POC for testing microservices orchestration patterns.
Checkout this project and install into local repository (with this bug #495 fixed):
git clone git@github.com:tentativafc/grpc-spring-boot-starter.git
cd grpc-spring-boot-starter
./gradlew publishToMavenLocalMake projects and run docker compose (Build, Uploads images and start docker compose)
./make.shStart application
docker-compose up -d| Service | Port Number | Type/Tech |
|---|---|---|
| Mysql Data-Service | 3306 | DB |
| Mysql Validation-Fields-Service | 3307 | DB |
| DLQ | 5672 | Rabbit MQ |
| Data-Service | 8080 | Spring Boot App |
| Validation-Fields-Service | 8081 | Spring Boot App |
| Data-Service-RPC | 9090 | GRPC |
| Validation-Fields-Service-RPC | 9091 | GRPC |
| Orchestrator-Service | 8082 | Spring Boot App |
| Service-Discovery | 8500 | Consul |
| Frontend | 8083 | VUEjs |
Generate data for performance tests (Jmeter script Test Plan.jmx)
-
Create virtualenv and install python dependencies
-
Make projects and run docker compose (Build, Uploads images and start docker compose) this step does not need repeat.
cd backend/gen-data virtualenv env source env/bin/activate pip install -r requirements.txt
-
Generate data:
./gen_data.sh
Create cluster
k3d cluster create k3d-poc-orchestration-cluster --servers 1 --agents 3 --port 9080:80@loadbalancer --port 9443:443@loadbalancer --api-port 6443 --k3s-server-arg '--no-deploy=traefik'
k3d kubeconfig merge k3d-poc-orchestration-cluster --kubeconfig-switch-context
kubectl cluster-info
kubectl get pods --all-namespaces
# Delete if you need
k3d cluster delete k3d-poc-orchestration-clusterDownload Istio
Install istio profile
istioctl install --set profile=demo -yAdd a namespace label to instruct Istio to automatically inject Envoy sidecar proxies when you deploy your application later
