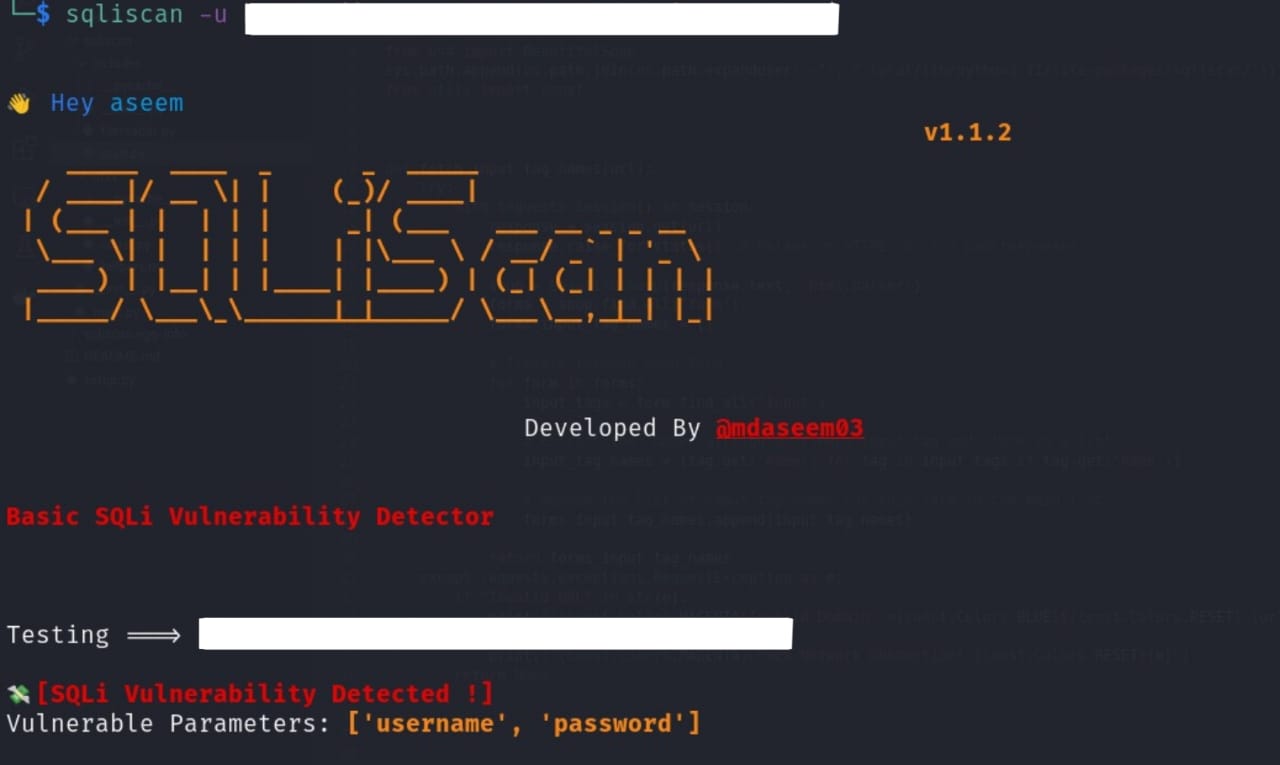
sqliscan is a simple Python tool designed for detecting SQL injection vulnerabilities in web applications.
- URL Scanning: Identifies and scans for SQL injection vulnerabilities in a provided URL.
- File Input: Supports scanning multiple URLs by reading them from a file.
- Payload Testing: Sends crafted payload to web forms to detect potential SQL injection vulnerabilities.
- Command-Line Interface: Easy-to-use command-line interface for scanning.
Before using sqliscan, make sure you have the following prerequisites installed:
-
Python 3.x: Ensure you have Python 3.x installed on your system. Download Python
-
Required Python Packages: Install the required Python packages using the following commands:
pip install click pip install requests pip install beautifulsoup4
pip install sqliscan
sudo cp ~/.local/bin/sqliscan /usr/bin -u, --url URL to scan sqliscan -u https://target.com
-i, --input <filename> Read input from txt sqliscan -i target.txt
-h, --help Help Menu
-
u, --url:Specify the URL to scan for the SQLi vulnerability. Example: sqliscan -u https://target.com -
i, --input:Read input URLs from a file. Example: sqliscan -i target.txt -
h, --help:Display the help menu.
This script is intended for educational and ethical purposes only. Unauthorized use of this script to perform malicious activities is strictly prohibited. The developers are not responsible for any misuse or damage caused by this script.
v1.0: Find SQLi Vulnerabilities in forms by using basic payloadv1.1: Fixed import module issuesv1.1.1: Fixed Bugsv1.1.2: Fixed Bugsv1.2: Finds SQLi in GET parameters from url