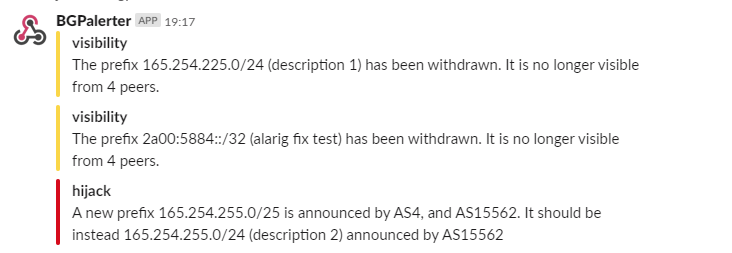
Self-configuring BGP monitoring tool, which allows you to monitor in real-time if:
- any of your prefixes loses visibility;
- any of your prefixes is hijacked;
- your AS is announcing RPKI invalid prefixes (e.g. not matching prefix length);
- your AS is announcing prefixes not covered by a ROAs;
- your AS is announcing a new prefix that was never announced before;
- one of the AS path used to reach your prefix matches a specific condition defined by you.
You just run it. You don't need to provide any data source or connect it to anything in your network since it connects to public repos.
It can deliver alerts on files, by email, on slack, and more.
BGPalerter connects to public BGP data repos (not managed by NTT) and the entire monitoring is done directly in the application (there are no NTT servers involved).
This section is useful if you don't care about the source code but you just want to run the monitor. Instead, if you want to run the source code (which is completely open) or develop, please read directly the documentation.
-
Download the binary here (be sure to select the one for your OS)
-
Execute the binary (e.g.
chmod +x bgpalerter-linux-x64 && ./bgpalerter-linux-x64)
The first time you run it, the auto-configuration will start.
If something happens (e.g. a hijack) you will see the alerts in logs/reports-YYYY-MM-DD.log.
In config.yml you can find other reporting mechanisms (e.g. email, Slack, Kafka) in addition to logging on files.
Please uncomment the related section and configure according to your needs.
If the installation doesn't go smoothly, read here.
Read the documentation below for more options.
- Installation
- Monitored prefixes list
- Configuration
- Update to latest version
- More information for developers
- BGPalerter for researchers
- Release process and Git flow
If you are using BGPalerter, feel free to sign here: Who is using BGPalerter