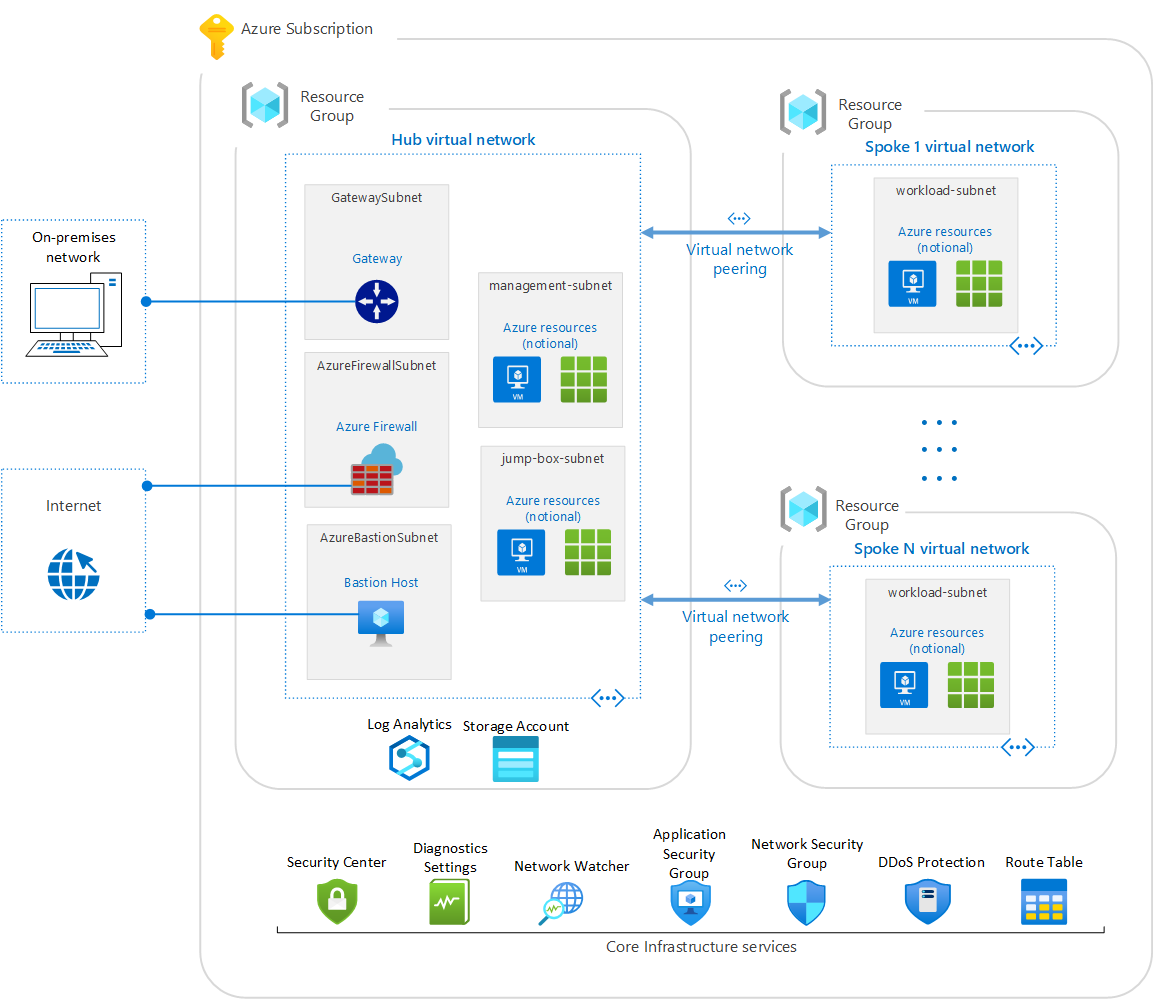
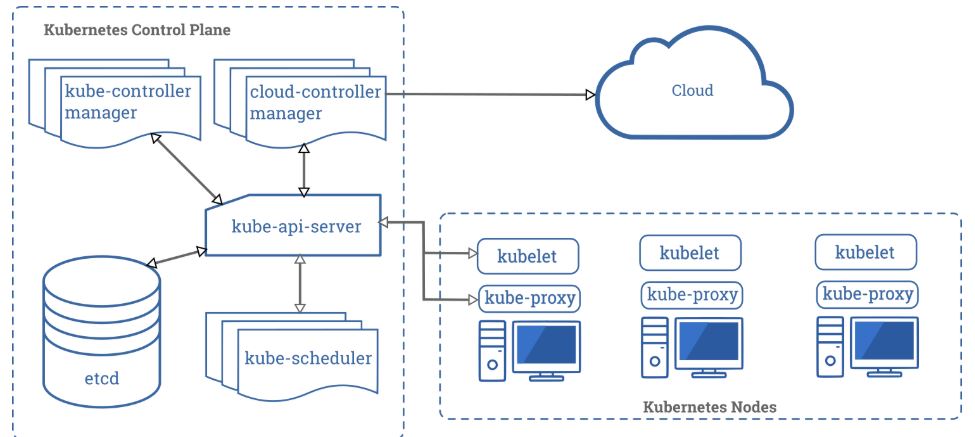
Cloud security is a vital aspect of protecting sensitive data and information stored in the cloud. It involves the use of various security measures and technologies to protect against unauthorized access, data breaches, and other cyber threats.
