| description |
|---|
This book contains a bunch of info, scripts and knowledge used during my pentests. |
Pentest Guide
Wiki:
- Make a recon!
- Scan ports?
- Doing a web pentest? Check out common attacks!
- Kubernetes, Docker cloud services.
- Mobile Android and iOS
- Burp Suite is the to go tool together with the preferred extensions
- For web services use Pentesting Web Checklist
- Install https://blackarch.org/index.html or https://www.kali.org
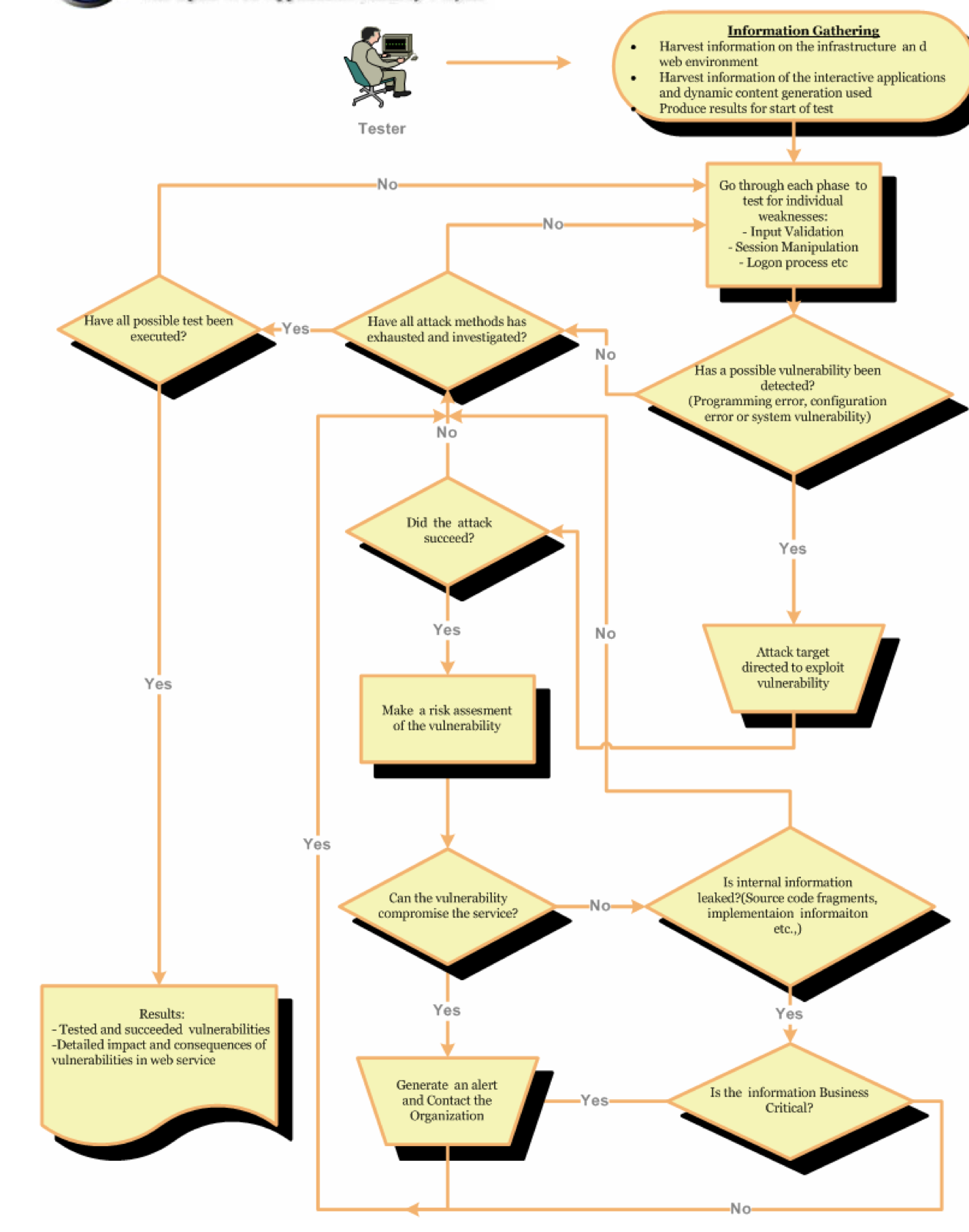
- The penetration test starts by gathering all possible information available regarding the infrastructure and applications involved. This stage is paramount as without a solid understanding of the underlying technology involved, sections may be missed during the testing phase
- The test should follow all the different phases described below
- Testers should attempt to exploit all discovered vulnerabilities. Even if the exploitation fails, the tester will have a better understanding of the vulnerability risk
- Any information returned by checking for vulnerabilities, for example, programming errors, source code retrieval or other internal information disclosure, should be used to re-assess the overall understanding of the application and how it performs
- If at any point during the testing a vulnerability is detected, which may lead to the successful compromise of the target or disclose business-critical information, the relevant contact for the company should be contacted immediately and made aware of the situation and risks involved.
Vulnerability Types
AppDOS
Flaws which may would allow an attacker to completely or partially prevent users from using an application properly.
AppDOS.Flood
Used for application denial of service problems that involve saturating a limited resource shared by all users of the application, such as disk space, CPU, network bandwidth, database connections, or memory.
AppDOS.Lockout
Used for application denial of service problems that involve using up a resource or limit allocated to users, such as failed logon attempts, messages, or transactions.
