XSS on 404 page of bugs.python.org
hannob opened this issue · 9 comments
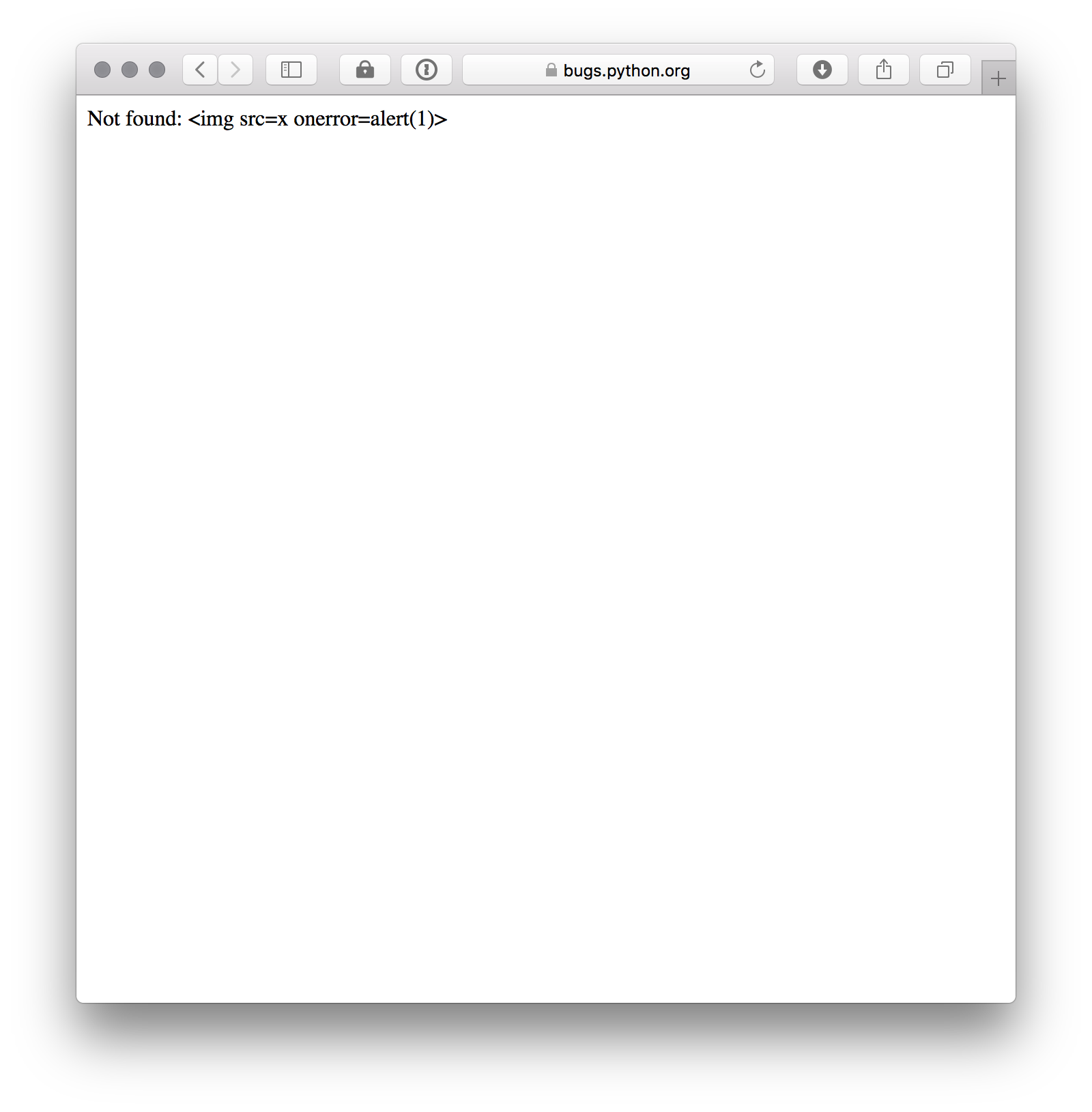
There's an XSS on the error page of bugs.python.org:
https://bugs.python.org/%3Cimg%20src=x%20onerror=alert%281%29%3E
(Not sure if this is the right place to report it, I already reported it to the python bugtracker itself despite it having no proper category for it https://bugs.python.org/issue36391 )
Hi @hannob! Thanks for reporting!
Looks to come from:
$ grep -r 'Not found'
roundup/cgi/wsgi_handler.py: request.wfile.write('Not found: %s'%client.path)
frontends/roundup.cgi: out.write('Not found: %s'%client.path)
may be fixed using cgi.escape().
Not sure how to do a pull request on this, @ewdurbin @ezio-melotti?
bugs.python.org branch at https://bitbucket.org/python/roundup/src/bugs.python.org/, and should likely be filed at issues.roundup-tracker.org as well
@ewdurbin It looks like I don't have the rights to push on this repo.
I'm proposing:
# HG changeset patch
# User Julien Palard <julien@palard.fr>
# Date 1553279943 -3600
# Fri Mar 22 19:39:03 2019 +0100
# Branch bugs.python.org
# Node ID 229ada7883f19aaf95f764c08e0f5cebc43844e2
# Parent d7454b42b914a69e6d1e1de99fe79fa6c8d6d982
FIX: XSS reported by hannob
fixes: https://github.com/python/bugs.python.org/issues/34
diff -r d7454b42b914 -r 229ada7883f1 frontends/roundup.cgi
--- a/frontends/roundup.cgi Tue Oct 09 17:48:10 2018 -0700
+++ b/frontends/roundup.cgi Fri Mar 22 19:39:03 2019 +0100
@@ -179,7 +179,7 @@
request.send_response(404)
request.send_header('Content-Type', 'text/html')
request.end_headers()
- out.write('Not found: %s'%client.path)
+ out.write('Not found: %s'%cgi.escape(client.path))
else:
import urllib
diff -r d7454b42b914 -r 229ada7883f1 roundup/cgi/wsgi_handler.py
--- a/roundup/cgi/wsgi_handler.py Tue Oct 09 17:48:10 2018 -0700
+++ b/roundup/cgi/wsgi_handler.py Fri Mar 22 19:39:03 2019 +0100
@@ -66,7 +66,7 @@
client.main()
except roundup.cgi.client.NotFound:
request.start_response([('Content-Type', 'text/html')], 404)
- request.wfile.write('Not found: %s'%client.path)
+ request.wfile.write('Not found: %s'%cgi.escape(client.path))
# all body data has been written using wfile
return []
imported, applied, deployed, confirmed: https://bitbucket.org/python/roundup/commits/51682dc2cd7e28421d749117c25bec58f632ee5f
@hannob Did you request a CVE identifier for this vulnerability?
No, after my last experiences with CVE assignments I decided that I'll just stop caring about it. If you care about it feel free to try to assign one. I posted it to oss-sec and sometimes this causes other people to request CVEs.
Alright. CVE requested via https://cveform.mitre.org/. Have a nice weekend.
Use CVE-2019-10904.