This terraform module creates all the necessary resources in AWS for highly scalable munki web setup using AWS S3 for object storage and AWS CloudFront (CDN) for content distribution. You can optionally secure the CDN via signed URLs so only clients that have your signing certificate can download content.
- High Level Features
- Versions
- Terraform Usage
- CloudFront signing key
- SNS Alerts
- Lambda Notes
- Inputs
- Outputs
Currently server side makecatalogs via the s3 Repo Plugin does not function with python3 and munki version 4+. I recommend you keep server_side_makecatalogs set to false.
- Restrictions on the S3 bucket to disallow any direct connections
- Use a custom DNS name for the web server or use a supplied URL from AWS
Rebuild the catalog files whenever a pkginfo file or icon is updated or modifiedSee Note above- Only pay for what you use
- Optional SNS Alert when a warning or error happen during
makecatalogrun - Custom TTL values for assets
- Baisc Auth and Cert Based ACL controls
At this time, it is impossible to supply your own lambda payload as such you are stuck on the following versions.
module "munki-service" {
source = "git@github.com:clburlison/terraform-munki.git?ref=v1.1.0"
s3_bucket_name = "megacorp-munki-repo"
tags = {
Environment = "prod"
BusinessUnit = "ClientABC"
}
}
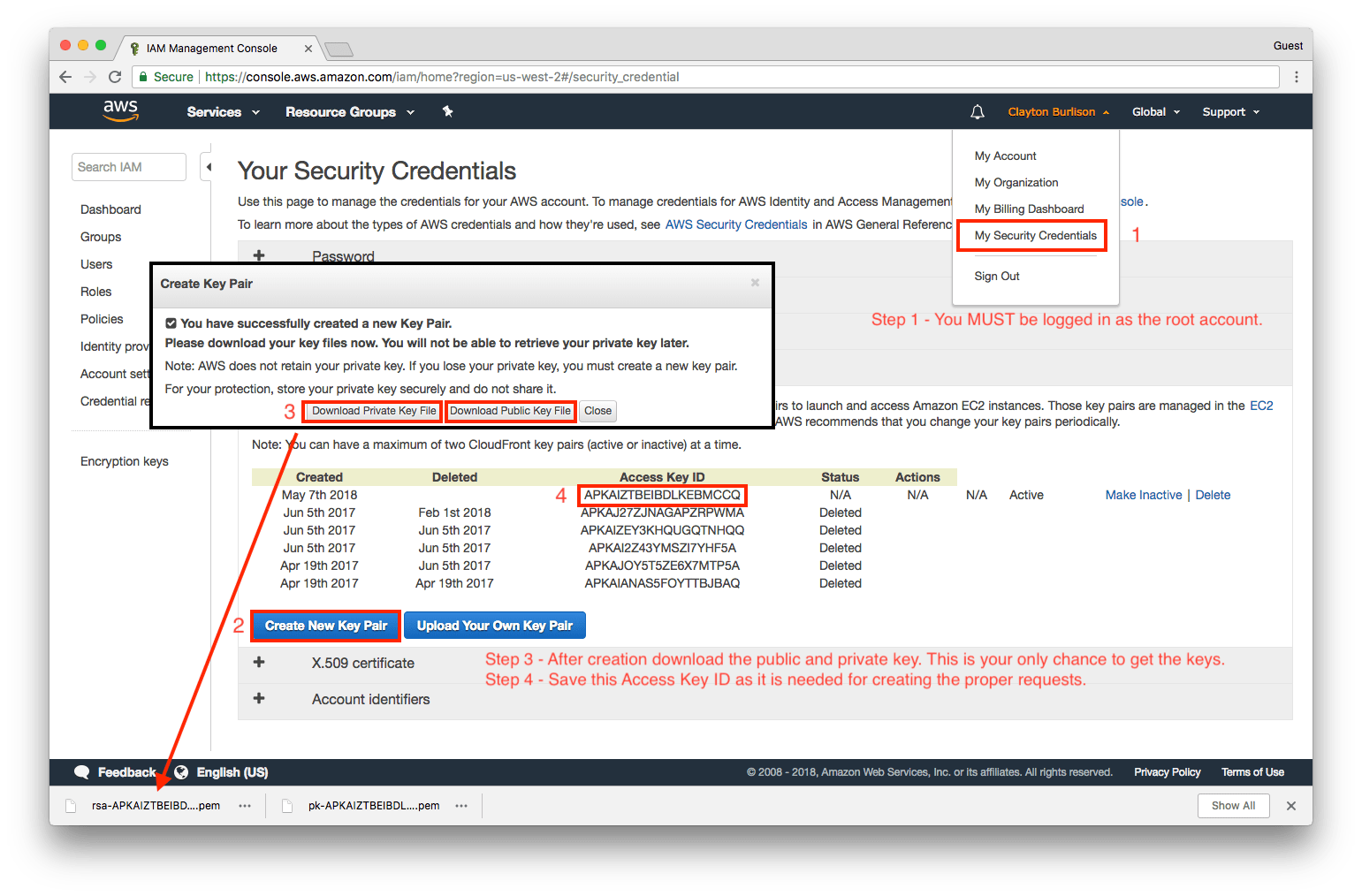
For additional instructions please checkout the [examples](./examples) directory.The CloudFront signing key can not be automatically created. This key can also only be created by the root account owner, administrator IAM users will not work.
The creation process can be followed in the following Amazon doc:
To create CloudFront key pairs
or via the following graphic:
Terraform is unable to create and validate Simple Notification Service (SNS) resources so a topic and subscription must be created manually. The following steps will guide you through an email alert:
- Log into the AWS Console
- Go to the Simple Notification Service (SNS) service
- Create a new topic
- Click on the created topic ARN to go to the details page
- Create a subscription
- Select the protocol and options you want
- Confirm the subscription (required for the email protocol)
- Copy the Topic ARN from this page and use in the terraform
alarm_arnvariable
The lambda_makecatalogs.py file runs as a AWS Lambda function. It is
triggered from the following s3 events:
- a file under pkginfo/ is modified or uploaded
- a file under icons/ with the extensions of the
.pngor.jpgis modified or uploaded
If this setup is destroyed and recreated the 'munki-s3-rw' policy will need to be re-applied to the 'munki_s3' user.
| Name | Version |
|---|---|
| terraform | >= 0.12 |
| Name | Version |
|---|---|
| archive | 2.2.0 |
| aws | 5.0 |
No modules.
