This Repository is intended for HybrIT Services Partners to easily and securely provide access to some or all subscriptions in their Azure Tenancy.
The Role base Azure Lighthouse configuration uses Privelege Groups in HybrIT's own AD Tenant. This provides a mechanism for auditable JIT privilege access at no additional cost to the partner.
This Feature was announced by Microsoft July 2021, for further reading please see Microsoft Azure Blog
- Introduction
- How to use
- What Roles get assigned and to who?
- Apply Backup Security (Resource Guard) to single subscription
- Remove Access
- Sign in to your Azure Tenancy using Windows PowerShell. Use an account that has owner rights against any subscriptions you want to enrol in Azure Lighthouse.
Connect-AzAccount
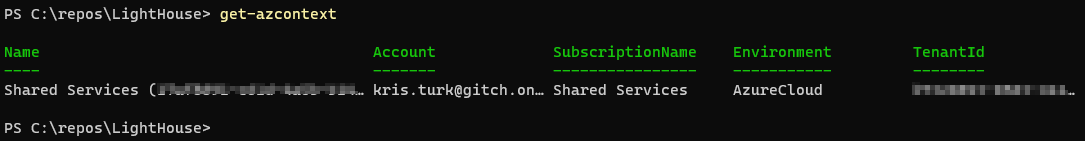
- If you would like to HybrIT to only access a single subscription via Azure Light house check you are connected to the correct subscription
Get-AzContext
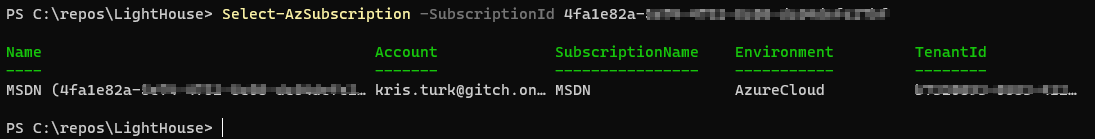
- If you need to switch subscriptions you can use the below command
Select-AzSubscription -SubscriptionId <SubscriptionID>
- Finally run the single powershell command to apply the template from this repository
New-AzSubscriptionDeployment -location uksouth -TemplateURI 'https://raw.githubusercontent.com/HybrIT-Services/AzureLighthouse/main/HybrITLightHouse.json'
Note: If you intend to use a seperate Subscription of Azure Resource Guard then ensure to deploy that subscription after running the below or apply one subscription at a time or exlude the Backup Security Subscription from the assignment
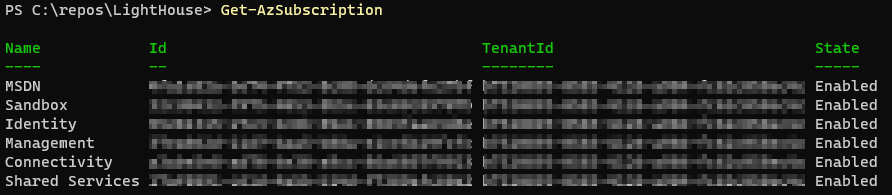
- To apply to all subscription that your signed in user has rights to run the below commands. Firstly check you can see the intented subscriptions from your PowerShell windows
Get-AzSubscription
You should see a return of the subscriptions you have access to.
- Run the below script to assign to all subscriptions
$subs = Get-AzSubscription
foreach ($sub in $subs) {
Select-AzSubscription -SubscriptionId $sub.Id
New-AzSubscriptionDeployment -location uksouth -TemplateURI 'https://raw.githubusercontent.com/HybrIT-Services/AzureLighthouse/main/HybrITLightHouse.json'
}
- If you need to exclude a subscription such as BackupSecurity filter it out with the below ensure to check your subscription name
$subs = Get-AzSubscription | Where-Object { $_.name -notlike "*BackupSecurity*" }
foreach ($sub in $subs) {
Select-AzSubscription -SubscriptionId $sub.Id
New-AzSubscriptionDeployment -location uksouth -TemplateURI 'https://raw.githubusercontent.com/HybrIT-Services/AzureLighthouse/main/HybrITLightHouse.json'
}
The roles JSON template is built form the Bicep file in this repository. The bicep file contains comments to indicate which role is assigned to which group. The comments are intended to quicky interpret which groups get which roles with out the need to cross reference the Role Definition ID Manually. How ever if you would like to double check these roles can be found here.
