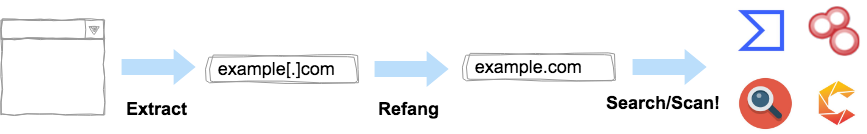
Mitaka is a browser extension for OSINT (open source intelligence) search which can:
- Extract & refang IoCs (indicators of compromise) from a selected block of text.
- E.g.
example[.]comtoexample.com,test[at]example.comtotest@example.com,hxxp://example.comtohttp://example.com, etc. - You can find all the refang techniques in here.
- E.g.
- Search / scan it on various engines.
- E.g. VirusTotal, urlscan.io, Censys, Shodan, etc.
| Name | Desc. | E.g. |
|---|---|---|
| asn | ASN | AS13335 |
| btc | BTC address | 1A1zP1eP5QGefi2DMPTfTL5SLmv7DivfNa |
| cve | CVE number | CVE-2018-11776 |
| domain | Domain name | github.com |
| Email address | test@test.com |
|
| eth | Ethereum address | 0x32be343b94f860124dc4fee278fdcbd38c102d88 |
| gaPubID | Google Adsense Publisher ID | pub-9383614236930773 |
| gaTrackID | Google Analytics Tracker ID | UA-67609351-1 |
| hash | MD5, SHA1, SHA256 | 44d88612fea8a8f36de82e1278abb02f |
| ip | IPv4 address | 8.8.8.8 |
| url | URL | https://github.com |
| Name | URL | Supported types |
|---|---|---|
| AbuseIPDB | https://www.abuseipdb.com | IP |
| AnyRun | https://app.any.run | Hash |
| apklab | https://apklab.io | Hash (SHA256) |
| archive.org | https://archive.org | URL |
| archive.today | http://archive.fo | URL |
| BGPView | https://bgpview.io | IP, ASN |
| BinaryEdge | https://app.binaryedge.io | IP, domain |
| BitcoinAbuse | https://www.bitcoinabuse.com | BTC |
| BitcoinWhosWhos | https://bitcoinwhoswho.com | BTC |
| Blockchain.com | https://www.blockchain.com | BTC |
| Blockchair | https://blockchair.com | BTC, ETH |
| BlockCypher | https://live.blockcypher.com | BTC |
| Censys | https://censys.io | IP, domain, ASN |
| Checkphish | https://checkphish.ai | IP, domain |
| crt.sh | https://crt.sh | Domain |
| DNSlytics | https://dnslytics.com | IP, domain |
| DomainBigData | https://domainbigdata.com | IP, domain, email |
| DomainTools | https://www.domaintools.com | IP, domain |
| DomainWatch | https://domainwat.ch | Domain, email |
| EmailRep | https://emailrep.io | |
| FOFA | https://fofa.so | IP, domain |
| FortiGuard | https://fortiguard.com | IP, URL, CVE |
| Google Safe Browsing | https://transparencyreport.google.com | Domain, URL |
| GreyNoise | https://viz.greynoise.io | IP, domain, ASN, CVE |
| Hashdd | https://hashdd.com | Hash |
| Hurricane Electric | https://bgp.he.net/ | IP, domain, ASN |
| HybridAnalysis | https://www.hybrid-analysis.com | IP, domain, hash |
| Intelligence X | https://intelx.io | IP, domain, URL, email, BTC |
| Intezer | https://analyze.intezer.com | Hash |
| IPinfo | https://ipinfo.io | IP, ASN |
| IPIP | https://en.ipip.net | IP, ASN |
| Joe Sandbox | https://www.joesandbox.com | Hash |
| MalShare | https://malshare.com | Hash |
| Maltiverse | https://www.maltiverse.com | Domain, hash |
| MalwareBazaar | https://bazaar.abuse.ch | Hash |
| Malwares | https://www.malwares.com | Hash |
| NVD | https://nvd.nist.gov | CVE |
| OOCPR | https://data.occrp.org | |
| ONYPHE | https://www.onyphe.io | IP |
| OpenTIP | https://opentip.kaspersky.com | Hash |
| OTX | https://otx.alienvault.com | IP, domain hash |
| Pulsedive | https://pulsedive.com | IP, domain, URL, hash |
| Radar | https://radar.cloudflare.com | IP, domain |
| RiskIQ | http://community.riskiq.com | IP, domain, email, Google Analytics Tracker ID |
| Robtex | https://www.robtex.com | IP, domain |
| Scumware | https://www.scumware.org | IP, domain, hash (MD5) |
| SecurityTrails | https://securitytrails.com | IP, domain, email |
| Shodan | https://www.shodan.io | IP, domain, ASN |
| Sploitus | https://sploitus.com | CVE |
| SpyOnWeb | http://spyonweb.com | IP, domain, Google Adsense Publisher ID, Google Analytics Tracker ID |
| Spyse | https://spyse.com | IP, domain, ASN |
| Talos | https://talosintelligence.com | IP, domain |
| ThreatConnect | https://app.threatconnect.com | IP, domain, email |
| ThreatCrowd | https://www.threatcrowd.org | IP, domain, email |
| ThreatMiner | https://www.threatminer.org | IP, domain, hash |
| TIP | https://threatintelligenceplatform.com | IP, domain |
| Triage | https://tria.ge | Hash, URL |
| URLhaus | https://urlhaus.abuse.ch | IP, domain |
| Urlscan | https://urlscan.io | IP, domain, ASN, URL |
| ViewDNS | https://viewdns.info | IP, domain, email |
| VirusTotal | https://www.virustotal.com | IP, domain, URL, hash |
| VMRay | https://www.vmray.com | Hash |
| Vulmon | https://vulmon.com | CVE |
| VulncodeDB | https://www.vulncode-db.com | CVE |
| VxCube | http://vxcube.com | IP, domain, hash |
| WebAnalyzer | https://wa-com.com | Domain |
| X-Force Exchange | https://exchange.xforce.ibmcloud.com | IP, domain, hash |
| ZoomEye | https://www.zoomeye.org | IP |
| name | url | supported types |
|---|---|---|
| Browserling | https://www.browserling.com | URL |
| HybridAnalysis | https://www.hybrid-analysis.com | URL |
| Urlscan | https://urlscan.io | IP, domain, URL |
| VirusTotal | https://www.virustotal.com | URL |
This browser extension shows context menus based on a type of IoC you select and then you can choose what you want to search / scan on.
Examples:
Also, there is a how-to article about Mitaka by Null Byte.
Note:
Please set your API keys in the options for enabling HybridAnalysis, urlscan.io and VirusTotal scans.
You can enable / disable a search engine on the options page based on your preference.
This browser extension requires the following permissions.
Read and change all your data on the websites you visit:- This extension creates context menus dynamically based on what you select on a website.
- It means this extension requires reading all your data on the websites you visit. (This extension doesn't change anything on the websites)
Display notifications:- This extension makes a notification when something goes wrong.
I don't (and will never) collect any information from the users.
- Q. The context menu is not showing.
- A. Sometimes it takes time to show the context menu in Chrome. Please wait for a second after selecting. Then the context menu will show.
- CrowdScrape
- Gotanda
- Sputnik
- ThreatConnect Integrated Chrome Extension
- ThreatPinch Lookup
- VTchromizer
Read the contribution guide and join the contributors.