| Name | Description | Type | Default | Required |
|---|---|---|---|---|
| alarm_arn | The arn to send alerts to on lambda errors and warnings | string |
"" |
no |
| basic_auth_password | Password for munki basic auth | string |
"" |
no |
| basic_auth_user | Username for munki basic auth | string |
"" |
no |
| catalogs_ordered_cache_behavior_default_ttl | The default amount of time (in seconds) that a catalog object is in a CloudFront cache before CloudFront forwards another request in the absence of an Cache-Control max-age or Expires header. | number |
30 |
no |
| catalogs_ordered_cache_behavior_max_ttl | The maximum amount of time (in seconds) that a catalog object is in a CloudFront cache before CloudFront forwards another request to your origin to determine whether the object has been updated. | number |
60 |
no |
| catalogs_ordered_cache_behavior_min_ttl | The minimum amount of time (in seconds) that you want catalog objects to stay in CloudFront caches before CloudFront queries your origin to see whether the object has been updated. | number |
0 |
no |
| cf_default_certificate | true if you want viewers to use HTTPS to request your objects and you're using the CloudFront domain name for your distribution. Specify this, cf_acm_certificate_arn, or cf_iam_certificate_id | string |
"true" |
no |
| cf_dns_aliases | Optionally a list of dns aliases to assign to the CloudFront distribution point | list(string) |
[] |
no |
| cf_minimum_protocol_version | The minimum version of the SSL protocol that you want CloudFront to use for HTTPS connections. One of SSLv3, TLSv1, TLSv1_2016, TLSv1.1_2016 or TLSv1.2_2018 | string |
"TLSv1.2_2018" |
no |
| cf_price_class | The CloudFront pricing tier. One of PriceClass_All, PriceClass_200, PriceClass_100 | string |
"PriceClass_All" |
no |
| cf_ssl_cert_arn | The ARN of the AWS Certificate Manager certificate to use. Specify this, cf_cloudfront_default_certificate, or cf_iam_certificate_id. The ACM certificate must be in US-EAST-1 | string |
"" |
no |
| cf_ssl_support_method | Specifies how you want CloudFront to serve HTTPS requests. Required if you specify acm_certificate_arn. One of vip or sni-only. vip is $600 a month don't select that option! | string |
"" |
no |
| cf_trusted_signers | The AWS accounts, if any, that you want to allow to create signed URLs for private content. Use ['self'] if you want to target the account that owns this CloudFront distribution point | list(string) |
[] |
no |
| default_cache_behavior_default_ttl | The default amount of time (in seconds) that an object is in a CloudFront cache before CloudFront forwards another request in the absence of an Cache-Control max-age or Expires header. | number |
86400 |
no |
