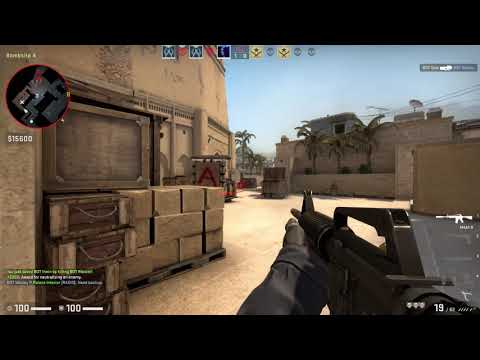
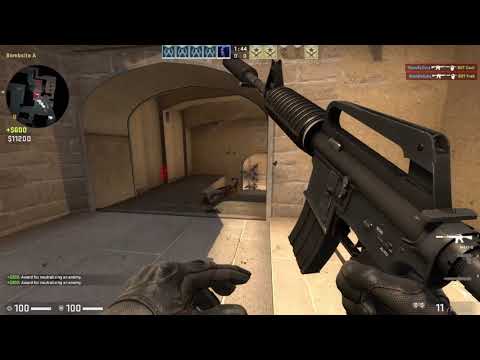
A project that demonstrates how to screw with CSGO from Kernel Space. Project comes with updated offsets, my aim was to create a project with more features achieved using a driver. I tend to hook DirectX, and implement Kernel-level drawing into this project. This has been done by a couple of people already, I mainly wanted to do one myself. The project has a UserMode application which uses IOCTL to control the Kernel Driver. This was something that helped me understand more of how Kernel Drivers work in particular, make a clean project for myself, and go forward.
Side note: No, this project has nothing to do with csgo's released source code or whatever. This project probably has mistakes. Feel free to correct me through PRs.
Project discussion: https://guidedhacking.com/threads/csgo-kernel-driver-multihack.15130/
WARNING: The project is for research purposes only and is not suitable for production environments, misusage, or commercial use. See License.
- Life45 for explaining me the basic work, pushing me to do this. Best guy eva.
- ThePaimon for menu related design and other works
- @ZeroMemory for providing videos for basic stuff.
- @hrt for a (not so much working) aimbot structure.
- Other fine members of NM team who will not be mentioned due to their requests
- Great open-source imgui projects / csgo reversers
- Driver Hiding (Kill Patchguard before use) @JKornev
- Process Hiding (Kill Patchguard before use) @landhb
- Menu rendering
- Bone rendering
- Aimbot
- Smooth aimbot
- TriggerBot - Supports randomized delay.
- Another simple program to Display Ranks (Not implemented to the rendering, but fairly easy to do)
- OBRegisterCallback to limit access to the GarhalController.exe & GarhalRankDisplayer.exe (Read VAC section)
- Highlights defuser (Not implemented to the rendering, but fairly easy to do)
- No flash (Flagged)
- Displays enemies on the Radar (Flagged)
- Bhop (Flagged)
- Simple glow Wallhack (Flagged / Removed)
- Changes on 2020.07.31: The driver now detects process termination. Should have coded It more faster than being lazy. The controller, and rankreader sends an IOCTL code to the driver once they have been launched, and loaded. If we would do this sooner, the applications would not start up. We are now completely re-writing the access flags, and the usermode applications should be untouchable by VAC for now. The usermode applications now wait until the addresses are not zero at startup. The plan to make an anti-aimbot was dropped. A kernel driver should be all about being non-straightforward, and used carefully to draw less attention. Please continue testing, and let me know if there are any issues.
Simple explanation: It's something that doesn't like kernel manipulation, and triggers a BSOD If detects It. Use something like EfiGuard or UPGDSED or Shark . I prefer the two latter. Doing so will give you sort of full "invisibility", but It's unnecessary (imo).
As long as you do not open a handle to the game you should be fine, but of course there are ways to detect Read/Write memories. It's just harder without a driver, and hence they haven't really done this since 2017 I hardly think they are going to. Here is some information from 2013, and 2016:
Both sources talk about that VAC opens handle to processes and searches all volumes with FindFirstVolumeW, FindNextVolumeW and closes handles with FindVolumeClose.
It opens every handle running with Query_Information, and VM_READ. Denying access with ObRegisterCallbacks to protect the controller would be more than enough to get rid of this scan.
-- After some emails I have decided to clear some things up. The project doesn't open a handle, and obviously doesn't use usermode RPM/WPM. Therefore the only detectable parts should be memory writing It self, and by VAC searching for the driver / usermode application. As stated above you can grant yourself "invisibility" (from VAC) atleast by using the implemented driver / process hiding. The driver also protects the usermode application from VAC's process scanning. (Stated in the VAC section) The project files could be flagged, and can get you banned If VAC detects you are running this certain program (Checking for name / hash, but It's a really bad approach from any anti-cheat)
if (EnumDeviceDrivers(drivers, sizeof(drivers), &cbNeeded) && cbNeeded < sizeof(drivers))To read why Garhal was changed to become an imgui project click here
I have purchased CSGO around April-May on a separate account, which you see in the sample videos. For 80+ hours I have been cheating on that account, for about a month or so. Revisited the game in August last time. I have used wallhack, triggerbot, aimbot without holding back and received countless reports from competetive matches. At this time being the account is still not banned for CSGO. Still, do not use it on your main accounts.
- DirectX SDK (DXSDK_Jun10.exe)
- You will need Visual Studio 2019 atleast, and amongs that the WDK. If you don't know how to compile a Kernel Driver, you will need to google a bit, or just click here.
Don't be a loser, dump with GH Dumper(Totally not an advert)
Use -insecure, and dump after.
Visit hazedumper for easy usage.
If you don't need the csrss.exe check just remove It (memory.c, but not recommended), or update the offsets manually for different windows versions.
Click Here to view the EPROCESS offsets. Click Here to view the release information site.
- Windows 10 1903
- Windows 10 1909
- Windows 10 2004
- Windows 10 2009
- Windows 10 2104
- Windows 10 2110
- Start the Driver.
- Start CSGO.
- Place the default config where GarhalController.exe is.
- Modify config to your needs.
- Start GarhalController.exe.
- Optional: If you are playing ranked, use GarhalRankDisplayer.exe to view ranks.
- Play the game.
- Beware of Overwatch.
Open up CMD as admin mode:
# Enable testmode and reboot.
bcdedit /set testsigning on
# Create service and start it.
sc create garhal type= kernel binpath="C:\Users...\Desktop\garhal.sys"
sc start garhal
# Stopping the service, bohoho...
sc stop garhal
# Disabling testmode...
bcdedit /set testsigning off- Uncomment the commented DriverEntry function in garhal.c.
- Rename the current one to DriverInitialize.
- Compile the driver with /GS- (Disable the security check).
- Use kdmapper or something else to load up your driver.
- Optional (and recommended if you are interested in kernel, rather than being a crappy user): Clear the MmUnloadedDrivers and PIBCache yourself, get the signature of these using WinDbg for example, don't use CreateDriver, hook an IOCTL function with a trick, or do some other type of communication. I'm not releasing practices for this for now, there is plenty available. If you manage to do these tricks you are free to attack any realistic anti-cheats with more work (BY REVERSING).
- Reboot your PC to clear out the driver entirely from the memory if you want to play different games.
There are various things you could be working on, It merely depends how far you want to go. For advanced anti-cheats you will need to research / figure out how to map, and fully hide your kernel driver so It's hidden in the best way possible. This also means ditching the IOCTL communication that this project has. You could also implement all sorts of rendering (such as radar) onto the current imgui setup, Xor the strings, hide the overlay window in a proper way, list goes on..