piVPN only sends packets through DMZ
neone35 opened this issue · 10 comments
In raising this issue, I confirm the following:
- I have read the documentation
- I have read and understood the PiVPN General Guidelines
Has your install failed? no
Describe the issue
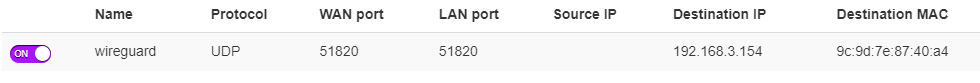
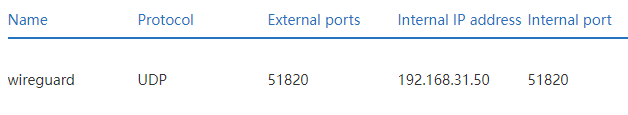
I have ISP router (Technicolor DGA0122) and my own router (Xiaomi Mi Router 4A Giga), where I've set up port forwarding for 51820 (wireguard) port as per PiVPN faq, so that ISP router points to Xiaomi and Xiaomi points to PiVPN with static IP (Xiaomi also has static IP). But these forwarding rules don't seem to work, because I only see packets (tcpdump -n -i eth0 udp port 51820) sent when I set Pi as DMZ through Xiaomi router. Here's my configuration screenshots on both routers (192.168.3.154 is Xiaomi and 192.168.31.50 is Pi):
Expected behavior
Ports are forwarded and packets are sent without enabling DMZ mode
Have you searched for similar issues and solutions? yes
Additional context
output of ufw show added
ufw route allow in on wg0 out on eth0 from 10.211.60.0/24
ufw allow 51820/udp comment 'allow-wireguard'
ufw allow in on wg0 from 10.211.60.0/24 to any port 53
ufw allow 22
ufw allow 80/tcp
ufw allow 53/tcp
ufw allow 53/udp
ufw allow 67/tcp
ufw allow 67/udp
ufw allow 546:547/udp
ufw allow 3389/tcp
ufw allow from 192.168.1.0/24 to any port 3389
ufw allow 51413
ufw allow 8080
ufw allow 9443
ufw allow 51820
ufw allow 12243
Have you taken any steps towards solving your issue?
enabling/disabling DMZ
forwarding other ports which I've seen in packets during DMZ mode
adding other wireguard clients
forwarding both TCP and UDP (not only UDP)
trying to access tunnel from local and public networks
Please provide your system information
What type of hardware are you running PiVPN at? Raspberrypi 4B 4GB
Output of uname -a
Linux artur-pi 5.15.0-1023-raspi #25-Ubuntu SMP PREEMPT Fri Jan 6 17:33:55 UTC 2023 aarch64 aarch64 aarch64 GNU/Linux
Output of cat /etc/os-release
PRETTY_NAME="Ubuntu 22.04.1 LTS"
NAME="Ubuntu"
VERSION_ID="22.04"
VERSION="22.04.1 LTS (Jammy Jellyfish)"
VERSION_CODENAME=jammy
ID=ubuntu
ID_LIKE=debian
HOME_URL="https://www.ubuntu.com/"
SUPPORT_URL="https://help.ubuntu.com/"
BUG_REPORT_URL="https://bugs.launchpad.net/ubuntu/"
PRIVACY_POLICY_URL="https://www.ubuntu.com/legal/terms-and-policies/privacy-policy"
UBUNTU_CODENAME=jammy
Console output of pivpn debug
:::: �[4mPiVPN debug�[0m ::::
=============================================
:::: �[4mLatest commit�[0m ::::
Branch: master
Commit: f7f81e1bf47b5f4564b6ded7a516da5fd3c2f63c
Author: 4s3ti
Date: Mon Nov 28 23:32:17 2022 +0100
Summary: fix(scripts): uninstall default option
=============================================
:::: �[4mInstallation settings�[0m ::::
PLAT=Ubuntu
OSCN=jammy
USING_UFW=1
pivpnforceipv6route=1
IPv4dev=eth0
install_user=artur
install_home=/home/artur
VPN=wireguard
pivpnPORT=51820
pivpnDNS1=10.211.60.1
pivpnDNS2=
pivpnHOST=REDACTED
pivpnPROTO=udp
pivpnMTU=1420
pivpnDEV=wg0
pivpnNET=10.211.60.0
subnetClass=24
pivpnenableipv6=0
ALLOWED_IPS="0.0.0.0/0, ::0/0"
UNATTUPG=1
INSTALLED_PACKAGES=(grepcidr net-tools bsdmainutils wireguard-tools qrencode)
=============================================
:::: �[4mServer configuration shown below�[0m ::::
[Interface]
PrivateKey = server_priv
Address = 10.211.60.1/24
MTU = 1420
ListenPort = 51820
### begin poco-f1 ###
[Peer]
PublicKey = poco-f1_pub
PresharedKey = poco-f1_psk
AllowedIPs = 10.211.60.2/32
### end poco-f1 ###
=============================================