kubectl label namespace default istio-injection=enabledInstall addons (Prometheus, Grafana, Jaeger and Kiali):
kubectl apply -f samples/addonsSimple application
kubectl apply -f k8s/demo.yaml
# Testing
kubectl exec "$(kubectl get pod -l app=demo -o jsonpath='{.items[0].metadata.name}')" -c demo -- curl -sS http://demo-svc:8080/demo
Install Service Discovery and Databases
kubectl apply -f k8s/infra.yamlInstall Data Service
kubectl apply -f k8s/data-service.yaml
# Testing
kubectl exec "$(kubectl get pod -l app=data-service -o jsonpath='{.items[0].metadata.name}')" -c data-service -- curl -sS http://data-service-svc:8080/actuator/healthInstall Validation-Service
kubectl apply -f k8s/validation-service.yaml
# Testing
kubectl exec "$(kubectl get pod -l app=validation-service -o jsonpath='{.items[0].metadata.name}')" -c validation-service -- curl -sS http://validation-service-svc:8080/actuator/healthkubectl apply -f k8s/orchestrator-service.yaml
# Testing
kubectl exec "$(kubectl get pod -l app=orchestrator-service -o jsonpath='{.items[0].metadata.name}')" -c orchestrator-service -- curl -sS http://orchestrator-service-svc:8080/actuator/healthCheck services and pods
# Check services
kubectl get services
# Check if service is binding to pod
kubectl describe svc <service_name>
#Check pods
kubectl get pods
#Check pods logs
kubectl logs <pod_name>
# If you need inspect process/files on pod (replaces <app_name>)
kubectl exec -it exec "$(kubectl get pod -l app=<app_name> -o jsonpath='{.items[0].metadata.name}')" -- shGateway config
kubectl apply -f k8s/orchestrator-gateway.yamlGet ingress server and port
kubectl get svc istio-ingressgateway -n istio-system
export INGRESS_HOST=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.status.loadBalancer.ingress[0].ip}')
export INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="http2")].nodePort}')