Encyclopedia is an excellent way to stay informed about the latest developments in cloud security. Many experts in the field publish regular updates on new technologies, best practices, and emerging threats. Some popular topics that are commonly discussed in cloud security blogs include:
Encryption and data protection: This includes the use of encryption to secure data in transit and at rest, as well as the use of secure key management systems.
Identity and access management: This involves the use of identity and access management (IAM) solutions to control access to cloud resources and ensure that only authorized users can access sensitive data.
Compliance and regulatory requirements: Many organizations must comply with various laws and regulations that govern the handling of sensitive data. Cloud security blogs often provide guidance on how to meet these requirements.
Cloud security best practices: Many blogs offer practical tips and advice on how to improve cloud security, such as implementing multi-factor authentication, monitoring for suspicious activity, and implementing regular security audits.
Cloud security threats and trends: As cyber threats continue to evolve, cloud security blogs keep readers informed about the latest trends and threats, such as the rise of cloud-native threats, IoT security challenges, and the increasing use of artificial intelligence and machine learning in cyber attacks.
-
API Secure: Fortifying Your Kubernetes API Server Against Cyber Threats
-
Building a Fortress in a Container: How to Create a Secure Kubernetes Image
-
How to Log and Monitor Events in Your Kubernetes Cluster - Part 1
-
How to Log and Monitor Events in Your Kubernetes Cluster - Part 2
-
Kubelet Security: Protecting the Heart of Your Kubernetes Cluster
-
AKS - Upgrading Kubernetes to the Latest Version - An Important Step Toward Kubernetes Security
-
Azure Kubernetes Service: Keep Your Runtime Secure with These Proven Tips - Part 1
-
Azure Kubernetes Service: Keep Your Runtime Secure with These Proven Tips - Part 2
-
Diving Deep: An In-Depth Look at Securing Your Azure Kubernetes Service
-
EKS - Upgrading Kubernetes to the Latest Version - An Important Step Toward Kubernetes Security
-
Elevate Your AKS Security: Boosting Authentication and Authorization - Part 1
-
Elevate Your AKS Security: Boosting Authentication and Authorization - Part 2
-
Elevate Your AKS Security: Boosting Authentication and Authorization - Part 3
-
Kuber-Proofing: Secure Your Pods with These Proven Tips for Configuring a Security Context - Part 1
-
Kuber-Proofing: Secure Your Pods with These Proven Tips for Configuring a Security Context - Part 2
-
Kuber-Proofing: Secure Your Pods with These Proven Tips for Configuring a Security Context - Part 3
-
Kuber-Safe: Secure Your Deployment with These Proven Best Practices for Kubernetes Security - Part 1
-
Kuber-Safe: Secure Your Deployment with These Proven Best Practices for Kubernetes Security - Part 2
-
Kuber-Secrets: 5 Proven Tips for Securing Your Kubernetes Clusters
-
Kuber-locking Down Your Cluster: A Guide to Securing Your Kubernetes Environment - Part 1
-
Kuber-locking Down Your Cluster: A Guide to Securing Your Kubernetes Environment - Part 2
-
Kubernetes DevSecOps: Navigating Vulnerabilities and Implementing Best Practices - Part 1
-
Kubernetes DevSecOps: Navigating Vulnerabilities and Implementing Best Practices - Part 2
-
Kubernetes DevSecOps: Navigating Vulnerabilities and Implementing Best Practices - Part 3
-
Protect Your Amazon EKS Cluster with CNCF Falco's Proven Runtime Security Techniques - Part 1
-
Protect Your Amazon EKS Cluster with CNCF Falco's Proven Runtime Security Techniques - Part 2
-
Protect Your Amazon EKS Cluster with CNCF Falco's Proven Runtime Security Techniques - Part 3
-
Protect Your Amazon EKS Cluster with CNCF Falco's Proven Runtime Security Techniques - Part 4
-
Securing the Foundation: Implementing Baseline Security for Azure Kubernetes Service (AKS)
AWS, Azure, GCP and Kubernetes Basic Knowledge
- Kubernetes Security Misconfiguration ETCD Controller Manager Kube API Server Scheduler
- Kubernetes Security Misconfiguration Ingress Egress Controller
- Kubernetes Security Misconfiguration Networking Controls
- AWS Kubernetes CIS Security Script
- Azure Kubernetes CIS Security Script
- GCP Kubernetes CIS Security Script
- Kubernetes CIS Security Script
- Kubernetes Benchmark Security Script
I have an experience of 13 years in Information Security, DevSecOps, Web, Cloud, Network Penetration Testing, Vulnerability Assessment, Red Teaming Activities(Mitre Attack Simulation), SAST, DAST, OWASP TOP 10, SANS 25, Active Bug Bounty Hunter and Cloud Security(AWS) in the Fintech and Crypto Regulation Space. I have written three books: Bounty Security Hack(Published in Amazon), API Security Bundle & CyberSecurity for CISO/CTO/CIO(Published in Amazon). I have got "Hall of Fame" from Microsoft (4 times), UpWork, Intel, Samsung, Indeed, Netflix, Seagate, Paypal, and Jet Airways. I have total five cloud security certifications: Certified Cloud Security Professional as AWS Certified Specialist, GCP Security Specialist Certified, CKA, CKS and OHCE (OFFENSIVE HACKING CERTIFIED EXPERT) from GCSRT.
If you have any feedback, please reach out to us at goyalvartul@gmail.com