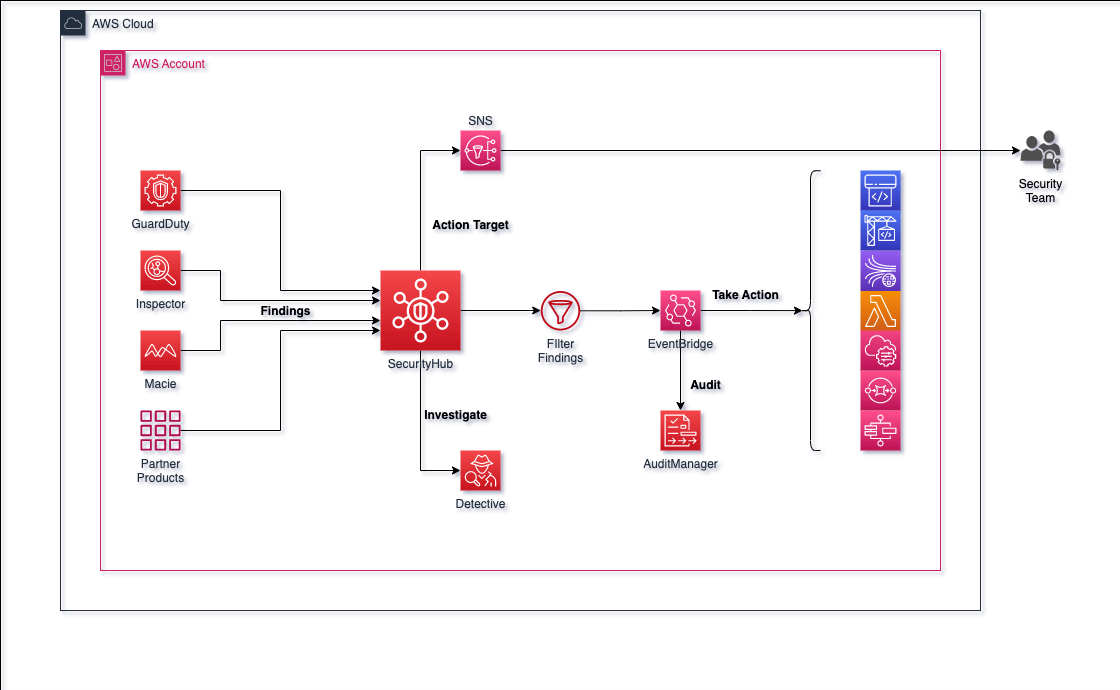
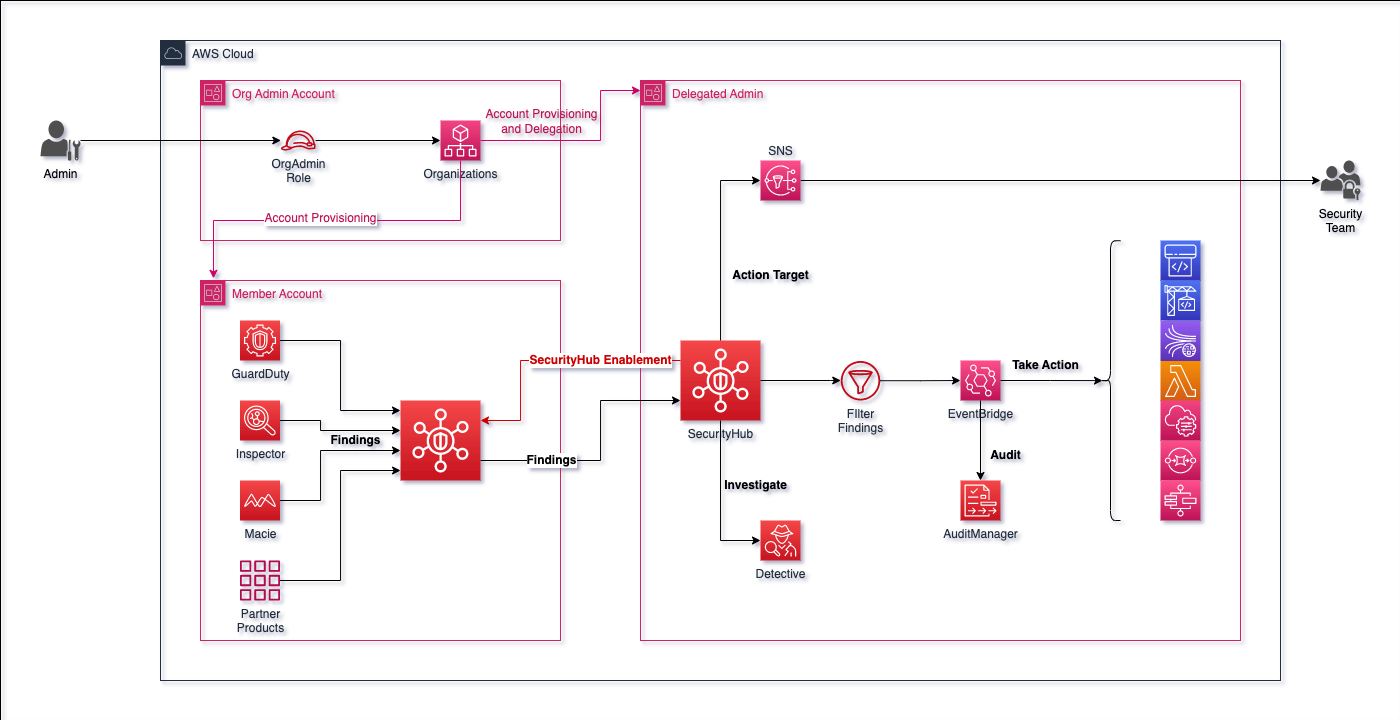
Terraform Module for AWS Security Hub Terraform module that creates AWS Security Hub resources.
