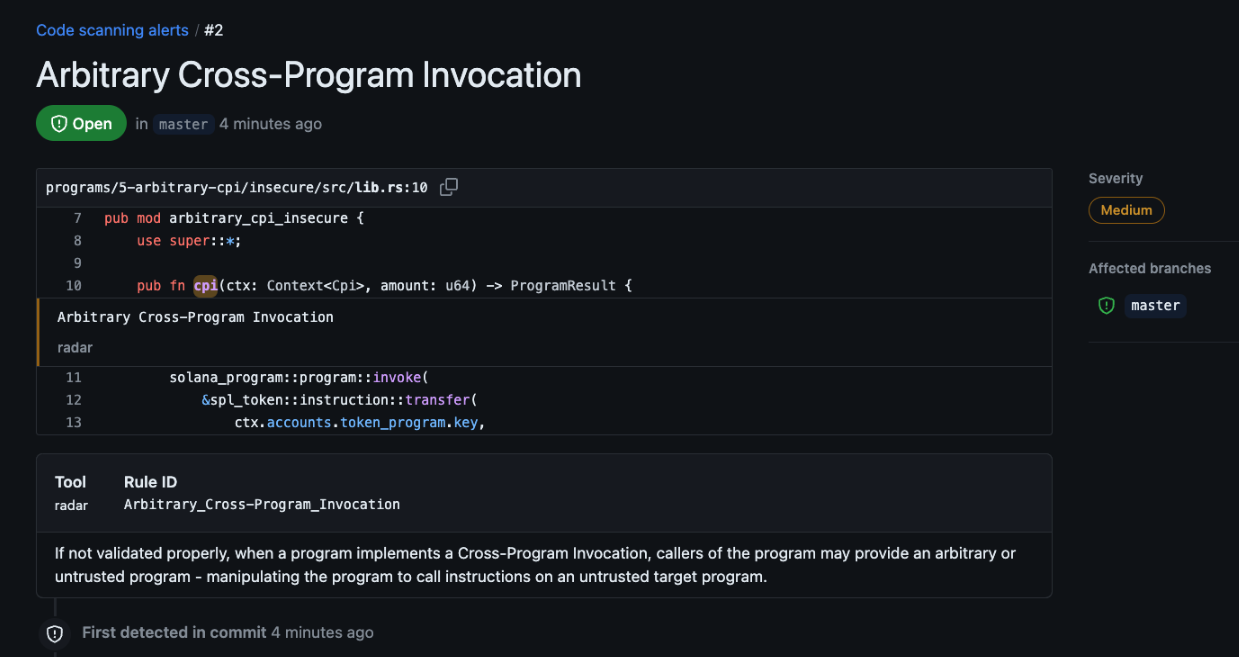
A static analysis tool for anchor rust programs.
radarallows you to write, share, and utilize templates to identify security issues in rust-based smart contracts using a powerful python based rule engine that enables automating detection of vulnerable code patterns through logical expressions.
-
Install and start docker
-
Install git
-
Install radar either from install script or from source
curl -L https://raw.githubusercontent.com/auditware/radar/main/install-radar.sh | bash
radar -p <your-contract-folder>OR
git clone https://github.com/auditware/radar.git
cd radar
./radar -p <your-contract-folder>A good contract to first test radar against is the beautiful repo sealevel-attacks
git clone https://github.com/coral-xyz/sealevel-attacks
radar -p sealevel-attacksIn a 10 seconds setup you can integrate radar-action and be alerted with radar's insights continuously through your contract repository.
After fixing issues, you could share that the action completes successfully each run by pasting a link similar to this in your repo's README.md:
<img src="https://img.shields.io/github/actions/workflow/status/<USER>/<REPO>/<RADAR-WORKFLOW-NAME>.yaml">If you're using pre-commit, you could also add radar to your workflow by adding radar to your .pre-commit-config.yaml configuration like so:
repos:
- repo: local
hooks:
- id: run-radar
name: Run Radar Static Analysis
entry: radar -p . --ignore low
language: system
stages: [commit]
pass_filenames: false
always_run: trueEither if you have a vulnerability to test in mind, or if you want to improve the quality of an existing one, templates are the best way to contribute to this repo! Open a PR to add your template to the built-ins.
We'd love to assist with writing your first template, and provide guidance.
Check out the Wiki for more details. For support reach out to the Audit Wizard Discord.