AccessControl
Problems which may allow users to access assets or functions they are not authorized for. Frequently, there is no access control mechanism where there should be. A proper access control mechanism should enforce the principles of a reference monitor: tamperproof, and analyzable.
Authentication
Used for problems related to determining the identity of individuals or entities and authenticating that identity.
Authentication.User
Used for issues related to identification and authentication of people who are intended to use an application. Problems with usernames, passwords, tokens, smartcards, biometrics, and other credentials are examples.
Authentication.UserManagement
Used for problems related to managing a set of users, especially the security relevant information such as roles, privileges, authorizations, groups, social security numbers, credit card numbers, and other sensitive information. Also problems with creating new users, registration, granting rights, and terminating access.
Authentication.Entity
Used for problems with authenticating automated systems, such as web services, databases, directories, and others. Examples include secure credential storage, securing transport, changing credentials, and terminating access.
Authentication.SessionManagement
Used for problems with issuing, using, protecting, changing, and terminating session identifiers of all kinds. Session identifiers stand in the place of authentication credentials yet are frequently not protected as carefully.
BufferOverflow
Flaws which may allow an attacker to use format strings to overwrite locations in memory, allowing data to be changed, program control to be altered, or the program to crash.
BufferOverflow.Heap
Flaws which may allow an attacker to overflow memory that is dynamically allocated by the application. The OWASP Web Application Penetration Check List This document is released under the GNU documentation license and is Copyrighted to the OWASP Foundation. You should read and understand that license and copyright conditions.
BufferOverflow.Stack
Flaws which may allow an attacker to write data into the stack, causing the program to crash or transfer control.
BufferOverflow.Format
Flaws which may allow an attacker to use format strings to overwrite locations in memory, allowing data to be changed, program control to be altered, or the program to crash.
Concurrency
Used for errors in multithreaded environments that allows data to be shared or corrupted. Examples include variables that are shared between threads and cause time-of-check-time-of-use (TOCTOU) problems, broken singleton patterns, and poor cache design.
ConfigurationManagement
Used to describe problems in the configuration of an application or application environment.
ConfigurationManagement.Administration
Used for problems in the application's mechanisms that enable remote administration, such as user management, credential management, database management, and other configuration options.
ConfigurationManagement.Application
Used to describe problems in the application's configuration, such as mis-configured security mechanisms, default programs, unused code, and unnecessarily enabled features.
ConfigurationManagement.Infrastrure
Used for problems with the configuration of the application's infrastructure, such as the web and application servers, filters, and external security mechanisms.
Cryptography
Used for problems related to encryption, decryption, signing, and verification.
Cryptography.Algorithm
Used for cryptographic algorithm selection, implementation, and analysis problems.
Cryptography.KeyManagement
Used for issues with certificate storage, tokens, revocation, certificates, key stores, issuing keys, and other key issues
DataProtection
Used for issues related to inappropriate disclosure of data.
DataProtection.Storage
Used for problems storing data securely, including storage of credentials, keys, and other sensitive information. Mistakes related to cryptographic mechanisms include poor sources of randomness, bad choice of algorithm, and poor implementation.
DataProtection.Transport
Used for problems related to secure transfer of information. Frequently, this will refer to problems with SSL or TLS configuration, but could include other protocols with security features.
ErrorHandling
Used for problems in handling errors, including printing stack traces to the screen, fail open security mechanisms, allowing errors to affect the operation of the entire application, and revealing too much information about a failure. The OWASP Web Application Penetration Check List This document is released under the GNU documentation license and is Copyrighted to the OWASP Foundation. You should read and understand that license and copyright conditions.
InputValidation
Used for issues related to failure to validate un-trusted input before it is relied on by an application.
InputValidation.User
Used for input validation problems where the input comes from a human user, such as HTTP request parameters, command line input, or input events from an application's GUI.
InputValidation.Network
Used for input validation problems where the input comes from a network protocol, such as HTTP headers, sequence numbers, or other protocol fields.
InputValidation.File
Used for input validation problems where the input comes from a file, such as a properties file, batch data file, flat-file databases, or other file based data.
Injection
Problems which may allow an attacker to bury commands into data and have them interpreted by some system that the data reaches.
Injection.SQL
Flaws which may allow an attacker to inject special characters and commands into a SQL database and modify the intended query. The attack might attempt to change the meaning of the query, or might attempt to chain additional commands.
Injection.HTML
Flaws which may allow an attacker to inject HTML into an application and modify the appearance of HTML generated by that application. For example, an attacker might inject an unwanted IMG tag into a guest book, and offend other users.
Injection.OSCommand
Flaws which may allow an attacker to inject special characters and commands into the operating system command shell and modify the intended command. The attack might attempt to modify how a program is invoked, or might attempt to chain additional commands.
Injection.LDAP
Flaws which may allow an attacker to inject special characters and search terms into an LDAP server and modify the intended query.
Injection.XSS
Flaws which may allow an attacker to send and execute malicious scripts through a web application. Stored XSS attacks store the script in the web application. Reflected XSS attacks are bounced off a web application in real time and require a user to be tricked into sending the request containing the attack.
Monitoring
Used for issues related to monitoring the security posture of a web application.
Monitoring.Logging
Used for issues concerning the proper logging of events, including what should be logged, how it should be logged, how logs should be reviewed, and other issues related to accountability.
Monitoring.Detection
Used for issues related to the detection of attacks on an application, how attacks should be handled, what information should be gathered, and who should be notified