The question of how to store your private keys in a way that is both secure and resistant to loss or damage is a challenge.
There are a number of different approaches that different hardware and software wallets use and one that has been gaining popularity, particularly with stateless wallets, is SeedQR… The thing is that while SeedQR is much quicker and easier than a standard seed phrase, storing and loading private keys via SeedQR all the time has it’s own issues relating to security, robustness and privacy…
That said, I think that saving secrets to a PIN protected Javacard addresses all of these issues in a really affordable and accessible way… I have been doing to integrate the Seedkeeper from Satochip with Seedsigner… Basically as a proof of concept… This is now at a point where it can be considered Beta software, in that it is mostly feature complete. (Though will still likely have other bugs and tweaks to come) You can read more about the rationale, software and hardware being used here
All releases are now running SeedSigner-OS and are built via BuildRoot just like official builds, meaning that the MicroSD card can be removed for normal operation. (Though the MicroSD needs to be left in while building and flashing Java applets or flashing SeedSigner images to MicroSD) This also means that installation images are much smaller and are also reproducible.
- Multiple Smartcard interface options…
- Standard USB CCID/PCSC readers
- PN532 NFC Reader Connected via I2C
- USB Phoenix Type "Sim Reader" supported via OpenCT
- Saving and Loading Seeds & Passphrases
- Supports loading of Seed, Seed+Passphrase in one go, or loading passphrase independently. (Potentially from a different SeedKeeper)
- Saving and Loading Multisig Descriptors
- Also changed default behavior to keep Descriptor loaded until manually cleared. (Including descriptor appearing in the Address Explorer when loaded)
- Descriptors are split up into a template and xpubs before being saved to SeedKeeper.
- Saving and loading generic secrets to a Seedkeeper card
- These secrets can be either viewed as text or displayed as a generic text QR code.
- Initialising Satochip Cards with SeedSigner
- Load any Seed from the SeedSigner on to the Satochip Card
- Enable 2FA on the Satochip Card
- Flashing Satochip Applets to blank Javacards
- Firmware comes bundled with applets for SeedSigner, Satochip and Satodime (Releases from Satochip Github)
- Firmware is also bundled with the source code for all three projects, along with a modified varient for THD-89 based Javacards. (This can be built from source on-device at run-time)
- MicroSD Card Tools
- Flashing MicroSD Cards with official SeedSigner Images (Bundled)
- Verification of freshly flashed MicroSD cards against known images
- Secure Wipe (Both with zeros and random data)
- Add ability to lock/unlock/manage Javacards
- Add ability to view additional sttings/information for the Satochip cards
- Tidy up code and reduce re-use
- Project Summary
- Shopping List
- Software Installation
- Enclosure Designs
- SeedQR Printable Templates
- Build from Source
- Developer Local Build Instructions
The goal of SeedSigner is to lower the cost and complexity of Bitcoin multi-signature wallet use. To accomplish this goal, SeedSigner offers anyone the opportunity to build a verifiably air-gapped, stateless Bitcoin signing device using inexpensive, publicly available hardware components (usually < $50). SeedSigner helps users save with Bitcoin by assisting with trustless private key generation and multisignature (aka "multisig") wallet setup, and helps users transact with Bitcoin via a secure, air-gapped QR-exchange signing model.
Additional information about the project can be found at SeedSigner.com.
You can follow @SeedSigner on Twitter for the latest project news and developments.
If you have specific questions about the project, our Telegram Group is a great place to ask them.
- Calculate the final word (aka checksum) of a 12- or 24-word BIP39 seed phrase
- Create a 24-word BIP39 seed phrase with 99 dice rolls or a 12-word with 50 rolls (Verifying dice seed generation)
- Create a 12- or 24-word BIP39 seed phrase via image entropy from the onboard camera
- Temporarily stores seeds in memory while the device is powered; all memory is wiped when power is removed
- SD card removable after boot to ensure no secret data can be written to it
- Guided interface to manually transcribe a seed to the SeedQR format for instant seed loading (demo video here)
- BIP39 passphrase (aka "word 25") support
- Native Segwit Multisig XPUB generation
- PSBT-compliant; scan and parse transaction data from animated QR codes
- Sign transactions & transfer XPUB data using animated QR codes (demo video here)
- Live preview during image entropy seed generation and QR scanning UX
- Optimized seed word entry interface
- Support for Bitcoin Mainnet & Testnet
- Support for custom user-defined derivation paths
- On-demand receive address verification
- Address Explorer for single sig and multisig wallets
- User-configurable QR code display density
- Responsive, event-driven user interface
- Built for compatibility with Specter Desktop, Sparrow, and BlueWallet Vaults
- Device takes up to 60 seconds to boot before menu appears (be patient!)
