- Do you monitor
invalid ssh userlogin attempts? - Do you monitor
invalid ssh keylogin attempts? - Do you monitor multiple
ssh disconnectsin a short period of time?
That is exactly what we are going to do right now using, AWS CloudWatch, AWS EC2, AWS StepFunctions & SNS
Follow this article in Youtube
-
This demo, instructions, scripts and cloudformation template is designed to be run in
us-east-1. With few modifications you can try it out in other regions as well(Not covered here).- AWS CLI pre-configured - Get help here
- Optional AWS CDK Installed & Configured - Get help here
-
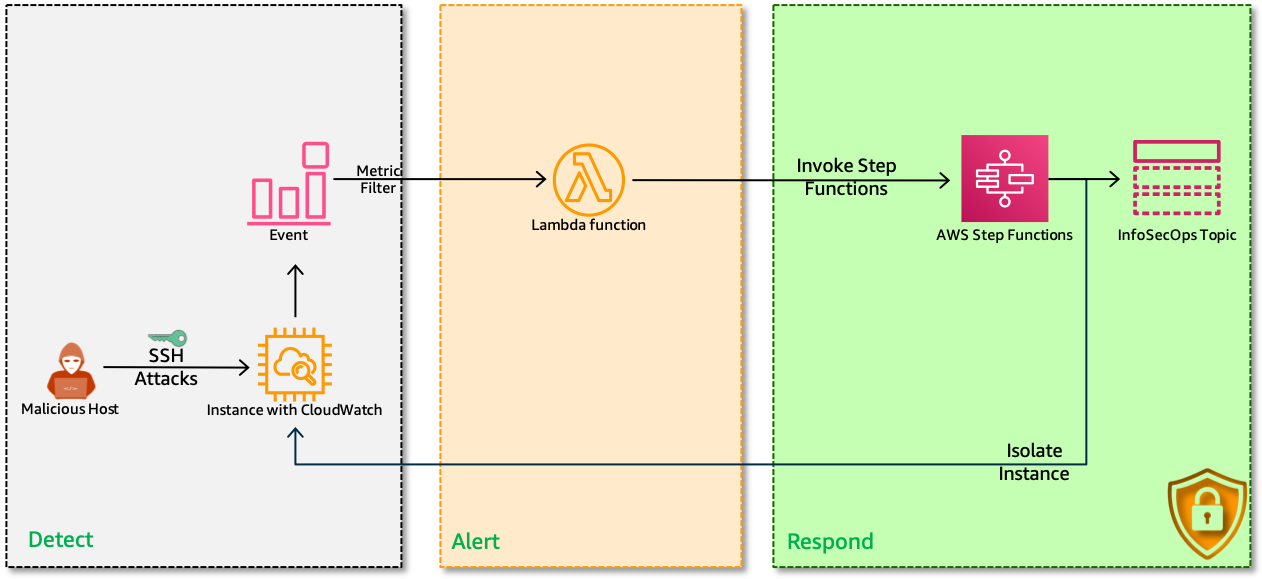
In this repo, I have included a cloudformation template that provisions the resources to setup a fully automatic remedation engine.
- EC2 Instance: We will use this instance to attack
- This instance will be pre-baked with cloudwatch agent to send
sshlogs to Cloudwatch LogGroups
- This instance will be pre-baked with cloudwatch agent to send
- CloudWatch LogGroup: Stores the
sshlogs from EC2- A Lambda function will be subscribed to this log group
- Lambda: Triggers the step function to isolate instance
- The trigger is based on
ssh_invalid_userlog filter - Pass the
inst_idto the step function
- The trigger is based on
- StepFunction:
- EXTREME REMEDIATION ACTION: Isolate the EC2 instance with quarantine security group
- As this is a demo, This automation will quarantine the EC2 Instance with SG. You can modify this lambda to suit your needs
- Notify InfoSecOps
- EXTREME REMEDIATION ACTION: Isolate the EC2 instance with quarantine security group
- CloudWatch Alarms
- Invalid User Alarm
- Invalid Key Alarm
- Too Many Disconnects
- IAM Roles: For lambda and step functions with restrictive permissions
Note: Sample commands to trigger ssh failures to test the solution can be found in the output section of the cloudformation template
- EC2 Instance: We will use this instance to attack
You have couple of options to set this up in your account, You can use AWS CDK or use the cloudformation template generated by CDK. All the necessary steps are baked into the templates, you can launch it and try it out.
-
If you have AWS CDK installed you can close this repository and deploy the stack with,
# If you DONT have cdk installed npm install -g aws-cdk git clone https://github.com/miztiik/security-automation-respond-to-failed-ssh-access.git cd security-automation-respond-to-failed-ssh-access source .env/bin/activate pip install -r requirements.txt
The very first time you deploy an AWS CDK app into an environment (account/region), you’ll need to install a
bootstrap stack, Otherwise just go ahead and deploy usingcdk deploycdk bootstrap cdk deploy
-
Look for the cloudformation template here:
cdk.outdirectory, From the CLI,aws cloudformation deploy \ --template-file ./cdk.out/security-automation-respond-to-failed-ssh-access.template.json \ --stack-name "MiztiikAutomationStack" \ --capabilities CAPABILITY_IAM -
- Goto EC2>SecurityGroup>Update port22 rule to allow only your IP(by default it allows ssh traffic from within the vpc)
- Goto
AWS SNSsubscribe yourself to theInfoSecOpsSNS Topic. - Use the commands given in the cloudformation template to trigger
invalid_ssh_userlogs, - You should receive an email with remediation action
- Check the step functions for execution(The EC2 instance also must have a new SG attached to it)
You should be able to see something like this for a successful remediation.
