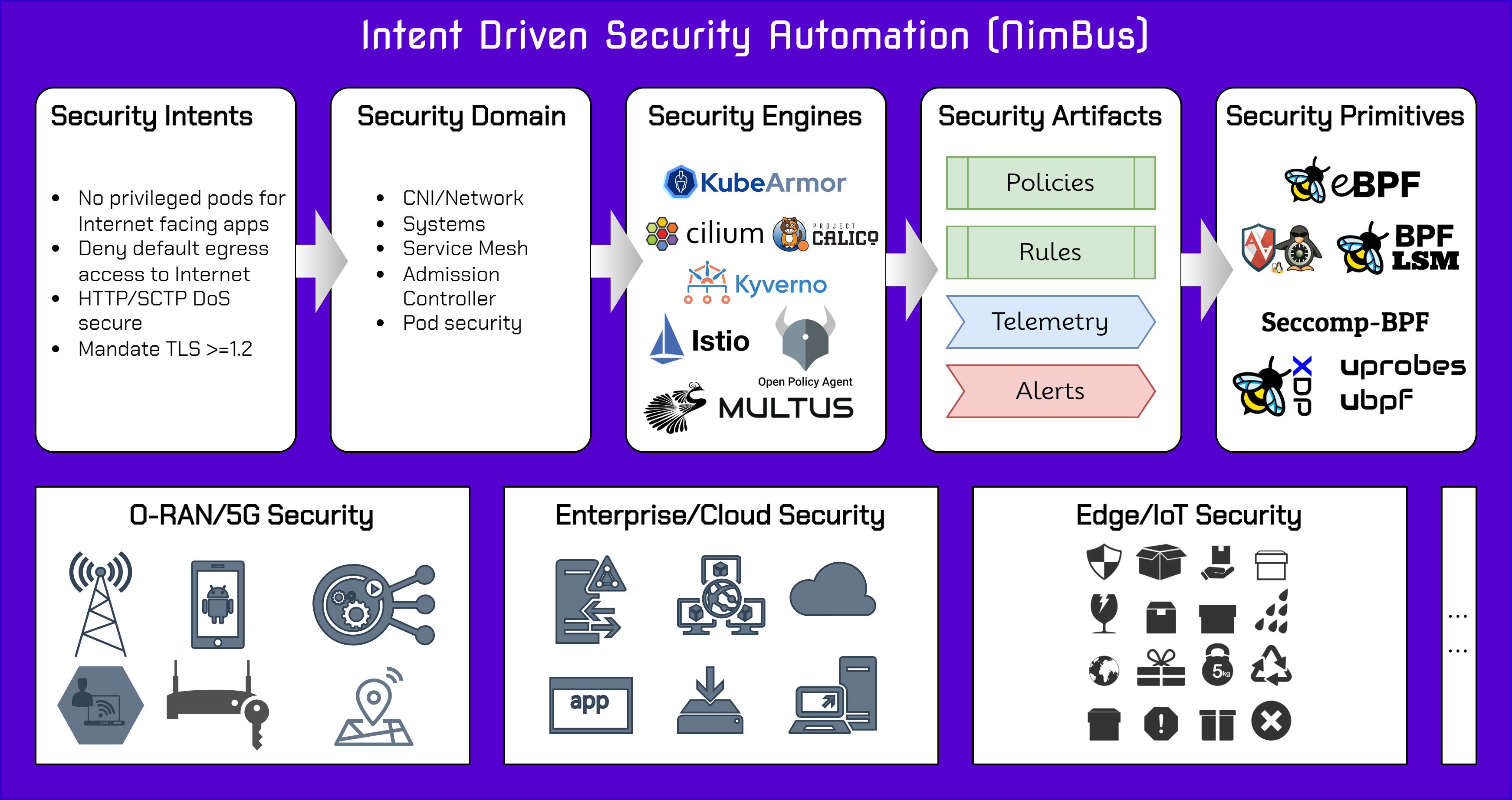
Repository to hold Security Intents in standard template format.
title: Scenario-title
description: Detailed description of the scenario
severity: High/Medium/Low
tags:
- oran
- 5gcore
- generic
detectionMethods: # Mechanisms to detect the threat
- name: Application log
tag:
- mitre/ds0015
description: Description # Optional
url: https://...
- name: Process
tag:
- accuknox/ax0015
description: Description # Optional
url: https://...
mitigationMethods: # Mechanisms to mitigate the threat
- name: Update Software
tag:
- mitre/ds0015
description: desc
url: https://...
- name: User Account Management
tag:
- accuknox/ax0015
description: desc
url: https://...
securityActions:
- sample-sa-1.yaml
- sample-sa-2.yaml
securityIntentBinding: # Set of labels, annotations describing workloads who would be impacted by this threat
- sample-si-binding.yaml
preDeploymentConsiderations: [ ] # Anything that can be done in CI/CD pipelines that can alleviate this threat
references:
- name: ref1
url: https://...
- name: ref2
url: https://...| Title | Description | Severity | Security Actions | References |
|---|---|---|---|---|
| DNS Manipulation | An adversary can manipulate DNS requests to redirect network traffic and potentially reveal end user activity. | high | accuknox/preventLocalDNSHijack, mitre/integrityProtection, mitre/networkTraffic | MITRE FiGHT |
| Exploit Public-Facing Application | High | FGT1190 | ||
| Exploit Semi-public Facing Application | High | mitre/networkTraffic | FGT5029 | |
| gNodeB Component Manipulation | An adversary may compromise a component of gNodeB to affect radio network configuration | high | MITRE FiGHT | |
| Protocol Tunneling | Adversaries may tunnel network communications to and from a victim system within a separate protocol to avoid detection/network filtering and/or enable access to otherwise unreachable systems. | High | mitre/encryptSensitiveInformation, mitre/networkTraffic | FGT1572.501 |
| Regitration of Malicious Network Functions | An adversary, such as an insider to the MNO or vendor, could install a malicious NF into the core network, in order to launch other attacks or get access to information. | high | mitre/networkSegmentation | MITRE FiGHT |
| Rogue xApps unauthorized access | Malicious xApps may gain unauthorized access to near-RT RIC and E2 nodes | High | mitre/credentialAccessProtection, mitre/networkSegmentation | FGT5034 |
| Software Deployment Tools | Adversaries may gain access to and use third-party software suites installed within an enterprise network, such as administration, monitoring, and deployment systems, to move laterally through the network. | High | accuknox/preventPkgInstall | FGT1072 |
| SupplyChainCompromise | Adversaries may manipulate products or product delivery mechanisms prior to receipt by a final consumer for the purpose of data or system compromise. | High | FGT1195 | |
| Unauthorized access to Network Exposure Function (NEF) via token fraud | An adversary controlling an (external) Application Function (AF) presents a fraudulent OAuth access token to access Network Exposure Function (NEF) services | High | FGT5011 | |
| Valid Accounts | High | FGT1078 |
- Fork and clone this repository
- Copy
res/threatTemplate.yamltemplate file in threats/tacticdirectory and edit the file's contents to accurately reflect the specific threat information. For e.g.,executiontactic from MITRE FiGHT.cp res/threatTemplate.yaml threats/execution/threat-name.yaml
- Create the Security Actions file(s) you listed in the
.securityActionsfield of thethreat-name.yamlfile, and place them within the actions directory. For e.g.,... securityActions: - sample-sa-1.yaml - sample-sa-2.yaml ...
- Run
make - Raise a PR