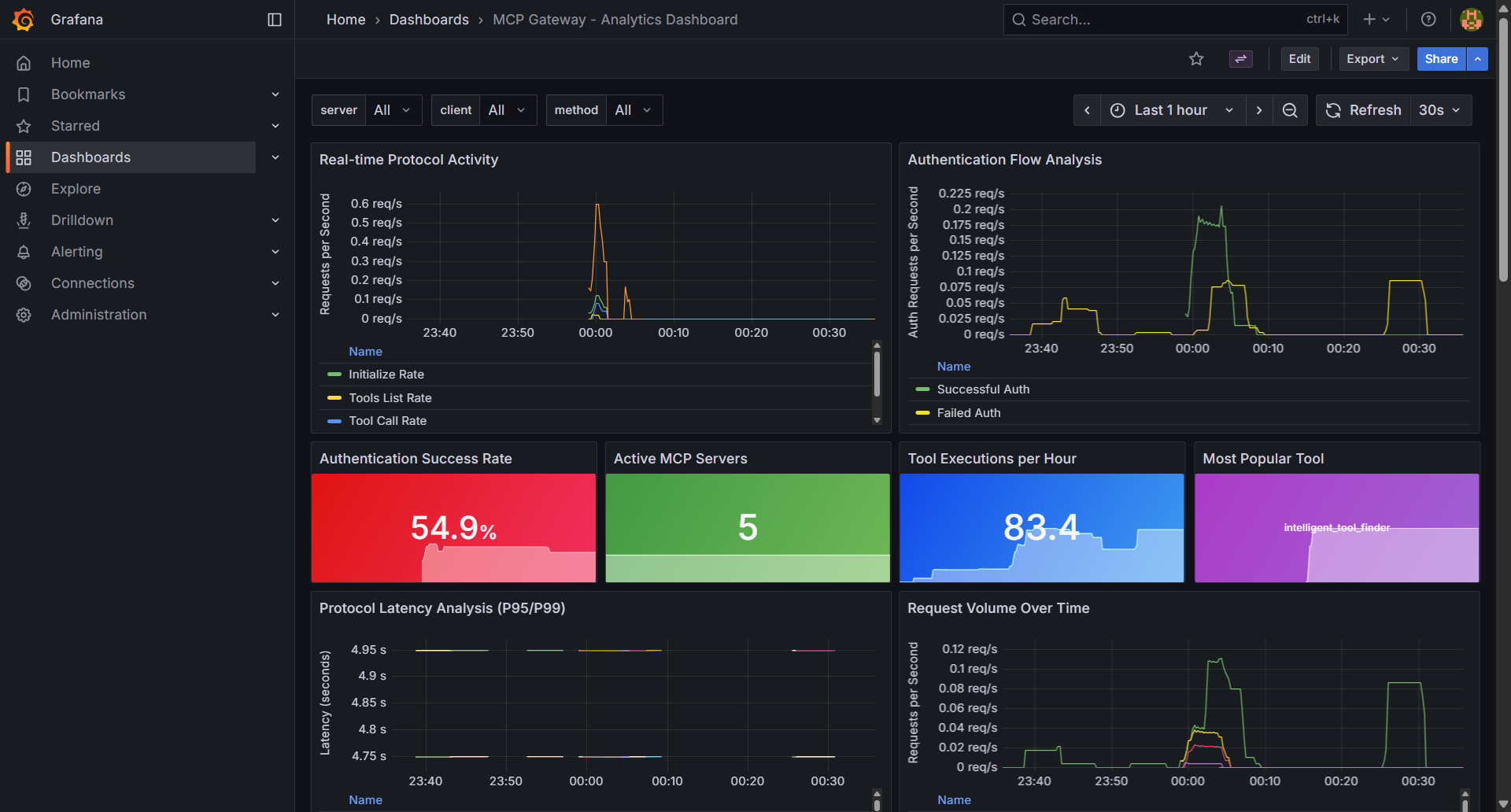
Real-time metrics and observability dashboard tracking server health, tool usage, and authentication events |
|
Seamlessly integrate with Anthropic's official MCP Registry to import and access curated MCP servers through your gateway:
- Import Servers: Select and import desired servers from Anthropic's registry with a single command
- Unified Access: Access imported servers through your gateway with centralized authentication and governance
- API Compatibility: Full support for Anthropic's Registry REST API specification - point your Anthropic API clients to this registry to discover available servers
Import and access curated MCP servers from Anthropic's official registry
Import Guide | Registry API Documentation
Integrated Vulnerability Detection:
- Automated Security Scanning - Integrated vulnerability scanning for MCP servers using Cisco AI Defence MCP Scanner, with automatic scans during registration and support for periodic registry-wide scans
- Detailed Security Reports - Comprehensive markdown reports with vulnerability details, severity assessments, and remediation recommendations
- Automatic Protection - Servers with security issues are automatically disabled with security-pending status to protect your infrastructure
- Compliance Ready - Security audit trails and vulnerability tracking for enterprise compliance requirements
Multiple Identity Modes:
- Machine-to-Machine (M2M) - For autonomous AI agents and automated systems
- Three-Legged OAuth (3LO) - For external service integration (Atlassian, Google, GitHub)
- Session-Based - For human developers using AI coding assistants and web interface
Supported Identity Providers: Keycloak, Amazon Cognito, and any OAuth 2.0 compatible provider. Learn more
Fine-Grained Permissions: Tool-level, method-level, team-based, and temporary access controls. Learn more
Cloud Platforms: Amazon EC2, Amazon EKS
| Getting Started | Enterprise Setup | Developer & Operations |
|---|---|---|
| Complete Setup Guide NEW! Step-by-step from scratch on AWS EC2 |
Authentication Guide OAuth and identity provider integration |
AI Coding Assistants Setup VS Code, Cursor, Claude Code integration |
| Installation Guide Complete setup instructions for EC2 and EKS |
Keycloak Integration Enterprise identity with agent audit trails |