- Always test your setup before transferring larger amounts of bitcoin (try Testnet first!)
- Taproot not quite yet supported
- Slightly rotating the screen clockwise or counter-clockwise should resolve lighting/glare issues
- If you think SeedSigner adds value to the Bitcoin ecosystem, please help us spread the word! (tweets, pics, videos, etc.)
- Multi-language support
- Significantly faster boot time
- Reproducible builds
- Port to MicroPython to broaden the range of compatible hardware to include low-cost microcontrollers
- Other optimizations based on user feedback!
To build a SeedSigner, you will need:
- Raspberry Pi Zero (preferably version 1.3 with no WiFi/Bluetooth capability, but any Raspberry Pi 2/3/4 or Zero model will work, Raspberry Pi 1 devices will require a hardware modification to the Waveshare LCD Hat, as per the instructions here)
- Waveshare 1.3" 240x240 pxl LCD (correct pixel count is important, more info at https://www.waveshare.com/wiki/1.3inch_LCD_HAT)
- Pi Zero-compatible camera (tested to work with the Aokin / AuviPal 5MP 1080p with OV5647 Sensor)
Notes:
- You will need to solder the 40 GPIO pins (20 pins per row) to the Raspberry Pi Zero board. If you don't want to solder, purchase "GPIO Hammer Headers" for a solderless experience.
- Other cameras with the above sensor module should work, but may not fit in the Orange Pill enclosure
- Choose the Waveshare screen carefully; make sure to purchase the model that has a resolution of 240x240 pixels
As is the nature of pre-packaged software downloads, downloading and using the prepared SeedSigner release images means implicitly placing trust in the people preparing those images; in our project the released images are prepared and signed by the eponymous creator of the project, SeedSigner "the person". That individual is additionally the only person in possession of the PGP keys that are used to sign the release images.
Starting with v0.7.0, the images distributed via GitHub are reproducible. This means you and others can verify the released images are byte-for-byte the same when built from source. You can contribute to this project by building from source and sharing the hash of the final images.
Instructions to build a SeedSigner OS image (using precisely the same process that is used to create the prepared release images) have been made available. We have put a lot of thought and work into making these instructions easy to understand and follow, even for less technical users. These instructions can be found here.
Download the current Version (0.7.0) software image that is compatible with your Raspberry Pi Hardware. The Pi Zero 1.3 is the most common and recommended board.
Note: If you have physically removed the WiFi component from your board, you will still use the image file of the original(un-modified) hardware. (Our files are compiled/based on the processor architecture). Although it is better to spend a few minutes upfront to determine which specific Pi hardware/model you have, if you are still unsure which hardware you have, you can try using the pi0.img file. Making an incorrect choice here will not ruin your board, because this is software, not firmware.
also download these 2 signature verification files to the same folder
The Plaintext manifest file
The Signature of the manifest file
Users familiar with older versions of the SeedSigner software might be surprised with how fast their software downloads now are, because since version 0.6.0 the software image files are now 100x smaller! Each image file is now under 42 Megabytes so your downloads and verifications will be very quick now (and might even seem too quick)!
Once the files have all finished downloading, follow the steps below to verify the download before continuing on to write the software onto a MicroSD card. Next, insert the MicroSD into your assembled hardware and connect the USB power. Allow about 45 seconds for our logo to appear, and then you can begin using your SeedSigner!
Our previous software versions are available here. Choose a specific version and then expand the Assets sub-heading to display the .img file binary and also the 2 associated signature files. Note: The prior version files will have lower numbers than the scripts and examples provided in this document, but the naming format will be the same, so you can edit them as required for signature verification etc.
