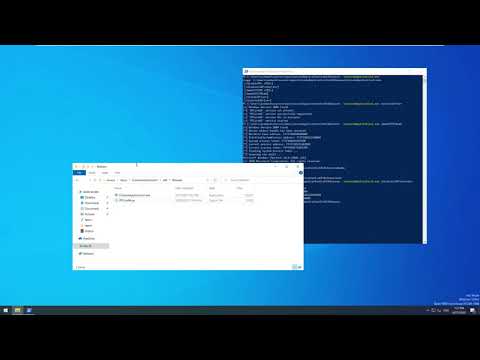
Tool to bypass LSA Protection (aka Protected Process Light)
I’ve noticed there is a common misconception that LSA Protection prevents attacks that leverage SeDebug or Administrative privileges to extract credential material from memory, like Mimikatz. LSA Protection does NOT protect from these attacks, at best it makes them slightly more difficult as an extra step needs to be performed.
- Open PPLKiller.sln wiht Visual Studio 2019 and build a Release binary which will be saved in PPLKiller\x64\Release\PPLKiller.exe
- Place the RTCore64.sys (see below) into the same folder as the PPLKiller.exe executable.
Download it HERE OR
- Install 7-Zip if you dont already have it
- Download and extract MSIAfterburnerSetup462Beta2.exe from http://download-eu2.guru3d.com/afterburner/[Guru3D.com]-MSIAfterburnerSetup462Beta2.zip
- Right-click MSIAfterburnerSetup462Beta2.exe and chose "Open archive"
- Select "RTCore64.sys" and chose Extract in the top menu
- Put THIS file in the same directory as PPLKiller.exe
You'll always want to run PPLKiller.exe /installDriver first, and then an attack like PPLKiller.exe /disableLSAProtection and lastly cleanup with PPLKiller.exe /uninstallDriver