This project provides an easy way to check whether the Resource value of a role policy statement is a wildcard.
Works with AWS::IAM::RolePolicy versions "2012-10-17" and "2008-10-17".
The IamRolePolicy type and the method below are defined in the iamrolepolicyparsing package.
The method checks whether in any statement in the policy, the Resource value of a role policy statement is a wildcard and returns false if it is.
func (p *IamRolePolicy) NoStatementHasWildcardResource() booliamRolePolicy := iamrolepolicyparsing.IamRolePolicy{}
err = iamRolePolicy.UnmarshalJSON(json)
if err != nil {
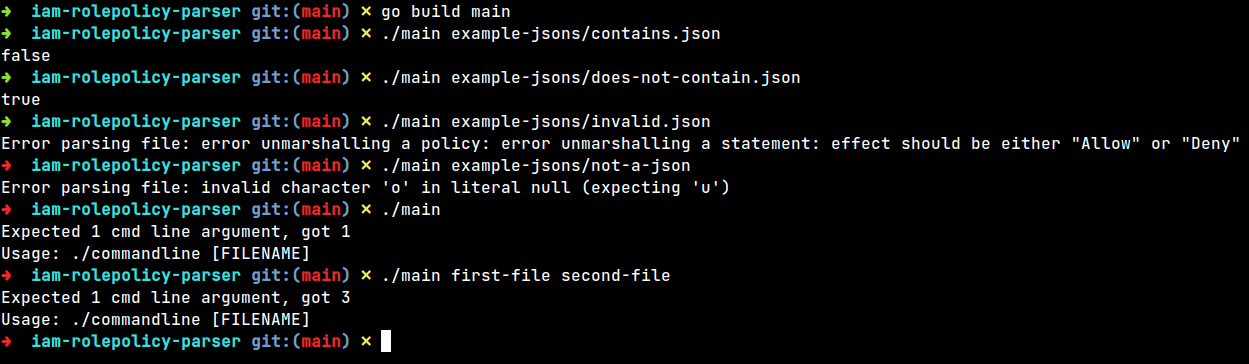
fmt.Println("Error parsing file:", err.Error())
os.Exit(1)
}
println(iamRolePolicy.NoStatementHasWildcardResource())You can use the method directly in your code, or you can compile and run the program from the command line with a file name as an argument.
- Go 1.22
go build main./main json-filenameThe JSON verification in this project is limited and does not include the following structures:
- action_string
- sid_string
- principal_id_string
- condition_type_string
- condition_key_string
- condition_value_string