[New WTFBin]: Suspicious characters in command line arguments for Ivanti Endpoint Manager logging processes
mbabinski opened this issue · 1 comments
Contributor Name: Micah Babinski
Application/Executable: Various Ivanti Endpoint Manager Logging Internals
- LDmemory.exe
- LDnetwork.exe
- LDdrives.exe
WTF Behavior Description:
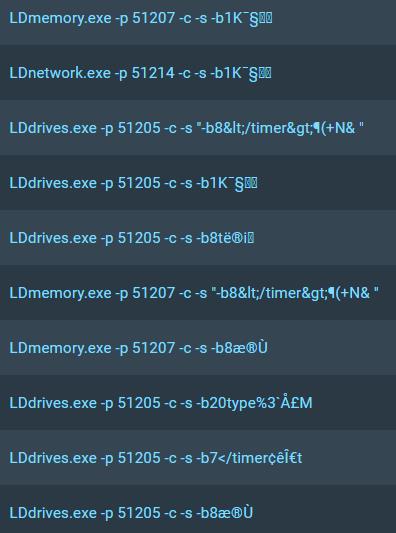
The command-line arguments for the exes listed above occassionally contain fragmented, seemingly-random strings containing special unicode characters, what looks like bits of HTML or XML tags, and/or URL-enocoded strings. For example:
- LDdrives.exe -p 51205 -c -s -b5D€\u001aCv
- LDdrives.exe -p 51205 -c -s -b8µq
- LDdrives.exe -p 51205 -c -s "-b8</timer>¶(+N& "
- LDmemory.exe -p 51207 -c -s "-b32164/><key nam=ÂgËo�"
- LDnetwork.exe -p 51214 -c -s -b10</timer>žÊ/€/�
These processes all spawn instances of Console Host (conhost.exe) with the 0x4 flag, like \??\C:\Windows\system32\conhost.exe 0x4.
Link to Documentation of Behavior:
None found. According to this page, the exes are components within Endpoint Manager's real time inventory and monitoring capabilities:
https://forums.ivanti.com/s/article/How-to-turn-on-logging-for-collector-exe-Real-time-inventory-and-monitoring?language=en_US
The -p flag matches with the expected communication port, but I was unable to find any documentation for the other flags in the command. This behavior will be detected by anyone using Sigma's Obfuscated Command Line Using Special Unicode Characters rule.
Please provide any images for additional evidence.
Thanks for considering my submission. I love the project btw!