It is a process in which security threats are detected, and potential risks that can impact the logical flow and architecture of systems can be mapped and listed. Aiming at a Shift-Left strategy, the introduction of Threat Modeling facilitates the implementation of Security-By-Design for your S-SDLC in the Design phase.
-> Threat identification and Classification
-> Identification of Threat Profiles
-> Verification of Implemented Security Requirements and Controls
-> Risk Classification
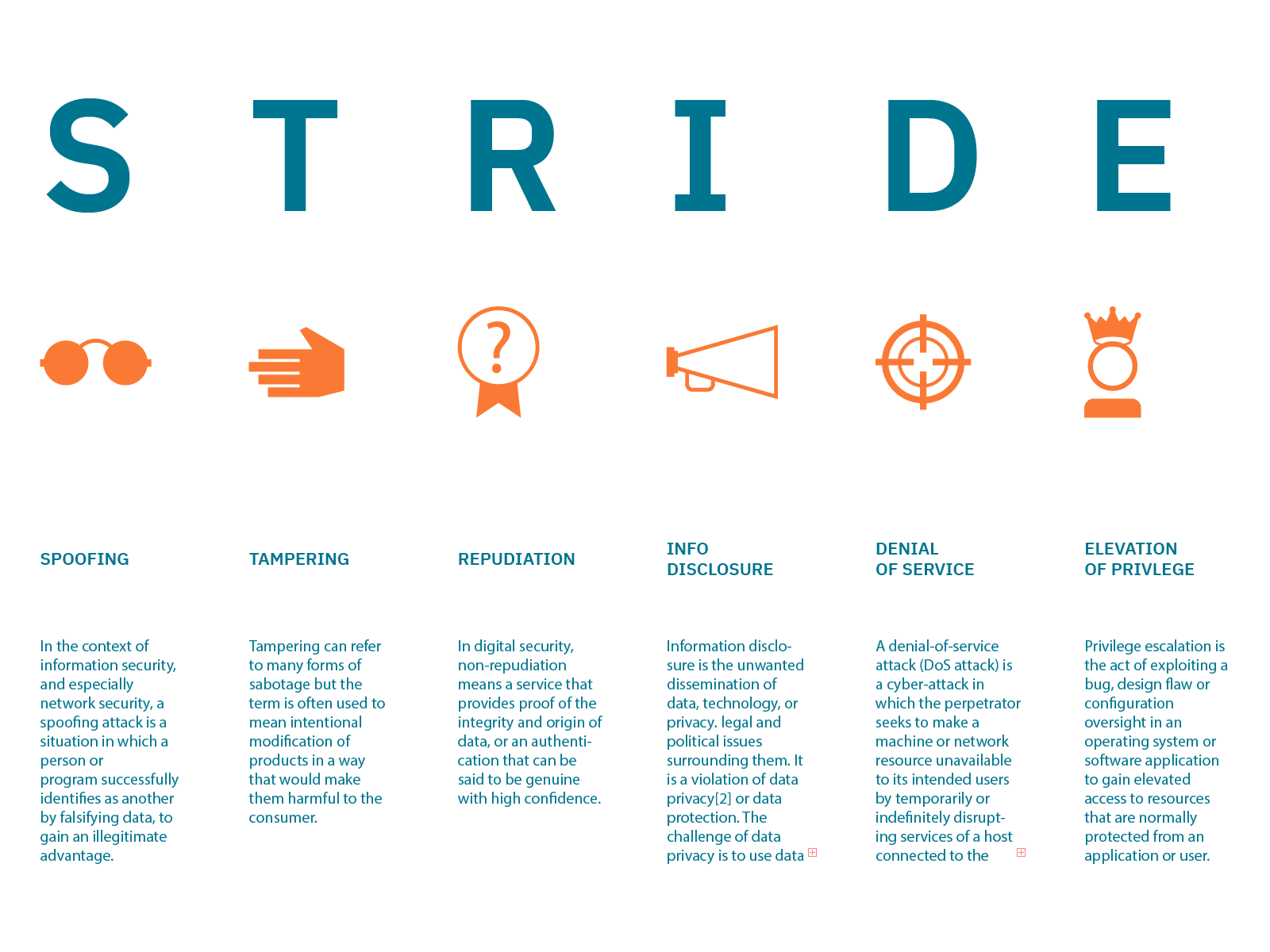
In a more traditional approach, it may be necessary to use a model to classify threats, the most used currently is STRIDE, but there are also others such as: DREAD, VAST, OCTAVE, FOLDER, DREAD, TRIKE.
