Example of accessing Amazon API Gateway with Amazon Cognito User Pools and Okta OpenID Connect Federation
The purpose of this codebase is to illustrate a possible implementation of the Authorization Code grant type, with Amazon Cognito and an OpenID Connect provider. The access token, retrieved as the final outcome of the flow, is then used by the client to access an endpoint, exposed by Amazon API Gateway and implemented by an AWS Lambda function.
The client is made of 2 software components: some basic HTML and JavaScript code runing in the user agent (browser) and an Express application running on Node.js.
On the server side, Amazon Cognito includes a dedicated user pool, associated to Okta, which is the selected OpenID Connect identity provider.
The sequence of calls to complete authorisation and resource retrieval is as follows:
Upon successful authentication with Okta, Amazon Cognito creates a user in the configured user pool, which you can see in the AWS Management Console.
- CDK setup
- Node.js installed
-
Setup a free trial account at Okta
-
Copy your account domain from the top right part of the screen, it looks like dev-{NUMBER}.okta.com
-
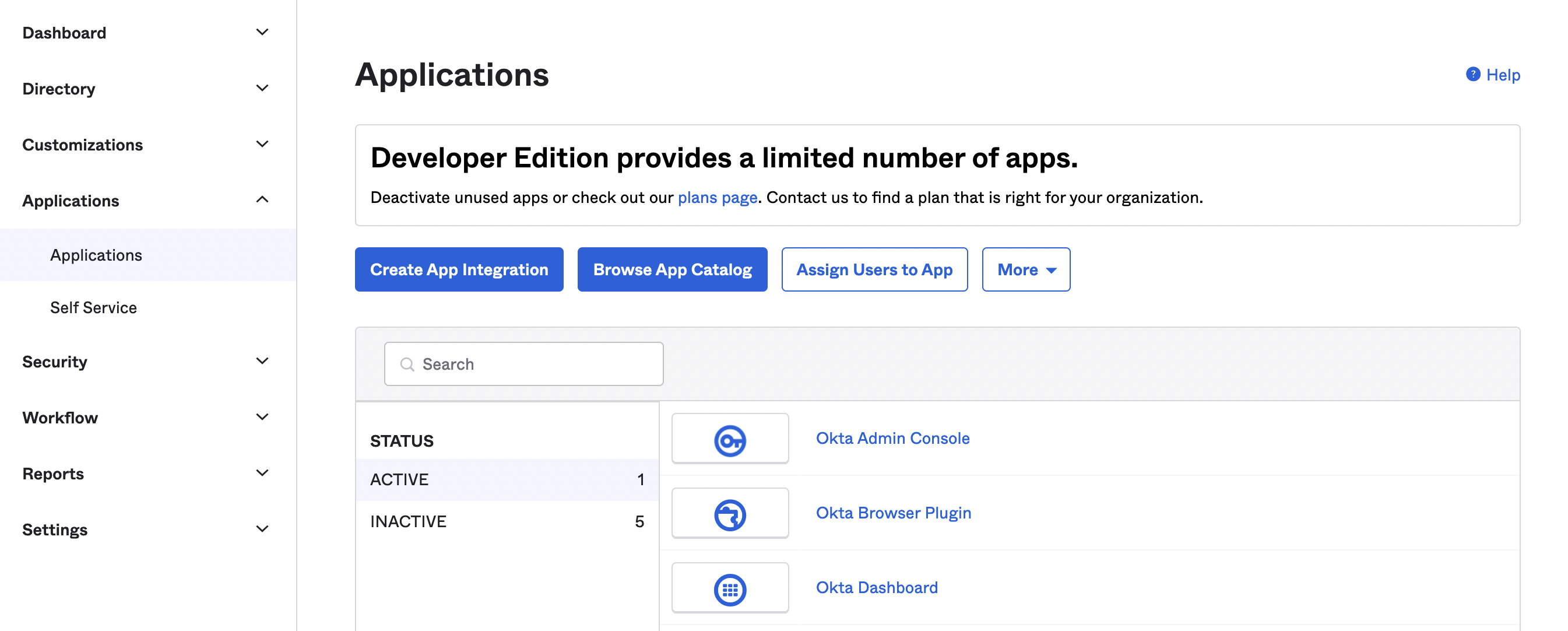
Create a new OpenID Connect (OIDC) app integration:
- On the left sidebar navigation menu, select Applications => Applications
- Select Create App Integration
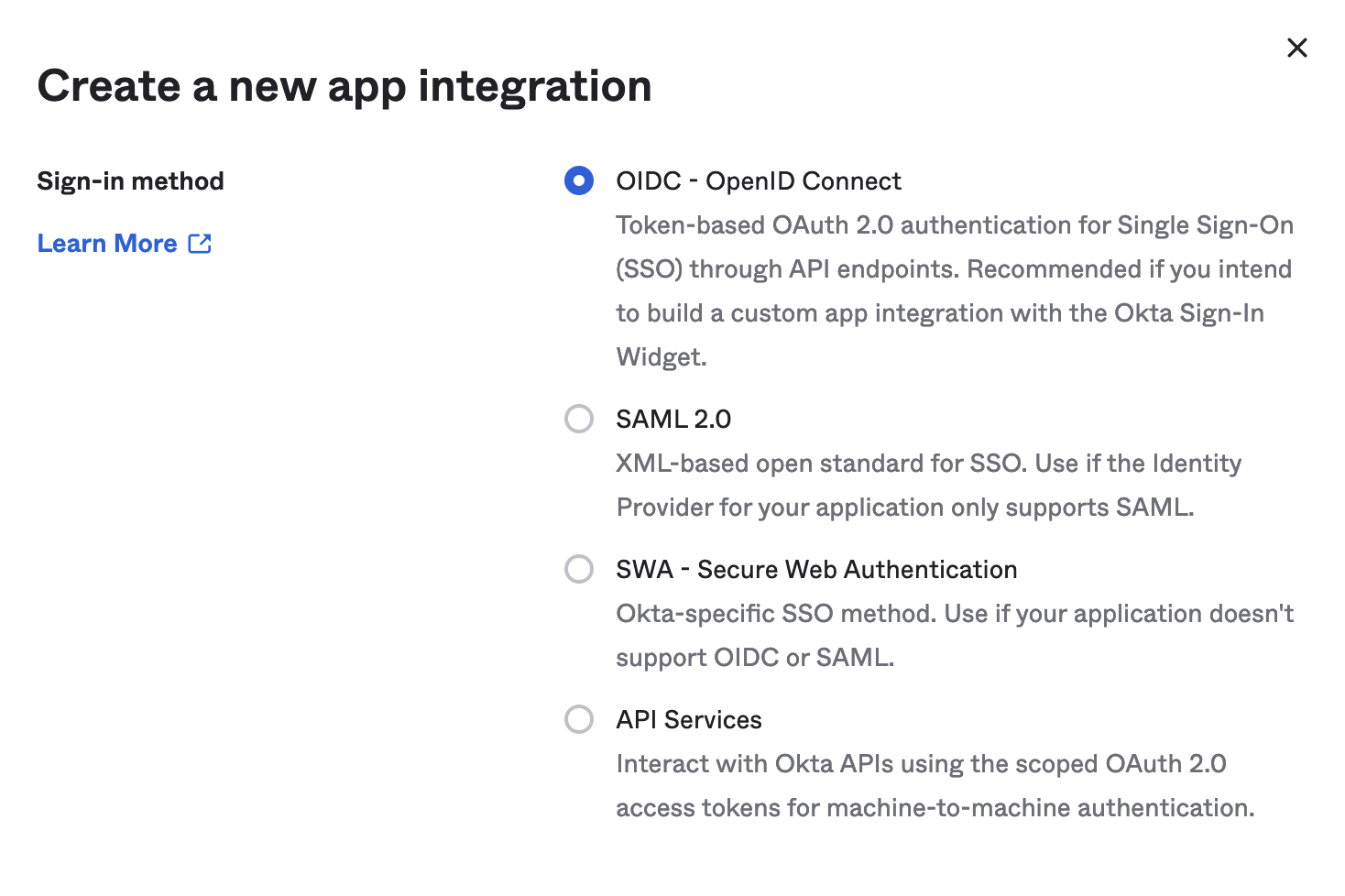
- Select OIDC - OpenID Connect
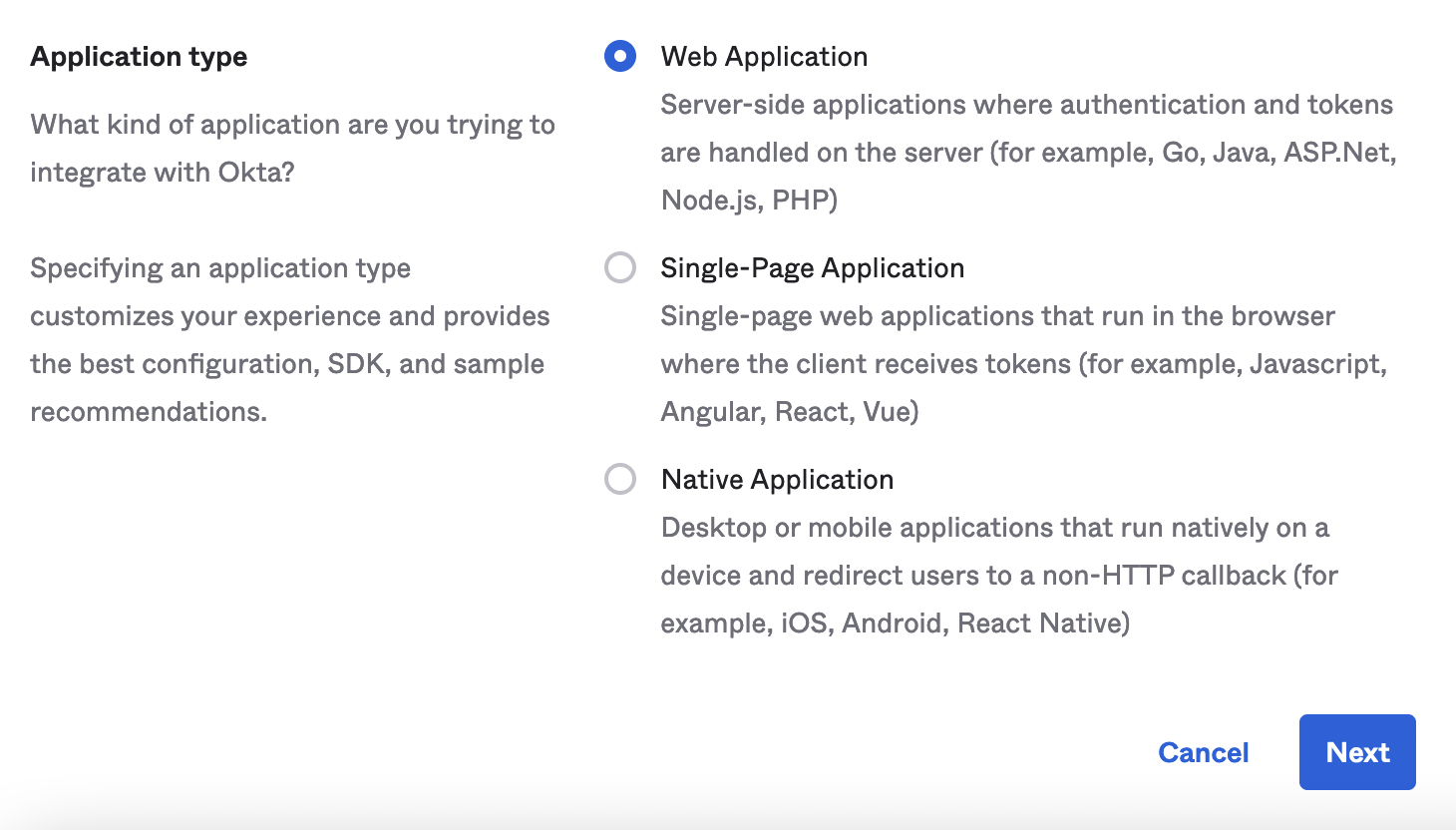
