Attack surface, attack tooling, and patch included
Directory
| Name | Purpose |
|---|---|
| attack | Resources for an attack on the IOT-light |
| img | Docs & diagrams |
| iot-lght | Firmware, Server, & UI for an IOT-light |
- 3 ESP32 dev boards, typically boards with an esp32 that has a cap with more detailed descriptions are higher quality, 3 for $15 is a good deal as of 2023
- Micro usb cable
- Breadboard
- Led's
- Resistors
git clone <your fork URL> && cd ctf
The IOT-light uses hardcoded credentials to connect to WiFi, check for updates and communications by connecting to a custom server, and if an update was available, will pull a new firmware from github.com or wherever the server tells it to
- Wire up an LED to GPIO32(D32) and a ground pin
- Open iot-light/app a terminal
- From the cmd line run
node index.jsto launch the app server, the app should be available at http://localhost,http://<your ip address>, andhttp://<your hostname>, scan the QR code to jump to the app on your phone if you're on the same wifi as your laptop - Run the
hostnamecommand in a bash terminal to find the hostname of your computer - Open iot-light/light in its own vscode window
- Plug in an esp32 dev board
- Create a config.h file with your wifi credentials and ip address, and add it to iot-light/light/include/
#define SSID "SSID"
#define PASS "PASS"
#define WSSERVER "IP_ADDRESS_OR_HOSTNAME_OF_SERVER"
#define WSPORT 80
- PlatformIO
 ->blue1->upload&monitor
->blue1->upload&monitor - Build all the other targets too, copy the firmware over to the releases folder and rename them
v<1-3>.bin, name the red target firmwarered-firmware.bin, this will be refrenced in the malicous server - If you're planning on using github to store firmware to pull, change the base address to your github fork url in iot-light/app/index.js, if not you will need to use a different root certificate in the patch
- To get the IOT-light to update change the version number (to 2 for the first update) in the IOT-light server (and resart it) iot-light/app/index.js
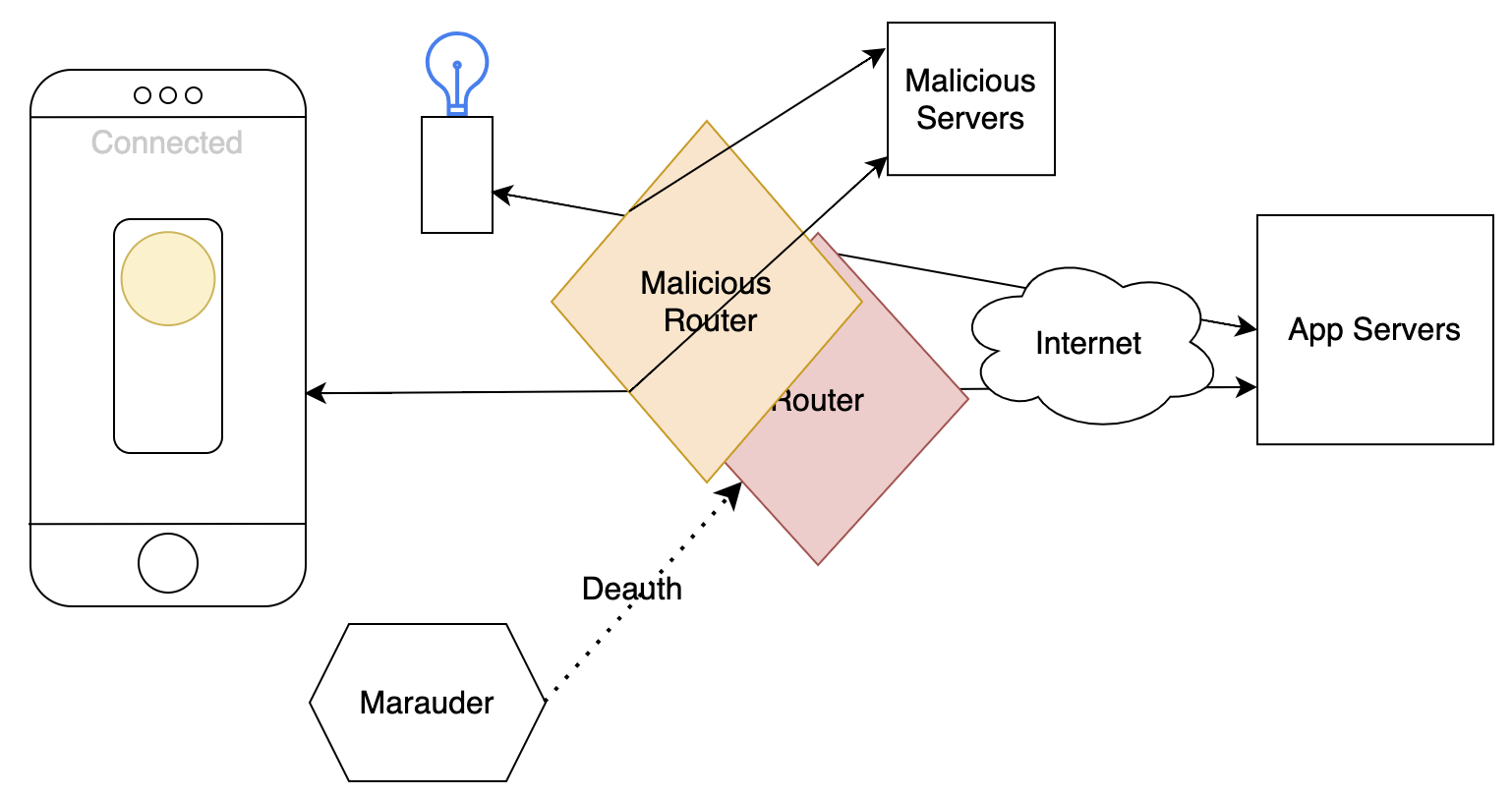
Getting full control of the IOT light
- Use tools like Fing and Wireshark to find the IOT-light connected to the wifi
