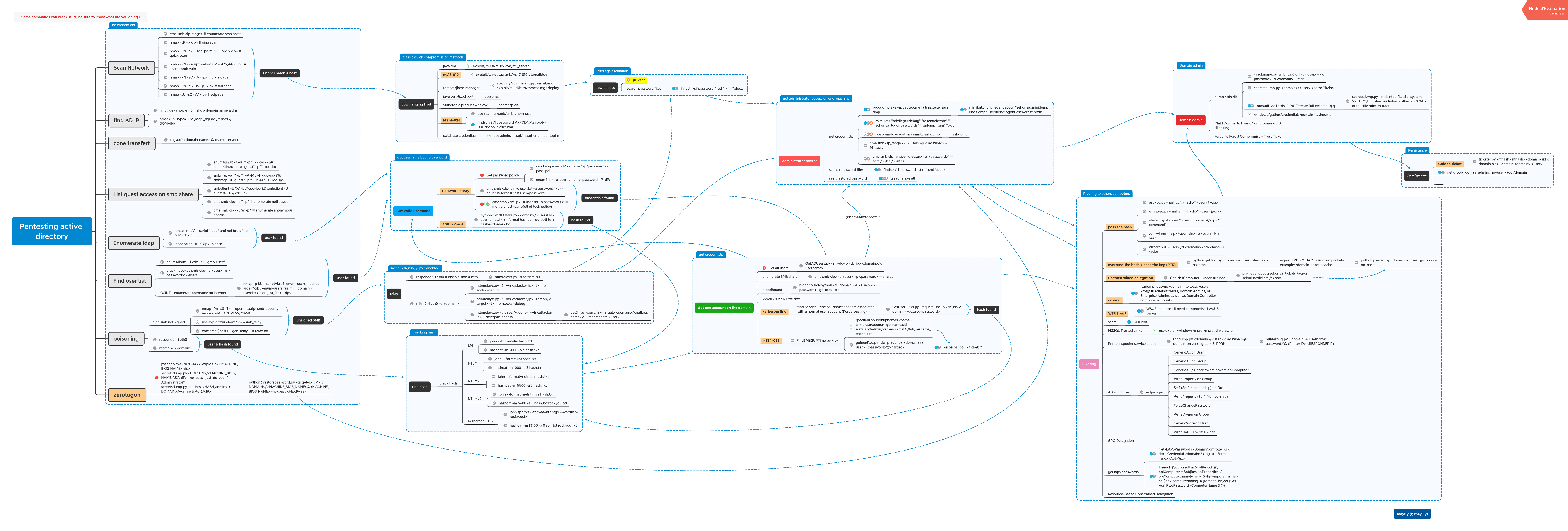
Arsenal is just a quick inventory, reminder and launcher for pentest commands.
This project written by pentesters for pentesters simplify the use of all the hard-to-remember commands
In arsenal you can search for a command, select one and it's prefilled directly in your terminal. This functionality is independent of the shell used. Indeed arsenal emulates real user input (with TTY arguments and IOCTL) so arsenal works with all shells and your commands will be in the history.
You have to enter arguments if needed, but arsenal supports global variables.
For example, during a pentest we can set the variable ip to prefill all commands using an ip with the right one.
To do that you just have to enter the following command in arsenal:
>set ip=10.10.10.10
Authors:
- Guillaume Muh
- mayfly
This project is inspired by navi (https://github.com/denisidoro/navi) because the original version was in bash and too hard to understand to add features
git clone https://github.com/Orange-Cyberdefense/arsenal.git
cd arsenal
./run
Inside your .bashrc or .zshrc add the path to run to help you do that you could launch the addalias.sh script
./addalias.sh
git clone https://github.com/Orange-Cyberdefense/arsenal.git
cd arsenal
python3 setup.py install
If you got on error on color init try :
export TERM='xterm-256color'
- msfvenom
- php
- python
- perl
- powershell
- java
- ruby
- php
- nodejs
- hash
- enum4linux
- smbmap
- smbget
- rpcclient
- rpcinfo
- nbtscan
- impacket
- impacket
- bloodhound
- mitm6
- responder
- ysoserial
- ysoserial.net
- hydra
- hashcat
- john
- nmap
- gobuster
- ffuf
- wfuzz
- dig
- dnsrecon
- dnsenum
- sublist3r
- rpcbind
- snmpwalk
- snmp-check
- onesixtyone
- sqlmap
- oscanner
- sqlplus
- tnscmd10g
- mysql
- showmount
- xfreerdp
- rdesktop
- ncrack
- sqsh
- evilwinrm
- redis-cli
- psql
- pgdump
- vncviewer
- xspy
- xwd
- xwininfo
- ldapsearch
- sslscan
- burp
- nikto
- tplmap
- drupwn
- wpscan