- On the same screen select Web Application
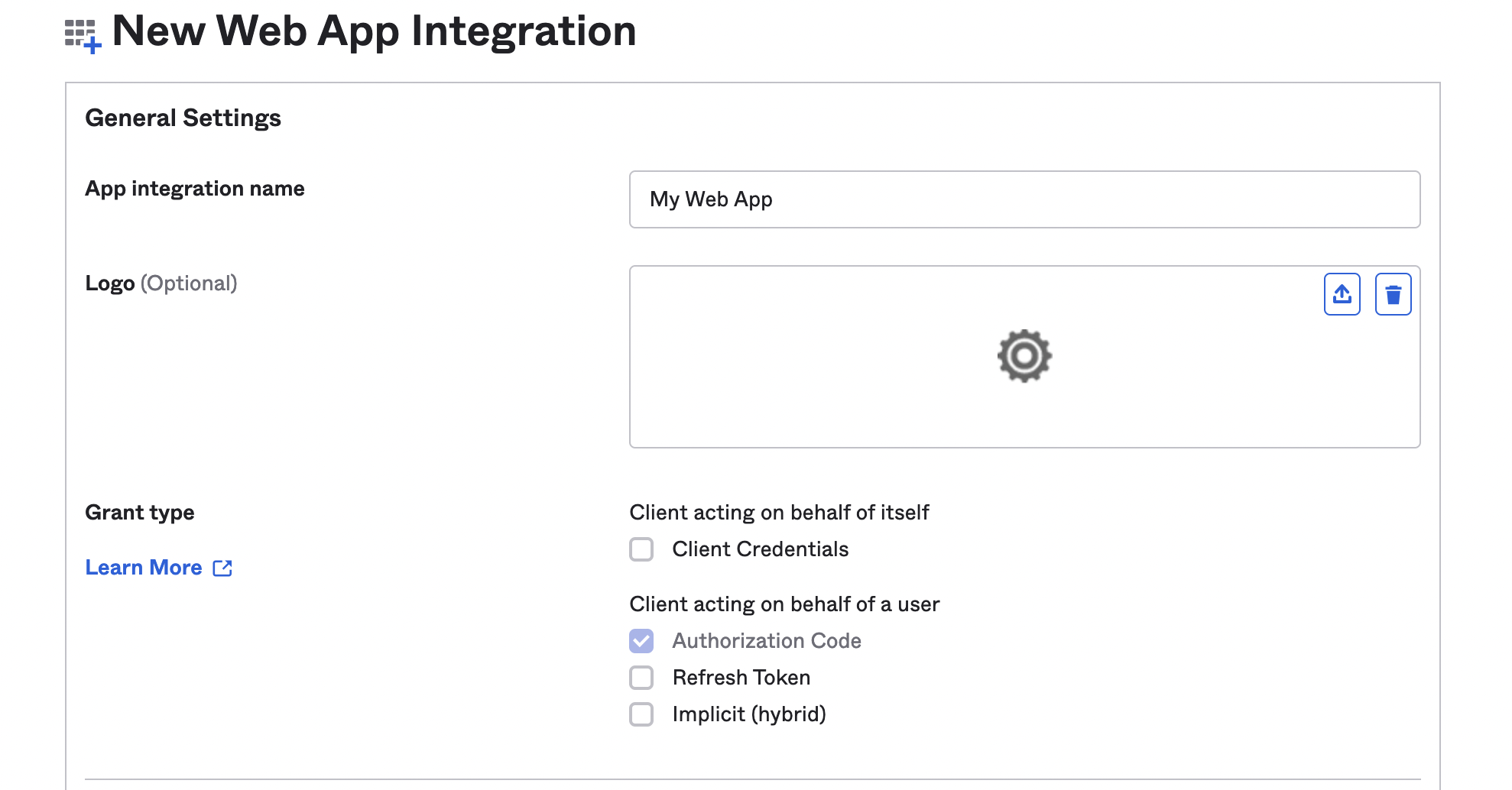
- Assign a name of your choice to App integration name (note: Grant type = Authorization Code will be auto-selected)
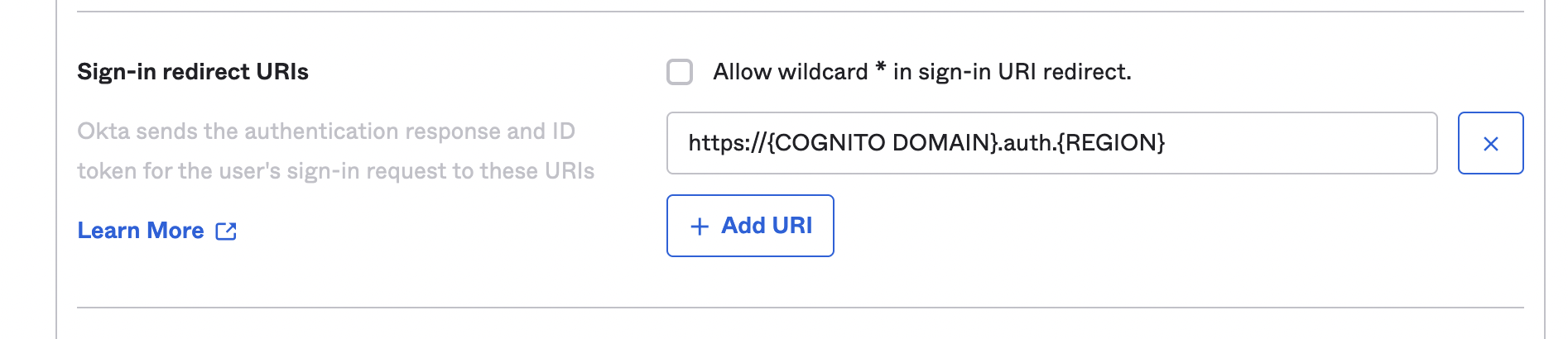
- Assign the following value to Sign-in redirect URIs: https://{COGNITO DOMAIN}.auth.{REGION}.amazoncognito.com/oauth2/idpresponse, where {COGNITO DOMAIN} is a unique value of your choice and {REGION} is the Region you selected on your AWS account