export SECURE_INGRESS_PORT=$(kubectl -n istio-system get service istio-ingressgateway -o jsonpath='{.spec.ports[?(@.name=="https")].nodePort}')
export GATEWAY_URL=$INGRESS_HOST:$INGRESS_PORT
echo "$GATEWAY_URL"Open in browser this url:
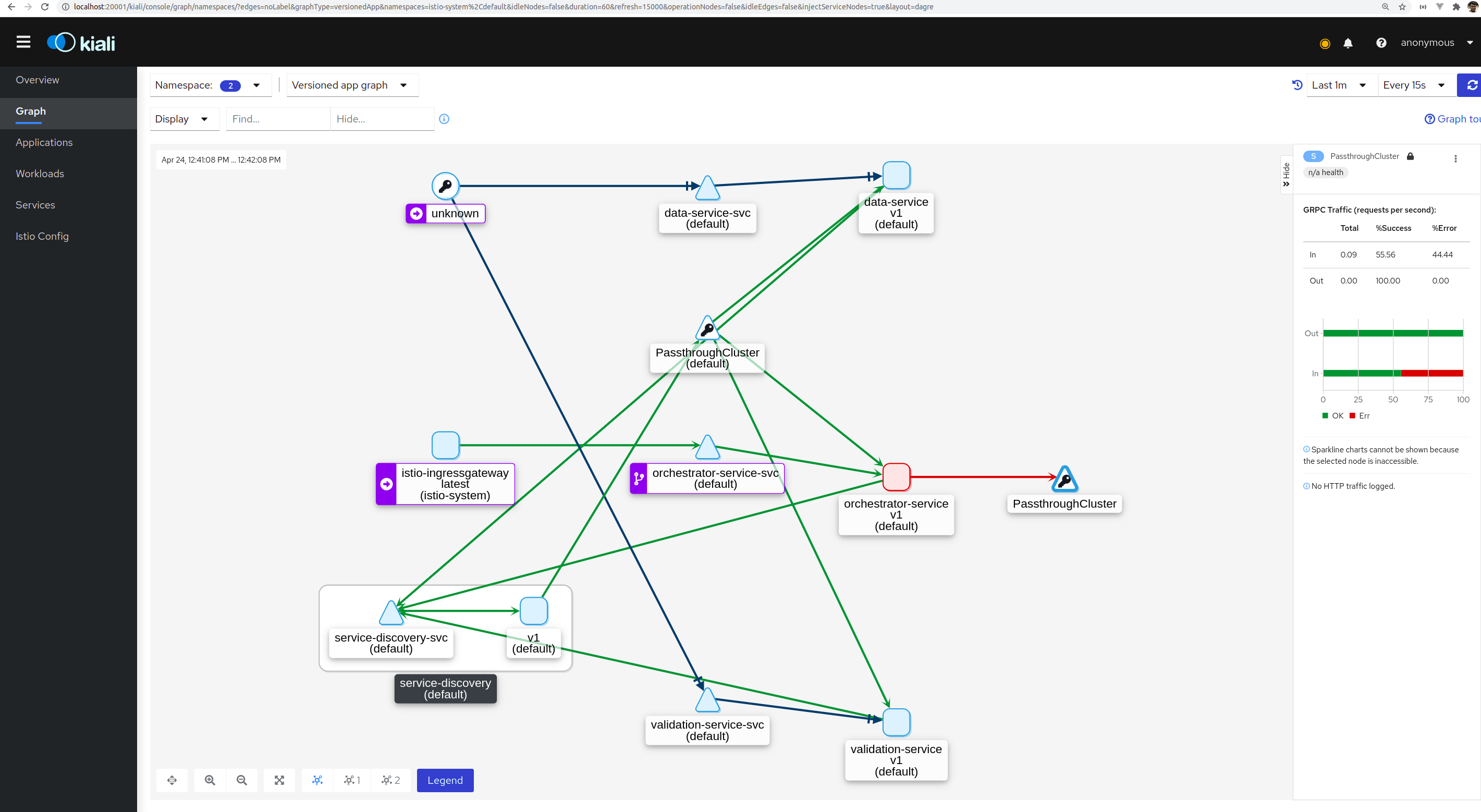
echo "http://$GATEWAY_URL/actuator/health"Kiali
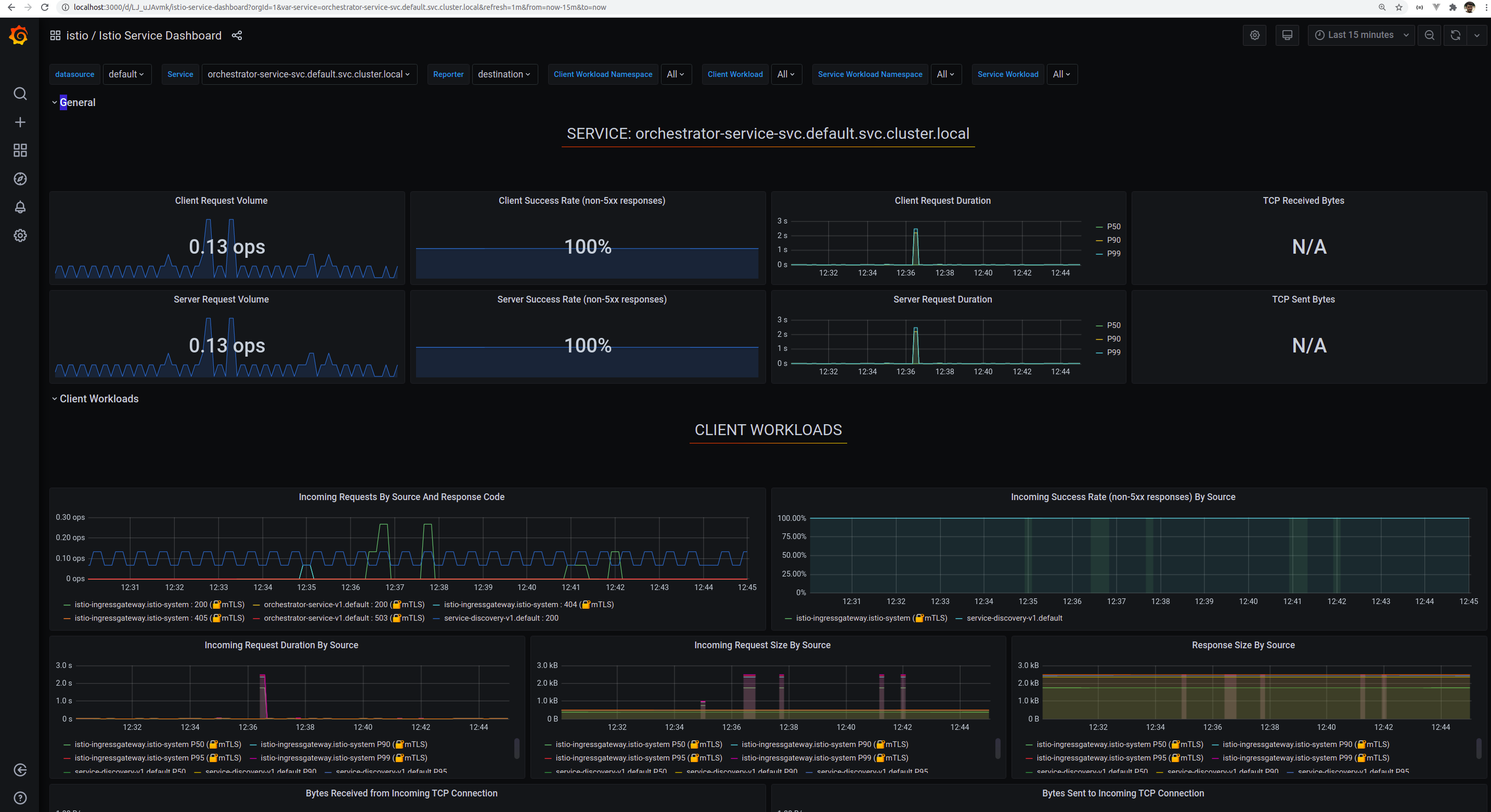
istioctl dashboard kialiGrafana
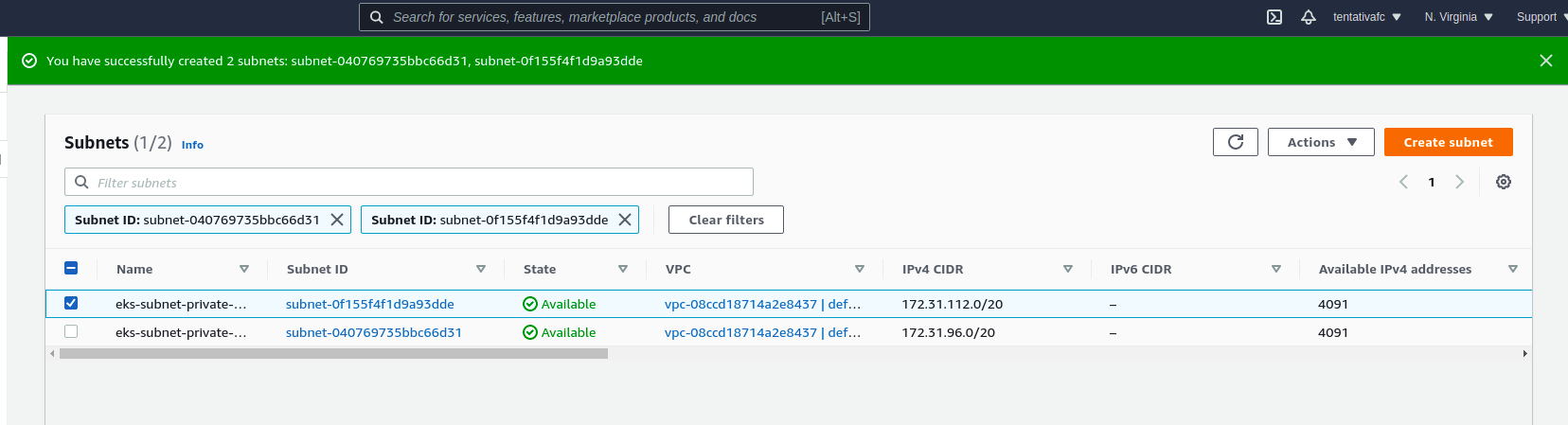
istioctl dashboard grafanaCreate the subnets
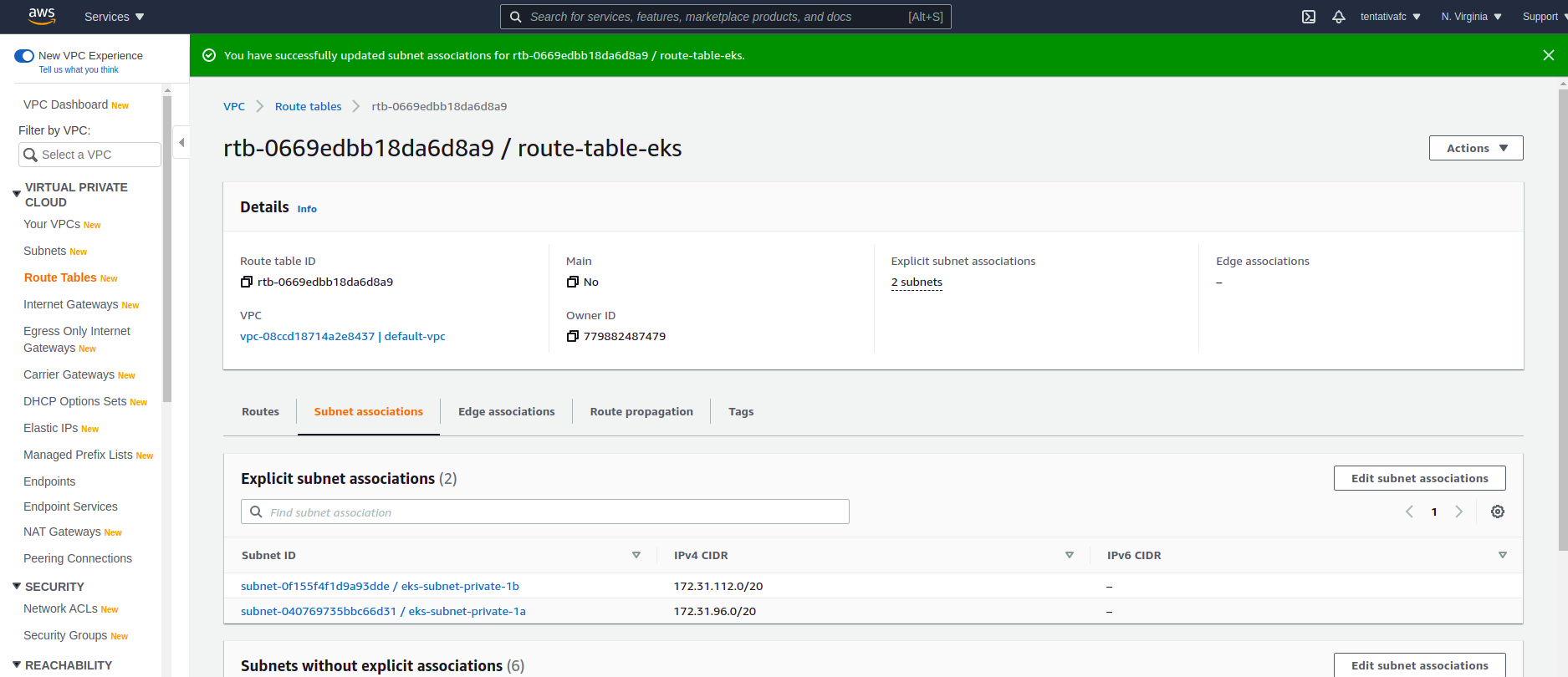
Create and associate route tables to subnets
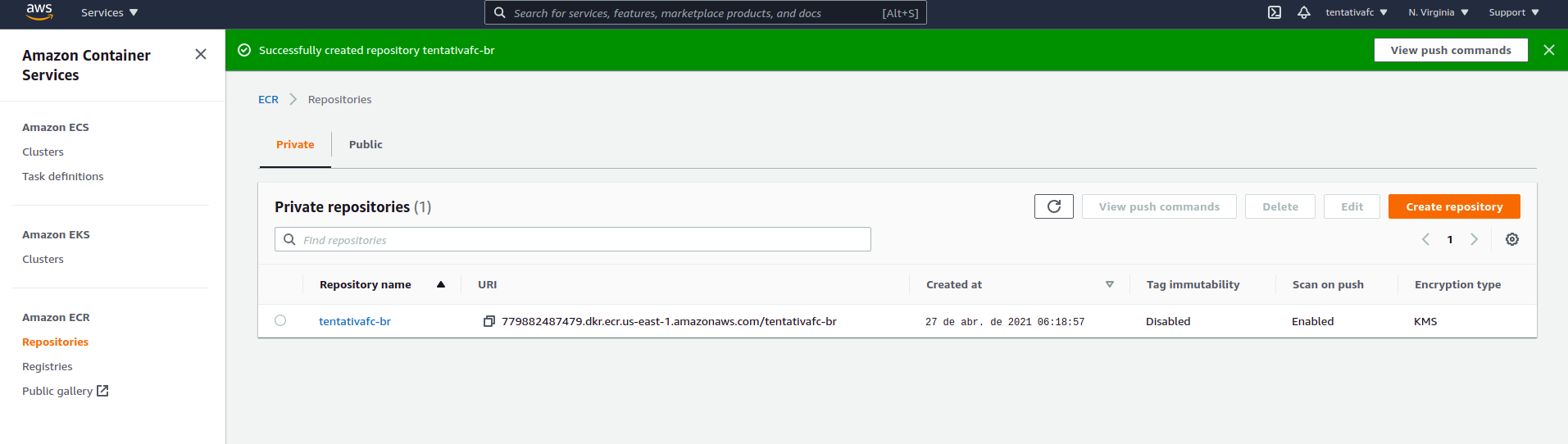
Create the ECR
Push images to ECR
# Docker login
aws ecr get-login-password --region us-east-1 | docker login --username AWS --password-stdin 779882487479.dkr.ecr.us-east-1.amazonaws.com
# Build image and push
cd backend/demo
mvn clean compile package
docker build -t demo:latest -f Dockerfile .