API Reference Programmatic registry management |
| Quick Start Tutorial Get running in 5 minutes |
Amazon Cognito Setup Step-by-step IdP configuration |
Token Refresh Service Automated token refresh and lifecycle management |
| Configuration Reference Environment variables and settings |
Anthropic Registry Import NEW! Import servers from Anthropic MCP Registry |
Observability Guide NEW! Metrics, monitoring, and OpenTelemetry setup |
| Anthropic Registry API NEW! REST API compatibility |
Fine-Grained Access Control Permission management and security |
Dynamic Tool Discovery Autonomous agent capabilities |
| Service Management Server lifecycle and operations |
||
| Production Deployment Complete setup for production environments |
||
| Troubleshooting Guide Common issues and solutions |
Join the Discussion
- GitHub Discussions - Feature requests and general discussion
- GitHub Issues - Bug reports and feature requests
Contributing
- Contributing Guide - How to contribute code and documentation
- Code of Conduct - Community guidelines
- Security Policy - Responsible disclosure process
The following GitHub issues represent our current development roadmap and planned features:
Major Features
-
#203 - Deploy MCP Gateway Registry on AWS ECS Fargate 🚧 IN PROGRESS Comprehensive production-ready ECS deployment guide with multi-AZ architecture, auto-scaling, HTTPS/SSL, CloudWatch monitoring, and NAT Gateway HA. Complete Terraform configuration templates for deploying the entire stack on AWS.
-
#195 - Add A2A (Agent-to-Agent) Protocol Support to Registry ✅ COMPLETE Agents can now register, discover, and communicate with other agents through the secure registry. Full implementation includes agent lifecycle management, Keycloak-based access control, fine-grained permissions, comprehensive testing, and documentation. A2A Guide
-
#128 - Add Microsoft Entra ID (Azure AD) Authentication Provider 🚧 IN PROGRESS Extend authentication support beyond Keycloak to include Microsoft Entra ID integration. Enables enterprise SSO for organizations using Azure Active Directory.
-
#170 - Architectural Proposal: Separate Gateway and Registry Containers 🚧 IN PROGRESS Architectural enhancement to separate gateway and registry functionality into independent containers for improved scalability, maintainability, and deployment flexibility.