You can quickly verify that the software you just downloaded is both authentic and unaltered, by following these instructions. We assume you are running the commands from a computer where both GPG and shasum are already installed, and that you also know how to navigate on a terminal.
You must run the following verification before opening or mounting the .img file. Some operating systems modify the file on mount causing verification to fail.
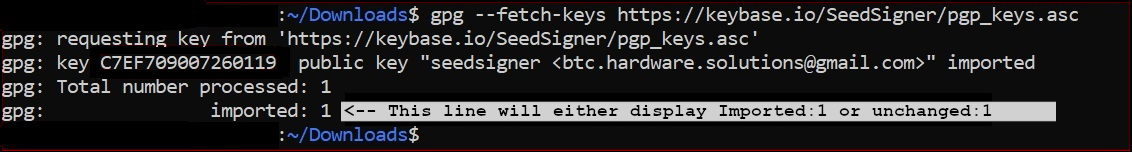
Run GPG's fetch-keys command to import the SeedSigner projects public key from the popular online keyserver called Keybase.io, into your computers keychain.
gpg --fetch-keys https://keybase.io/seedsigner/pgp_keys.asc
The result should confirm that 1 key was either imported or updated. Ignore any key ID's or email addresses shown.
Next, you will run the verify command on the signature (.sig) file. (Verify must be run from inside the same folder that you downloaded the files into earlier. The *'s in this command will auto-fill the version from your current folder, so it should be copied and pasted as-is.)
gpg --verify seedsigner.0.7.*.sha256.txt.sig
When the verify command completes successfully, it should display output like this:
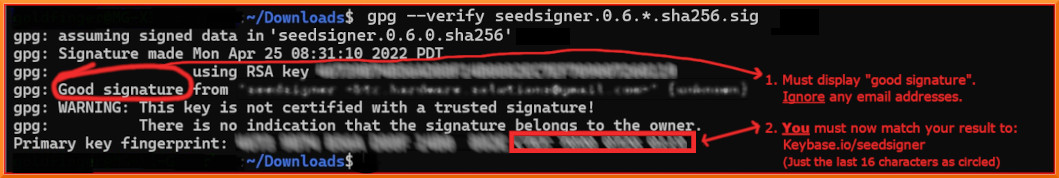
The result must display "Good signature". Ignore any email addresses - only matching Key fingerprints count here. Stop immediately if it displays "Bad signature"!
On the last output line, look at your rightmost 16 characters (the 4 blocks of 4).
Crucially, we must now check WHO that Primary key fingerprint /ID belongs to. We will start by looking at Keybase.io to see if it is the SeedSigner project 's public key or not.
About the warning message:
Since you are about to match the outputted fingerprint/ID against the proofs at Keybase.io/SeedSigner, and thereby confirm who the pubkey really belongs to-, you can safely ignore this warning message:
> WARNING: This key is not certified with a trusted signature!
> There is no indication that the signature belongs to the owner.
More about how the verify command works:
The verify command will attempt to decrypt the signature file (sha256.sig) by trying each public key already imported into your computer. If the public key we just imported (via fetch-keys), manages to: (a) successfully decrypt the .sig file , and (b), that result matches exactly to the clear-text equivalent (.sha256) of the .sig file, then its "a good signature"!
Crucially, we must still manually check who exactly owns the Key ID which gave us that "Good signature". Thats what the warning message means- Who does the matching key really belong to? We will start by looking at keybase.io to see if it is "The SeedSigner project"'s public Key or not. Note that it is the file hashes of .sig and .sha256 that verify compares, not their raw contents.
