Automation of IT related tasks
This playbook uses Ansible Vaults. The password file, GPG encryped and shared amongst Le Détour admins by an out-of-band mean of communication, is expected to be named .vault_password.gpg in this cloned repo root folder.
Install community package for creating and using roles:
ansible-galaxy collection install -r requirements.yml
# TODO: When Ansible 2.10 is released, this should be enough
# ansible-galaxy install -r requirements.ymlServers and workstations are linked together by a wireguard network. To generate a wireguard config for a given workstation, execute ansible on a local connection and set its limit to the targeted workstation:
ansible-playbook playbook.yml --connection local --limit the-workstation-nameThis will create a wg-ledetour.conf-the-workstation-name in the same directy as playbook.yml. Check the output for ansible for info on how to use that file:
...
TASK [wireguard : Wireguard info] ***************************************************************************
ok: [charles-xps15] => {
"msg": [
"Created wireguard config file wg-ledetour.conf-charles-xps15",
"Install it as root with `mv wg-ledetour.conf-charles-xps15 /etc/wireguard/wg-ledetour.conf`",
"Activate wireguard with:",
"- Either directly with wg-quick `wg-quick up wg-ledetour`",
"- Or with systemd `sysemctl start wg-quick@wg-ledetour.service`",
"Don't forget to open your firewall: UDP outbound port 51820"
]
}
...
ansible-playbook playbook.ymlThis playbook.yml will setup all machines described in hosts according to the configuration described in /roles.
- Install debian 10 (buster)
- Full disk encryption
- Add a single user
debian - Ensure openssh server is running
ssh-copy-idfor the user / machine ansible will be ran from- Install
sudo:apt install sudo - Configure user
debianfor passwordless sudo. Create a new file/etc/sudoers.d/adminwith this content:debian ALL = NOPASSWD: ALL - Run ansible against a first time with the LAN IP of the machine. This will bootstrap the Wireguard connection that will be used by default next time:
ansible-playbook -e "ansible_host=[LAN IP] ansible_user=debian" playbook.yml --limit [hostname], for exampleansible-playbook -e "ansible_user=debian ansible_host=192.168.1.42" playbook.yml --limit laptopserver - The machine is likely to reboot on first ansible run: be ready to enter disk decryption keys
# Encrypt the secret file
ansible-vault encrypt --vault-id @prompt secret.yml
# View the content of the secret file, will ask for password
ansible-vault view secret.yml
# Decrypt the content of the secret file, will ask for password
ansible-vault decrypt secret.ymlAnsible should have installed and configured wireguard automatically.
However, if you would like to configure it manually:
# TODO: use Ansible to only generate the wg config file
# Install wireguard for your Linux distribution
sudo apt install wg
# Setup the connection using the config file generated by 'ansible-playbook playbook.yml' at /etc/wireguard/wg-ledetour.conf
sudo wg-quick up wg-ledetour
#Confirm your virtual interface and peers are setup
sudo wg showYou can now ping other machines in the vpn according to the IPs specified in the file hosts.
If Ansible has added your public ssh keys to other machines in the wireguard network, you can now ssh into them using the username specified in the file hosts.
A Vagrant virtual machine can be used during development to safely test new configurations without modifying the production servers.
# Creates and run the virtual machines
vagrant up
# Run the Ansible playbook on the Vagrant virtual machine
vagrant provisionsudo grep sshd /var/log/auth.logw
12:42:14 up 1 min, 1 user, load average: 0.06, 0.04, 0.01
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
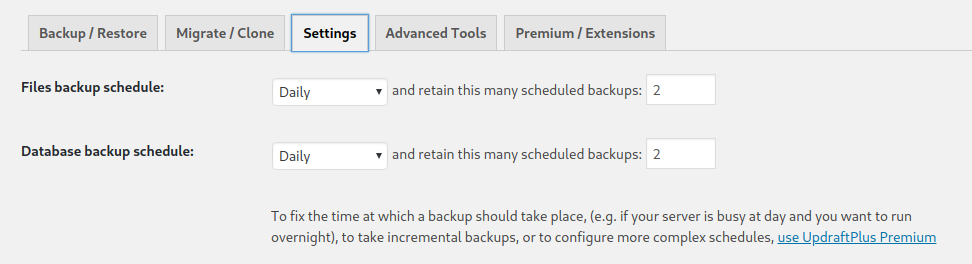
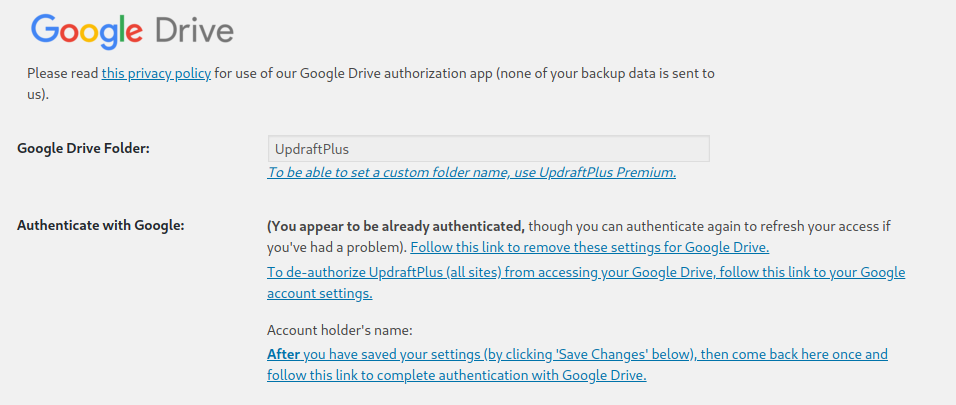
vagrant pts/0 10.0.2.2 12:41 1.00s 0.07s 0.00s wThe plugin used for backups of the wordpress documents and databases is UpDraftPlus. To change the google drive recipient account of the wordpress backups. You may go to the settings page.
Go to the settings tab showed below
Scroll down until you reach the Google Drive section