Assume AWS roles under the motto "don't make me think".
awscredx has a goal to make the role assumption on the command line simple and intuitive.
Download the binary.
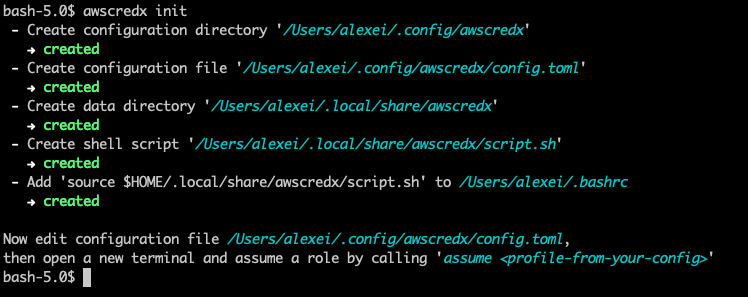
Add awscredx into your PATH and call awscredx init.
It will print what it has done.
The awscredx init sets up a shell script with the function assume.
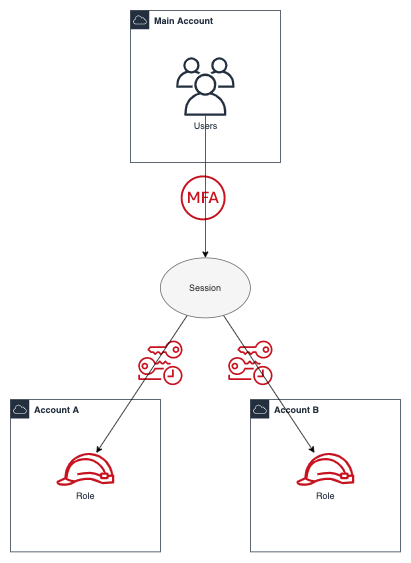
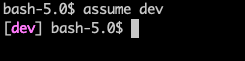
In a new shell you can call assume <profile name> to assume the role from <profile name>.
- Fancy colorful profile name in your prompt with remaining time until expiration.
- Support for
bash,zshandfish.
Well documented configuration file.
[profiles]
dev = "arn:aws:iam::123456589012:role/Admin"
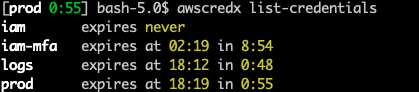
prod = "arn:aws:iam::123456589013:role/TestRole"You can print the web console sign-in URL for the currently assumed profile.
Or you can make awscredx directly open the sign-in URL in your default web browser.
awscredx web-console-signin --service ecs --open-in-browserYou can assume a role k8s-admin from a role prod that is in turn assumed from your main account credentials.
[profiles.k8s-admin]
role_arn = "arn:aws:iam::123456589014:role/K8sAdminRole"
parent_profile = "prod"# Uncomment the following line to enable automatic credentials rotation of the main profile every N days.
# rotate_credentials_days = 7The MFA is read from your Yubikey so you do not need to type it.
It is just a single binary that creates all required helper shell scripts.
It explains what has been done.
In case you are behind a corporate proxy.
MIT