Now to determine who the Public key ID belongs to: Goto Keybase.io/SeedSigner
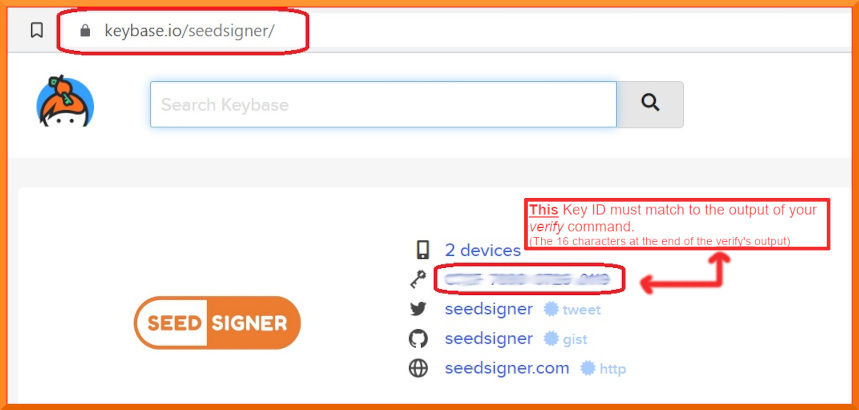
You must now manually compare: The 16 character fingerprint ID (as circled in red above) to, those rightmost 16 characters from your verify command.
If they match exactly, then you have successfully confirmed that your .sig file is authentically from the SeedSigner Project!
Learn more about how keybase.io helps you check that someone (online) is who they say they are:
Keybase.io allows you to independently verify that the public key saved on Keybase.io, is both authentic and that it belongs to the organization it claims to represent. Keybase has already checked the three pubkey file locations cryptographically when they were saved there. You can further verify the key publications if you would like:
- via Keybase: By clicking on any of the three blue badges to see that the "proof" was published at that location. (The blue badge marked as tweet, is in the most human-readable form and it is also a bi-directional link on Twitter)
or, - without keybase (out-of-band): By using these 3 links directly: Twitter, Github and SeedSigner.com. This method can be used if you would like to make an even deeper, independent inspection without relying on Keybase at all, or if the Keybase.io site is no longer valid or it is removed entirely.
Once you have used one of these methods, you will know if the Public Key stored on Keybase, is genuinely from the SeedSinger Project or not.
If the two ID's do not match, then you must stop here immediately. Do not continue. Contact us for assistance in the Telegram group address above.
Now that you have confirmed that you do have the real SeedSigner Project's Public Key (ie the 16 characters match) - you can return to your terminal window. Running the shasum command, is the final verification step and will confirm (via file hashing) that the software code/image files, were also not altered since publication, or even during your download process.
(Prior to version 0.6.0 , your verify command will check the .zip file which contains the binary files.)
On Linux or OSX: Run this command
shasum -a 256 --ignore-missing --check seedsigner.0.7.*.sha256.txt
On Windows (inside Powershell): Run this command
CertUtil -hashfile seedsigner_os.0.7.0.Insert_Your_Pi_Models_binary_here_For_Example_pi02w.img SHA256
On Windows, you must then manually compare the resulting file hash value to the corresponding hash value shown inside the .SHA256 cleartext file.
Wait up to 30 seconds for the command to complete, and it should display:
seedsigner_os.0.7.x.[Your_Pi_Model_For_Example:pi02w].img: OK
If you receive the "OK" message for your seedsigner_os.0.7.x.[Your_Pi_Model_For_Example:pi02w].img file, as shown above, then your verification is fully complete!
All of your downloaded files have now been confirmed as both authentic and unaltered! You can proceed to create/write your MicroSD card😄😄 !!
If your file result shows "FAILED", then you must stop here immediately. Do not continue. Contact us for assistance at the Telegram group address above.
Please recognize that this process can only validate the software to the extent that the entity that first published the key is an honest actor, and their private key is not compromised or somehow being used by a malicious actor.
To write the SeedSigner software onto your MicroSD card, there are a few options available:
| Application | Description | Platform and official Source |
|---|---|---|
| Balena Etcher | The application is called Etcher, and the company that wrote it is called Balena. Hence Etcher by Balena or Balena Etcher | Available for Windows, Mac and Linux |
| Raspberry Pi Imager | Produced by the Raspberry Pi organization. | Available for Windows, Mac and Linux |
| DD Command Line Utility | Built-in to Linux and MacOS, the DD (Data Duplicator) is a tool for advanced users. If not used carefully it can accidentally format the incorrect disk! | Built-in to Linux and MacOS |
Be sure to download the software from the genuine publisher.
Either of the Etcher or Pi Imager software is recommended. Some SeedSigner users have reported a better experience with one or the other. So, if the one application doesn’t work well for your particular machine, then please try the other one.