https://docs.microsoft.com/en-us/azure/role-based-access-control/built-in-roles
HybrIT are using privlege access groups to provide access into your environment. This means no user or admin will have standing access. To gain access HybrIT's consultants will need to elevate themselves into the group using Privlege Identity Management with in the HybrIT Azure AD Tenant. This has the benefit of having a full audit trail of who had access and when, additionally it means the licenses required for PIM are assigned within HybrIT's own Azure AD Tenant and incurs no cost to the Partner.
Additionally when elevating into groups with any kind of write privilege (all except reader) HybrIT's consultant will immediately be subject to MFA.
| Privilelege Access Group | Role Assignment |
|---|---|
| Lighthouse - Azure Privilege Contributors | Contributor |
| Lighthouse - Azure Privilege Contributors | Managed Services Registration assignment |
| Lighthouse - Azure Privilege Contributors | Assign roles to Managed Identities |
| Lighthouse - Azure Contributors | Contributor |
| Lighthouse - Azure Reader | Reader |
| Lighthouse - Azure Operators | Virtual Machine Contributor |
| Lighthouse - Azure Operators | Backup Operator |
| Lighthouse - Azure Operators | Reader |
| Lighthouse - Azure Operators | Log Analytics Contributor |
| Lighthouse - Azure Operators | Monitoring Contributor |
| Lighthouse - Azure Operators | Automation Operator |
| Lighthouse - Azure Operators | Automation Runbook Operator |
| Lighthouse - Azure Operators | Managed Application Operator |
| Lighthouse - Azure Operators | Site Recovery Operator |
