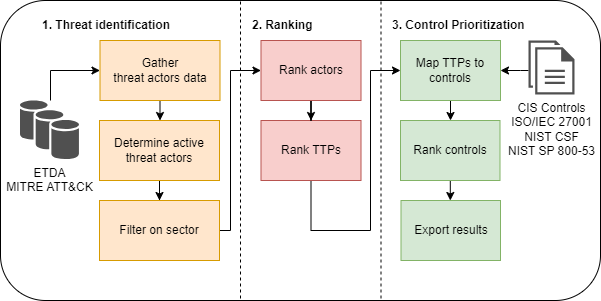
This repository contains various notebooks with code to prioritize security controls based on a determined active threat profile for a sector. The threat profile Based on their used TTPs, controls will be prioritized. The notebooks contain various approaches to reach this goal, and are part of the masters thesis of Abe Winters. The current supported control frameworks implemented are:
- NIST SP 800-53 rev.5
- NIST CSF
- ISO 27001:2013
- ISO 27001:2022
- CIS v8
In its current state, this repository has not been optimized for ease of use, but left as is from my thesis. This includes code scraps at various places and files that can be removed.
In the near-future, I will focus on cleaning up the repository to present the resulting model as an easy-to-use tool.
To run the notebooks, clone this repository and install the required packages using:
pip install -r requirements.txt
The model makes use of a merge between MITRE ATT&CK and ETDA Threat Group Cards. A local file is included, but to make sure that the most recent data has been pulled, run the following command:
python pull_data.py
The idea is that you set the parameters in the first cell of the notebook, and then run all cels. For options for the parameters, see options.md.
The results are written as an Excel spreadsheet within the results folder with the following four tabs:
| Tab | Content |
|---|---|
| Controls | Prioritized controls of the selected control framework, including control identifier, name and weight. |
| TTP and Control mitigations | TTP and control mappings used in the control prioritization. This sheet can be used to understand to which specific identified TTPs the controls map. |
| TTPs | Weighted TTPs from the identified threat actors in the sector |
| Actors | Weighted threat actors for the sector |
Based on the three methods from the thesis, three models will be tested.
- Method 1: Threat-report skimming
- Method 2: Threat-report scanning
- Method 3: Operations
- Method X has been created to work on a predetermined list of TTPs
At first, the skimming method is implemented based on the resulting spreadsheet build from skimming the reports. The reports are in PDF format and can be found in reports, containing reports grouped per year in subfolders. This list is used to create a basis of the possible threats and actors and the reports are scanned using these search words. The result is a generated dictionary of the number of occurences per report. This is further enhanced with data from public sources to rank actors and ttps, and finally prioritize controls. This pipeline can be found in Method 1.ipynb
The second method is somewhat based on the first method, but does not require skimming the reports. A basis of actor names is retrieved and used to scan the threat reports. This method can be found in Method 2.ipynb
The third method is based on operation dates. An interval can be selected, and actors are retrieved based on their activity within that period. The actor weights are determined by the amount of activity within the timeframe. The recent operations are weighted heavier than older operations with the use of an inverse function. Since newer threat actors do not have a lot of operations, but can still be very active, a newness multiplier is included as well. This is a multiplier based on the year this actor has first been seen, to compensate for the lack of operations. The pipeline can be found in Method 3.ipynb.
Within the mappings folder exist spreadsheets containing mappings to and from control frameworks. The notebook attck-nist-mappings.ipynb explores mappings between MITRE ATT&CK and NIST SP-800 53 r5. The notebook cis-mappings.ipynb creates mappings by leveraging the CIS Controls, since there exist many mappings to and from this control set.
This repository makes use of the following sources:
- MITRE ATT&CK. To access the data, their mitreattack-python package is used.
- ETDA
- tropChaud's Categorized Adversary TTPs. This code has been edited to include the full ETDA dataset and include activity dates. This edited fork is published in the following repository: Categorized Adversary TTPs
The thesis is is a master's thesis for the Cybersecurity master at the University of Twente, and has been the result of an internship at Secura. It is written by Abe Winters and can be found via the following link [will be added once available].