The writing and verify steps are very quick from version 0.6.0 upwards, so please pay close attention to your screen.
Make sure to set any write-protection physical slider on the MicroSD Card Adapter to UN-locked.
You also don’t need to pre-format the MicroSD beforehand. You dont need to unzip any .zip file beforehand.
Current Etcher and Pi Imager software will perform a verify action (by default) to make sure the card was written successfully! Watching for that verify step to complete successfully, can save you a lot of headaches if you later need to troubleshoot issues where your SeedSigner device doesn’t boot up at power on.
Writing the MicroSd card is also known as flashing.
It will overwrite everything on the MicroSD card.
If the one application fails for you, then please try again using our other recommended application.
Advanced users may want to try the Linux/MacOS DD command instead of using Etcher or Pi Imager, however, a reminder is given that DD can overwrite the wrong disk if you are not careful !
Use the Pi imager software as your first choice on Windows. Windows can sometimes flag the writing of a MicroSD as risky behaviour and hence it may prevent this activity. If this happens, your writing/flashing will fail, hang or wont even begin, in which case you should to try to run the Etcher/Pi-Imager app "As administrator", (right-click and choose that option). It can also be blocked by windows security in some cases, so If you have the (non-default) Controlled Folder Access option set to active, try turning that off temporarily.
The Open Pill enclosure design is all about quick, simple and inexpensive depoloyment of a SeedSigner device. The design does not require any additional hardware and can be printed using a standard FDM 3D printer in about 2 hours, no supports necessary. A video demonstrating the assembly process can be found here. To access the design file and printable model, click here.
The Orange Pill enclosure design offers a more finished look that includes button covers and a joystick topper. You'll also need the following additional hardware to assemble it:
- 4 x F-F M2.5 spacers, 10mm length
- 4 x M2.5 pan head screws, 6mm length
- 4 x M2.5 pan head screws, 12mm length
The upper and lower portions of the enclosure can be printed using a standard FDM 3D printer, no supports necessary. The buttons and joystick nub should ideally be produced with a SLA/resin printer. An overview of the entire assembly process can be found here. To access the design files and printable models, click here.
- Lil Pill by @_CyberNomad
- OrangeSurf Case by @OrangeSurfBTC
- PS4 SeedSigner by @Silexperience
- OpenPill Faceplate by @Revetuzo
- Waveshare CoverPlate by @Adathome1
You can use SeedSigner to export your seed to a hand-transcribed SeedQR format that enables you to instantly load your seed back into SeedSigner.
More information about SeedQRs
 |
Standard SeedQR templates:
- 12-word SeedQR template dots (25x25)
- 24-word SeedQR template dots (29x29)
- 12-word SeedQR template grid (25x25)
- 24-word SeedQR template grid (29x29)
- Baseball card template: 24-word SeedQR (29x29)
CompactSeedQR templates:
- 12-word CompactSeedQR template dots (21x21)
- 24-word CompactSeedQR template dots (25x25)
- 12-word CompactSeedQR template grid (21x21)
- 24-word CompactSeedQR template grid (25x25)
- Baseball card template: 12-word Compact SeedQR (21x21)
- Baseball card template: 24-word Compact SeedQR (25x25)
2-sided SeedQR templates - 8 per sheet Printing settings - (2-sided)("flip on long edge")("Actual Size") If printing on cardstock, adjust your printer settings via its control panel
A4 templates(210mm * 297mm):
- 21x21 - stores 12-word seeds ONLY in CompactSeedQR format ONLY
- 25x25 - stores 12-word or 24 word seeds depending on SeedQR format
- 29x29 - stores 24-word seeds ONLY as plaintext SeedQR format ONLY
Letter templates(8.5in * 11in):
- 21x21 - stores 12-word seeds ONLY in CompactSeedQR format ONLY
- 25x25 - stores 12-word or 24 word seeds depending on format
- 29x29 - stores 24-word seeds ONLY as plaintext SeedQR format ONLY
See the SeedSigner OS repo for instructions.
Raspberry Pi OS is commonly used for development. See the Raspberry Pi OS Build Instructions