This repo contains my write-ups and scripts for solving the PortSwigger WebSecurity Academy. I plan to vaguely follow the learning path provided by PortSwigger, however, I expect to skip some of the expert-level labs initially.
If you find any problems with the descriptions or the scripts, feel free to open an issue to help me improve the content of this repository.
I also post these write-ups and other content on medium.com. If you want to get notifications there, follow my profile on medium.
My ultimate goal is to obtain a level of expertise in the matter at hand to be able to pass the Burp Suite Certified Practitioner examination. As such, I not only want to solve the labs but also understand why the solution works.
The scripts are there to help me obtain some routine for creating such script files. Such a skill may not be that important to solve individual labs or the exam itself. But in real-life scenarios the ability to quickly create proofs-of-concept for vulnerabilities is helpful.
So I create the scripts to learn about python and how to use it to interact with websites. Can these scripts be used to cheat the progress in the labs? Yes, but you only cheat yourself.
| ID | Topic | Apprentice | Practitioner | Expert |
|---|---|---|---|---|
| Server-side topics | ||||
| 01 | SQL injection | ✔️ 2/2 | ✔️ 15/15 | - |
| 02 | Authentication | ✔️ 3/3 | ✔️ 9/9 | ✔️ 2/2 |
| 03 | Directory traversal | ✔️ 1/1 | ✔️ 5/5 | - |
| 04 | Command inection | ✔️ 1/1 | ✔️ 4/4 | - |
| 05 | Business logic vulnerabilities | ✔️ 4/4 | ✔️ 7/7 | - |
| 06 | Information disclosure | ✔️ 4/4 | ✔️ 1/1 | - |
| 07 | Access control | ✔️ 9/9 | ✔️ 4/4 | - |
| 08 | File upload vulnerabilities | ✔️ 2/2 | ✔️ 4/4 | ✖️ 0/1 |
| 09 | Server-side request forgery (SSRF) | ✔️ 2/2 | ✔️ 3/3 | ✔️ 2/2 |
| 10 | XXE injection | ✔️ 2/2 | ✔️ 6/6 | ✔️ 1/1 |
| Client-side topics | ||||
| 11 | Cross-site scripting (XSS) | ✔️ 9/9 | ✖️ 13/15 | ✖️ 0/6 |
| 12 | Cross-site request forgery (CSRF) | ✔️ 1/1 | ✔️ 7/7 | - |
| 13 | Cross-origin resource sharing (CORS) | ✔️ 2/2 | ✔️ 1/1 | ✖️ 0/1 |
| 14 | Clickjacking | ✔️ 3/3 | ✔️ 2/2 | - |
| 15 | DOM-based vulnerabilities | - | ✔️ 5/5 | ✖️ 0/2 |
| 16 | WebSockets | ✔️ 1/1 | ✔️ 2/2 | - |
| Advanced topics | ||||
| 17 | Insecure deserialization | ✔️ 1/1 | ✖️ 5/6 | ✖️ 0/3 |
| 18 | Server-side template injection | - | ✖️ 2/5 | ✖️ 0/2 |
| 19 | Web cache poisoning | - | ✖️ 0/9 | ✖️ 0/4 |
| 20 | HTTP Host header attacks | ✔️ 2/2 | ✖️ 0/4 | ✖️ 0/1 |
| 21 | HTTP request smuggling | - | ✖️ 1/15 | ✖️ 0/7 |
| 22 | OAuth authentication | ✔️ 1/1 | ✖️ 1/4 | ✖️ 0/1 |
| 23 | JWT attacks | ✔️ 2/2 | ✖️ 2/4 | ✖️ 0/2 |
| 24 | Client-side prototype pollution | - | ✖️ 0/5 | - |
| 25 | Essential skills | - | ✖️ 0/1 | - |
Current status of script solutions:
For the most part, I try to stick with using Burp Suite Pro and a browser only. I recommend using a cookie editor in the browser as well as a quick switch to using Burp Proxy.
Personally, I use Cookie-Editor for manipulating cookies as well as Proxy SwitchyOmega to quickly (or even automatically) switch to Burp Proxy.
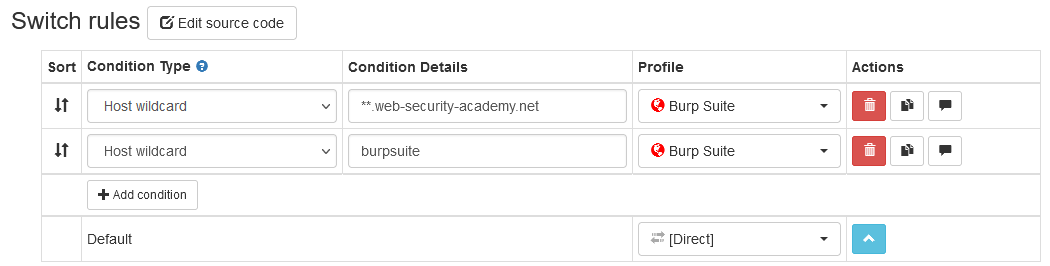
If you like to have the switching to proxy automated, you can setup a switch profile like this:
This way, all lab traffic automatically goes to Burp, while all other traffic gets the direct connection.
PortSwigger has very nice learning resources on their website. Basically, everything required to get started is there.
For a nice video series I can recommend the video series of Rana Khalil on youtube. At the current time, she uploaded videos that cover SQL Injection and CSRF, but she shows everything she does and explains very nicely. And she uploads a new lab video each week (roughly), so I'm sure over time she will cover the full content of the WebSecurity Academy.