https://developer.ibm.com/articles/threat-modeling-microservices-openshift-4/
https://learn.microsoft.com/pt-br/azure/security/develop/threat-modeling-tool-threats
For this phase there are some tools that can be used for free, such as Microsoft's Threat Modeling Tool based on the STRIDE methodology:
https://learn.microsoft.com/pt-br/azure/security/develop/threat-modeling-tool
e.g.

The strategy of drawing a threat tree is a good approach to sequentially explain the path to exploit a given threat:

It is important during Threat Modeling to have a clear understanding of the threat profiles, that is, the profiles of attackers that can exploit certain threats, which may include figures such as:
-> Spammer
-> Troll
-> Ransomware Hacker
-> Hacktivist
-> Organized Crime
-> fraudster
-> Cyber Espionage (governmental, industrial)
-> Cyber terrorism
-> Hacker
etc...
A security requirements check can be listed in a threat modeling to help prevent threats that were initially identified and correlated with the chosen threat identification model, for example:
ASVS is a great framework for this, as it provides requirements for testing technical application security controls and a list of requirements for secure development.
https://owasp.org/www-project-application-security-verification-standard/
CIS Critical Security Controls Version 8 can also be implemented during Threat Modeling, and is a set of prioritized best practices for mitigating cyber attacks.
https://www.cisecurity.org/controls/v8
It is necessary to use a Risk Classification Methodologies in the elaboration of Threat Modeling, which will serve as a basis for prioritization, giving a focal point to the greatest risks, among the most used methodologies are:
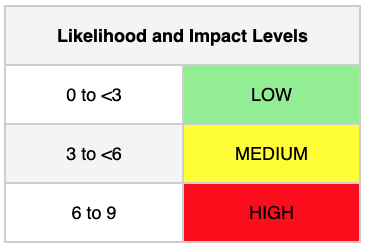
Below are the probability levels and impact:
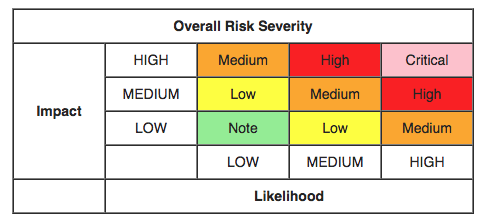
The calculation of Impact x Probability results in the Overall Risk Gravity, following the OWASP Risk Rating methodology.
https://owasp.org/www-community/OWASP_Risk_Rating_Methodology
In this part, to support the penetration tests that may occur after the threat modeling work, possible attack vectors are listed that will be correlated with threats using CAPEC MITRE.
https://capec.mitre.org/
The Pentest with Threat Modeling approach aims to implement a more comprehensive threat analysis strategy adding greater executive value by defining specific risks for the business, and also adds value to Pentest execution, since with more information provided about the application architecture, the pentest will be performed with better efficiency.
The structure of a pentesting report with a threat modeling approach would look like this:
-> Architecture Information and Threat Identification
-> Executive Report
-> Architecture Information
-> Technical Report
-> Identified Vulnerabilities
-> Risk Classification
-> Remediation report
-> Threat Prioritization
-> Report Pentest with Threat Modeling Approach
-> Other Docs:
https://threatmodeler.com/threat-modeling-for-security-penetration-testing/
https://www.triaxiomsecurity.com/threat-modeling-for-penetration-testers/
-> AWS Cloud
https://github.com/EasyAppSecurity/aws-threat-modeling-tool-template
-> Azure Cloud and Medical Device
https://github.com/microsoft/threat-modeling-templates
-> Automotive Threat Modeling
https://github.com/zhendongma/Automotive_Threat_Modeling
-> Other
https://github.com/matthiasrohr/OTMT