-
#129 - Virtual MCP Server Support - Dynamic Tool Aggregation and Intelligent Routing 🚧 IN PROGRESS Enable logical grouping of tools from multiple backend servers with intelligent routing using Lua/JavaScript scripting. Provides purpose-built virtual servers that abstract away backend complexity.
-
#118 - Agent-as-Tool Integration: Dynamic MCP Server Generation Convert existing AI agents into MCP servers dynamically, enabling legacy agent ecosystems to participate in the MCP protocol without code rewrites.
-
#121 - Migrate to OpenSearch for Server Storage and Vector Search Replace current storage with OpenSearch to provide advanced vector search capabilities and improved scalability for large server registries.
-
#98 - Complete GDPR and SOX Compliance Implementation Full compliance implementation for GDPR and SOX requirements, including data retention policies, audit trails, and privacy controls.
-
#39 - Tool Popularity Scoring and Rating System Enhance tool discovery with popularity scores and star ratings based on usage patterns and agent feedback.
DevOps & Operations
-
#48 - Update EKS Helm Chart for Multi-Container Architecture Update Helm charts to support the new multi-container Docker Compose architecture for Kubernetes deployments.
-
#70 - Docker Build & Runtime Performance Optimization Optimize Docker build times and runtime performance for faster development and deployment cycles.
Completed
-
#132 - Registry UI: Add MCP Configuration Generator ✅ COMPLETED Copy-paste MCP configuration generator added to Registry UI for seamless integration with AI coding assistants (VS Code, Cursor, Claude Code).
-
#171 - Feature: Import Servers from Anthropic MCP Registry ✅ COMPLETED Anthropic MCP Registry import functionality implemented. Import curated servers with a single command and access through the gateway with full REST API compatibility. Import Guide | API Documentation
-
#37 - Multi-Level Registry Support ✅ COMPLETED (Closed via #179, #181) Registry-to-registry integration now supported through Anthropic MCP Registry import, enabling federated server discovery and access across different registries.
-
#159 - Add scope management: create/delete Keycloak groups with scope configuration ✅ COMPLETED Dynamic scope management functionality implemented with create-group, delete-group, list-groups, and server-to-group assignment commands through service management CLI. Includes comprehensive user management with group-based access control. Service Management Guide
-
#160 - Documentation: Add Amazon Bedrock AgentCore Gateway integration example ✅ COMPLETED Comprehensive documentation and examples for integrating Amazon Bedrock AgentCore Gateway with dual authentication (Keycloak ingress + Cognito egress), passthrough token mode, and complete MCP protocol flow. Integration Guide
-
#158 - Replace /opt/mcp-gateway with ${HOME}/mcp-gateway to eliminate sudo requirements ✅ COMPLETED Installation experience improved by using user home directory instead of /opt, removing the need for sudo privileges during setup.
-
#111 - Standalone Metrics Collection Service ✅ COMPLETED Dedicated metrics collection service implemented for comprehensive monitoring and analytics across all MCP Gateway components. Documentation
-
#38 - Usage Metrics and Analytics System ✅ COMPLETED Comprehensive usage tracking implemented across user and agent identities, with metrics emission from auth server, registry, and intelligent tool finder. Documentation
-
#120 - CLI Tool for MCP Server Registration and Health Validation ✅ COMPLETED Command-line interface for automated server registration, health checks, and registry management. Streamlines DevOps workflows and CI/CD integration. Documentation
-
#119 - Implement Well-Known URL for MCP Server Discovery ✅ COMPLETED Standardized discovery mechanism using /.well-known/mcp-servers endpoint for automatic server detection and federation across organizations.
-
#18 - Add Token Vending Capability to Auth Server ✅ COMPLETED Auth server token vending capabilities implemented for enhanced authentication workflows with OAuth token management and service account provisioning.
-
#5 - Add Support for KeyCloak as IdP Provider ✅ COMPLETED KeyCloak integration implemented with individual agent audit trails, group-based authorization, and production-ready service account management. Documentation
For the complete list of open issues, feature requests, and bug reports, visit our GitHub Issues page.
This project is licensed under the Apache-2.0 License - see the LICENSE file for details.
⭐ Star this repository if it helps your organization!