A simple demonstration to use User Assigned Identity with Azure MySQL for secure authentication
We will create two identities, one for administring the SQL users(aka control plane) and for interacting with the database and the data(ie. data plane operations)
-
This demo, along with its instructions, scripts, and Bicep template, has been specifically designed to be executed in the
northeuroperegion. However, with minimal modifications, you can also try running it in other regions of your choice (the specific steps for doing so are not covered in this context)- 🛠 Azure CLI Installed & Configured - Get help here
- 🛠 Azure Function Core Tools - Get help here
- 🛠 Bicep Installed & Configured - Get help here
- 🛠 [Optional] VS Code & Bicep Extenstions - Get help here
jq- Get help herebashor git bash - Get help here
-
-
Get the application code
git clone https://github.com/miztiik/azure-web-server-to-mysql.git cd azure-web-server-to-mysql
-
-
Ensure you have jq, Azure Cli and bicep working
jq --version func --version bicep --version bash --version az account show
-
-
Stack: Main Bicep The params required for the modules are in
params.json. Modify them as needed. The helper deployment scriptdeploy.shwill deploy themain.bicepfile. This will create the following resoureces- Resource Group(RG)
- VNet, Subnet & Virtual Machine
- Virtual Machine(Ubuntu) -
1- Defined inparams.jsonnamedvmCount- Bootstrapped with custom libs using
userDatascript - Installs Nginx - Install Azure Monitoring Agent
- Bootstrapped with custom libs using
- User Managed Identity - Identity attached to the VM with the following permissions,
- Monitoring Metrics Publisher
- SQL Admin User Managed Identity - Identity attached to the VM with the following permissions,
- We will have to add Directory Reader privileges manullay to this identity, as it can couldn't be done through bicep
- Azure Database for MySQL Server - Flexible
- Admin User
- Admin Password
- SQL Version -
8.0 - Apparently Northeurope doesn't support high availability for Flexible servers as of Q2-2023
Note - I hacked the template from another repo of mine, so you will see some unused resources(log analytics workspace/queues etc.,). You can safely ignore them, But do remember to clean up your Resource Group to avoid unnecessary costs.
# make deploy sh deployment_scripts/deploy.shAfter successfully deploying the stack, Check the
Resource Groups/Deploymentssection for the resources. -
-
-
Add SQL Admin
Directory Readerprivileges - Ref this doc

-
Enable AAD Authetication for Azure MySQL - Ref this doc
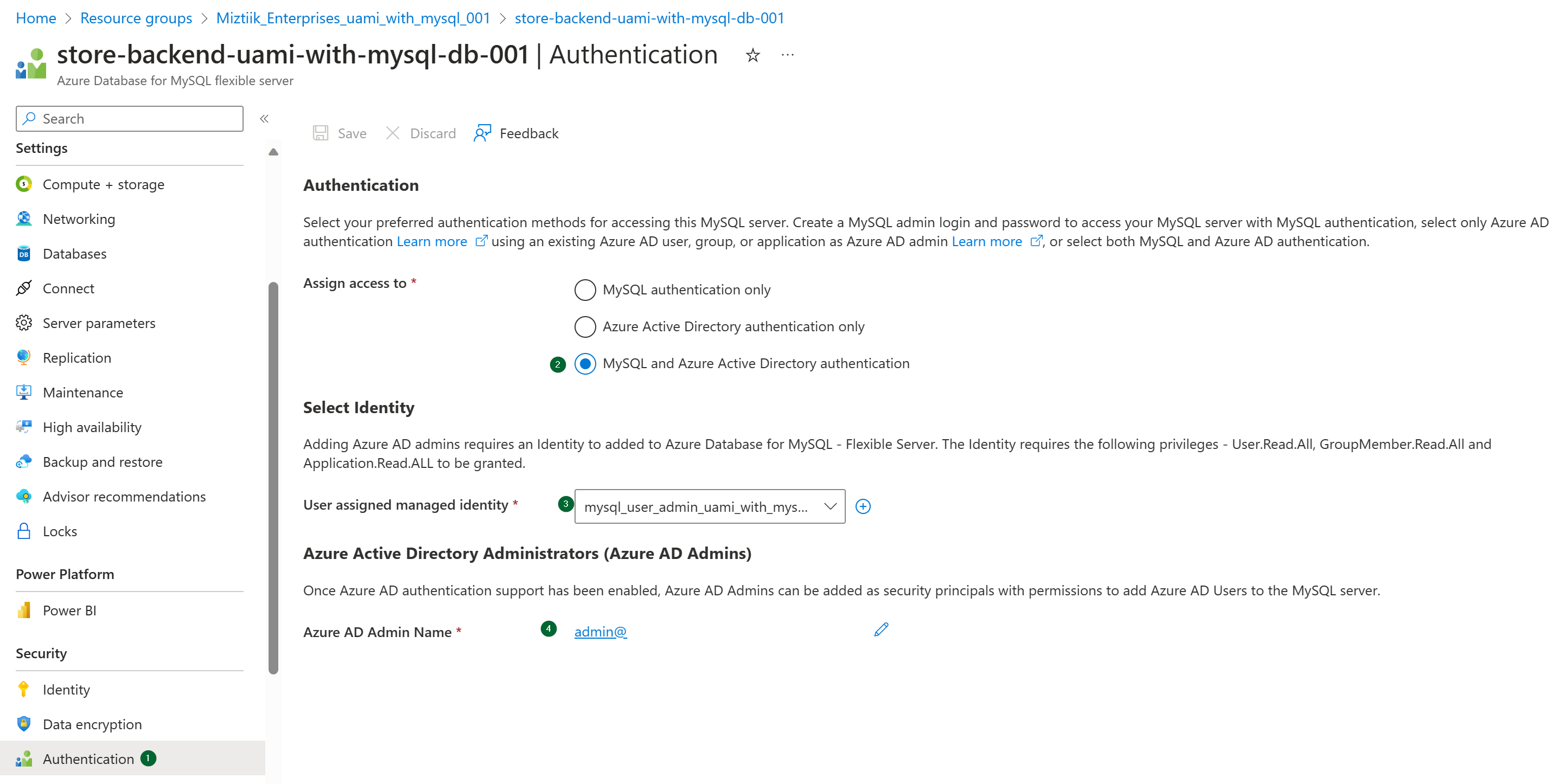