docker tag tentativafc-br:latest 779882487479.dkr.ecr.us-east-1.amazonaws.com/tentativafc-br:demo
docker push 779882487479.dkr.ecr.us-east-1.amazonaws.com/tentativafc-br:demoCreate cluster EKS (eksctl)
# Creates using eksctl
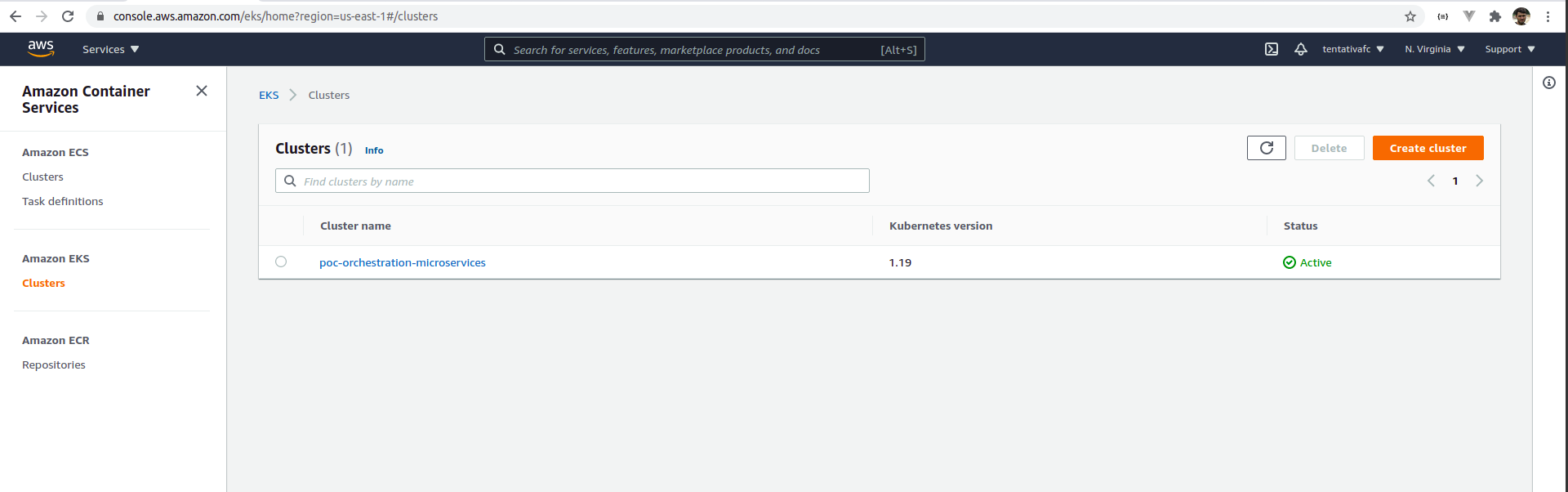
eksctl create cluster --name poc-orchestration-microservices --version 1.19 --region us-east-1 --nodegroup-name ng-poc-1 --node-type m5.xlarge --nodes 2 --nodes-min 1 --nodes-max 3 --managed
# Delete if you need
eksctl delete cluster --name poc-orchestration-microservicesOr Cloudformation
# Create cluster
aws cloudformation create-stack --stack-name poc-eks-cluster --template-body file://AWS/eks-cluster-cf-template.json --capabilities CAPABILITY_IAM
# Create nodegroup
aws cloudformation create-stack --stack-name poc-eks-cluster-nodegroup --template-body file://AWS/eks-nodegroups-cf-template.json --capabilities CAPABILITY_IAMOr Terraform
cd AWS
# Init terraform state
terraform init
# Create infra
terraform applyEnable kubectl connection
aws eks update-kubeconfig --name poc-orchestration-microservices --region us-east-1Private subnets 1 Private subnets 2 Private subnets 3
Force container recreation:
docker-compose up --build --force-recreate data-serviceStop all containers:
docker-compose down
docker stop $(docker container ls -aq)Run Spring Boot like nodemon (nodejs)
./mvnw spring-boot:runDelete all containers:
docker rm -f $(docker container ls -aq)Create docker image and push to docker-hub:
docker build -t tentativafc/ib-sts-service:1.0-snapshot -f Dockerfile .docker push tentativafc/ib-sts-service:1.0-snapshotRun docker image:
docker run --rm -d --network host --name my_sts_service sts-service:latestGenerating GRPC stub:
protoc sts.proto --go_out=plugins=grpc:.Configure pod or service:
kubectl apply -f <filename>Delete running pod or service:
kubectl delete -f <filename>List pods, services or deployments:
kubectl get <pods/services/deployments>Detail object:
kubectl describe <object type> <object name>Create and list secrets:
kubectl create secret <type of secret> <secret name> --from literal key=value
kubectl get secrets