| default_cache_behavior_max_ttl | The maximum amount of time (in seconds) that an object is in a CloudFront cache before CloudFront forwards another request to your origin to determine whether the object has been updated. | number |
31536000 |
no |
| default_cache_behavior_min_ttl | The minimum amount of time (in seconds) that you want objects to stay in CloudFront caches before CloudFront queries your origin to see whether the object has been updated. | number |
0 |
no |
| enable_icons_basic_auth | When set to 'true' the resource will enable basic auth for icons/ subpath | bool |
true |
no |
| icons_ordered_cache_behavior_default_ttl | The default amount of time (in seconds) that a icon object is in a CloudFront cache before CloudFront forwards another request in the absence of an Cache-Control max-age or Expires header. | number |
30 |
no |
| icons_ordered_cache_behavior_max_ttl | The maximum amount of time (in seconds) that a icon object is in a CloudFront cache before CloudFront forwards another request to your origin to determine whether the object has been updated. | number |
60 |
no |
| icons_ordered_cache_behavior_min_ttl | The minimum amount of time (in seconds) that you want icon objects to stay in CloudFront caches before CloudFront queries your origin to see whether the object has been updated. | number |
0 |
no |
| manifests_ordered_cache_behavior_default_ttl | The default amount of time (in seconds) that a manifest object is in a CloudFront cache before CloudFront forwards another request in the absence of an Cache-Control max-age or Expires header. | number |
30 |
no |
| manifests_ordered_cache_behavior_max_ttl | The maximum amount of time (in seconds) that a manifest object is in a CloudFront cache before CloudFront forwards another request to your origin to determine whether the object has been updated. | number |
60 |
no |
| manifests_ordered_cache_behavior_min_ttl | The minimum amount of time (in seconds) that you want manifest objects to stay in CloudFront caches before CloudFront queries your origin to see whether the object has been updated. | number |
0 |
no |
| name | Name to be used on all resources as the identifier | string |
"munki" |
no |
| s3_bucket_create | Set to true to create a new s3 bucket. If false you can reuse a current bucket | bool |
true |
no |
| s3_bucket_name | The s3 bucket name to use | any |
n/a | yes |
| s3_encryption_enabled | When set to 'true' the resource will have aes256 encryption enabled by default | bool |
true |
no |
| server_side_makecatalogs | Set to true to enable server side makecatalogs when s3 bucket changes happen | bool |
false |
no |
| tags | A map of tags to add to all resources | map(string) |
{} |
no |
| Name | Description |
|---|---|
| cf_domain_name | The cloudfront distribution point domain name |
| cf_hosted_zone_id | The cloudfront distribution point zone id |