- Setup a malicous router with same wifi and ssid as the target, launch & connect malicous servers to it
- Use the Maurauder to disconnect the IOT-Light so it will recconnect to the fake access point
- Identify web requests from the IOT-light using network tools like
tcpdumpand wireshark - When a request to get the new firmware is made, the IOT-light will get the firmware provided by the malicous servers
- Open the ESP32Marauder folder in vscode, let platformio process
- From the platformio menu, select upload
- Connect to the MarauderOTA wifi, password is justcallmekoko
- Go to 192.18.4.1
- Login with user admin password admin
- Choose file -> attack/ESP32Marauder/esp32_marauder_v0_13_3_20231114_old_hardware.bin, and select update
- Wait like 60 seconds, a little after the 100% percent feedback is reached
- Great! You made a marauder! Now you can connect over serial using the platformio monitor button, after a few confguartion messages the cli should pop up
CLI Ready
>
@@@@@@
@@@@@@@@
@@@@@@@@@@@
@@@@@@ @@@@@@
@@@@@@@ @@@@@@@
@@@@@@ @@@@@@
@@@@@@@ @@@@@@@
@@@@@@ @@@@@@
@@@@@@@ @@@@@@@@@@@@@@@@
@@@@@ @@@@@@@@@@@@@@@
@@@@@ @@@@@@@
@@@@@ @@@@@@
@@@@@@ @@@@@@@
@@@@@@ @@@@@@@@@@@@
@@@@@@@ @@@@@@
@@@@@@ @@@@@@
@@@@@@@ @@@@@@
@@@@@@ @@@@@@
@@@@@@@ @@@@@@
@@@@@@ @@@@@@
@@@@@@@@@
@@@@@@
@@@@
--------------------------------
ESP32 Marauder
v0.13.4
By: justcallmekoko
--------------------------------
>#
- Open the esp32_nat_server folder in vscode, let platformio process, then press the upload button
- On another device you should see a wifi named ESP32 NAT router, connect
- A router settings page should be available @ http://192.168.4.1
For reference, the following line in attack/esp32_nat_router/main/esp32_nat_router.c has been changed so that the first device connnected is the default dns server if traffic is not being forwarded to another router
#define DEFAULT_DNS "192.168.4.2"Options
- Use Fing to identify devices on the same network
- Use the maurader to discconect the target from the wifi, host a router that will route dns requests to your computer, use a dns server to analze requests made from the target.
