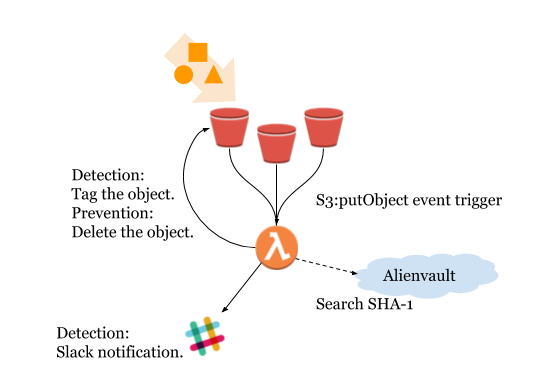
Hunting malware in your s3 bucket by using Alienvault threat intelligence source. Have prevention and detection mode.
Sign up an Alienvault account then go to "https://otx.alienvault.com/api" and get api key. (Alienvault OTX: https://www.alienvault.com/open-threat-exchange)
Follow 'https://api.slack.com/incoming-webhooks' to the 'Getting started with Incoming Webhooks' section's step 3. Let your channel and webhook URL ready.
Creat an IAM role for lambda use and the IAM policy are shown as below. IAM policy:
- Lambda basic execution permission
- s3:getObject
- s3:putObject
Create Lambda function then setting the enviroment variables. Lambda's enviroment variables:
- ALIEN_API_KEY: value is your Alienvault api key.
- ALIEN_URL: 'https://otx.alienvault.com/api/v1/indicators/file/'
- ACTION: 'DETECTION' or 'PREVENTION'
- CONFIDENCE: Recommended value is '0', means any source detect this file is malware the lambda do the action(notify or remove).
- HOOK_URL: your slack webhook URL(Necessary when ACTION is DETECTION)
- SLACK_CHANNEL: your slack channel(Necessary when ACTION is DETECTION)
- LOG_LEVEL: lambda log level(Recommended value is 'info')
- TAG: Recommended value is 'TRUE'(Necessary when ACTION is DETECTION)
Follow 'https://docs.aws.amazon.com/AmazonS3/latest/dev/NotificationHowTo.html' and trigger the lambda function we create.
- Note: You can easily change region by change the URL's region(such as ap-northeast-1 -> us-east-1).
- Setup S3 event trigger is not inclue so setup the S3 event manually is necessary.
Use the sam folder to deploy.
- Setup S3 event trigger is not inclue so setup the S3 event manually is necessary.
MIT License Details are in the LICENSE file.
Please feel free to contact me if you have any questions. :) mailto: anderson.lin0803@gmail.com/ anderson.lin@senao.com.tw