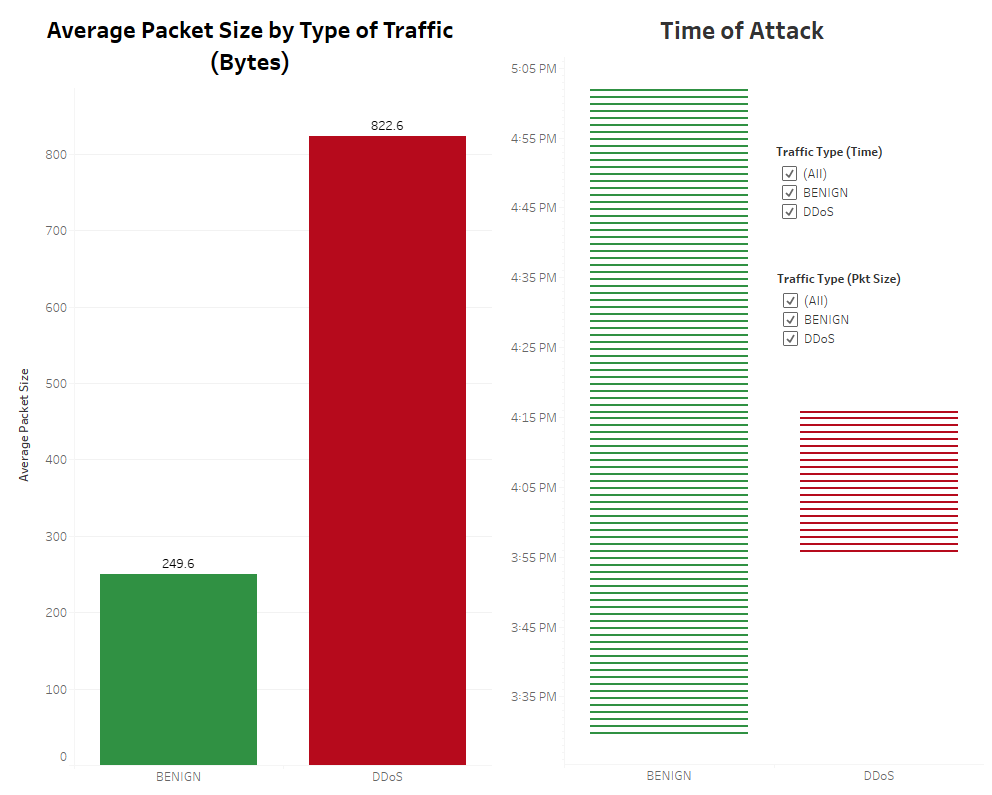
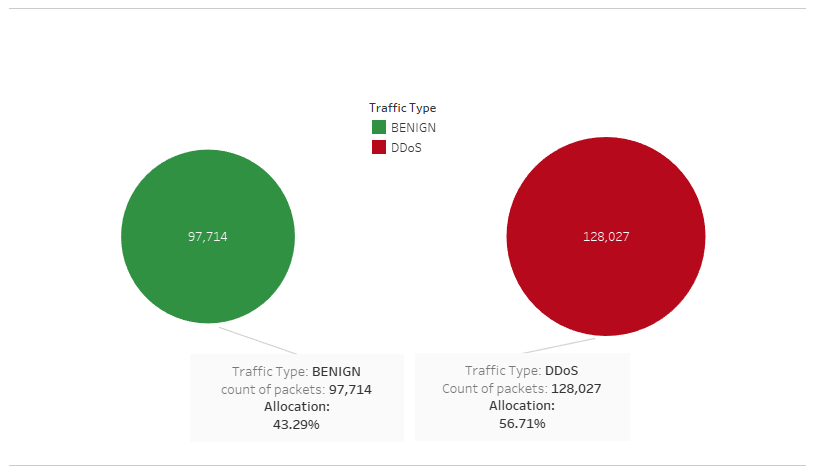
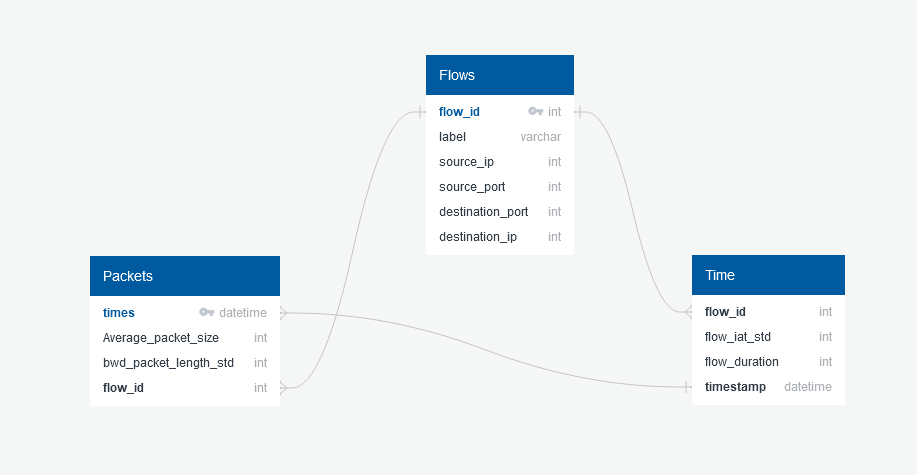
We are using a machine learning model to detect factors that contribute to DDoS cyber attacks in an effort to limit the vulnerability of the average consumer.
Benign: Harmless or well intentioned, the opposite of malicious.
DDoS: Distributed Denial of Service (DDoS). A term used to identify a type malicious attack.
Living in a digital age, Cybersecurity is not only necessary but crucial. Preparedness is key to swiftly detecting and remedying an attack. Preventative measures can help secure your personal information and time from a legitimate cyber threat. We chose this topic to inform the general public of DDoS attacks, the common variables associated, and preventative measure they can take.
Link to Presentation Slides: Project Slides
Link to Tableau Dashboard: Tableau Dashboard
-
How does a DDoS attack happen? -
What does a DDoS attack affect? -
Who is the target audience for DDoS attacks? -
What preventative measures can be taken to protect the average user from a malicious DDoS attack?
-
"The CICIDS2017 dataset consists of labeled network flows, including full packet payloads in pcap format, the corresponding profiles and the labeled flows (GeneratedLabelledFlows.zip) and CSV files for machine and deep learning purposes."
