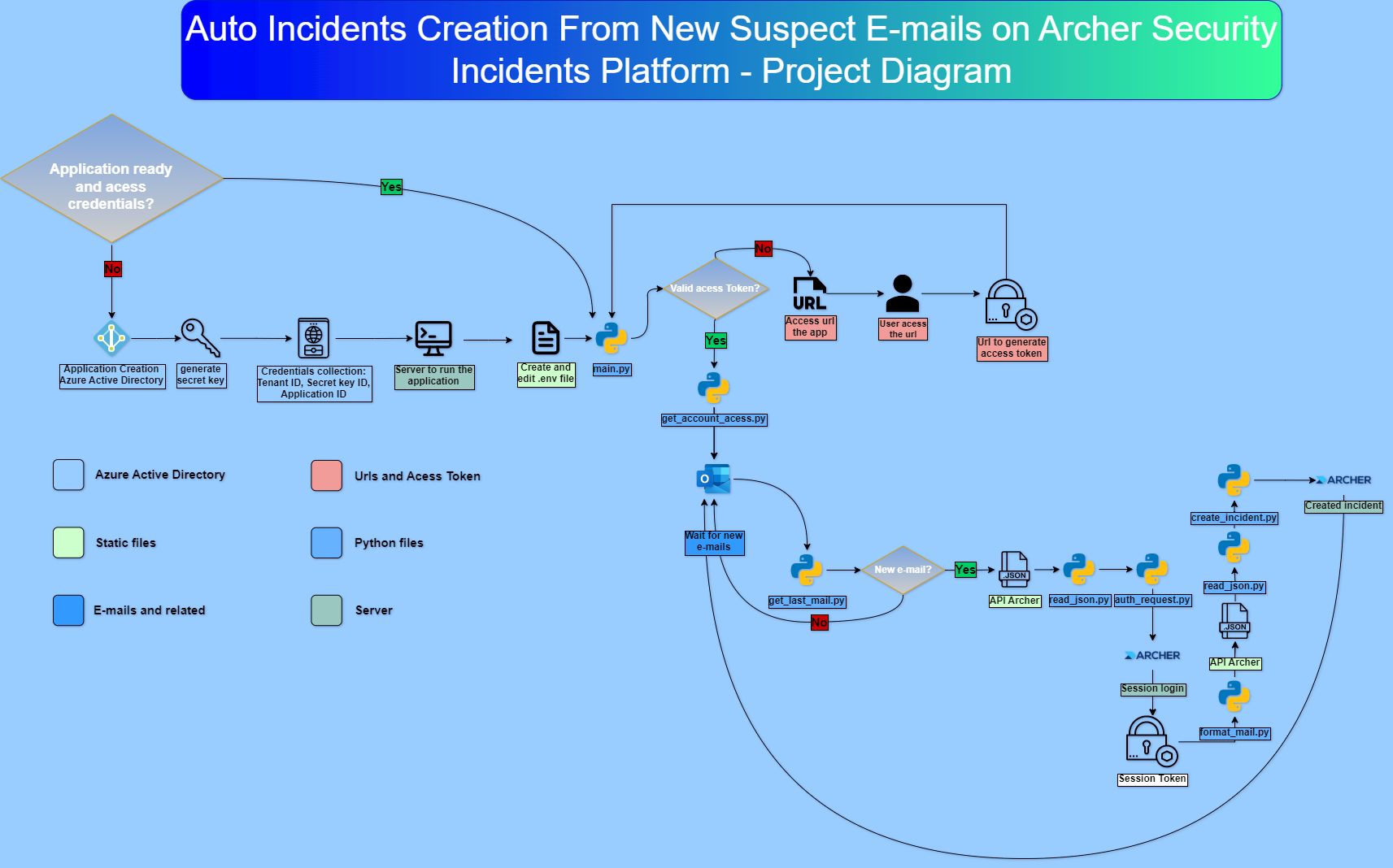
This project aims to automate the process of creating new incidents on Archer security incidents platform by collecting suspicious e-mails from a mailbox and creating a new incident report on the platform, with all required fields covered by the automation
Solution created using Python Language, Microsoft Graph API, python-o365 library to collect e-mails and acess mailbox and Archer API to open new incidents on the platform.