- For the purpose of this exercise, under Controlled access, select Allow everyone in your organization to access and click save
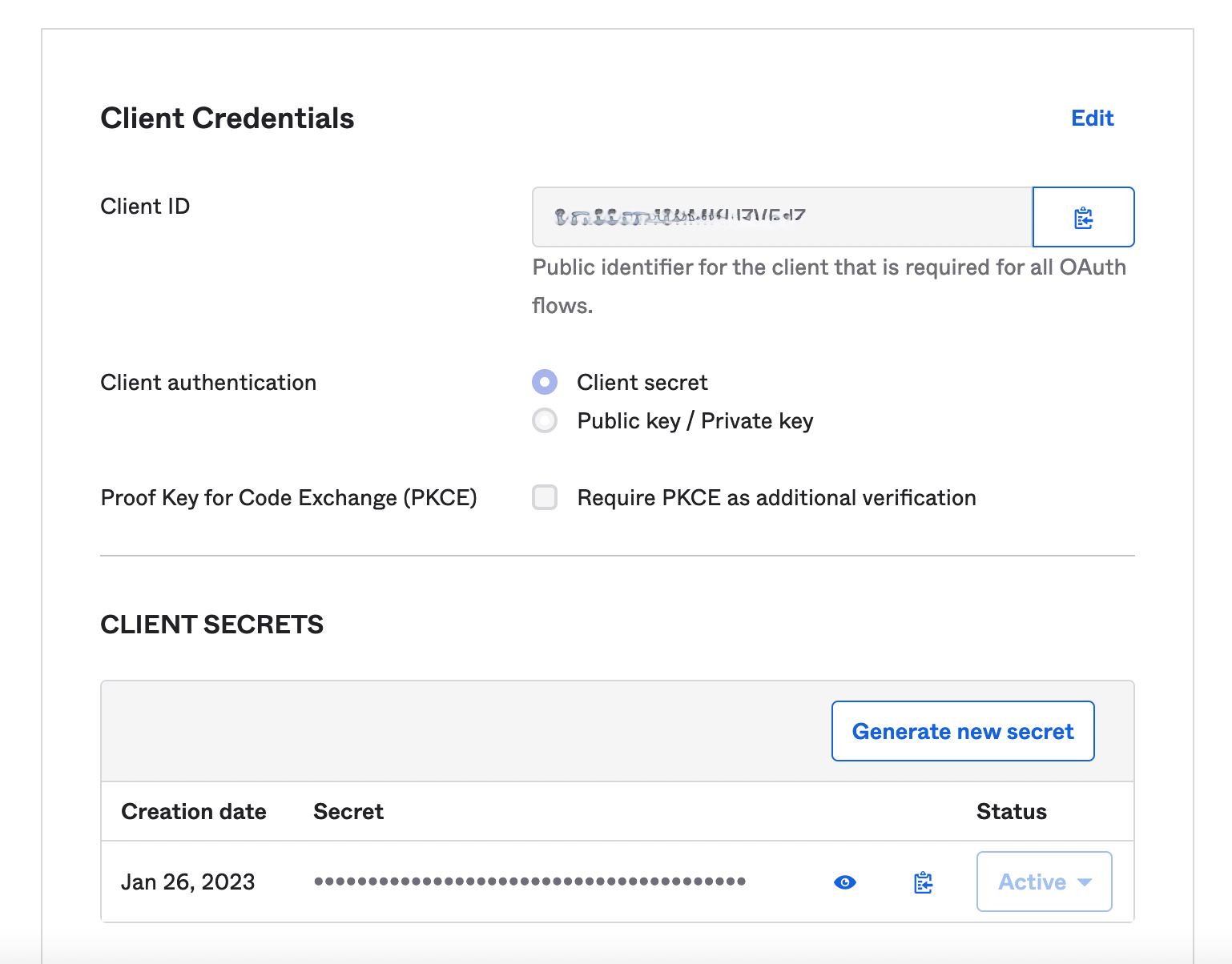
- After saving, copy Client ID and Secret under CLIENT SECRETS
-
Fill in cdk/config.json according to the comments in the file
-
cd to the cdk directory and run npm install && cdk deploy on a Terminal window
-
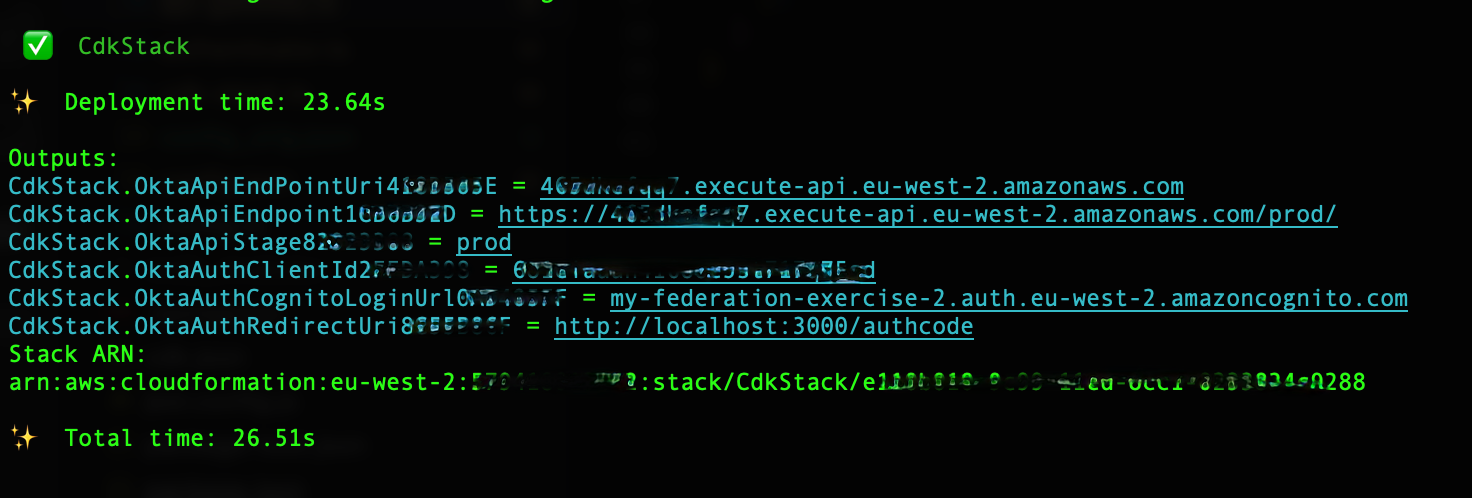
Note the Outputs section of the log:
- Fill in src/config.js according to the output above and the comments in the file
- cd to the src directory and run npm install && npm start
- On a browser, navigate to http://localhost:3000/
- Tap Login
- Select Okta authentication from the next screen (Sign in with your corporate ID)
- Authenticate with your Okta user
- After redirection, tap Call API Gateway
- If all ok, you will be able to see the message Hello! You've successfully hit /hello
See CONTRIBUTING for more information.
This library is licensed under the MIT-0 License. See the LICENSE file.