If your engagement with HybrIT is only in the discovery phases and read access is the only requirement then you can use the same script logic as the previous section as the previous section but reference the HybrITReaderLighthouse.json file.
For instructions on connecting and selecting single subscriptions please see earlier instructions. The run the appropriate powershell command below
New-AzSubscriptionDeployment -location uksouth -TemplateURI 'https://raw.githubusercontent.com/HybrIT-Services/AzureLighthouse/main/HybrITReaderLightHouse.json'
$subs = Get-AzSubscription
foreach ($sub in $subs) {
Select-AzSubscription -SubscriptionId $sub.Id
New-AzSubscriptionDeployment -location uksouth -TemplateURI 'https://raw.githubusercontent.com/HybrIT-Services/AzureLighthouse/main/HybrITReaderLightHouse.json'
}
If you require HybrIT to provide Multi-User authorization to protect your back up against "Critical Operations" such as preventing deletion by a bad actor then apply the below command against a dedicated Subscription that is used only for the purpose of Resource Guard. For more information see: https://docs.microsoft.com/en-us/azure/backup/multi-user-authorization
Be Careful not to apply other lighthouse files to your BackupSecurity Subscription
New-AzSubscriptionDeployment -location uksouth -TemplateURI 'https://raw.githubusercontent.com/HybrIT-Services/AzureLighthouse/main/HybrITSecureBackupLightHouse.json'
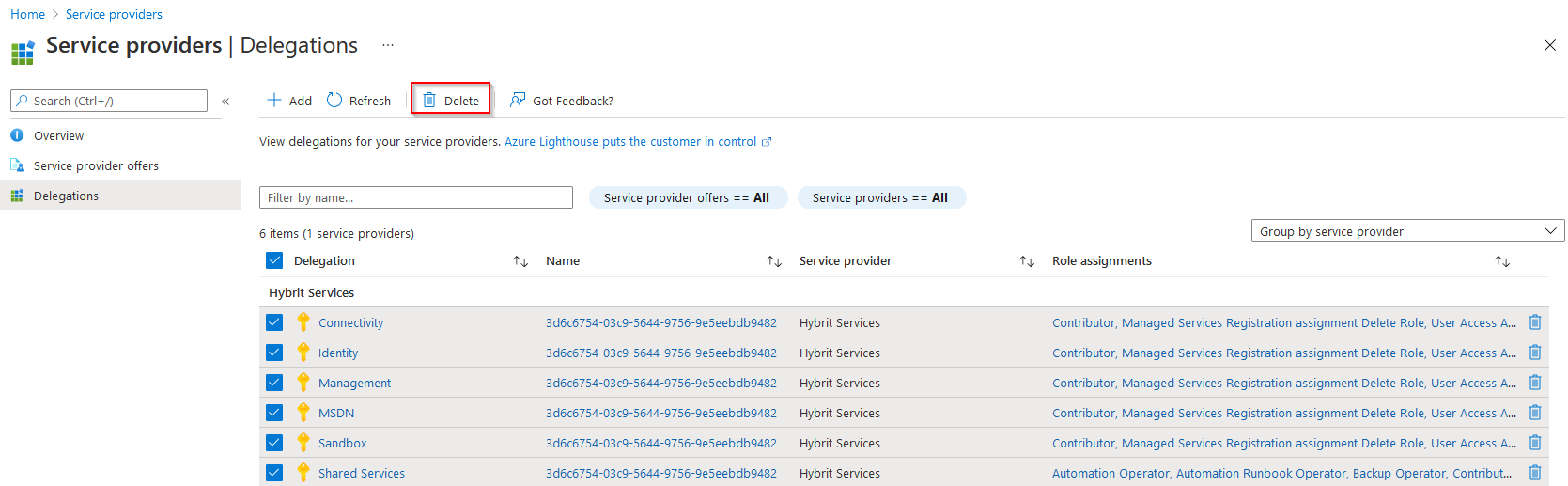
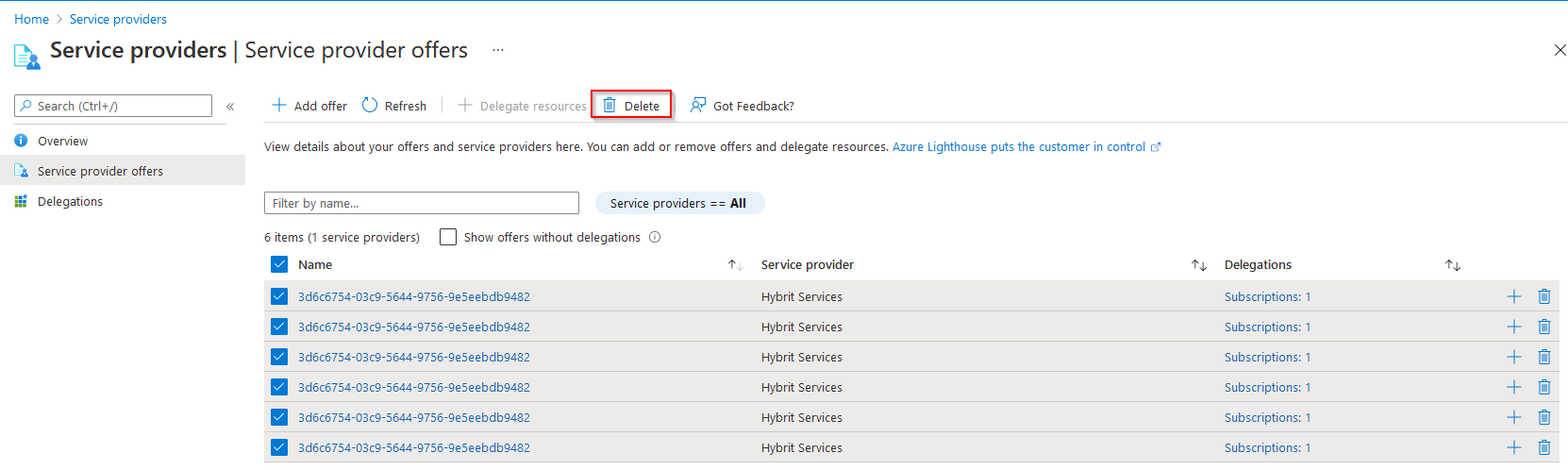
Access can be removed at any time from the Portal or by using Azure PowerShell. To remove from Access from the portal use the search bar to find "Service Providers"
Under Delegations simply select and and Delete
To also clean up the left over "Offers" goto the Service Provider offers section. Again select all offers and click the Delete button.