👤 Antonio Costa
- Github: @Antonio-Costa00
- Linkedin: @Antonio Costa
Contributions, issues and feature requests are welcome!
Give a ⭐️ if this project helped you!
Copyright © 2022 Antonio Costa.
This project is MIT licensed.
Creating the application it's necessary to enable the reading permission of user's email.
With the creation of the application, it's possible to read any email account within the box, only possessing the application ID, the tenant ID and the secret key ID.*
Note: Only Azure administrators can create new applications unless the permission of creating new applications has been released to users.*
For app creation, the following steps should be followed:
- 1 - Application creation on Microsoft Azure
- 2 - Generating a Secret Key
- 3 - Setting application
- 4 - Start application
For access to email, it's necessary to create an application in Microsoft Azure Directory, with application permission to access the email reading permittions
For app creation, the user must follow the following steps:
-
Access portal azure
-
Access Azure Active Directory
-
Application registration
-
Give a name to the application
-
In types of accounts supported, select Accounts in this organizational directory only (tenant name only - Single tenant)
Note:
-
Selecting Accounts in this organizational directory only (tenant name only - Single tenant) only tenant accounts can access the app
-
If someone outside the tenant tries to acess the application, the follow error will be generated: "You cannot sign in here with a personal account. Instead, use your school or professional account."
-
Selecting Platform, Web Application
-
Within url redirecting, select the address https://login.microsoftonline.com/common/oauth2/nativeclient
-
Register the app
-
Collect the application ID (client) and the tenant ID (directory).
- On app registrations, Certificates & secrets
- New client secret
- Select a validate time
- Add
- Copy the value of ID¹
² The value of the ID is only possible to preview once, so the value of the ID should be collected immediately after the creation of it.
- API permissions
- Add a permision
- Microsoft Graph
- Delegated permissions
- Search for mail and select All Read permissions that you want.
- Add permissions.
- Create a file named .env
- Copy all content from .env.example to .env file
- Edit the .env environment file
- Within the file, edit the APPLICATION_ID, SECRET_ID and TENANT_ID values, with the collected values of the creation of the application.
- Also edit the ACCOUNT_TO_ACESS variable with the email address to be read.¹
¹This option it's necessary on case the mail is a shared mail
There is a Archer API file .json on ./Archer/ArcherAPI/example_API.json
You must replace the API with informatios from your Archer System.
After following the previous steps, we need to install the project dependencies
pip3 install -r requirements.txt
If you want to run the application in a simple way you can run the command
python3 main.py
If you want your application to run as a background process:
sh start_restart_application.sh
This script will start to run the application as a background process.
OBS:
- At the moment, this solution only runs on Linux servers, and in the future I will create an equal Windows solution.
At the first time you run your application a message asking for an access token will emerge.
https://login.microsoftonline.com/...
Paste the authenticated url here:
- To add acess the mailbox, you must acess the link token generated on the terminal screen
- If it is the first time accessing the application, it will be asked about what the app wants to do, and in our case, perform the reading of the mailbox.
- If you are repeating the process, nothing will be erased.
- In both cases, a new url will be generated in the browser.
- Collect the URL and paste the terminal.
- If all happened well, the following message would appear in the terminal.
Authentication Flow Completed. Oauth Access Token Stored. You can now use the API.
For this project, after the 90 days, a new access token must be generated, repeating the errors of the previous session.
And now everytime the mailbox receives a new email automatically the solution will create a new incident on Archer platform
If you don't want to follow this 90 days rule, feel free to read the oficial documentation.