(This tool is under development phase. We appreciate your patience.)
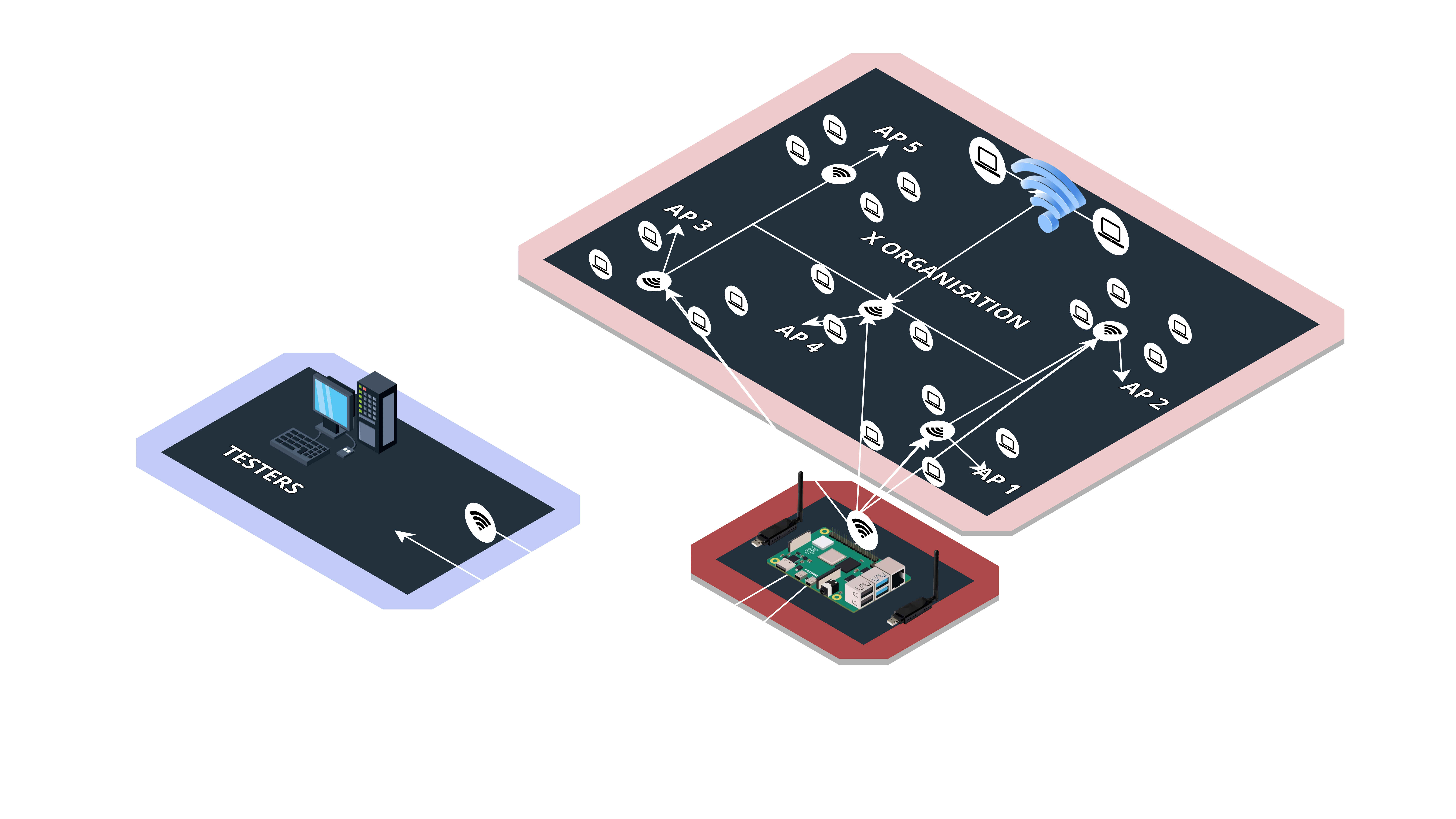
AIR SPECTER is a hardware tool designed using a Raspberry Pi 3+ model and an external NIC card. It is developed with the objective of creating a rogue access point (AP) to compromise Wi-Fi networks and perform network traffic monitoring and manipulation. The tool aims to gain unauthorized access to sensitive information and systems connected within the target organization's network.
The key features and functionality of the AIR SPECTER tool include:
-
Rogue AP Creation: AIR SPECTER is capable of emulating a legitimate Wi-Fi network, creating a rogue access point that appears genuine to lure unsuspecting users.
-
Network Traffic Monitoring: The tool intercepts and captures network traffic passing through the rogue AP, enabling the monitoring of packets exchanged between users and servers.
-
Packet Analysis: AIR SPECTER analyzes the intercepted network packets, examining packet headers and payloads to identify potential vulnerabilities, sensitive information, and security weaknesses.
-
Vulnerability Assessment: The tool assesses the security vulnerabilities present in the intercepted network traffic, providing insights into weak encryption protocols, insecure authentication mechanisms, and misconfigured devices within the target network.
-
Packet Manipulation: AIR SPECTER allows for the manipulation of network packets, enabling simulation of attacks and modification of packet content to test the network's resilience against specific threats.
-
Data Extraction: The tool focuses on extracting sensitive information from the intercepted network traffic, such as login credentials, personal data, or any other valuable information that can be exploited for unauthorized access.
-
Countermeasures: The tool suggests countermeasures and security enhancements for the target network, providing recommendations to address identified vulnerabilities, strengthen network security, and prevent future attacks by scanning vulnerable areas inside network.
To utilize AIR SPECTER, the following hardware and software requirements are necessary:
- Raspberry Pi 3+ model
- External network interface card (NIC) for wireless communication and monitor mode support
- Power supply, SD card, HDMI display, keyboard, and mouse for Raspberry Pi setup
- Operating system compatible with Raspberry Pi(kali linux, raspberry os)
The AIR SPECTER tool operates within the following overall system architecture:
AIR SPECTER is a powerful tool designed to compromise Wi-Fi networks, intercept network traffic, and gain unauthorized access to sensitive information. It provides advanced functionalities for packet analysis, vulnerability assessment, packet manipulation, data extraction, and countermeasure recommendations. By utilizing this tool responsibly, organizations can enhance their network security by identifying and addressing potential vulnerabilities.