- On a malicous router running linux, it is possible to view network traffic using
tcpdump
- Open 3 terminals in the main project directory
- Download the malicicous servers local dependencies
cd attack/servers && npm install - Connect to the mauraduer with screen,
ls /dev/tty*to find your usb connection to your mauraduer, thenscreen /dev/tty<USB1orSomething> 115200, typehelpfor a help menu to pop up scanapwith the marauder to scan for access points,stopscanafter you've seen the ssid the IOT-light is connected tolist -ato list the wifi ap'sselect -a <n,n,n>"ORselect -a -f "contains <unique substring of the ap to attack>"to select the device(s) to fake death packets from so connected devices will switch to the fake access point (if its in range)- Power up the bad router with the wifi credentials of the ap to attack
- Connect to it, the blue light will start blinking
- Keep the screen terminal open, open two terminals in the main ctf directory
- In another terminal run
node attack/servers/dns-server.js - In the last terminal run
node attack/index.js - In the screen terminal
attack -t deauth, butattack -t probemay also work, now hopefully the iot-light will connect to the bad router, all dns & http requests will be redirected to your machine, and you'll be able to replace the firmware when a request is made on the iot-light (when it starts flashing), watch the other two terminals for requests
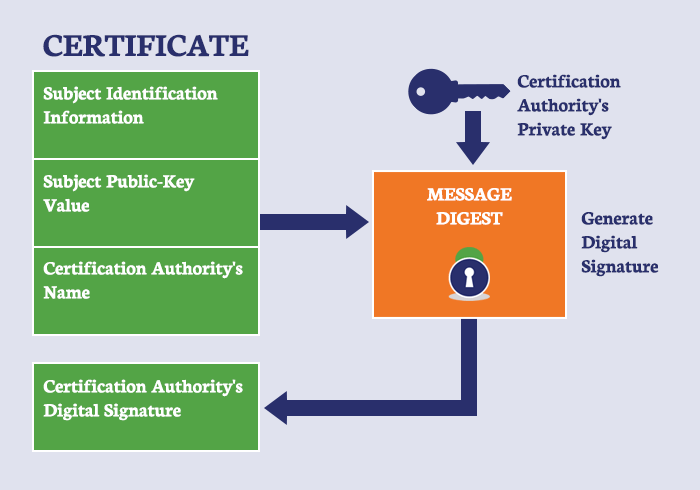
Updated browsers including Chrome and Safari, verify the authorship of a website’s certificate through the verification of its digital signature. An https website can either have a self signed certificate or a certificate signed by a certificate authority. Common browsers and advanced IOT devices have a list of various certificate authorities and their public keys, which can be used to decrypt a portion of a certificate with their signature. Only a certificate organization's private key can produce a signature that will be successfully unencrypted by a public key. In this way, the signature is verified, and the connections can be evaluated as secure or insecure.
Image Taken From Thesslstore
The patched firmware that verifies authorship before pulling a new image is listed in iot-light/light/src/main-patch.cpp. It can be built and uploaded with the options for the target labeled "patch". To do this open a vscode window in the iot-light/light directory, platformio should automatically detect the platformio.ini file that is at the top level of the file system in the window, after a few seconds, pressing the bug icon in the extension tabs should show the targets available.
IOT devices are commonly built with certain hardware constraints, limiting them to use IP over wifi or some subset of wireless communication protocol like Zigbee or espnow to interact with each other
Wireless communication represents a greater hardware security risk than a wired connection. The that cost of attacks are reduced when physical access is extened to a larger range and physical techniques for wire tapping are not required
Hardware security threats are all across the board, including
- Spoofing ex. Malicious router broadcasting the same name/ssid as a trusted router
- Tampering ex. Man in the middle altering data
- Information disclosure ex. Man in the middle capturing data
- Repudiation ex. Malicious router can imitate authorship credentials
- Denial of Service ex. Deauth with udp packets or flooding wifi channel with noise
- Elevation of Privilege ex. Can’t think of one at the moment but there is probably one out there
Here is a paper about this project, Here are some slides too, Here is a youtube playlist of the demos
- Rui & Sarah Santos: ESP32 https requests
- QR code generator
- Whats EAP
- Fritzing arduino diagram tool
- Wifi passwords are encryption keys
- Dr. Michael Zuzak, CMPE 361 Intro to Hardware Security Course & Advising, Contact For Resources
- Long lam, Hardware Security Tutorials & Advising, Contact For Resources
- Thesslstore, Signed Cert Image, https://www.thesslstore.com/blog/ssltls-certificate-its-architecture-process-interactions