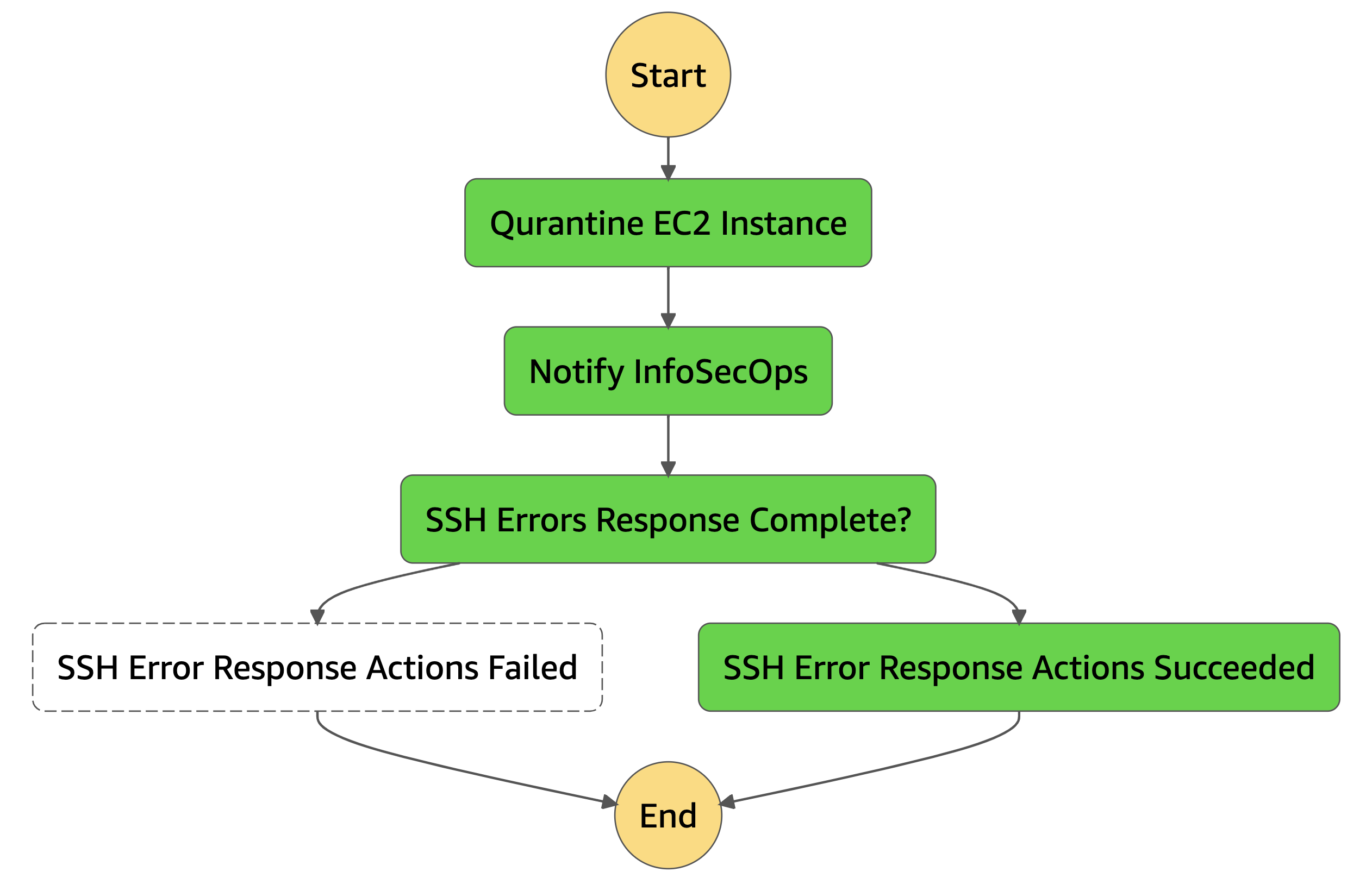
Now that we have confirmed the solution is working, you can extend the solution as required.
-
- Qurantine User/Role triggering multiple failures
- Look at removing SSH/22 access completely
-
As mentioned earlier, this is a reactive solution. This automation should not be the primary means of defence against weak security controls. You should consider,
- Who has permissions to change SSH Keys.
- Are those permissions restricted only the resources they own? - Refer Attribute Based Access Control - ABAC
- Are you auditing those privileges automatically?
- If all else fails, do you have mechanisms that will automatically respond to events?
-
If you want to destroy all the resources created by the stack, Execute the below command to delete the stack, or you can delete the stack from console as well
- Delete Quarantine Security Group
- Delete CloudWatch Lambda LogGroups
- Delete the stack[s],
# Delete the CF Stack aws cloudformation delete-stack \ --stack-name "MiztiikAutomationStack" \ --region "${AWS_REGION}"
This is not an exhaustive list, please carry out other necessary steps as maybe applicable to your needs.
Buy me a coffee ☕ through Paypal, or You can reach out to get more details through here.
Level: 200