You will need the client Id of the managed identity

mysql> SET aad_auth_validate_oids_in_tenant = OFF; Query OK, 0 rows affected (0.02 sec) mysql> CREATE AADUSER 'miztiik_aad_user' IDENTIFIED BY '3b9..d2cf'; Query OK, 0 rows affected (0.03 sec)
Now we are all set, What have we done so far?
- Created a SQL Admin User Managed Identity - Gave it
Directory Readerprivileges - Enabled AAD Authetication for Azure MySQL
- Created a AAD User
miztiik_aad_userwith the client id of the SQL User Managed Identity(Note: This is not the same as the SQL Admin User Managed Identity). This user will be used to connect to the database from the VM.
- Created a SQL Admin User Managed Identity - Gave it
-
Login to your VM, You can find the public IP address in the resource blade. You can also get it from the Azure Portal. You may also try connecting to the database from local machine if you have mysql client, In this case, lets use the Azure VM as it is already bootstrapped with the mysql client
ssh miztiik@<PUBLIC_IP_ADDRESS>
# Connect to the database HOST='store-backend-uami-with-mysql-db-001.mysql.database.azure.com' PORT=3306 USERNAME='miztiik_aad_user' # This is the client id of the user managed identity # CLIENT_ID='3b9f63..cd2cf' # Retrieve the access token ACCESS_TOKEN=$(curl -s "http://169.254.169.254/metadata/identity/oauth2/token?api-version=2018-02-01&resource=https%3A%2F%2Fossrdbms-aad.database.windows.net&client_id=$CLIENT_ID" -H Metadata:true | jq -r .access_token) # echo $ACCESS_TOKEN mysql -h $HOST --user $USERNAME --enable-cleartext-plugin --password=$ACCESS_TOKEN
Verify the user details,
```sql mysql> SELECT USER(), CURRENT_USER(); +-------------------------------+--------------------+ | USER() | CURRENT_USER() | +-------------------------------+--------------------+ | miztiik_aad_user@20.238.78.77 | miztiik_aad_user@% | +-------------------------------+--------------------+ 1 row in set (0.00 sec) mysql>
-
-
In this demonstration, we have shown how to connect to Azure DB for Flexible MySQL using Managed Identities.
-
If you want to destroy all the resources created by the stack, Execute the below command to delete the stack, or you can delete the stack from console as well
- Resources created during Deploying The Solution
- Any other custom resources, you have created for this demo
# Delete from resource group az group delete --name Miztiik_Enterprises_xxx --yes # Follow any on-screen prompt
This is not an exhaustive list, please carry out other necessary steps as maybe applicable to your needs.
This repository aims to show how to Bicep to new developers, Solution Architects & Ops Engineers in Azure.
Thank you for your interest in contributing to our project. Whether it is a bug report, new feature, correction, or additional documentation or solutions, we greatly value feedback and contributions from our community. Start here

- Azure Docs: Connect with Managed Identity to Azure Database for MySQL
- Azure Docs: Assign Directory Readers role to an Azure AD group
- Azure Docs: Connect with Managed Identity to Azure Database for MySQL
- Azure Docs: Just In Time Access
Level: 100

