Virtual Machine for interpreting EsetVm2 (.evm) binary programs.
Input binaries (.evm) could be compiled from specific Eset assembeler (.easm) files with compiler task/compiler.py. Eset assembler language is described in task/task.pdf. Documentation contains description of file format, bytecode, data encoding, threading model, memory initialization etc. The code examples could be found in task/samples. Precompiled examples are in task/samples/precompiled.
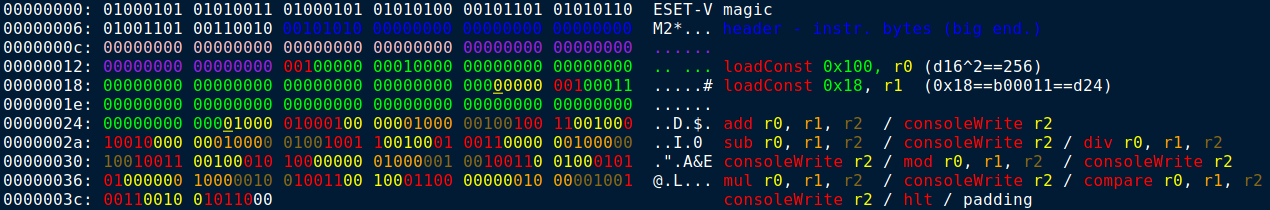
The EsetVm2 virtual machine is able to interpret encoded instructions from input binary file in evm format. It simulates harvard architecture computer with own computing engine, code and data memory, io module, registers, instruction pointer or program counter, stack and also multi-threading module. The virtual machine provides support for instructions related to mathematical computation, program flow changes like function calls and jumps, multi threading support and synchronization, console and file io operations.
make./esetvm2 task/samples/precompiled/math.evm./test.shpython2 task/samples/math.easm task/samples/precompiled/math.evmThe source code could be found under src and includes directories. The task/task.pdf is fully implemented.
Notes related to task and binary files analysis are stored as cherry tree notes analysis/notes/notes.ctb or as web page analysis/notes/ESET_HTML/index.html. There could be found also chapter related to documentation bugs.
I have created some own elementary easm/evm examples for specific testing purposes. They are stored under analysis/samples and analysis/samples/precompiled.
The application was tested with valgrind and it's free of memory leaks.
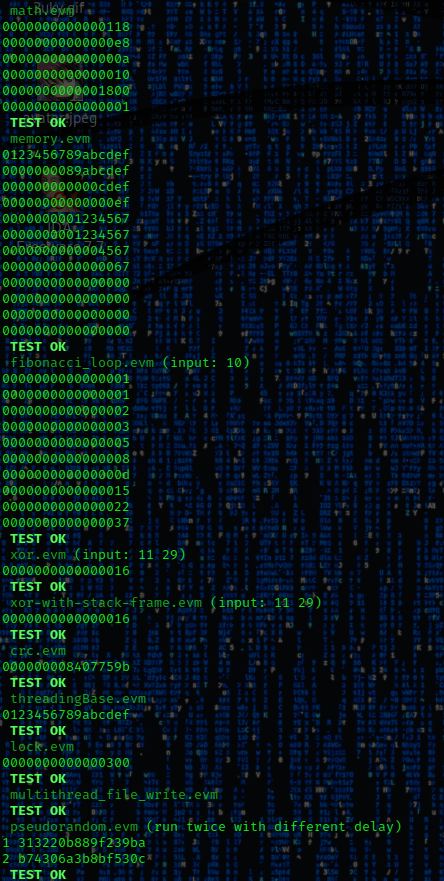
The regression test.sh recompiles esetvm2 application and run it with all input binaries from samples\precompiled. The results are compared with expected outputs stored in analysis\results and specified by samples\sample.txt. The philosophers.evm runs without deadlock they were tested for more then 30 minutes.