:::: �[4mClient configuration shown below�[0m ::::
[Interface]
PrivateKey = poco-f1_priv
Address = 10.211.60.2/24
DNS = 10.211.60.1
[Peer]
PublicKey = server_pub
PresharedKey = poco-f1_psk
Endpoint = REDACTED:51820
AllowedIPs = 0.0.0.0/0, ::0/0
=============================================
:::: �[4mRecursive list of files in�[0m ::::
:::: �[4m/etc/wireguard shown below�[0m ::::
/etc/wireguard:
configs
keys
wg0.conf
/etc/wireguard/configs:
clients.txt
poco-f1.conf
/etc/wireguard/keys:
poco-f1_priv
poco-f1_psk
poco-f1_pub
server_priv
server_pub
=============================================
:::: �[4mSelf check�[0m ::::
:: [OK] IP forwarding is enabled
:: [OK] Ufw is enabled
:: [OK] Iptables MASQUERADE rule set
:: [OK] Ufw input rule set
:: [OK] Ufw forwarding rule set
:: [OK] WireGuard is running
:: [OK] WireGuard is enabled
(it will automatically start on reboot)
:: [OK] WireGuard is listening on port 51820/udp
=============================================
:::: Having trouble connecting? Take a look at the FAQ:
:::: �[1mhttps://docs.pivpn.io/faq�[0m
=============================================
:::: �[1mWARNING�[0m: This script should have automatically masked sensitive ::::
:::: information, however, still make sure that �[4mPrivateKey�[0m, �[4mPublicKey�[0m ::::
:::: and �[4mPresharedKey�[0m are masked before reporting an issue. An example key ::::
:::: that you should NOT see in this log looks like this: ::::
:::: YIAoJVsdIeyvXfGGDDadHh6AxsMRymZTnnzZoAb9cxRe ::::
=============================================
:::: �[4mDebug complete�[0m ::::
To be clear, Xiaomi Mi Router 4A Giga's IP as seen from Technicolor DGA0122 is 192.168.3.154 and 192.168.31.50 is Raspberry Pi's IP as seen from Xiaomi Mi Router 4A Giga, right? The xiaomi router may have a firewall blocking the port.
You're right. I see no firewall options on xiaomi router. Only thing I found is Wi-Fi security.
According to some information I found online, you may need to disable UPnP and reconfigure port forwarding on the Xiaomi Mi Router 4A Giga
But I use upnp to watch movies over network from other devices
UPnP is basically “port forwarding on demand”, not sure why you need that to watch movies over the network (not internet). It’s not mutually exclusive with manual port forwarding but perhaps the xiaomi is reserving a port range that cannot be manually forwarded when upnp is on.
Just peaking in to mention that.
UPnP is a security risk and should not be used for anything, and port forwarding should be set up manually.
But I noticed that in services list I see openvpn service, not wireguard? Why is it so? I choose wireguard.
Where do you see that? You may have installed openvpn, then wireguard, but didn't remove openvpn (you can use both at the same time).
You can also connect the Pi directly to the Technicolor DGA0122.
I see that when listing running services on pi using service --status-all | grep '\[ + \]'
I can't connect directly to ISP router because there's reason I bought xiaomi. My ISP router has IPTV and pi-hole doesn't go together well - I can't use custom dns service. That's why I put all my network on xiaomi and left only TV on technicolor.
You can stop and disable the service with systemctl disable --now openvpn.service and uninstall with pivpn uninstall (but make sure to select openvpn).
I can't help much with the router. You can temporarily connect a client to the Technicolor and then connect to wireguard using 192.168.3.154 as the Endpoint IP in the .conf file to test just the Xiaomi port forward.