module "security_hub" {
source = " ../../../" enable_default_standards = false
control_finding_generator = " STANDARD_CONTROL" auto_enable_controls = true
product_config = = true
arn = " arn:aws:securityhub:${ data . aws_region . current . name } ::product/aws/guardduty" standards_config = = {
enable = true
status = " ENABLED" = {
enable = false
}
cis_aws_foundations_benchmark_v140 = {
enable = true
status = " ENABLED" = {
enable = false
}
pci_dss = {
enable = false
}
}
action_target = = " Send to Amazon SNS" = " SendToSNS" = " This is a custom action to send findings to SNS Topic" resource "aws_securityhub_standards_control" "ensure_iam_password_policy_prevents_password_reuse" {
standards_control_arn = " arn:aws:securityhub:${ data . aws_region . current . name } :${ data . aws_caller_identity . current . account_id } :control/cis-aws-foundations-benchmark/v/1.4.0/1.10" control_status = " DISABLED" disabled_reason = " Password policies are managed by external resource" depends_on = module . security_hub ]
}
resource "aws_securityhub_insight" "this" {
filters {
created_at {
date_range {
unit = " DAYS" value = 7
}
}
network_source_ipv4 {
cidr = " 10.0.0.0/16" criticality {
gte = " 80" resource_tags {
comparison = " EQUALS" key = " Environment" value = " Development" group_by_attribute = " AwsAccountId" name = " insight" depends_on = module . standalone_security_hub ]
}module "delegated_admin" {
source = " aws-ia/terraform-aws-security-hub/aws//modules/organizations_admin/" admin_account_id = . aws_caller_identity . current . account_id
auto_enable_standards = " DEFAULT" depends_on = module . security_hub ]
}
module "member_account" {
source = " aws-ia/terraform-aws-security-hub/aws//modules/organizations_member/" providers = = aws
aws.member = aws.member
}
member_config = = " 281190191734" = " required@example.com" = false
}]
depends_on = module . security_hub ]
}
module "security_hub" {
source = " aws-ia/terraform-aws-security-hub" enable_default_standards = false
control_finding_generator = " STANDARD_CONTROL" auto_enable_controls = true
product_config = = true
arn = " arn:aws:securityhub:${ data . aws_region . current . name } ::product/aws/guardduty" standards_config = = {
enable = true
status = " ENABLED" = {
enable = false
}
cis_aws_foundations_benchmark_v140 = {
enable = true
status = " ENABLED" = {
enable = false
}
pci_dss = {
enable = false
}
}
action_target = = " Send to Amazon SNS" = " SendToSNS" = " This is a custom action to send findings to SNS Topic" resource "aws_securityhub_insight" "this" {
filters {
aws_account_id {
comparison = " EQUALS" value = " 123456789012" aws_account_id {
comparison = " EQUALS" value = " 098765432109" created_at {
date_range {
unit = " DAYS" value = 7
}
}
network_source_ipv4 {
cidr = " 10.0.0.0/16" criticality {
gte = " 80" resource_tags {
comparison = " EQUALS" key = " Environment" value = " Development" group_by_attribute = " AwsAccountId" name = " insight-per-account-id" depends_on = module . security_hub ]
}
Name
Version
aws >= 4.47
time >= 0.9
No modules.
Name
Description
Type
Default
Required
action_target Creates Security Hub custom action.name - The description for the custom action target.identifier - The ID for the custom action target.description - The name of the custom action target.
list(object({ []no
auto_enable_controls Whether to automatically enable new controls when they are added to standards that are enabled. By default, this is set to true, and new controls are enabled automatically. To not automatically enable new controls, set this to false.
booltrueno
control_finding_generator Updates whether the calling account has consolidated control findings turned on. If the value for this field is set to SECURITY_CONTROL, Security Hub generates a single finding for a control check even when the check applies to multiple enabled standards. If the value for this field is set to STANDARD_CONTROL, Security Hub generates separate findings for a control check when the check applies to multiple enabled standards. For accounts that are part of an organization, this value can only be updated in the administrator account.
string"STANDARD_CONTROL"no
enable_default_standards Whether to enable the security standards that Security Hub has designated as automatically enabled including: AWS Foundational Security Best Practices v1.0.0 and CIS AWS Foundations Benchmark v1.2.0. Defaults to true.
booltrueno
linking_mode Indicates whether to aggregate findings from all of the available Regions or from a specified list. The options are ALL_REGIONS, ALL_REGIONS_EXCEPT_SPECIFIED or SPECIFIED_REGIONS. When ALL_REGIONS or ALL_REGIONS_EXCEPT_SPECIFIED are used, Security Hub will automatically aggregate findings from new Regions as Security Hub supports them and you opt into them.
string"ALL_REGIONS"no
product_config The ARN of the product that generates findings that you want to import into Security Hub.
list(object({ nullno
specified_regions List of regions to include or exclude (required if linking_mode is set to ALL_REGIONS_EXCEPT_SPECIFIED or SPECIFIED_REGIONS)
list(string)nullno
standards_config aws_foundational_security_best_practices - AWS Foundational Security Best Practicescis_aws_foundations_benchmark_v120 - CIS AWS Foundations Benchmark v1.2.0cis_aws_foundations_benchmark_v140 - CIS AWS Foundations Benchmark v1.4.0nist_sp_800_53_rev5 - NIST SP 800-53 Rev. 5pci_dss - PCI DSSobject({ { no