-
Intrusion Detection Evaluation Dataset (CIC-IDS2017) from the Canadian Institute for Cybersecurity.
Description taken from: Data Source
-
Explored numerical values of the cleaned DDoS dataframe.
-
Checked or outliers in the dataframe by creating and analyzing visualizations.
-
Explored each visualization for possible errors and anomalies.
-
Separated data to find the percentage of DDoS data and Benign data.
-
Explore to find missing values and remove them.
-
Gather what columns would be useful to detect DDoS attacks.
-
Build a dataframe using the data attributed to DDoS attacks.
-
Iman Sharafaldin, Arash Habibi Lashkari, and Ali A. Ghorbani, “Toward Generating a New Intrusion Detection Dataset and Intrusion Traffic Characterization”, 4th International Conference on Information Systems Security and Privacy (ICISSP), Portugal, January 2018 -
CISA. (2009, November 4). Understanding Denial-of-Service Attacks. National Cyber Awareness System. Retrieved November 1, 2022, from https://www.cisa.gov/uscert/ncas/tips/ST04-015
- Tableau Public
- VS Code
- Pandas
- Python
- PostgresSQL
-
Friday-WorkingHours-Afternoon-DDos.pcap_ISCX.csv (View/Download)
-
Cleaned_DDoS_Dataframe.csv (View/Download)